Multi-Stage Phishing Campaign Targets Russia with Amnesia RAT and Ransomware
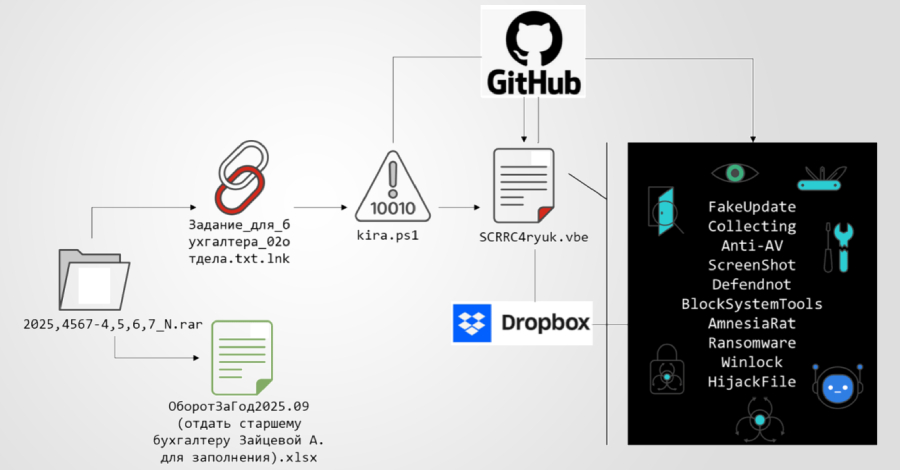
A new multi-stage phishing campaign has been observed targeting users in Russia with ransomware and a remote access trojan called Amnesia RAT. “The attack begins with social engineering lures delivered via business-themed documents crafted to appear routine and benign,” Fortinet FortiGuard Labs researcher Cara Lin said in a technical breakdown published this week. “These documents…
Read more