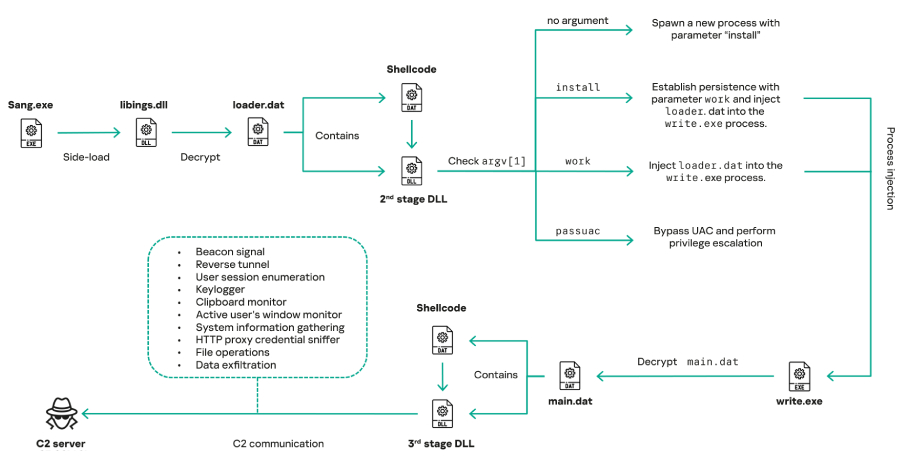
Google Disrupts IPIDEA — One of the World’s Largest Residential Proxy Networks
Google on Wednesday announced that it worked together with other partners to disrupt IPIDEA, which it described as one of the largest residential proxy networks in the world. To that end, the company said it took legal action to take down dozens of domains used to control devices and proxy traffic through them. As of…
Read more