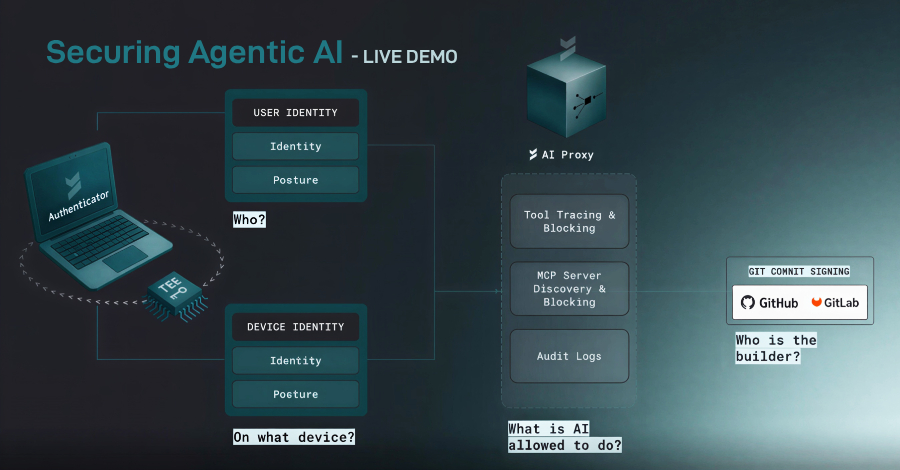
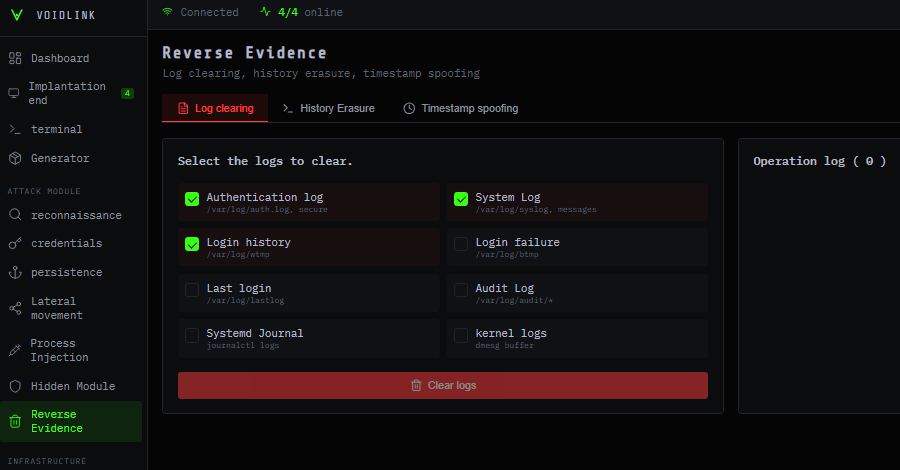
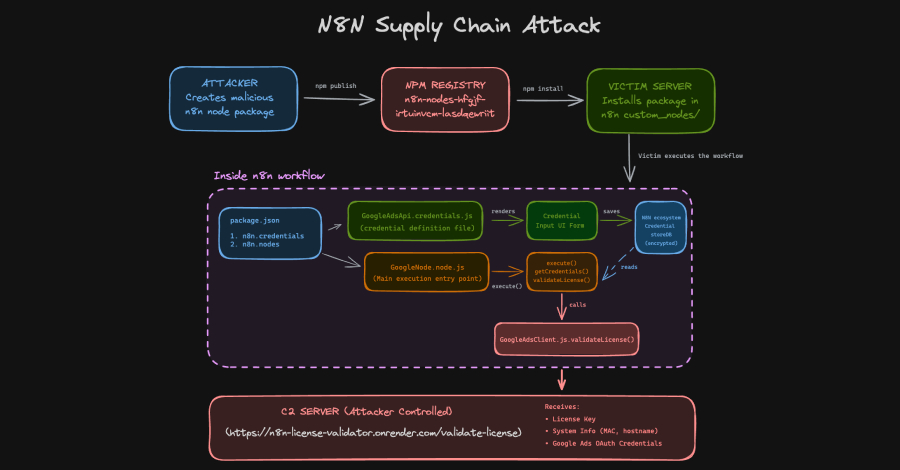
New Research: 64% of 3rd-Party Applications Access Sensitive Data Without Justification
Research analyzing 4,700 leading websites reveals that 64% of third-party applications now access sensitive data without business justification, up from 51% in 2024. Government sector malicious activity spiked from 2% to 12.9%, while 1 in 7 Education sites show active compromise. Specific offenders: Google Tag Manager (8% of violations), Shopify (5%), Facebook Pixel (4%). Download…
Read more