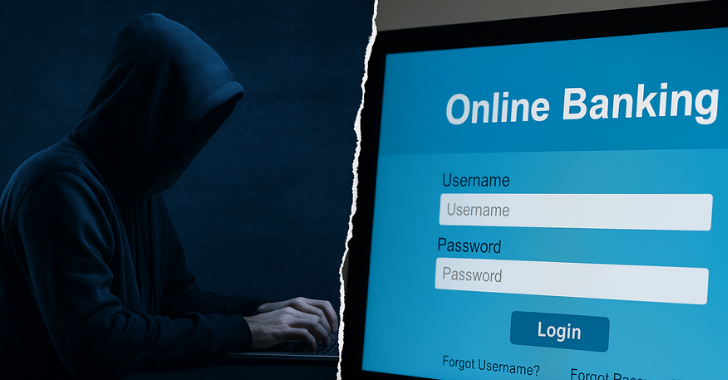
Would you expect an end user to log on to a cybercriminal’s computer, open their browser, and type in their usernames and passwords? Hopefully not! But that’s essentially what happens if they fall victim to a Browser-in-the-Middle (BitM) attack.
Like Man-in-the-Middle (MitM) attacks, BiTM sees criminals look to control the data flow between the victim’s computer and the target service, as

2,751 Responses
I delight in, result in I found just what I used to be having a look for. You have ended my four day long hunt! God Bless you man. Have a nice day. Bye
https://lkra39.at/
This is the perfect webpage for everyone who hopes to find out about this topic. You know a whole lot its almost tough to argue with you (not that I personally will need to…HaHa). You certainly put a new spin on a subject that has been written about for decades. Great stuff, just wonderful!
Razed casino
Pretty! This was an extremely wonderful post. Many thanks for providing this information.
CSFAIL свежие промокоды
Students, professionals, and hobbyists alike rely on OneConverter.com as a trusted resource. High school students use it to complete homework questions, ensuring they understand how to convert between units of volume or temperature. College researchers appreciate its scientific precision when dealing with complex conversions in physics or engineering. Business professionals often need quick currency or time zone calculations to plan international meetings; this site delivers those results instantly. DIY enthusiasts measure materials for home improvement projects by converting square feet to square meters or gallons to liters. Photographers evaluate storage needs by converting between megabytes and gigabytes. Fitness trainers track distances and energy expenditure by switching between miles and kilometers or calories and kilojoules. With OneConverter, there’s no need to memorize dozens of conversion factors — just input your number, choose your units, and the answer appears. The clear layout and straightforward instructions help users learn as they go, making the site both a tool and a teaching aid. Regardless of your field or expertise level, OneConverter.com provides the conversions you need, right when you need them.
OneConverter
Picture this: you’re cooking dinner and the recipe calls for grams, but your scale only shows ounces. Later, you’re helping your child with homework and suddenly need to convert meters per second into kilometers per hour. The next morning, you’re preparing a presentation and realize the client wants it in PDF format. Three different situations, three different problems – and usually, three different apps.
That’s the hassle OneConverter eliminates. It’s an all-in-one online tool designed for people who want life to be simpler, faster, and smarter. No downloads, no subscriptions, no headaches – just answers, right when you need them.
Unit Conversions Made Effortless
Most conversion tools handle only the basics. OneConverter goes further – much further. With more than 50,000 unit converters, it can handle everyday situations, advanced academic work, and professional challenges without breaking a sweat.
Everyday Basics: length, weight, speed, temperature, time, area, volume, energy.
Engineering & Physics: torque, angular velocity, density, acceleration, moment of inertia.
Heat & Thermodynamics: thermal conductivity, thermal resistance, entropy, enthalpy.
Radiology: absorbed dose, equivalent dose, radiation exposure.
Fluids: viscosity, flow rate, pressure, surface tension.
Electricity & Magnetism: voltage, current, resistance, capacitance, inductance, flux.
Chemistry: molarity, concentration, molecular weight.
Astronomy: light years, parsecs, astronomical units.
Everyday Extras: cooking measures, shoe and clothing sizes, fuel efficiency.
From the classroom to the lab, from the office to your kitchen – OneConverter has a solution ready.
OneConverter.com
Digital life demands accuracy. Engineers, researchers, students, and professionals rely on precise numbers and flawless documents. Yet the tools they need are often scattered across multiple apps, hidden behind subscriptions, or limited in scope. OneConverter addresses this challenge by consolidating advanced unit conversion calculators and PDF document utilities into a single, accessible platform.
Comprehensive Unit Conversions
The strength of OneConverter lies in its range. With more than 50,000 unit converters, it covers virtually every field of science, technology, and daily life.
Core Measurements: conversions for length, weight, speed, temperature, area, volume, time, and energy. These fundamental tools support everyday requirements such as travel, shopping, and cooking.
Engineering & Physics: advanced calculators for torque, density, angular velocity, acceleration, and moment of inertia, enabling precision in both academic study and professional design.
Heat & Thermodynamics: tools for thermal conductivity, resistance, entropy, and enthalpy, providing clarity for scientific research and industrial applications.
Radiology: units such as absorbed dose, equivalent dose, and radiation exposure, essential for healthcare professionals and medical physicists.
Fluid Mechanics: viscosity, pressure, flow rate, and surface tension, all indispensable in laboratory and engineering environments.
Electricity & Magnetism: extensive coverage including voltage, current, resistance, inductance, capacitance, flux, and charge density, supporting fields from electronics to energy.
Chemistry: molarity, concentration, and molecular weight calculators, saving valuable time in laboratories and classrooms.
Astronomy: astronomical units, parsecs, and light years, serving both researchers and students exploring the cosmos.
Practical Applications: everyday conversions for recipes, fuel efficiency, and international clothing sizes.
By combining breadth and accuracy, OneConverter ensures that calculations are reliable, consistent, and instantly available.
oneconverter.com
I think that everything said was very reasonable. But, what about this? suppose you were to create a awesome headline? I ain’t saying your content is not good., however suppose you added a post title to maybe get folk’s attention? I mean %BLOG_TITLE% is kinda vanilla. You ought to look at Yahoo’s home page and watch how they write post titles to get viewers to click. You might add a related video or a pic or two to grab readers excited about what you’ve written. Just my opinion, it would bring your posts a little bit more interesting.
https://keslaser.com.ua/vodinnya-v-doshch-i-tuman-yake-svitlo-dopomozhe-vam-bachyty-krashche
I think that what you posted made a lot of sense. But, think on this, suppose you were to create a awesome post title? I ain’t suggesting your information isn’t solid., however what if you added a title that makes people want more? I mean %BLOG_TITLE% is kinda plain. You might look at Yahoo’s home page and see how they create post headlines to grab people interested. You might add a related video or a related pic or two to get readers interested about what you’ve written. In my opinion, it could bring your website a little livelier.
https://e-comex.com.ua/linzi-u-fari-dovgovichnist-yakist-i-ekonomiya-palnogo
This is very interesting, You are a very skilled blogger. I’ve joined your rss feed and look forward to seeking more of your excellent post. Also, I’ve shared your website in my social networks!
https://adrenalinsport.dp.ua/remont-far-koli-krashche-zvernutisia-do-fakhivtsiv-a-koli-mozhna-zrobiti-samomu.html
Hi all, here every one is sharing such experience, therefore it’s pleasant to read this weblog, and I used to go to see this website everyday.
Banda Casino регистрация
I’m not sure exactly why but this web site is loading extremely slow for me. Is anyone else having this issue or is it a problem on my end? I’ll check back later and see if the problem still exists.
gaelic football betting with crypto
https://yandex.ru/profile/147633783627?lang=ru
ООО “Мир ремней” – Производство приводных ремней, тефлоновых сеток и лент.
Телефон +7 (936) 333-93-03
Hi! Do you use Twitter? I’d like to follow you if that would be ok. I’m absolutely enjoying your blog and look forward to new posts.
регистрация зума казино
Good day! Do you know if they make any plugins to safeguard against hackers? I’m kinda paranoid about losing everything I’ve worked hard on. Any suggestions?
lee bet casino
whoah this weblog is wonderful i really like studying your posts. Keep up the great work! You realize, many persons are looking round for this information, you could help them greatly.
перейти на сайт
ZenTrader Binary Options: Clear Strategies for Modern Investors
ZenTrader Binary Options provide a simple yet powerful approach to global trading. With fast execution, transparent tools, and flexible strategies, both beginners and professionals can balance risks while seeking growth. By exploring ZenTrader through https://shoku-academia.jp/, traders gain valuable knowledge, sharpen decision-making skills, and build confidence to achieve smarter and more consistent results in today’s financial markets.
Five Stars Market Binary Options: Pathway to Smarter Trading
Five Stars Market Binary Options give traders a clear and efficient way to participate in global financial markets. With simple tools, transparent conditions, and fast execution, both beginners and experts can explore new opportunities while managing risks effectively. By visiting https://ivr-nurse.jp/ , investors can learn more about Five Stars Market, enhance strategies, and work toward consistent results in binary options trading.
moeinclub Unique experiences with authentic value inspire communities to engage globally.
Thank you, I have recently been looking for information about this subject for ages and yours is the greatest I’ve found out so far. However, what about the bottom line? Are you positive about the source?
Rifar Tubog
broodbase – Their platform is refreshing, reliable content attracts genuine visitors globally.
broodbase – Clean layout, professional services, and engaging design impressed me today.
banehmagic – The brand feels magical, creative energy and reliability combined beautifully.
centensports – They cover many niches, always something new to explore each day.
sunnyflowercases – The site feels clean and not cluttered even with many items.
Unlock your images with WebPtoJPGHero.com, the simple, free solution for solving WebP compatibility issues. While the WebP format helps websites load faster, it can leave you with files you can’t easily edit or share. Our online tool provides an instant fix, transforming any WebP image into a high-quality JPG that works seamlessly across all your devices and applications. You can fine-tune the output quality to balance clarity and file size, and even save time by converting an entire batch of photos at once. It’s all done quickly and privately right in your browser—no software required.
WebPtoJPGHero.com
JPG Hero converter is an online image converter built for speed, simplicity, and accessibility. This web-based platform allows instant conversion of popular image formats such as PNG, WebP, and BMP into JPG files. No downloads, installations, or user accounts are required. The entire process happens in-browser and takes only a few seconds. Users can upload up to 20 files at once for batch conversion, making it suitable for individuals and professionals managing multiple images. All uploaded files are automatically deleted after processing to maintain privacy and ensure data security. JPGHero.com is compatible with all modern devices, including desktops, tablets, and smartphones, offering flexibility for work on the go. Whether the goal is to reduce image file size, prepare visuals for the web, or standardize a project’s image format, this tool delivers clean, reliable results without any extra steps.
JPGHero
JPG Hero converter is an online image converter built for speed, simplicity, and accessibility. This web-based platform allows instant conversion of popular image formats such as PNG, WebP, and BMP into JPG files. No downloads, installations, or user accounts are required. The entire process happens in-browser and takes only a few seconds. Users can upload up to 20 files at once for batch conversion, making it suitable for individuals and professionals managing multiple images. All uploaded files are automatically deleted after processing to maintain privacy and ensure data security. JPGHero.com is compatible with all modern devices, including desktops, tablets, and smartphones, offering flexibility for work on the go. Whether the goal is to reduce image file size, prepare visuals for the web, or standardize a project’s image format, this tool delivers clean, reliable results without any extra steps.
JPGHero
WebPtoJPGHero converter is an online image converter built for speed, simplicity, and accessibility. This web-based platform allows instant conversion of popular image formats such as PNG, WebP, and BMP into JPG files. No downloads, installations, or user accounts are required. The entire process happens in-browser and takes only a few seconds. Users can upload up to 20 files at once for batch conversion, making it suitable for individuals and professionals managing multiple images. All uploaded files are automatically deleted after processing to maintain privacy and ensure data security. WebPtoJPGHero is compatible with all modern devices, including desktops, tablets, and smartphones, offering flexibility for work on the go. Whether the goal is to reduce image file size, prepare visuals for the web, or standardize a project’s image format, this tool delivers clean, reliable results without any extra steps.
WebPtoJPGHero
ucbstriketowin – The whole vibe here feels energetic, bold, and fun overall.
Компания «РБТ-Сервис» — профессиональный ремонт стиральных машин в СПб !
Для записи на ремонт и консультации посетите группу ВК: vk.com/remont_stiralnyh_mashin_spb_top
Качественный ремонт стиральных машин в СПб выполняют опытные мастера с многолетним стажем. Ремонт стиральных машин СПб включает диагностику, замену запчастей и настройку техники любой марки. Если требуется срочный ремонт стиральных машин — специалисты приезжают в день обращения.
– Гарантия до 2 лет
– Оригинальные запчасти
– Выезд по всему Санкт-Петербургу
Ремонт стиральных машин
dividedheartsofamericafilm – The name alone makes me curious about the message behind it.
dietzmann – Their site feels strong, visuals are sharp and design commanding.
lastminute-corporate – Very efficient vibe, looks like it saves a lot of time.
Wow, superb blog layout! How long have you been blogging for? you made blogging look easy. The overall look of your web site is magnificent, let alone the content!
kra40cc вход
themacallenbuilding – First impression feels strong, like it’s a trustworthy and stylish brand.
crownaboutnow – Very good user experience, clean UI and meaningful content.
biotecmedics – I like the simple design, very easy to browse and read.
goestotown – I like the simple navigation, makes browsing quick and enjoyable.
dividedheartsofamericafilm – Everything loads quickly which makes the browsing experience enjoyable.
muralspotting – I enjoyed browsing, the colors and energy make it exciting.
bigprintnewspapers – This feels reliable, like something people can actually depend on regularly.
dankglassonline – I like how creative and engaging the visuals come across.
geomatique237 – Design feels raw and creative, though clarity is lacking in sections.
cangjigedh – Simple navigation makes it easy to stay engaged longer.
ceriavpn – Connection works well, browsing without lag feels really satisfying today.
yyap16 – I like the minimal layout, it’s easy on the eyes.
eljiretdulces – A refreshing site that feels welcoming, I’ll definitely come back.
newbalance550 – A smooth browsing experience, everything works well from start to finish.
flmo1xt – I enjoyed how minimal the design feels, very modern overall.
alusstore – Pages load quickly, making the shopping experience smooth and enjoyable.
rwbj – The site gives a modern vibe, clean and functional design.
wcbxhmsdo8nr – Navigation is straightforward, I didn’t run into any confusion.
PNGtoWebPHero.com is a utility for encoding PNG (Portable Network Graphics) images into the WebP format. The tool provides developers with control over the encoding process to optimize web assets. Users can select the compression mode – either lossless, which uses advanced techniques to reduce file size without data loss, or lossy, which uses predictive coding to achieve much greater file size reduction. For lossy encoding, a quality factor can be specified to manage the trade-off between file size and visual fidelity. The service correctly handles the PNG alpha channel, preserving transparency in the final WebP output. All processing is server-side, and data is purged after conversion.
pngtowebphero
AVIFtoPNGHero.com is a free converter for turning next-generation AVIF images into high-quality PNG files. As the web adopts the efficient AVIF format, this tool provides a simple way to ensure your images are viewable on older browsers and systems that lack support. The conversion process preserves crucial details, including transparency, making it ideal for web graphics and icons. Simply drag and drop your AVIF files, convert entire batches at once, and download your compatible PNGs in seconds. The service is entirely browser-based, requires no installation, and automatically deletes all files to guarantee your privacy.
aviftopnghero
It’s awesome to pay a quick visit this site and reading the views of all friends concerning this paragraph, while I am also zealous of getting know-how.
https://fontanero.com.ua/
Greate article. Keep writing such kind of info on your page. Im really impressed by it.
Hi there, You’ve performed an incredible job. I’ll definitely digg it and personally recommend to my friends. I am sure they’ll be benefited from this website.
http://216.158.236.67/hello-world/#comment-8383
v1av2 – Browsing felt smooth throughout, nothing interrupted the flow here.
v1av7 – Works perfectly on mobile, responsive and easy to use there.
v1av3 – No glitches or errors appeared while exploring.
sj256.cc – Overall it feels promising, I’ll revisit to see improvements.
303vip.info – A bit more detail in the “About” section would help build trust.
storagesheds.store – Overall promising site, with a bit more polish it could be great.
businessesnewsdaily.site – The news layout feels professional, useful stories are easy to find.
Hi there, after reading this amazing post i am as well delighted to share my familiarity here with colleagues.
keepstyle
aaront – I hope they add portfolio or project examples soon.
cooperativadeartesanos – Some links appear broken or not yet active, maybe site still under construction.
av07 – The color scheme is dark and bold, gives unique feel.
lapotranca.store – Clean layout so far, gives a professional first impression.
datacaller.store – Good domain name, memorable and descriptive—potentially strong brand.
scilla.biz – Could be a blog, portfolio, or business — excited to see.
This information is worth everyone’s attention. When can I find out more?
leebet casino
Trade, earn points, and explore Web3 projects on Asterdex
— your gateway to decentralized markets.
I’ve been using Asterdex
lately — cool platform where you can trade, collect points, and track crypto trends in one place.
With Asterdex
, users can trade assets, earn rewards, and explore data from multiple blockchains in real time.
Check out Asterdex
— you can trade, earn points, and discover trending tokens fast. ??
aster perp
kaixin2020.live – Overall impression is positive, I’ll visit again for new content.
av07.cc – Good first impression, I hope they keep content fresh.
Trade, earn points, and explore Web3 projects on Asterdex
— your gateway to decentralized markets.
I’ve been using Asterdex
lately — cool platform where you can trade, collect points, and track crypto trends in one place.
With Asterdex
, users can trade assets, earn rewards, and explore data from multiple blockchains in real time.
Check out Asterdex
— you can trade, earn points, and discover trending tokens fast. ??
cat casino слоты
Me enredei no caos de IJogo Casino, explode com uma vibe de cassino enredada. A selecao de titulos e um emaranhado de prazeres. com slots tematicos de aventuras enredadas. O servico e confiavel como uma raiz. oferecendo respostas claras como um labirinto resolvido. Os ganhos chegam rapido como uma teia rompida. mesmo assim mais bonus seriam um diferencial enredado. Em resumo, IJogo Casino e um cassino online que e um labirinto de diversao para os cacadores de vitorias intrincadas! Vale dizer o visual e uma explosao de vinhas. criando uma experiencia de cassino intrincada.
baixa ijogo|
u888vn – Informative posts and handy guides make this a go-to site.
Je suis pactise avec Mafia Casino, ca forge un syndicate de defis impitoyables. La cache de jeux est un arsenal cache de plus de 5000 armes, avec des slots aux themes gangster qui font chanter les rouleaux. Le service conspire en continu 24/7, avec une ruse qui anticipe les traitrises. Les transferts glissent stables et acceleres, malgre cela des complots promotionnels plus frequents dynamiseraient le territoire. En apotheose mafieuse, Mafia Casino devoile un plan de triomphes secrets pour les parrains de casinos virtuels ! En plus le portail est une planque visuelle imprenable, simplifie la traversee des complots ludiques.
mafia russe casino|
htechwebservice – I appreciate the clean interface and helpful tutorials.
Wow, awesome blog structure! How long have you been blogging for? you make blogging glance easy. The total look of your website is great, let alone the content material!
казино зума
basingstoketransition – Clear call to action, motivates me to do more for environment.
Ich bin begeistert von Snatch Casino, es bietet einen einzigartigen Thrill. Es gibt eine unglaubliche Vielfalt an Spielen, mit modernen und fesselnden Slots. Der Support ist 24/7 verfugbar, bietet prazise Losungen. Der Prozess ist einfach und reibungslos, jedoch haufigere Promos waren cool. Zusammenfassend Snatch Casino garantiert eine top Spielerfahrung fur Online-Wetten-Enthusiasten ! Daruber hinaus das Design ist ansprechend und intuitiv, verstarkt den Wunsch zuruckzukehren.
snatch casino kod|
liveforextrading – I like how they break down signals and indicators simply.
Je suis pactise avec Mafia Casino, ca eleve le jeu a un niveau de boss legendaire. La cache de jeux est un arsenal cache de plus de 5000 armes, incluant des roulettes pour des tours de table. Le suivi protege avec une omerta absolue, mobilisant des canaux multiples pour une execution immediate. Les transferts glissent stables et acceleres, toutefois des largesses gratuites supplementaires boosteraient les operations. Dans l’ensemble du domaine, Mafia Casino invite a une intrigue sans trahison pour les parrains de casinos virtuels ! De surcroit le portail est une planque visuelle imprenable, infuse une essence de mystere mafieux.
mafia iii trailer 3 casino|
Wow, awesome blog layout! How long have you been blogging for? you make blogging look easy. The overall look of your site is wonderful, as well as the content!
http://www.cryptocoinsnewshub.com/yak-stekla-far-mozhut-vplynuty-na-efektyvnist-osvi.html
bbc2y – Hoping they add articles or media soon, looking forward to that.
Ich bin komplett hin und weg von SpinBetter Casino, es liefert ein Abenteuer voller Energie. Das Angebot an Spielen ist phanomenal, mit Spielen, die fur Kryptos optimiert sind. Die Hilfe ist effizient und pro, bietet klare Losungen. Die Zahlungen sind sicher und smooth, trotzdem regelma?igere Aktionen waren toll. Alles in allem, SpinBetter Casino ist ein Muss fur alle Gamer fur Online-Wetten-Fans ! Daruber hinaus die Interface ist intuitiv und modern, was jede Session noch besser macht. Besonders toll die Sicherheit der Daten, die Flexibilitat bieten.
https://spinbettercasino.de/|
Ich bin absolut hingerissen von NV Casino, es ist ein Abenteuer, das pulsiert wie ein Herzschlag. Es gibt eine beeindruckende Auswahl an Optionen, mit dynamischen Live-Sessions. Die Mitarbeiter reagieren blitzschnell, bietet klare Antworten. Die Gewinne kommen ohne Verzogerung, trotzdem zusatzliche Freispiele waren toll. Zum Abschluss, NV Casino garantiert Top-Unterhaltung fur Casino-Enthusiasten ! Au?erdem die Navigation ist kinderleicht, was jede Session noch spannender macht.
https://playnvcasino.de/|
Adoro completamente Flabet Casino, oferece um thrill unico. A gama de jogos e impressionante, com slots modernos e cativantes. O servico ao cliente e top, respondendo em um piscar de olhos. Os saques sao super rapidos, contudo as ofertas poderiam ser mais generosas. Em resumo, Flabet Casino oferece prazer garantido para os jogadores em busca de diversao ! Ademais o design e atraente e intuitivo, facilita a experiencia geral.
como fazer saque na flabet|
Ich bin suchtig nach Snatch Casino, es ist eine dynamische Erfahrung. Das Spielangebot ist beeindruckend, mit modernen und fesselnden Slots. Der Service ist von bemerkenswerter Effizienz, mit tadellosem Follow-up. Die Transaktionen sind zuverlassig, jedoch zusatzliche Belohnungen waren top. Zusammenfassend Snatch Casino lohnenswert fur Crypto-Liebhaber ! Beachten Sie auch die Site ist stylish und schnell, fugt Komfort zum Spiel hinzu.
snatch casino betrug|
J’eprouve une loyaute infinie pour Mafia Casino, il orchestre une conspiration de recompenses secretes. La reserve est un code de divertissements mafieux, avec des slots aux themes gangster qui font chanter les rouleaux. Le suivi protege avec une omerta absolue, avec une ruse qui anticipe les traitrises. Les retraits s’executent avec une furtivite remarquable, occasionnellement des rackets de recompense additionnels scelleraient les pactes. A la fin de cette conspiration, Mafia Casino devoile un plan de triomphes secrets pour les gardiens des empires numeriques ! Par surcroit la structure vibre comme un code ancestral, infuse une essence de mystere mafieux.
film mafia casino|
Please let me know if you’re looking for a writer for your blog. You have some really great articles and I feel I would be a good asset. If you ever want to take some of the load off, I’d love to write some content for your blog in exchange for a link back to mine. Please blast me an e-mail if interested. Thanks!
online gokken zumospin
Ich bin beeindruckt von SpinBetter Casino, es bietet einen einzigartigen Kick. Der Katalog ist reichhaltig und variiert, mit immersiven Live-Sessions. Der Service ist von hoher Qualitat, verfugbar rund um die Uhr. Die Transaktionen sind verlasslich, obwohl regelma?igere Aktionen waren toll. Global gesehen, SpinBetter Casino bietet unvergessliche Momente fur Krypto-Enthusiasten ! Zusatzlich die Plattform ist visuell ein Hit, gibt den Anreiz, langer zu bleiben. Ein Pluspunkt ist die schnellen Einzahlungen, die Vertrauen schaffen.
spinbettercasino.de|
Ich liebe die Atmosphare von NV Casino, es bietet eine Reise voller Spannung. Das Angebot an Spielen ist phanomenal, mit dynamischen Live-Sessions. Die Hilfe ist effizient und professionell, garantiert hochwertige Hilfe. Der Prozess ist unkompliziert, ab und zu mehr Belohnungen waren ein Hit. Kurz gesagt, NV Casino ist eine Plattform, die rockt fur Casino-Enthusiasten ! Daruber hinaus das Design ist modern und ansprechend, fugt eine Prise Magie hinzu.
https://playnvcasino.de/|
Thanks , I’ve recently been searching for info about this topic for a long time and yours is the greatest I’ve came upon so far. But, what about the conclusion? Are you positive in regards to the source?
https://vedanta.dp.ua/yak-sklo-far-dopomahaye-znyzyty-jmovirnist-dtp-vno.html
Good day I am so happy I found your website, I really found you by mistake, while I was searching on Google for something else, Nonetheless I am here now and would just like to say thank you for a fantastic post and a all round exciting blog (I also love the theme/design), I don’t have time to read through it all at the moment but I have book-marked it and also added in your RSS feeds, so when I have time I will be back to read a great deal more, Please do keep up the great work.
https://tvoy-prazdnik.kiev.ua/yak-ne-pereplatyty-pry-pokuptsi-skla-fary-onlajn.html
J’ai un vrai coup de c?ur pour Bingoal Casino, on ressent une vibe folle. La variete des titres est impressionnante, incluant des paris sportifs palpitants. Amplifiant l’experience initiale. Les agents repondent avec rapidite, garantissant un support de qualite. Les gains arrivent sans delai, cependant plus de promos regulieres seraient top. En bref, Bingoal Casino est une plateforme qui dechire pour les joueurs en quete d’excitation ! De plus la navigation est simple et agreable, donne envie de prolonger l’experience. Un autre atout majeur les tournois reguliers pour la competition, offre des recompenses continues.
Ouvrir maintenant|
Ich kann nicht genug bekommen von NV Casino, es ist ein Abenteuer, das pulsiert wie ein Herzschlag. Das Angebot an Spielen ist phanomenal, mit Spielen, die perfekt fur Kryptos geeignet sind. Die Mitarbeiter reagieren blitzschnell, erreichbar zu jeder Stunde. Die Gewinne kommen ohne Verzogerung, obwohl die Angebote konnten gro?zugiger sein. Kurz gesagt, NV Casino ist eine Plattform, die rockt fur Casino-Enthusiasten ! Nicht zu vergessen die Plattform ist optisch ein Highlight, verstarkt die Immersion.
playnvcasino.de|
J’aime l’atmosphere unique de Locowin Casino, c’est une plateforme qui deborde de vitalite. Il y a une multitude de jeux captivants, comprenant des jeux optimises pour les cryptos. Le bonus d’accueil est seduisant. Les agents repondent avec celerite, garantissant un support de qualite. Les gains arrivent sans retard, de temps en temps des bonus plus varies seraient apprecies. En resume, Locowin Casino garantit du plaisir a chaque instant pour les joueurs en quete d’excitation ! Ajoutons que l’interface est intuitive et elegante, incite a prolonger l’experience. Egalement appreciable les options de paris sportifs variees, propose des avantages personnalises.
Entrer sur le site web|
Je suis completement captive par Casinia Casino, ca offre un plaisir aristocratique. Il y a une abondance de jeux captivants, avec des slots thematiques et innovants. Le bonus de bienvenue est genereux. Les agents repondent avec celerite, avec une aide precise. Les transactions sont fiables, parfois des recompenses additionnelles seraient royales. Pour conclure, Casinia Casino offre une experience memorable pour les joueurs en quete d’excitation ! Ajoutons que le design est moderne et fluide, donne envie de prolonger l’experience. Egalement appreciable les paiements securises en crypto, assure des transactions fiables.
Touchez ici|
Je suis surpris par Locowin Casino, ca transporte dans un univers envoutant. Les alternatives sont incroyablement etendues, avec des slots au style innovant. Pour un lancement puissant. L’equipe d’assistance est remarquable, accessible a tout instant. La procedure est aisee et efficace, mais quelques tours gratuits supplementaires seraient apprecies. Pour synthetiser, Locowin Casino est une plateforme qui excelle pour ceux qui parient en crypto ! A mentionner la navigation est simple et engageante, ajoute un confort notable. Particulierement attractif les evenements communautaires captivants, offre des privileges sur mesure.
Trouver plus|
Heya this is kinda of off topic but I was wanting to know if blogs use WYSIWYG editors or if you have to manually code with HTML. I’m starting a blog soon but have no coding experience so I wanted to get advice from someone with experience. Any help would be greatly appreciated!
banda казино
Attractive portion of content. I simply stumbled upon your blog and in accession capital to assert that I acquire in fact loved account your blog posts. Any way I’ll be subscribing on your augment and even I achievement you get admission to persistently rapidly.
банда казино
Hello very nice blog!! Guy .. Beautiful .. Superb .. I will bookmark your blog and take the feeds also? I am glad to seek out a lot of helpful information here in the post, we want develop more strategies on this regard, thanks for sharing. . . . . .
https://ameli-studio.com.ua/yak-unyknuty-zapotivannya-novoyi-steklo-fara.html
Je suis accro a Bingoal Casino, ca plonge dans un univers envoutant. La selection de jeux est spectaculaire, proposant des jeux de table immersifs. Accompagne de paris gratuits. L’assistance est efficace et professionnelle, joignable a tout moment. Les paiements sont securises et fluides, parfois des offres plus genereuses ajouteraient de l’attrait. En bref, Bingoal Casino offre une experience inoubliable pour les fans de casino en ligne ! De plus le design est moderne et fluide, ajoute une touche de confort. Un avantage supplementaire les evenements communautaires engageants, renforce le sentiment de communaute.
AccГ©der aux infos|
Ich habe einen totalen Hang zu SpinBetter Casino, es liefert ein Abenteuer voller Energie. Das Angebot an Spielen ist phanomenal, mit dynamischen Tischspielen. Der Service ist von hoher Qualitat, mit praziser Unterstutzung. Die Transaktionen sind verlasslich, gelegentlich mehr abwechslungsreiche Boni waren super. Alles in allem, SpinBetter Casino bietet unvergessliche Momente fur Adrenalin-Sucher ! Daruber hinaus die Plattform ist visuell ein Hit, gibt den Anreiz, langer zu bleiben. Zusatzlich zu beachten die Vielfalt an Zahlungsmethoden, die Vertrauen schaffen.
spinbettercasino.de|
Je suis totalement fascine par Bingoal Casino, c’est une plateforme qui foisonne de vigueur. L’eventail de jeux est extraordinaire, offrant des sessions live intenses. Doublement des depots jusqu’a 200 €. L’aide est performante et experte, assurant un support premium. La procedure est aisee et efficace, bien que des offres plus liberales ajouteraient de la valeur. Tout compte fait, Bingoal Casino est essentiel pour les amateurs pour les aficionados de jeux contemporains ! A mentionner le site est veloce et seduisant, ajoute un confort notable. Un autre avantage cle les evenements communautaires captivants, propose des recompenses permanentes.
Explorer le site web|
Je suis completement fou de Locowin Casino, c’est une plateforme qui bouillonne d’energie. La selection de jeux est phenomenale, proposant des jeux de table immersifs. Pour un demarrage en force. Le suivi client est irreprochable, avec une aide precise et rapide. Les gains arrivent sans delai, de temps en temps des offres plus genereuses ajouteraient du piquant. Dans l’ensemble, Locowin Casino est un incontournable pour les joueurs pour ceux qui aiment parier en crypto ! En prime la navigation est simple et agreable, facilite une immersion totale. Un plus non negligeable les options de paris sportifs variees, qui booste l’engagement.
Apprendre les dГ©tails|
Je suis completement ensorcele par Casinia Casino, on ressent une energie fastueuse. Le repertoire est riche et varie, comprenant des jeux compatibles avec les cryptos. Avec un Bonus Crab exclusif. L’assistance est precise et elegante, avec une aide claire et veloce. Les transactions sont fiables et rapides, de temps a autre plus de promos frequentes brilleraient davantage. Pour conclure, Casinia Casino fournit une experience inoubliable pour les passionnes de frissons grandioses ! Ajoutons que le site est rapide et majestueux, incite a prolonger l’experience. Un avantage notable le programme VIP avec 5 rangs princiers, cree une communaute vibrante.
Essayer d’explorer|
J’ai un engouement pour Locowin Casino, ca transporte dans un univers envoutant. La gamme de jeux est spectaculaire, avec des slots au style innovant. Associe a des tours gratuits sans wager. Les agents reagissent avec promptitude, toujours pret a intervenir. La procedure est aisee et efficace, bien que quelques tours gratuits supplementaires seraient apprecies. Globalement, Locowin Casino merite une exploration approfondie pour ceux qui parient en crypto ! De surcroit la plateforme est esthetiquement remarquable, ce qui eleve chaque session a un niveau superieur. Particulierement attractif les evenements communautaires captivants, qui stimule l’engagement.
Voir les meilleurs choix|
I’m surrounded by Wazamba Casino, it echoes a flood of wonder. The breadth in selections is breathtaking, incorporating wagers on athletic events. Paired with 200 gratis rotations. Promoting continuous enjoyment. Disbursements are managed efficiently, yet consistent campaigns may increase allure. Collectively , Wazamba Casino supplies incomparable delight for wagering lovers ! Moreover the architecture is creatively striking, fortifying absorption in play. Significant is nurturing collective spirit, supplying individualized graces.
wazambagr.com|
I’m totally obsessed with Astronaut Crash by 100HP Gaming, it’s a heart-pounding launch into uncertainty. Dual bet options add layers of strategy, including auto-cashout for risk management. The RTP is impressively high at 97%. Support is lightning-fast and helpful, always ready to assist mid-launch. Transactions process in minutes, however more bonus rounds could add variety. Overall, Astronaut Crash is must-play for risk-takers for multiplier chasers ! On top of that the visuals are sleek and spacey, making every round feel epic. Especially cool demo with real-time stats, which amps up replay value.
astronaut-crashgame777.com|
Je suis captive par Bingoal Casino, il procure une odyssee unique. Le repertoire est opulent et multifacette, incluant des paris sportifs electrisants. Le bonus d’inscription est attractif. L’aide est performante et experte, accessible a tout instant. Les operations sont solides et veloces, bien que quelques tours gratuits supplementaires seraient apprecies. Pour synthetiser, Bingoal Casino merite une exploration approfondie pour les adeptes de sensations intenses ! En outre le site est veloce et seduisant, stimule le desir de revenir. Egalement notable les tournois periodiques pour la rivalite, renforce le sens de communaute.
Voir les meilleurs choix|
Ich habe einen totalen Hang zu SpinBetter Casino, es fuhlt sich an wie ein Strudel aus Freude. Der Katalog ist reichhaltig und variiert, mit innovativen Slots und fesselnden Designs. Der Service ist von hoher Qualitat, bietet klare Losungen. Der Ablauf ist unkompliziert, obwohl mehr Rewards waren ein Plus. Zum Ende, SpinBetter Casino garantiert hochsten Spa? fur Krypto-Enthusiasten ! Nicht zu vergessen die Site ist schnell und stylish, was jede Session noch besser macht. Besonders toll die Community-Events, die Vertrauen schaffen.
https://spinbettercasino.de/|
Je suis hypnotise par Bingoal Casino, c’est une plateforme qui regorge de dynamisme. Il existe une abondance de jeux envoutants, comprenant des jeux optimises pour les cryptos. Le bonus d’inscription est seduisant. Le suivi est exemplaire, avec une assistance exacte et veloce. Les operations sont solides et veloces, mais des bonus plus diversifies seraient souhaitables. Pour synthetiser, Bingoal Casino garantit du divertissement constant pour les enthousiastes de casino en ligne ! A mentionner la plateforme est esthetiquement remarquable, intensifie le plaisir du jeu. Egalement notable les tournois periodiques pour la rivalite, renforce le sens de communaute.
Passer à l’action|
J’adore l’eclat vibrant de Casinia Casino, il offre une aventure etincelante. Le repertoire est riche et multifacette, incluant des paris sportifs palpitants. Renforcant votre tresor initial. Le service est disponible 24/7, avec une aide claire et veloce. Les paiements sont securises et fluides, mais des offres plus genereuses seraient un plus. Au final, Casinia Casino merite une exploration eblouissante pour les amateurs de casino en ligne ! Par ailleurs le site est rapide et envoutant, ajoute une touche de splendeur. Un atout cle les options de paris sportifs variees, qui renforce l’engagement.
VГ©rifier les infos|
J’ai une passion debordante pour Casinia Casino, c’est une plateforme qui brille d’une energie lumineuse. La diversite des titres est eblouissante, incluant des paris sportifs palpitants. Renforcant votre tresor initial. Le suivi est irreprochable, toujours pret a eclairer. Les paiements sont securises et fluides, parfois plus de promos regulieres ajouteraient de l’eclat. En bref, Casinia Casino est un joyau pour les joueurs pour les amateurs de casino en ligne ! Par ailleurs la plateforme scintille comme une etoile, intensifie l’eclat du jeu. Egalement remarquable les tournois reguliers pour la rivalite, garantit des transactions fiables.
Explorer le site|
J’ai un faible pour Casinia Casino, ca procure un plaisir aristocratique. La selection de jeux est royale, proposant des jeux de table elegants. Renforcant votre capital initial. Les agents repondent avec celerite, offrant des reponses claires. Le processus est simple et elegant, cependant plus de promos regulieres seraient un plus. En resume, Casinia Casino offre une experience memorable pour ceux qui aiment parier en crypto ! Notons aussi la navigation est simple et agreable, facilite une immersion totale. Un autre atout majeur les evenements communautaires engageants, assure des transactions fiables.
DГ©couvrir|
Je suis epate par Locowin Casino, ca procure un plaisir intense. Il y a une multitude de jeux excitants, comprenant des jeux compatibles avec les cryptos. Accompagne de tours gratuits sans wager. Le service est disponible 24/7, toujours pret a aider. Les retraits sont ultra-rapides, de temps en temps quelques tours gratuits en plus seraient cool. Au final, Locowin Casino est un incontournable pour les joueurs pour les passionnes de jeux modernes ! Notons aussi le design est moderne et fluide, donne envie de prolonger l’experience. Egalement appreciable les tournois reguliers pour la competition, offre des recompenses continues.
http://www.locowincasinoapp.fr|
I’m obsessed with Wazamba Casino, it’s an odyssey that echoes with intrigue. There’s a vast spectrum of options, incorporating live sessions for authentic interaction. Matching initial funds up to €500. Answering queries rapidly. Profits are delivered swiftly, occasionally further spins could be advantageous. To conclude, Wazamba Casino merits investigation for enthusiasts of betting ! In addition the environment loads efficiently, magnifying each episode’s appeal. Especially noteworthy acquiring items for advantages, granting sustained incentives.
https://wazambagr.com/|
hop event
I adore the rush of Astronaut Crash by 100HP Gaming, it mimics a high-altitude adrenaline surge. The mechanics are sleek and engaging, showcasing a multiplier that escalates dramatically. Free play mode to hone your edge. Forums buzzing with player tactics, upholding outcome transparency. Profits land in your account pronto, still weekly challenges could ramp up fun. Wrapping up, Astronaut Crash shines bright in 100HP’s portfolio for fast-action fans ! Bonus speeds are blisteringly quick, cranking the ascent hype. Highlight practice arena with live data, sparks a vibrant player network.
Astronaut Crash Game|
Ich habe einen totalen Hang zu SpinBetter Casino, es liefert ein Abenteuer voller Energie. Das Angebot an Spielen ist phanomenal, mit dynamischen Tischspielen. Die Agenten sind blitzschnell, immer parat zu assistieren. Die Auszahlungen sind ultraschnell, obwohl mehr abwechslungsreiche Boni waren super. In Kurze, SpinBetter Casino ist ein Muss fur alle Gamer fur Spieler auf der Suche nach Action ! Au?erdem die Plattform ist visuell ein Hit, verstarkt die Immersion. Zusatzlich zu beachten die Vielfalt an Zahlungsmethoden, die das Spielen noch angenehmer machen.
https://spinbettercasino.de/|
Je suis stupefait par Locowin Casino, ca fournit un plaisir intense. Il y a une profusion de jeux captivants, proposant des jeux de table immersifs. Associe a des tours gratuits sans wager. Le suivi est exemplaire, assurant un support premium. Les benefices arrivent sans latence, mais plus de promotions frequentes seraient un atout. En synthese, Locowin Casino garantit du divertissement constant pour ceux qui parient en crypto ! Ajoutons que la navigation est simple et engageante, ajoute un confort notable. Un autre avantage cle les evenements communautaires captivants, propose des recompenses permanentes.
Aller plus loin|
Je suis hypnotise par Casinia Casino, ca distille un plaisir majestueux. La diversite des titres est somptueuse, proposant des jeux de table raffines. L’offre de bienvenue est somptueuse. Les agents repondent avec une rapidite fulgurante, offrant des solutions limpides. Le processus est lisse et distingue, neanmoins plus de promos frequentes brilleraient davantage. En somme, Casinia Casino est une plateforme qui trone en maitre pour les aficionados de jeux modernes ! Ajoutons que la plateforme scintille comme un palais, ajoute une touche de splendeur. Un avantage notable les options de paris sportifs etendues, garantit des transactions fiables.
Ouvrir la page maintenant|
Je suis captive par Casinia Casino, ca transporte dans un palais enchanteur. Les options sont vastes comme un royaume, offrant des sessions live immersives. Plus un Bonus Crab pour demarrer. Le support client est imperial, garantissant un support de qualite. Les retraits sont rapides comme l’eclair, cependant des bonus plus varies seraient apprecies. En bref, Casinia Casino est une plateforme qui regne en maitre pour les fans de casino en ligne ! Notons aussi la navigation est simple et fluide, amplifie le plaisir de jouer. Egalement appreciable les evenements communautaires engageants, offre des recompenses continues.
AccГ©der au site|
J’ai un engouement sincere pour Locowin Casino, il delivre une experience unique. Il y a une profusion de jeux captivants, incluant des paris sportifs electrisants. Associe a des tours gratuits sans wager. Les agents reagissent avec promptitude, assurant un support premium. Les operations sont solides et veloces, de temps a autre plus de promotions frequentes seraient un atout. Globalement, Locowin Casino garantit du divertissement constant pour les adeptes de sensations intenses ! En outre la navigation est simple et engageante, intensifie le plaisir du jeu. Particulierement attractif les paiements securises en crypto, renforce le sens de communaute.
Voir tout de suite|
Thank you for the auspicious writeup. It in reality was a leisure account it. Glance complicated to far brought agreeable from you! However, how can we communicate?
kraken маркетплейс
I’m addicted to Wazamba Casino, it unleashes a special vibe. The game lineup is extraordinary, including live casino for real-time action. Kickstarting your adventure. Support team is exceptional. Rewards reach you fast, although additional incentives would shine. In summary, Wazamba Casino delivers unmatched fun for betting devotees ! Additionally the visuals are captivating and immersive, motivating return visits. Noteworthy is secure crypto payment methods, offering tailored benefits.
wazambagr.com|
Ich habe einen totalen Hang zu SpinBetter Casino, es fuhlt sich an wie ein Strudel aus Freude. Es gibt eine unglaubliche Auswahl an Spielen, mit aufregenden Sportwetten. Der Kundenservice ist ausgezeichnet, immer parat zu assistieren. Der Ablauf ist unkompliziert, gelegentlich mehr abwechslungsreiche Boni waren super. In Kurze, SpinBetter Casino ist absolut empfehlenswert fur Casino-Liebhaber ! Zusatzlich die Navigation ist kinderleicht, was jede Session noch besser macht. Zusatzlich zu beachten die schnellen Einzahlungen, die den Spa? verlangern.
https://spinbettercasino.de/|
J’aime l’atmosphere unique de Locowin Casino, ca immerse dans un monde fascinant. Le catalogue est abondant et multifacette, proposant des jeux de table immersifs. Le bonus d’accueil est seduisant. Le service est disponible 24/7, avec une aide precise et rapide. Le processus est simple et reibungslos, parfois des offres plus genereuses ajouteraient de l’attrait. Dans l’ensemble, Locowin Casino offre une experience inoubliable pour ceux qui aiment parier en crypto ! De plus la navigation est simple et plaisante, amplifie le plaisir de jouer. Particulierement interessant les evenements communautaires engageants, assure des transactions fiables.
Trouver le meilleur|
J’ai un engouement sincere pour Locowin Casino, on detecte une vibe folle. Le repertoire est opulent et multifacette, comprenant des jeux adaptes aux cryptos. Doublement des depots jusqu’a 1850 €. Les agents reagissent avec promptitude, accessible a tout instant. Les benefices arrivent sans latence, bien que des offres plus liberales ajouteraient de la valeur. Pour synthetiser, Locowin Casino merite une exploration approfondie pour ceux qui parient en crypto ! Ajoutons que la plateforme est esthetiquement remarquable, stimule le desir de revenir. Un autre avantage cle les evenements communautaires captivants, propose des recompenses permanentes.
Essayer en ligne|
J’ai un veritable engouement pour Locowin Casino, ca fournit un plaisir intense. Les alternatives sont incroyablement etendues, comprenant des jeux adaptes aux cryptos. Pour un lancement puissant. L’equipe d’assistance est remarquable, proposant des reponses limpides. Les operations sont solides et veloces, par moments des incitations additionnelles seraient un benefice. Pour synthetiser, Locowin Casino est une plateforme qui excelle pour ceux qui parient en crypto ! En outre le site est veloce et seduisant, intensifie le plaisir du jeu. Un autre avantage cle les paiements securises en crypto, offre des privileges sur mesure.
Explorer le site|
I’m hooked on Wazamba Casino, it provides a thrilling journey. The selection of games is phenomenal, including slots with tribal themes. Building your bankroll effectively. Available 24/7 for any queries. The system is user-friendly, nevertheless additional bonuses might be welcome. All in all, Wazamba Casino is essential for gamers for adrenaline seekers ! Also navigation is effortless, deepens immersion in the game. One more highlight crypto-friendly banking options, providing personalized perks.
https://wazambagr.com/|
Tenho uma paixao intensa por BETesporte Casino, transporta para um mundo de apostas vibrante. O catalogo e rico e diversificado, com sessoes ao vivo imersivas. Eleva a experiencia de jogo. O acompanhamento e impecavel, sempre pronto para o jogo. As transacoes sao confiaveis, no entanto ofertas mais generosas dariam um toque especial. No fim, BETesporte Casino vale uma aposta certa para fas de cassino online ! Tambem o site e veloz e envolvente, tornando cada sessao mais competitiva. Igualmente impressionante o programa VIP com niveis exclusivos, fortalece o senso de comunidade.
Ver agora|
J’adore l’ambiance de Locowin Casino, il offre une experience unique. Il y a une multitude de jeux excitants, avec des slots au design innovant. Doublement des depots jusqu’a 1850 €. Le service est disponible 24/7, joignable a toute heure. Le processus est simple et efficace, cependant quelques tours gratuits en plus seraient cool. En resume, Locowin Casino est une plateforme qui dechire pour les fans de casino en ligne ! Cerise sur le gateau le site est rapide et attrayant, ajoute une touche de confort. Egalement appreciable les options de paris sportifs variees, qui booste l’engagement.
Voir maintenant|
Je suis surpris par Locowin Casino, c’est une plateforme qui explose d’energie. La diversite des titres est epoustouflante, incluant des paris sportifs electrisants. Doublement des depots jusqu’a 1850 €. L’aide est performante et experte, proposant des reponses limpides. Les benefices arrivent sans latence, de temps a autre quelques tours gratuits supplementaires seraient apprecies. Globalement, Locowin Casino garantit du divertissement constant pour les joueurs a la recherche d’aventure ! En outre l’interface est intuitive et raffinee, facilite une immersion complete. Un plus significatif les paiements securises en crypto, renforce le sens de communaute.
Cliquer pour les infos|
J’ai un engouement pour Locowin Casino, ca fournit un plaisir intense. Le repertoire est opulent et multifacette, comprenant des jeux adaptes aux cryptos. Renforcant l’experience de depart. Le suivi est exemplaire, accessible a tout instant. Les operations sont solides et veloces, bien que plus de promotions frequentes seraient un atout. En fin de compte, Locowin Casino merite une exploration approfondie pour les joueurs a la recherche d’aventure ! De surcroit l’interface est intuitive et raffinee, facilite une immersion complete. A souligner aussi les paiements securises en crypto, propose des recompenses permanentes.
Aller sur le site|
Estou alucinado com BR4Bet Casino, vibra como um farol em alto-mar. A colecao e um facho de diversao. com caca-niqueis que brilham como holofotes. Os agentes voam como claroes. com solucoes precisas e instantaneas. Os saques voam como um facho de luz. ocasionalmente mais bonus seriam um diferencial reluzente. Para encurtar, BR4Bet Casino e uma fogueira de adrenalina para os exploradores de jogos online! E mais a navegacao e facil como um facho de luz. tornando cada sessao ainda mais brilhante.
br4bet quantos saques por dia|
Je suis fou de Simsinos Casino, ca degage une ambiance de jeu aussi coloree qu’un studio d’animation. Le repertoire du casino est un studio de divertissement. avec des machines a sous de casino modernes et rebondissantes. offre un soutien qui crayonne tout. proposant un appui qui enchante. Les gains du casino arrivent a une vitesse cartoon. parfois plus de tours gratuits au casino ce serait cartoon. En conclusion, Simsinos Casino est un joyau pour les fans de casino pour les fans de symphonies colorees! Bonus offre un orchestre de couleurs rebondissantes. ce qui rend chaque session de casino encore plus animee.
simsinos casino erfahrungen|
Tenho uma paixao vibrante por BETesporte Casino, e uma plataforma que vibra como um estadio lotado. O catalogo e vibrante e diversificado, com slots modernos e tematicos. Eleva a experiencia de jogo. Os agentes respondem com rapidez, oferecendo respostas claras. As transacoes sao confiaveis, de vez em quando promocoes mais frequentes seriam um plus. Em sintese, BETesporte Casino vale uma aposta certa para amantes de apostas esportivas ! Tambem a plataforma e visualmente impactante, adiciona um toque de estrategia. Outro destaque os torneios regulares para rivalidade, assegura transacoes confiaveis.
Ir para a web|
Fiquei impressionado com PlayPIX Casino, leva a um universo de pura adrenalina. A variedade de titulos e estonteante, suportando jogos compativeis com criptomoedas. Eleva a experiencia de jogo. O servico esta disponivel 24/7, sempre pronto para resolver. Os pagamentos sao seguros e fluidos, no entanto recompensas extras seriam eletrizantes. No geral, PlayPIX Casino e uma plataforma que brilha para quem aposta com cripto ! Acrescentando que a plataforma e visualmente espetacular, tornando cada sessao mais vibrante. Notavel tambem os pagamentos seguros em cripto, oferece recompensas continuas.
Saiba mais|
Je suis accro a Locowin Casino, ca transporte dans un monde captivant. La selection de jeux est phenomenale, proposant des jeux de table immersifs. Accompagne de tours gratuits sans wager. Le service est disponible 24/7, joignable a toute heure. Le processus est simple et efficace, neanmoins plus de promos regulieres seraient top. Au final, Locowin Casino vaut largement le detour pour ceux qui aiment parier en crypto ! De plus le design est moderne et fluide, amplifie le plaisir de jouer. Egalement appreciable les options de paris sportifs variees, qui booste l’engagement.
Explorer le contenu|
Je suis emerveille par Casinia Casino, on ressent une aura radieuse. Le repertoire est riche et multifacette, incluant des paris sportifs palpitants. 100% jusqu’a 500 € + 200 tours gratuits. Le suivi est irreprochable, avec une aide claire et veloce. Les gains arrivent a la vitesse de la lumiere, mais des recompenses additionnelles seraient scintillantes. En somme, Casinia Casino merite une exploration eblouissante pour les aficionados de jeux modernes ! En bonus la plateforme scintille comme une etoile, facilite une immersion totale. Particulierement captivant les paiements securises en crypto, propose des recompenses sur mesure.
Aller lГ -bas|
Je suis accro a Locowin Casino, ca procure un plaisir intense. Le catalogue est riche et diversifie, incluant des paris sportifs palpitants. Pour un demarrage en force. Les agents repondent avec rapidite, toujours pret a aider. Les retraits sont ultra-rapides, de temps en temps des recompenses supplementaires seraient un atout. Au final, Locowin Casino est une plateforme qui dechire pour les amateurs de sensations fortes ! Notons aussi la navigation est simple et agreable, ajoute une touche de confort. Egalement appreciable les paiements securises en crypto, qui booste l’engagement.
Explorer tout le site|
Me encantei pelo fulgor de Verabet Casino, pulsa com uma forca de cassino digna de um xama. O catalogo de jogos e um altar de prazeres. com slots tematicos de cerimonias antigas. O suporte e um fulgor reluzente. com ajuda que ilumina como uma pira. Os saques queimam como brasas. mesmo assim mais giros gratis seriam incendiarios. Para encurtar, Verabet Casino e uma pira de adrenalina para os cacadores de vitorias incendiarias! Alem disso o design e um espetaculo visual flamejante. tornando cada sessao ainda mais flamejante.
bet/vera|
Me encantei pelo fulgor de Fogo777 Casino, oferece uma aventura que reluz como brasas vivas. Tem uma enxurrada de jogos de cassino irados. oferecendo lives que explodem como uma pira. Os agentes sao rapidos como uma faisca. respondendo veloz como uma faisca. As transacoes sao faceis como um fulgor. as vezes queria promocoes que explodem como labaredas. Para encurtar, Fogo777 Casino vale explorar esse cassino ja para os viciados em emocoes de cassino! De bonus a plataforma reluz com um visual ritualistico. criando uma experiencia de cassino incendiaria.
www fogo777|
Sou totalmente viciado em BETesporte Casino, e uma plataforma que vibra como um estadio em dia de final. A selecao de jogos e fenomenal, oferecendo jogos de mesa dinamicos. Eleva a experiencia de jogo. O suporte ao cliente e excepcional, acessivel a qualquer hora. O processo e simples e direto, embora ofertas mais generosas seriam bem-vindas. No geral, BETesporte Casino vale uma aposta certa para amantes de apostas esportivas ! Alem disso a plataforma e visualmente impactante, tornando cada sessao mais competitiva. Notavel tambem o programa VIP com niveis exclusivos, que impulsiona o engajamento.
Saber mais|
Tenho um entusiasmo vibrante por PlayPIX Casino, e uma plataforma que transborda vitalidade. A selecao de jogos e fenomenal, com sessoes ao vivo cheias de energia. Com uma oferta inicial para impulsionar. O suporte ao cliente e excepcional, oferecendo respostas claras. Os saques sao rapidos como um raio, as vezes promocoes mais frequentes dariam um toque extra. Para finalizar, PlayPIX Casino vale uma visita epica para fas de cassino online ! Tambem o site e rapido e cativante, instiga a prolongar a experiencia. Igualmente impressionante os torneios regulares para competicao, oferece recompensas continuas.
Ver o site|
Hi there! Do you use Twitter? I’d like to follow you if that would be okay. I’m absolutely enjoying your blog and look forward to new updates.
банзай казино
Hi there to every , for the reason that I am really keen of reading this webpage’s post to be updated regularly. It consists of good information.
онлайн казино Dragon Money
I got this web page from my friend who shared with me about this site and at the moment this time I am visiting this web page and reading very informative content at this place.
https://artwhite.ru/
Superb post but I was wondering if you could write a litte more on this topic? I’d be very grateful if you could elaborate a little bit further. Bless you!
официальный сайт lee bet casino
Why people still use to read news papers when in this technological globe all is presented on web?
сайт битц казино
Sou viciado no brilho de BR4Bet Casino, oferece uma aventura que brilha como um candelabro em chamas. As escolhas sao vibrantes como um farol. com slots tematicos de aventuras radiantes. Os agentes voam como claroes. garantindo suporte direto e sem escuridao. Os saques sao velozes como um clarao. porem as ofertas podiam ser mais generosas. Resumindo, BR4Bet Casino e um clarao de emocoes para os faroleiros do cassino! E mais o layout e vibrante como uma tocha. tornando cada sessao ainda mais brilhante.
suporte br4bet|
Estou pirando com OshCasino, e um cassino online que detona como um vulcao. Os titulos do cassino sao um espetaculo vulcanico, oferecendo sessoes de cassino ao vivo que sao uma chama. O suporte do cassino ta sempre na ativa 24/7, dando solucoes na hora e com precisao. Os saques no cassino sao velozes como uma erupcao, porem mais giros gratis no cassino seria uma loucura. No geral, OshCasino oferece uma experiencia de cassino que e puro fogo para os aventureiros do cassino! Alem disso a interface do cassino e fluida e cheia de energia ardente, faz voce querer voltar pro cassino como uma erupcao.
osh code bonus|
Ich liebe die Atmosphare von NV Casino, es ist ein Abenteuer, das pulsiert wie ein Herzschlag. Der Katalog ist reich und vielfaltig, mit Spielen, die perfekt fur Kryptos geeignet sind. Der Support ist von herausragender Qualitat, mit praziser Unterstutzung. Die Transaktionen sind zuverlassig, dennoch regelma?igere Promos waren super. Insgesamt, NV Casino bietet unvergesslichen Spa? fur Casino-Enthusiasten ! Hinzu die Oberflache ist intuitiv und stylish, was jede Session noch spannender macht.
playnvcasino.de|
Fiquei impressionado com BETesporte Casino, e uma plataforma que pulsa com emocao atletica. Ha uma multidao de jogos emocionantes, com sessoes ao vivo imersivas. Eleva a experiencia de jogo. O servico esta disponivel 24/7, acessivel a qualquer hora. As transacoes sao confiaveis, embora ofertas mais generosas dariam um toque especial. No geral, BETesporte Casino oferece uma experiencia inesquecivel para entusiastas de jogos modernos ! Adicionalmente o site e veloz e envolvente, tornando cada sessao mais competitiva. Notavel tambem as opcoes variadas de apostas esportivas, que impulsiona o engajamento.
Explorar o site|
hip
Ich finde absolut wild Lowen Play Casino, es bietet ein Casino-Abenteuer, das wie ein Urwald leuchtet. Die Casino-Optionen sind vielfaltig und kraftvoll, mit einzigartigen Casino-Slotmaschinen. Der Casino-Kundenservice ist wie ein Leitlowe, ist per Chat oder E-Mail erreichbar. Der Casino-Prozess ist klar und ohne Fallen, dennoch mehr Freispiele im Casino waren ein wilder Triumph. Insgesamt ist Lowen Play Casino ein Muss fur Casino-Fans fur Fans moderner Casino-Slots! Extra die Casino-Seite ist ein grafisches Meisterwerk, Lust macht, immer wieder ins Casino zuruckzukehren.
löwen play lohne|
Sou louco pelo role de PagolBet Casino, parece uma tempestade de diversao. As opcoes de jogo no cassino sao ricas e vibrantes, com jogos de cassino perfeitos pra criptomoedas. O servico do cassino e confiavel e brabo, dando solucoes na hora e com precisao. Os saques no cassino sao velozes como um trovao, mesmo assim mais giros gratis no cassino seria uma loucura. No fim das contas, PagolBet Casino e o point perfeito pros fas de cassino para os viciados em emocoes de cassino! E mais o design do cassino e uma explosao visual vibrante, torna o cassino uma curticao total.
pagolbet..com|
Ich bin komplett hin und weg von SpinBetter Casino, es fuhlt sich an wie ein Strudel aus Freude. Es wartet eine Fulle spannender Optionen, mit innovativen Slots und fesselnden Designs. Der Service ist von hoher Qualitat, garantiert top Hilfe. Die Gewinne kommen prompt, dennoch regelma?igere Aktionen waren toll. Zusammengefasst, SpinBetter Casino ist ein Muss fur alle Gamer fur Online-Wetten-Fans ! Au?erdem die Plattform ist visuell ein Hit, verstarkt die Immersion. Besonders toll die schnellen Einzahlungen, die Flexibilitat bieten.
https://spinbettercasino.de/|
Ich bin verblufft von NV Casino, es ist ein Abenteuer, das pulsiert wie ein Herzschlag. Das Angebot an Spielen ist phanomenal, mit Spielen, die perfekt fur Kryptos geeignet sind. Der Service ist rund um die Uhr verfugbar, erreichbar zu jeder Stunde. Der Prozess ist unkompliziert, manchmal regelma?igere Promos waren super. Zum Abschluss, NV Casino bietet unvergesslichen Spa? fur Krypto-Liebhaber ! Daruber hinaus die Navigation ist kinderleicht, verstarkt die Immersion.
playnvcasino.de|
Amo a energia de BETesporte Casino, oferece um prazer esportivo intenso. A variedade de titulos e impressionante, com slots modernos e tematicos. O bonus de boas-vindas e empolgante. O servico esta disponivel 24/7, sempre pronto para entrar em campo. O processo e simples e direto, contudo bonus mais variados seriam um golaco. No fim, BETesporte Casino e uma plataforma que domina o campo para jogadores em busca de emocao ! Tambem a navegacao e intuitiva e rapida, facilita uma imersao total. Muito atrativo os eventos comunitarios envolventes, oferece recompensas continuas.
Explorar agora|
Hey this is kind of of off topic but I was wondering if blogs use WYSIWYG editors or if you have to manually code with HTML. I’m starting a blog soon but have no coding expertise so I wanted to get guidance from someone with experience. Any help would be enormously appreciated!
официальный сайт lee bet
Hi colleagues, how is everything, and what you wish for to say regarding this article, in my view its actually awesome for me.
казино риобет
Sou viciado no glamour de Richville Casino, e um cassino online que reluz como um palacio dourado. Tem uma cascata de jogos de cassino fascinantes, com jogos de cassino perfeitos para criptomoedas. A equipe do cassino oferece um atendimento digno de realeza, acessivel por chat ou e-mail. Os ganhos do cassino chegam com a velocidade de um jato particular, de vez em quando mais bonus regulares no cassino seria chique. Na real, Richville Casino e uma joia rara para os fas de cassino para os nobres do cassino! E mais a plataforma do cassino reluz com um estilo digno de um palacio, eleva a imersao no cassino ao apice.
richville park|
Sou louco pelo batuque de RioPlay Casino, da uma energia de cassino que e puro axe. As opcoes de jogo no cassino sao ricas e dancantes, incluindo jogos de mesa de cassino com gingado. Os agentes do cassino sao rapidos como um passista, dando solucoes na hora e com precisao. Os ganhos do cassino chegam voando como um mestre-sala, porem queria mais promocoes de cassino que botam pra quebrar. No geral, RioPlay Casino garante uma diversao de cassino que e uma folia total para os viciados em emocoes de cassino! Alem disso a interface do cassino e fluida e vibrante como uma escola de samba, o que torna cada sessao de cassino ainda mais animada.
rioplay games apk|
Estou completamente encantado por PlayPIX Casino, proporciona uma aventura eletrizante. A variedade de titulos e deslumbrante, oferecendo jogos de mesa imersivos. Com um bonus extra para comecar. O acompanhamento e impecavel, com suporte preciso e rapido. As transacoes sao confiaveis, as vezes mais promocoes regulares seriam otimas. No geral, PlayPIX Casino e indispensavel para jogadores para fas de cassino online ! Acrescentando que o site e rapido e atraente, facilita uma imersao total. Igualmente impressionante o programa VIP com 5 niveis exclusivos, assegura transacoes confiaveis.
Ver agora|
Amo a atmosfera de BETesporte Casino, transporta para um mundo de apostas vibrante. As opcoes sao vastas como um campeonato, com sessoes ao vivo imersivas. Eleva a experiencia de jogo. Os agentes respondem com velocidade, oferecendo respostas claras. Os ganhos chegam sem demora, no entanto mais apostas gratis seriam incriveis. No fim, BETesporte Casino garante diversao a cada rodada para fas de cassino online ! Adicionalmente a plataforma e visualmente impactante, aumenta o prazer de apostar. Muito atrativo os eventos comunitarios envolventes, oferece recompensas continuas.
Ver o site|
Курс по литературе ЕГЭ https://courses-ege.ru
social event
Acho simplesmente fenomenal Brazino Casino, parece um abismo de adrenalina subaquatica. A colecao e uma onda de entretenimento. com caca-niqueis modernos que nadam como peixes tropicais. O suporte e um farol subaquatico. assegurando apoio sem turbulencia aquatica. Os ganhos chegam rapido como uma corrente. mas mais recompensas fariam o coracao nadar. Ao final, Brazino Casino e o point perfeito pros fas de cassino para os mergulhadores do cassino! Como extra o design e um espetaculo visual aquatico. fazendo o cassino reluzir como um recife.
brazino777 cГіdigo promocional 2022|
Estou completamente vidrado por SambaSlots Casino, e um cassino online que samba como um desfile de carnaval. A selecao de titulos do cassino e um desfile de cores, com slots de cassino tematicos de festa. O servico do cassino e confiavel e cheio de gingado, com uma ajuda que e puro axe. Os ganhos do cassino chegam voando como uma rainha de bateria, mesmo assim mais recompensas no cassino seriam um diferencial insano. Na real, SambaSlots Casino e o point perfeito pros fas de cassino para os apaixonados por slots modernos de cassino! E mais a interface do cassino e fluida e vibrante como uma escola de samba, eleva a imersao no cassino ao ritmo do pandeiro.
casino la sambaslots mon compte|
Ich liebe den Wahnsinn von JackpotPiraten Casino, es fuhlt sich an wie eine wilde Piratenjagd. Der Katalog des Casinos ist ein Schatztruhe voller Spa?, mit Casino-Spielen, die fur Kryptowahrungen optimiert sind. Der Casino-Support ist rund um die Uhr verfugbar, sorgt fur sofortigen Casino-Support, der beeindruckt. Casino-Transaktionen sind simpel wie ein Kompass, ab und zu mehr Casino-Belohnungen waren ein echter Schatz. Alles in allem ist JackpotPiraten Casino ein Casino, das man nicht verpassen darf fur Fans von Online-Casinos! Ubrigens die Casino-Seite ist ein grafisches Meisterwerk, Lust macht, immer wieder ins Casino zuruckzukehren.
jackpotpiraten bonus code ohne einzahlung|
Je suis enthousiaste a propos de 7BitCasino, c’est une veritable plongee dans un univers palpitant. La gamme de jeux est tout simplement impressionnante, offrant des sessions de casino en direct immersives. Les agents sont disponibles 24/7, offrant des reponses rapides et precises. Les retraits sont ultra-rapides, cependant j’aimerais plus d’offres promotionnelles, comme des offres de cashback plus avantageuses. Globalement, 7BitCasino ne decoit jamais pour les adeptes de sensations fortes ! Ajoutons que le site est concu avec style et modernite, ce qui intensifie le plaisir de jouer.
7bitcasino free spins code|
Sou viciado em PlayPIX Casino, proporciona uma aventura pulsante. A selecao de jogos e fenomenal, suportando jogos compativeis com criptomoedas. Com uma oferta inicial para impulsionar. Os agentes respondem com agilidade, acessivel a qualquer momento. Os ganhos chegam sem atraso, de vez em quando promocoes mais frequentes dariam um toque extra. Para finalizar, PlayPIX Casino vale uma visita epica para amantes de emocoes fortes ! Tambem a plataforma e visualmente espetacular, aumenta o prazer de jogar. Um diferencial significativo as opcoes variadas de apostas esportivas, fortalece o senso de comunidade.
Ler os detalhes|
Amo a energia de BETesporte Casino, oferece um prazer esportivo intenso. Ha uma explosao de jogos emocionantes, incluindo apostas esportivas que aceleram o coracao. O bonus de boas-vindas e empolgante. O acompanhamento e impecavel, sempre pronto para entrar em campo. Os ganhos chegam sem atraso, no entanto mais apostas gratis seriam incriveis. Resumindo, BETesporte Casino e uma plataforma que domina o campo para fas de cassino online ! Vale destacar a plataforma e visualmente impactante, adiciona um toque de estrategia. Outro destaque os pagamentos seguros em cripto, assegura transacoes confiaveis.
Consultar os detalhes|
telecharger 1xbet cameroun 1xbet cameroun apk
Ich bin total begeistert von PlayJango Casino, es bietet ein Casino-Abenteuer, das wie ein Regenbogen funkelt. Die Auswahl im Casino ist ein echtes Spektakel, mit modernen Casino-Slots, die einen in ihren Bann ziehen. Der Casino-Service ist zuverlassig und strahlend, ist per Chat oder E-Mail erreichbar. Casino-Transaktionen sind simpel wie ein Sonnenstrahl, trotzdem mehr regelma?ige Casino-Boni waren ein Knaller. Alles in allem ist PlayJango Casino ein Casino, das man nicht verpassen darf fur Abenteurer im Casino! Zusatzlich das Casino-Design ist ein optisches Spektakel, das Casino-Erlebnis total elektrisiert.
playjango online casino|
Adoro o brilho estelar de SpeiCasino, oferece uma aventura de cassino que orbita como um satelite. O catalogo de jogos do cassino e uma constelacao de prazeres, incluindo jogos de mesa de cassino com um toque cosmico. O suporte do cassino ta sempre na ativa 24/7, garantindo suporte de cassino direto e sem buracos negros. Os ganhos do cassino chegam voando como um meteoro, as vezes mais bonus regulares no cassino seria intergalactico. Resumindo, SpeiCasino vale demais explorar esse cassino para os viciados em emocoes de cassino! E mais o design do cassino e um espetaculo visual intergalactico, eleva a imersao no cassino a um nivel cosmico.
spei apk|
Sou viciado no reverb de JonBet Casino, tem uma energia de jogo tao pulsante quanto um eco em caverna. Os jogos formam uma ressonancia de diversao. com caca-niqueis que vibram como harpas. O servico e confiavel como uma camara. com ajuda que ressoa como um sino. Os pagamentos sao seguros e fluidos. ocasionalmente as ofertas podiam ser mais generosas. Em resumo, JonBet Casino promete uma diversao que e uma onda sonora para os exploradores de jogos online! Adicionalmente a plataforma vibra com um visual ressonante. adicionando um toque de eco ao cassino.
jonbet 40 rodadas gratis|
Sou louco pela energia de BacanaPlay Casino, da uma energia de cassino que e pura purpurina. As opcoes de jogo no cassino sao ricas e cheias de gingado, oferecendo sessoes de cassino ao vivo que sambam com energia. O atendimento ao cliente do cassino e uma rainha de bateria, com uma ajuda que brilha como serpentinas. Os saques no cassino sao velozes como um carro alegorico, mesmo assim as ofertas do cassino podiam ser mais generosas. Na real, BacanaPlay Casino oferece uma experiencia de cassino que e puro axe para quem curte apostar com gingado no cassino! Alem disso o design do cassino e um desfile visual vibrante, faz voce querer voltar ao cassino como num desfile sem fim.
bacanaplay app baixar|
Tenho uma paixao ardente por BETesporte Casino, oferece um prazer esportivo inigualavel. Ha uma explosao de jogos emocionantes, suportando jogos compativeis com criptomoedas. Fortalece seu saldo inicial. A assistencia e eficiente e amigavel, sempre pronto para entrar em campo. As transacoes sao confiaveis, de vez em quando ofertas mais generosas seriam bem-vindas. Em sintese, BETesporte Casino garante diversao constante para quem usa cripto para jogar ! Adicionalmente a interface e fluida e energetica, facilita uma imersao total. Um diferencial importante os pagamentos seguros em cripto, assegura transacoes confiaveis.
Aprender os detalhes|
Наша платформа https://probilets работает круглосуточно и не знает слова «перерыв». Бронировать и планировать можно где угодно: в поезде, на даче, в кафе или лежа на диване. Хотите купить билет, пока идёте по супермаркету? Просто достаньте телефон и оформите поездку. Нужно скорректировать планы, отменить или перенести билет? Это тоже можно сделать онлайн, без звонков и визитов.
Ich bin vollig begeistert von Richard Casino, es pulsiert mit einer luxuriosen Casino-Energie. Es gibt eine Flut an fesselnden Casino-Titeln, mit modernen Casino-Slots, die einen verzaubern. Die Casino-Mitarbeiter sind schnell wie ein kaiserlicher Bote, ist per Chat oder E-Mail erreichbar. Casino-Zahlungen sind sicher und reibungslos, manchmal mehr Casino-Belohnungen waren ein koniglicher Gewinn. Insgesamt ist Richard Casino eine Casino-Erfahrung, die wie ein Kronungsjuwel glanzt fur Fans moderner Casino-Slots! Und au?erdem die Casino-Plattform hat einen Look, der wie ein Kronungsmantel glanzt, den Spielspa? im Casino auf ein konigliches Niveau hebt.
richard casino 5|
Acho simplesmente magico SpellWin Casino, parece um portal mistico cheio de adrenalina. Tem uma enxurrada de jogos de cassino fascinantes, com slots de cassino tematicos de fantasia. O servico do cassino e confiavel e encantador, respondendo mais rapido que um estalo magico. O processo do cassino e limpo e sem truques, mesmo assim mais bonus regulares no cassino seria brabo. No geral, SpellWin Casino garante uma diversao de cassino que e magica para os apaixonados por slots modernos de cassino! Alem disso a navegacao do cassino e facil como um passe de magica, adiciona um toque de encantamento ao cassino.
george spellwin|
Adoro o brilho de BetorSpin Casino, tem uma vibe de jogo tao vibrante quanto uma supernova dancante. A gama do cassino e simplesmente uma constelacao de prazeres, com slots de cassino tematicos de espaco sideral. A equipe do cassino entrega um atendimento que e puro cometa, dando solucoes na hora e com precisao. Os pagamentos do cassino sao lisos e blindados, mas mais giros gratis no cassino seria uma loucura estelar. Na real, BetorSpin Casino e um cassino online que e uma galaxia de diversao para os apaixonados por slots modernos de cassino! Vale dizer tambem a interface do cassino e fluida e reluz como uma constelacao, eleva a imersao no cassino a um nivel cosmico.
cupom betorspin|
Estou totalmente fascinado por BETesporte Casino, me leva a um universo de apostas vibrante. O catalogo e vibrante e multifacetado, com slots modernos e tematicos. Eleva a experiencia de jogo. A assistencia e eficiente e amigavel, com suporte preciso e confiavel. O processo e simples e direto, de vez em quando bonus mais variados seriam um golaco. No fim, BETesporte Casino oferece uma experiencia inesquecivel para entusiastas de jogos modernos ! Vale destacar a plataforma e visualmente impactante, aumenta o prazer de apostar. Outro destaque as opcoes variadas de apostas esportivas, assegura transacoes confiaveis.
Descobrir mais|
Estou completamente encantado por PlayPIX Casino, sinto um ritmo alucinante. A selecao de jogos e fenomenal, com sessoes ao vivo dinamicas. Fortalece seu saldo inicial. O servico esta disponivel 24/7, oferecendo respostas claras. O processo e simples e elegante, de vez em quando ofertas mais generosas dariam um toque especial. No final, PlayPIX Casino garante diversao a cada momento para fas de cassino online ! Acrescentando que o design e moderno e vibrante, facilita uma imersao total. Igualmente impressionante as opcoes variadas de apostas esportivas, fortalece o senso de comunidade.
Ver mais|
Adoro o impacto de SupremaBet Casino, da uma energia de cassino que e puro dominio. Tem uma tempestade de jogos de cassino irados, com caca-niqueis de cassino modernos e eletrizantes. O servico do cassino e confiavel e majestoso, acessivel por chat ou e-mail. Os ganhos do cassino chegam voando como um falcao real, mesmo assim as ofertas do cassino podiam ser mais generosas. Em resumo, SupremaBet Casino oferece uma experiencia de cassino que e puro cetro para os soberanos do cassino! Alem disso a plataforma do cassino brilha com um visual que e puro trono, torna a experiencia de cassino um reinado de prazer.
supremabet-pb|
Achou totalmente epico DiceBet Casino, da uma energia de cassino que e fora da curva. As opcoes de jogo no cassino sao ricas e vibrantes, oferecendo sessoes de cassino ao vivo que sao uma bomba. Os agentes do cassino sao rapidos como um foguete, dando solucoes claras na hora. Os pagamentos do cassino sao lisos e seguros, porem queria mais promocoes de cassino que mandam ver. No fim das contas, DiceBet Casino e um cassino online que e uma pedrada para quem curte apostar com estilo no cassino! De bonus o design do cassino e uma explosao visual, o que deixa cada sessao de cassino ainda mais animal.
dicebet reclame aqui|
Amo a energia de PlayPIX Casino, transmite uma energia vibrante. As opcoes sao amplas como um festival, oferecendo jogos de mesa envolventes. 100% ate €500 + rodadas gratis. O servico esta disponivel 24/7, oferecendo respostas claras. Os saques sao rapidos como um raio, embora mais rodadas gratis seriam um diferencial. Resumindo, PlayPIX Casino garante diversao constante para jogadores em busca de adrenalina ! Vale destacar a navegacao e intuitiva e envolvente, facilita uma imersao total. Notavel tambem as opcoes variadas de apostas esportivas, oferece recompensas continuas.
Consultar os detalhes|
Ich bin total begeistert von Trickz Casino, es bietet ein Casino-Abenteuer, das wie eine Illusion verblufft. Der Katalog des Casinos ist ein magischer Zirkus voller Action, mit modernen Casino-Slots, die einen in Bann ziehen. Der Casino-Support ist rund um die Uhr verfugbar, ist per Chat oder E-Mail erreichbar. Der Casino-Prozess ist klar und ohne Tauschung, trotzdem mehr Freispiele im Casino waren ein magischer Volltreffer. Kurz gesagt ist Trickz Casino ein Casino mit einem Spielspa?, der wie eine Illusion verblufft fur die, die mit Stil im Casino wetten! Nebenbei die Casino-Oberflache ist flussig und funkelt wie ein Zauberstab, den Spielspa? im Casino auf ein magisches Niveau hebt.
trickz casino logga in|
Je suis totalement electrifie par Donbet Casino, c’est une deflagration de fun absolu. La gamme est une eruption de delices, incluant des jeux de table d’une energie debordante. Les agents repondent a la vitesse d’un meteore, avec une aide aussi fluide qu’un courant. Les gains arrivent a une vitesse supersonique, mais les offres pourraient etre plus volcaniques. Au final, Donbet Casino promet une aventure incandescente pour les amateurs de sensations explosives ! A noter la navigation est intuitive comme un eclair, donne envie de replonger dans la tempete.
donbet code promo|
Ich finde es unglaublich toll Billy Billion Casino, es bietet ein Eintauchen in eine pulsierende Spielwelt. Der Katalog ist unglaublich umfangreich, mit modernen Slots wie Gates of Olympus und Book of Dead. Das Team bietet schnelle und effektive Unterstutzung, ist 24/7 erreichbar. Gewinne kommen in Rekordzeit an, gelegentlich ich mir mehr regelma?ige Aktionen wunschen wurde. Alles in allem ist Billy Billion Casino enttauscht nie fur Leidenschaftliche Gamer! Erganzend die Seite ist mit Stil und Benutzerfreundlichkeit gestaltet, die Immersion verstarkt.
billy billion casino|
I loved as much as you’ll receive carried out right here. The sketch is attractive, your authored material stylish. nonetheless, you command get bought an shakiness over that you wish be delivering the following. unwell unquestionably come further formerly again since exactly the same nearly a lot often inside case you shield this hike.
https://staffinggoals.com
Je suis fou de VBet Casino, on dirait une eruption de plaisirs incandescents. Les options de jeu au casino sont riches et enflammees, offrant des sessions de casino en direct qui crepitent comme des flammes. L’assistance du casino est chaleureuse et irreprochable, assurant un support de casino immediat et incandescent. Les transactions du casino sont simples comme une braise, mais des recompenses de casino supplementaires feraient exploser. Au final, VBet Casino c’est un casino a explorer sans tarder pour ceux qui cherchent l’adrenaline enflammee du casino ! Par ailleurs la plateforme du casino brille par son style volcanique, donne envie de replonger dans le casino sans fin.
vbet огляди|
Attractive section of content. I simply stumbled upon your web site and in accession capital to say that I get actually loved account your blog posts. Anyway I will be subscribing to your feeds and even I achievement you get right of entry to consistently fast.
https://easystaffingmd.com/
Ich bin total begeistert von Lowen Play Casino, es ist ein Online-Casino, das wie ein Lowe brullt. Der Katalog des Casinos ist ein Dschungel voller Nervenkitzel, mit Casino-Spielen, die fur Kryptowahrungen optimiert sind. Der Casino-Support ist rund um die Uhr verfugbar, ist per Chat oder E-Mail erreichbar. Casino-Gewinne kommen wie ein Blitz, manchmal die Casino-Angebote konnten gro?zugiger sein. Alles in allem ist Lowen Play Casino ein Muss fur Casino-Fans fur Fans von Online-Casinos! Ubrigens die Casino-Seite ist ein grafisches Meisterwerk, Lust macht, immer wieder ins Casino zuruckzukehren.
löwen play rastatt|
Unlock your images with WebPtoJPGHero.com, the simple, free solution for solving WebP compatibility issues. While the WebP format helps websites load faster, it can leave you with files you can’t easily edit or share. Our online tool provides an instant fix, transforming any WebP image into a high-quality JPG that works seamlessly across all your devices and applications. You can fine-tune the output quality to balance clarity and file size, and even save time by converting an entire batch of photos at once. It’s all done quickly and privately right in your browser — no software required.
Hi there, You’ve done a great job. I will certainly digg it and personally recommend to my friends. I am sure they’ll be benefited from this site.
https://kidsvisitor.com.ua/yak-pravylno-vstanovyty-linzy-v-fary-dlya-optymaln.html
J’ai une passion devorante pour Monte Cryptos Casino, il propose une odyssee chiffree. Le catalogue est opulent et divers, offrant des sessions en direct immersives. Elevant l’experience de jeu. L’assistance est precise et professionnelle, toujours pret a decoder. Le processus est fluide comme un smart contract, mais des bonus plus varies seraient un atout. En bref, Monte Cryptos Casino offre une experience inoubliable pour les adeptes de jeux modernes ! A noter l’interface est fluide comme un flux de donnees, amplifie le plaisir de jouer. Particulierement captivant le programme VIP avec des niveaux exclusifs, propose des avantages uniques.
DГ©couvrir le guide|
J’adore l’elegance de Impressario Casino, on ressent une ambiance delicate. La selection de jeux est somptueuse, comprenant des jeux compatibles avec les cryptos. Le bonus de bienvenue est delicieux. L’assistance est efficace et professionnelle, joignable a toute heure. Les transactions sont fiables, parfois des bonus plus varies seraient un delice. En resume, Impressario Casino est un incontournable pour les amateurs pour les passionnes de jeux modernes ! A noter la navigation est simple et gracieuse, amplifie le plaisir de jouer. A souligner le programme VIP avec niveaux exclusifs, propose des avantages personnalises.
Explorer le guide|
J’aime l’aura futuriste de Monte Cryptos Casino, ca transporte dans un ocean virtuel. La selection de jeux est astronomique, comprenant des jeux optimises pour BTC et ETH. 100% jusqu’a 300 € + tours gratuits. Le support client est stellaire, avec une aide precise et fiable. Les retraits filent comme une transaction blockchain, neanmoins des bonus plus varies seraient un tresor. Au final, Monte Cryptos Casino offre une experience memorable pour les amateurs de casino en ligne ! A noter le site est rapide et futuriste, facilite une immersion totale. A souligner les options de paris variees, garantit des transactions fiables.
Visiter pour plus|
J’ai une passion ardente pour Monte Cryptos Casino, c’est une plateforme qui vibre d’innovation. Le choix de titres est eblouissant, proposant des jeux de table sophistiques. Avec des promotions crypto rapides. Disponible 24/7 via chat ou email, avec une aide precise et fiable. Les transactions sont securisees par blockchain, parfois des offres plus genereuses ajouteraient du prestige. Dans l’ensemble, Monte Cryptos Casino est une plateforme qui domine le jeu virtuel pour les joueurs en quete d’innovation ! A noter la plateforme est visuellement futuriste, ce qui rend chaque session plus immersive. Particulierement captivant les tournois reguliers pour la competition, propose des avantages sur mesure.
Cliquer et aller|
Je suis totalement envoute par BassBet Casino, ca offre un plaisir fluvial. Les options sont vastes comme un delta, avec des slots aux designs fluviaux. Amplifiant le plaisir de jeu. L’assistance est efficace et professionnelle, offrant des reponses claires. Les retraits sont fluides comme un delta, parfois des offres plus genereuses seraient dynamiques. En bref, BassBet Casino est un incontournable pour les joueurs pour ceux qui aiment parier en crypto ! A noter la navigation est simple et rapide, amplifie le plaisir de jouer. A souligner le programme VIP avec des niveaux exclusifs, offre des recompenses continues.
bassbetcasinobonus777fr.com|
J’adore l’atmosphere rythmee de BassBet Casino, c’est une plateforme qui vibre comme un saxophone. Les options sont vastes comme un concert, proposant des jeux de table elegants. 100% jusqu’a 500 € + tours gratuits. Le support est irreprochable, garantissant un support de qualite. Le processus est simple et elegant, cependant des recompenses additionnelles seraient rythmees. En bref, BassBet Casino vaut une jam session pour ceux qui aiment parier en crypto ! En bonus l’interface est fluide comme un solo, ce qui rend chaque session plus groovy. Egalement appreciable les tournois reguliers pour la competition, qui booste l’engagement.
bassbetcasinologinfr.com|
J’ai une passion narrative pour Spinit Casino, on ressent une ambiance de livre. Le catalogue est riche et varie, proposant des jeux de table elegants. Avec des depots instantanes. L’assistance est efficace et professionnelle, garantissant un support de qualite. Les paiements sont securises et rapides, bien que des offres plus genereuses seraient enchantees. Au final, Spinit Casino offre une experience memorable pour les joueurs en quete d’excitation ! A noter la navigation est simple et magique, ce qui rend chaque session plus enchantee. Un plus le programme VIP avec des niveaux exclusifs, qui booste l’engagement.
https://spinitcasinologinfr.com/|
Je suis totalement enchante par Spinit Casino, il procure une experience magique. Il y a une profusion de jeux fascinants, comprenant des jeux compatibles avec les cryptos. Amplifiant le plaisir de jeu. L’assistance est efficace et professionnelle, garantissant un support de qualite. Les transactions sont fiables, bien que plus de promos regulieres ajouteraient de la magie. Au final, Spinit Casino offre une experience memorable pour ceux qui aiment parier en crypto ! A noter le site est rapide et captivant, ajoute une touche de mystere. A souligner les options de paris sportifs variees, propose des avantages personnalises.
https://casinospinitfr.com/|
Je suis captive par Olympe Casino, ca offre un plaisir immortel. Les options sont vastes comme un pantheon, proposant des jeux de table glorieux. 100% jusqu’a 500 € + tours gratuits. Les agents repondent comme des dieux, garantissant un support celeste. Les gains arrivent sans delai, bien que des offres plus genereuses seraient olympiennes. En bref, Olympe Casino est une plateforme qui regne sur l’Olympe pour les passionnes de jeux antiques ! De plus l’interface est fluide comme un nectar, donne envie de prolonger l’aventure. Un plus divin les tournois reguliers pour la competition, propose des avantages sur mesure.
https://olympefr.com/|
Hi there, yup this paragraph is actually pleasant and I have learned lot of things from it on the topic of blogging. thanks.
бонус драгон мани казино
Because the admin of this site is working, no uncertainty very quickly it will be famous, due to its quality contents.
зеркало zooma casino
J’ai une passion ardente pour Monte Cryptos Casino, ca transporte dans un monde virtuel. Le catalogue est opulent et divers, avec des slots aux designs modernes. Elevant l’experience de jeu. Disponible 24/7 via chat ou email, joignable a tout moment. Les paiements sont securises par blockchain, de temps a autre des offres plus genereuses ajouteraient du charme. Dans l’ensemble, Monte Cryptos Casino vaut une exploration virtuelle pour ceux qui parient avec des cryptos ! A noter la navigation est simple comme un wallet, facilite une immersion totale. A souligner le programme VIP avec des niveaux exclusifs, offre des recompenses continues.
Découvrir l’avis|
J’aime l’ambiance numerique de Monte Cryptos Casino, il propose une odyssee chiffree. Le catalogue est opulent et divers, proposant des tables sophistiquees. Boostant votre capital initial. Les agents repondent avec une vitesse fulgurante, offrant des solutions claires. Les gains arrivent sans delai, cependant des offres plus genereuses ajouteraient du charme. En resume, Monte Cryptos Casino est un must pour les fans de blockchain pour les adeptes de jeux modernes ! De plus la plateforme est visuellement eblouissante, ajoute une touche de sophistication. Egalement cool les options de paris variees, propose des avantages uniques.
Apprendre les dГ©tails|
Je suis enchante par Impressario Casino, c’est une plateforme qui evoque le raffinement. Les options sont vastes comme un menu etoile, incluant des paris sportifs distingues. Renforcant votre capital initial. Les agents repondent avec courtoisie, avec une aide precise. Les retraits sont fluides comme la Seine, neanmoins des offres plus genereuses seraient exquises. Au final, Impressario Casino est un incontournable pour les amateurs pour les joueurs en quete d’excitation ! De plus la navigation est simple et gracieuse, amplifie le plaisir de jouer. Un plus les paiements securises en crypto, assure des transactions fiables.
Jeter un coup d’œil|
Je suis charme par Impressario Casino, ca offre un plaisir sophistique. La selection de jeux est somptueuse, proposant des jeux de table raffines. Le bonus de bienvenue est delicieux. Le suivi est irreprochable, garantissant un support de qualite. Le processus est simple et elegant, bien que plus de promos regulieres ajouteraient du piquant. Pour conclure, Impressario Casino offre une experience memorable pour les joueurs en quete d’excitation ! Par ailleurs le design est moderne et chic, ce qui rend chaque session plus raffinee. Egalement appreciable le programme VIP avec niveaux exclusifs, qui booste l’engagement.
Obtenir les bonus|
Je suis ensorcele par Monte Cryptos Casino, on capte une energie decentralisee. Les options sont vastes comme un reseau, offrant des sessions en direct immersives. Le bonus d’entree est scintillant. Le support client est futuriste, avec une aide precise. Le processus est lisse comme un smart contract, cependant des bonus plus varies seraient un plus. Dans l’ensemble, Monte Cryptos Casino est un must pour les fans de blockchain pour les amateurs de casino en ligne ! Ajoutons que la plateforme est visuellement eblouissante, ce qui rend chaque session plus immersive. Un avantage notable le programme VIP avec des niveaux exclusifs, offre des recompenses continues.
Cliquer et voir|
I blog often and I really appreciate your content. This great article has really peaked my interest. I am going to bookmark your site and keep checking for new details about once per week. I subscribed to your Feed too.
регистрация казино либет
What a information of un-ambiguity and preserveness of precious know-how regarding unexpected emotions.
казино banda
Hey there, You’ve done an excellent job. I will certainly digg it and personally suggest to my friends. I am sure they will be benefited from this site.
купить виртуальный номер
J’ai un amour vibrant pour BassBet Casino, il cree une ambiance de studio live. La selection de jeux est explosive, avec des slots aux designs dynamiques. L’offre de bienvenue est electrisante. L’assistance est rapide et pro, toujours pret a mixer. Les transactions sont fiables, neanmoins quelques tours gratuits en plus seraient top. En resume, BassBet Casino est une plateforme qui pulse pour ceux qui parient avec des cryptos ! Ajoutons que le design est moderne et vibrant, facilite une immersion totale. Particulierement cool le programme VIP avec des niveaux exclusifs, assure des transactions fiables.
https://bassbetcasinoappfr.com/|
BassBet Casino m’a captive BassBet Casino, c’est une plateforme qui scintille comme un neon. Le catalogue est riche en surprises, avec des slots aux designs fluorescents. 100% jusqu’a 500 € + tours gratuits. L’assistance est rapide et pro, toujours pret a eclairer. Le processus est simple et lumineux, neanmoins plus de promos regulieres ajouteraient du scintillement. Au final, BassBet Casino vaut une soiree lumineuse pour les fans de casino en ligne ! Par ailleurs le site est rapide et captivant, ce qui rend chaque session plus brillante. Un atout les paiements securises en crypto, assure des transactions fiables.
bassbetcasinopromocodefr.com|
J’adore l’atmosphere aquatique de BassBet Casino, ca plonge dans un monde de vagues. Les options sont vastes comme un lac, offrant des sessions live immersives. Renforcant votre capital initial. Le support client est dynamique, offrant des reponses claires. Les gains arrivent sans delai, de temps a autre plus de promos regulieres ajouteraient du rythme. En bref, BassBet Casino vaut une peche excitante pour les passionnes de jeux modernes ! De plus le design est moderne et dynamique, facilitate une immersion totale. Un autre atout les evenements communautaires engageants, renforce le sentiment de communaute.
bassbetcasinobonusfr.com|
J’ai une passion parfumee pour Spinit Casino, ca plonge dans un monde aromatique. La variete des titres est raffinee, comprenant des jeux compatibles avec les cryptos. Amplifiant le plaisir de jeu. Le support client est impeccable, offrant des reponses claires. Les gains arrivent sans delai, neanmoins quelques tours gratuits supplementaires seraient bien venus. En resume, Spinit Casino vaut une visite sophistiquee pour les passionnes de jeux modernes ! En bonus le design est moderne et chic, donne envie de prolonger l’experience. Un plus le programme VIP avec des niveaux exclusifs, offre des recompenses continues.
spinitcasinobonusfr.com|
J’ai une affection pour Impressario Casino, c’est une plateforme qui evoque le raffinement. La variete des titres est raffinee, offrant des sessions live sophistiquees. 100% jusqu’a 500 € + tours gratuits. L’assistance est efficace et professionnelle, avec une aide precise. Les paiements sont securises et rapides, cependant des recompenses additionnelles seraient royales. En bref, Impressario Casino vaut une visite sophistiquee pour les joueurs en quete d’excitation ! De plus la navigation est simple et gracieuse, amplifie le plaisir de jouer. Particulierement interessant les paiements securises en crypto, renforce le sentiment de communaute.
DГ©couvrir la page|
Je suis seduit par Impressario Casino, on ressent une ambiance sophistiquee. Il y a une abondance de jeux captivants, avec des slots aux designs raffines. 100% jusqu’a 500 € + tours gratuits. Le suivi est irreprochable, joignable a toute heure. Le processus est simple et elegant, cependant des recompenses additionnelles seraient royales. Pour conclure, Impressario Casino offre une experience memorable pour les passionnes de jeux modernes ! Ajoutons que la plateforme est visuellement somptueuse, ce qui rend chaque session plus raffinee. A souligner les options de paris sportifs variees, renforce le sentiment de communaute.
Obtenir l’offre|
J’adore l’elegance de Impressario Casino, c’est une plateforme qui evoque le raffinement. La variete des titres est raffinee, avec des slots aux designs elegants. Le bonus de bienvenue est delicieux. Le service est disponible 24/7, offrant des reponses claires. Les gains arrivent sans delai, cependant des recompenses additionnelles seraient royales. Au final, Impressario Casino garantit un plaisir constant pour les passionnes de jeux modernes ! Par ailleurs l’interface est fluide comme un banquet, facilite une immersion totale. Un autre atout le programme VIP avec niveaux exclusifs, propose des avantages personnalises.
Jeter un coup d’œil|
Ich liebe die Atmosphare bei Snatch Casino, es verspricht ein einzigartiges Abenteuer. Es gibt zahlreiche spannende Spiele, mit Spielautomaten in beeindruckenden Designs. Der Willkommensbonus ist ein Highlight. Der Support ist effizient und professionell. Transaktionen sind zuverlassig und klar, in manchen Fallen mehr Promo-Vielfalt ware toll. Letztlich, Snatch Casino sorgt fur kontinuierlichen Spa?. Au?erdem die Oberflache ist glatt und benutzerfreundlich, eine tiefe Immersion ermoglicht. Ein gro?er Pluspunkt die dynamischen Community-Events, ma?geschneiderte Vorteile liefern.
Snatch Casino|
whoah this weblog is wonderful i like reading your articles. Stay up the good work! You realize, a lot of persons are hunting around for this information, you can help them greatly.
https://almaty-kz.forum2x2.ru/t760-topic#1091
Thank you for any other informative website. Where else may I am getting that type of information written in such an ideal manner? I have a challenge that I’m just now operating on, and I have been at the look out for such information.
http://blooms.com.ua/yak-pravylno-vybyraty-steklo-fara-dlya-retro-avtom.html
I savour, cause I found exactly what I was having a look for. You’ve ended my four day lengthy hunt! God Bless you man. Have a great day. Bye
маркетплейс kraken
Je suis epoustoufle par BassBet Casino, il cree une ambiance de concert. Le catalogue est riche en emotions, offrant des sessions live immersives. Amplifiant l’excitation du jeu. Le suivi est impeccable, joignable a tout moment. Le processus est simple et vibrant, de temps en temps plus de promos regulieres ajouteraient du rythme. Pour conclure, BassBet Casino garantit un fun non-stop pour les joueurs en quete d’adrenaline ! Par ailleurs la navigation est simple et rythmee, booste le plaisir de jouer. Un atout le programme VIP avec des niveaux exclusifs, renforce la communaute.
https://bassbetcasinopromocodefr.com/|
J’ai une passion cyclonique pour Spinit Casino, ca offre un plaisir veloce. La variete des titres est rapide, offrant des sessions live immersives. 100% jusqu’a 500 € + tours gratuits. Le support client est veloce, offrant des reponses claires. Le processus est simple et elegant, neanmoins des bonus plus varies seraient un sprint. Pour conclure, Spinit Casino garantit un plaisir constant pour les joueurs en quete d’excitation ! Ajoutons que le site est rapide et attractif, ce qui rend chaque session plus excitante. Un autre atout les evenements communautaires engageants, qui booste l’engagement.
https://casinospinitfr.com/|
Je suis totalement envoute par BassBet Casino, on ressent une ambiance de studio. La variete des titres est harmonieuse, incluant des paris sportifs dynamiques. Amplifiant le plaisir de jeu. Le service est disponible 24/7, joignable a toute heure. Les paiements sont securises et rapides, parfois plus de promos regulieres ajouteraient du groove. En bref, BassBet Casino garantit un plaisir constant pour les passionnes de jeux modernes ! A noter l’interface est fluide comme un riff, ajoute une touche de rythme. Egalement appreciable les paiements securises en crypto, renforce le sentiment de communaute.
bassbetcasinobonusfr.com|
Je suis emerveille par Spinit Casino, ca plonge dans un monde de legendes. Les options sont vastes comme un grimoire, offrant des sessions live immersives. Avec des depots instantanes. L’assistance est efficace et professionnelle, joignable a toute heure. Le processus est simple et elegant, bien que des recompenses additionnelles seraient narratives. Dans l’ensemble, Spinit Casino est un incontournable pour les joueurs pour les passionnes de jeux modernes ! En bonus l’interface est fluide comme un conte, ajoute une touche de mystere. A souligner le programme VIP avec des niveaux exclusifs, renforce le sentiment de communaute.
spinitcasinobonusfr.com|
Je suis emerveille par Impressario Casino, il evoque un jardin parfume. L’eventail de jeux est somptueux, avec des slots aux designs soignes. L’offre de bienvenue est envoutante. Disponible 24/7 via chat ou email, avec une aide efficace. Les transactions sont fiables, cependant des bonus plus varies seraient un delice. Pour conclure, Impressario Casino vaut une visite elegante pour les joueurs en quete de magie ! A souligner le site est rapide et envoutant, ajoute une touche de finesse. Particulierement captivant le programme VIP avec des niveaux exclusifs, offre des recompenses continues.
DГ©couvrir le site|
Je suis ebloui par Monte Cryptos Casino, il propose une odyssee chiffree. Les options sont vastes comme un ledger, comprenant des jeux optimises pour les cryptos. Boostant votre capital initial. Disponible 24/7 via chat ou email, toujours pret a decoder. Le processus est fluide comme un smart contract, mais quelques tours gratuits en plus seraient bienvenus. Au final, Monte Cryptos Casino offre une experience inoubliable pour ceux qui parient avec des cryptos ! En bonus la navigation est simple comme un wallet, donne envie de prolonger l’aventure. Un atout cle les tournois reguliers pour la competition, offre des recompenses continues.
Ouvrir le site|
Je suis fascine par Impressario Casino, c’est une plateforme qui brille comme un festival. Le catalogue est riche et varie, incluant des paris sportifs dynamiques. Avec des depots rapides. Le suivi est d’une precision remarquable, garantissant un service de star. Les paiements sont securises et rapides, de temps en temps quelques tours gratuits supplementaires seraient apprecies. En bref, Impressario Casino garantit un plaisir constant pour les amateurs de casino en ligne ! A souligner la plateforme brille comme une premiere, facilite une immersion totale. Egalement remarquable les options de paris variees, assure des transactions fiables.
Aller sur le site web|
May I just say what a relief to discover an individual who truly knows what they’re talking about on the net. You definitely realize how to bring an issue to light and make it important. More people really need to look at this and understand this side of your story. It’s surprising you are not more popular since you surely possess the gift.
маркетплейс kraken
Keep on writing, great job!
https://kra42c.com
Keep on working, great job!
https://kra41c.com
Je suis captive par Olympe Casino, il procure une experience harmonieuse. Il y a une profusion de jeux captivants, offrant des sessions live immortelles. Renforcant votre tresor initial. Le suivi est irreprochable, garantissant un support celeste. Le processus est simple et glorieux, parfois plus de promos regulieres ajouteraient de la gloire. En bref, Olympe Casino est un incontournable pour les joueurs pour ceux qui aiment parier en crypto ! Par ailleurs la navigation est simple comme un oracle, ajoute une touche de mythologie. A souligner les paiements securises en crypto, propose des avantages sur mesure.
olympefr.com|
Ich freue mich sehr uber Cat Spins Casino, es begeistert mit Dynamik. Es gibt eine Fulle an aufregenden Titeln, mit spannenden Sportwetten-Angeboten. Mit blitzschnellen Einzahlungen. Der Service ist von hochster Qualitat. Auszahlungen sind schnell und reibungslos, allerdings mehr Bonusvarianten waren ein Hit. Abschlie?end, Cat Spins Casino sorgt fur ununterbrochenen Spa?. Au?erdem die Navigation ist unkompliziert, das Vergnugen maximiert. Ein starker Vorteil die vielfaltigen Sportwetten-Optionen, die die Gemeinschaft starken.
Zur Seite gehen|
Ich bin vollig uberzeugt von Cat Spins Casino, es bietet ein mitrei?endes Spielerlebnis. Es gibt unzahlige packende Spiele, mit Krypto-kompatiblen Spielen. Mit blitzschnellen Einzahlungen. Der Kundendienst ist ausgezeichnet. Auszahlungen sind zugig und unkompliziert, dennoch waren mehr Bonusvarianten ein Plus. Kurz und bundig, Cat Spins Casino ist ein Muss fur Spieler. Au?erdem die Plattform ist optisch ein Highlight, zum Verweilen einladt. Ein tolles Extra die lebendigen Community-Events, ma?geschneiderte Vorteile liefern.
Inhalt entdecken|
J’adore l’ambiance electrisante de Ruby Slots Casino, il offre une experience dynamique. La variete des jeux est epoustouflante, offrant des experiences de casino en direct. Il booste votre aventure des le depart. Les agents sont rapides et pros. Les retraits sont fluides et rapides, rarement des bonus plus varies seraient un plus. Au final, Ruby Slots Casino merite une visite dynamique. En complement le design est moderne et attrayant, donne envie de continuer l’aventure. Egalement genial les options de paris sportifs variees, qui motive les joueurs.
Consulter les dГ©tails|
Je suis captive par Sugar Casino, il cree un monde de sensations fortes. Le catalogue de titres est vaste, avec des machines a sous aux themes varies. 100% jusqu’a 500 € avec des free spins. Les agents sont toujours la pour aider. Les retraits sont fluides et rapides, toutefois des recompenses en plus seraient un bonus. Au final, Sugar Casino vaut une visite excitante. A noter le design est moderne et attrayant, donne envie de prolonger l’aventure. Particulierement cool les evenements communautaires dynamiques, propose des privileges personnalises.
Approfondir|
J’adore l’ambiance electrisante de Ruby Slots Casino, on y trouve une vibe envoutante. Les titres proposes sont d’une richesse folle, incluant des paris sur des evenements sportifs. 100% jusqu’a 500 € avec des spins gratuits. Disponible 24/7 par chat ou email. Le processus est simple et transparent, cependant plus de promotions variees ajouteraient du fun. En bref, Ruby Slots Casino offre une aventure inoubliable. Notons egalement le design est moderne et energique, donne envie de continuer l’aventure. Un avantage les tournois reguliers pour la competition, assure des transactions fluides.
Lancer le site|
code promo abidjan Ultimately, the goal is to find a “code promo pour 1xBet” or “code promo sur 1xbet” that provides a real advantage. Whether it’s a “bonus d’inscription 1xbet” or a “code promo 1xbet 131$,” smart bettors understand the power of a well-chosen promotional code. Thorough research, verification, and understanding the terms and conditions are paramount to successfully leveraging these offers.
This site definitely has all of the information and facts I wanted about this subject and didn’t know who to ask.
https://demo73.symatrixdigitalmarketing.co.in/2025/10/09/skachat-melbet-na-telefon-android-2025/
What’s up to all, it’s really a good for me to go to see this web page, it includes useful Information.
https://atm87.com/skachat-melbet-na-android-s-oficialnogo-2025/
Je suis captive par Olympe Casino, ca offre un plaisir melodieux. Il y a une profusion de jeux captivants, offrant des sessions live immortelles. 100% jusqu’a 500 € + tours gratuits. L’assistance est efficace et sage, garantissant un support celeste. Les retraits sont rapides comme une melodie, neanmoins des recompenses supplementaires seraient eternelles. Pour conclure, Olympe Casino offre une experience legendaire pour les passionnes de jeux antiques ! De plus la plateforme est visuellement olympienne, facilite une immersion totale. Un plus divin les tournois reguliers pour la competition, qui booste l’engagement.
https://olympefr.com/|
Ich bin vollig uberzeugt von Cat Spins Casino, es bietet eine Welt voller Action. Es gibt unzahlige packende Spiele, mit klassischen Tischspielen. 100 % bis zu 500 € inklusive Freispiele. Der Kundendienst ist ausgezeichnet. Transaktionen sind zuverlassig und klar, jedoch zusatzliche Freispiele waren willkommen. Im Gro?en und Ganzen, Cat Spins Casino ist ein Muss fur Spieler. Hinzu kommt die Navigation ist intuitiv und einfach, eine vollstandige Immersion ermoglicht. Ein wichtiger Vorteil die breiten Sportwetten-Angebote, die die Gemeinschaft starken.
Mehr darГјber erfahren|
Ich liebe das Flair von Cat Spins Casino, es sorgt fur ein fesselndes Erlebnis. Das Spieleportfolio ist unglaublich breit, mit klassischen Tischspielen. Er bietet einen gro?artigen Vorteil. Der Kundendienst ist hervorragend. Auszahlungen sind einfach und schnell, allerdings mehr Bonusvarianten waren ein Hit. In Summe, Cat Spins Casino ist ein Muss fur Spielbegeisterte. Hinzu kommt ist das Design modern und einladend, eine vollstandige Eintauchen ermoglicht. Ein tolles Feature die vielfaltigen Wettmoglichkeiten, exklusive Boni bieten.
Jetzt ausprobieren|
Je suis enthousiasme par Sugar Casino, il offre une experience dynamique. Le catalogue est un tresor de divertissements, proposant des jeux de table classiques. Avec des depots rapides et faciles. Disponible a toute heure via chat ou email. Les paiements sont securises et instantanes, cependant quelques tours gratuits en plus seraient geniaux. Pour conclure, Sugar Casino offre une aventure inoubliable. A mentionner le design est moderne et energique, permet une immersion complete. Un point fort les tournois frequents pour l’adrenaline, cree une communaute soudee.
En savoir davantage|
Je suis epate par Ruby Slots Casino, on ressent une ambiance de fete. Les jeux proposes sont d’une diversite folle, incluant des paris sportifs pleins de vie. Avec des depots rapides et faciles. Le support est fiable et reactif. Les gains sont transferes rapidement, par moments plus de promotions frequentes boosteraient l’experience. Au final, Ruby Slots Casino est un choix parfait pour les joueurs. En plus la plateforme est visuellement electrisante, facilite une immersion totale. A souligner le programme VIP avec des privileges speciaux, propose des privileges sur mesure.
Aller plus loin|
Je ne me lasse pas de Sugar Casino, on y trouve une vibe envoutante. Les options de jeu sont incroyablement variees, incluant des paris sportifs en direct. Il offre un demarrage en fanfare. Le support est fiable et reactif. Les retraits sont lisses comme jamais, par ailleurs des recompenses en plus seraient un bonus. Au final, Sugar Casino est un endroit qui electrise. A noter le site est fluide et attractif, ce qui rend chaque moment plus vibrant. Un element fort les paiements en crypto rapides et surs, qui dynamise l’engagement.
Jeter un coup d’œil|
Je suis accro a Ruby Slots Casino, on y trouve une energie contagieuse. Les titres proposes sont d’une richesse folle, offrant des experiences de casino en direct. Avec des depots fluides. Le suivi est d’une precision remarquable. Le processus est transparent et rapide, parfois quelques tours gratuits en plus seraient geniaux. Pour conclure, Ruby Slots Casino est une plateforme qui pulse. Notons aussi la plateforme est visuellement dynamique, booste l’excitation du jeu. Un point cle les transactions crypto ultra-securisees, assure des transactions fiables.
Naviguer sur le site|
Ich habe eine Leidenschaft fur Cat Spins Casino, es ladt zu unvergesslichen Momenten ein. Das Spieleportfolio ist unglaublich breit, mit stilvollen Tischspielen. Er steigert das Spielvergnugen sofort. Der Support ist professionell und schnell. Transaktionen sind zuverlassig und effizient, trotzdem zusatzliche Freispiele waren ein Bonus. Abschlie?end, Cat Spins Casino sorgt fur ununterbrochenen Spa?. Au?erdem die Oberflache ist glatt und benutzerfreundlich, eine vollstandige Eintauchen ermoglicht. Ein starkes Feature die regelma?igen Turniere fur Wettbewerbsspa?, sichere Zahlungen garantieren.
Zur Website gehen|
Ich liebe das Flair von Cat Spins Casino, es sorgt fur pure Unterhaltung. Die Spielauswahl ist ein echtes Highlight, inklusive dynamischer Sportwetten. Er macht den Einstieg unvergesslich. Der Kundensupport ist top. Transaktionen sind zuverlassig und effizient, allerdings regelma?igere Promos wurden das Spiel aufwerten. Alles in allem, Cat Spins Casino ist eine Plattform, die uberzeugt. Nebenbei ist das Design stilvoll und einladend, eine Prise Stil hinzufugt. Ein starkes Feature sind die schnellen Krypto-Transaktionen, die die Begeisterung steigern.
Zur Website gehen|
Ich bin suchtig nach Cat Spins Casino, es bietet ein immersives Erlebnis. Die Spiele sind abwechslungsreich und fesselnd, mit modernen Slots in ansprechenden Designs. Er steigert das Spielvergnugen sofort. Verfugbar 24/7 fur alle Fragen. Die Zahlungen sind sicher und sofortig, jedoch mehr Bonusoptionen waren top. Letztlich, Cat Spins Casino ist ein Ort, der begeistert. Au?erdem die Benutzeroberflache ist flussig und intuitiv, jede Session unvergesslich macht. Ein besonders cooles Feature die zahlreichen Sportwetten-Moglichkeiten, die Gemeinschaft starken.
Jetzt entdecken|
Ich bin beeindruckt von der Qualitat bei Cat Spins Casino, es bietet packende Unterhaltung. Das Spieleportfolio ist unglaublich breit, inklusive dynamischer Sportwetten. Er gibt Ihnen einen tollen Boost. Erreichbar rund um die Uhr. Transaktionen sind zuverlassig und effizient, allerdings mehr Promo-Vielfalt ware toll. In Summe, Cat Spins Casino ist ein Highlight fur Casino-Fans. Au?erdem die Plattform ist optisch ansprechend, eine vollstandige Eintauchen ermoglicht. Ein gro?es Plus ist das VIP-Programm mit besonderen Vorteilen, fortlaufende Belohnungen bieten.
Website besuchen|
Ich freue mich riesig uber Cat Spins Casino, es sorgt fur pure Unterhaltung. Das Portfolio ist vielfaltig und attraktiv, mit interaktiven Live-Spielen. Er macht den Start aufregend. Der Service ist immer zuverlassig. Die Zahlungen sind sicher und sofortig, ab und zu gro?ere Boni waren ideal. Am Ende, Cat Spins Casino ist ein Top-Ziel fur Spieler. Au?erdem die Oberflache ist glatt und benutzerfreundlich, und ladt zum Verweilen ein. Ein starkes Feature sind die zuverlassigen Krypto-Zahlungen, die die Begeisterung steigern.
Eintauchen|
Je suis sous le charme de Ruby Slots Casino, ca transporte dans un monde d’excitation. Les options de jeu sont incroyablement variees, offrant des sessions live palpitantes. Il propulse votre jeu des le debut. Le support est efficace et amical. Les transactions sont fiables et efficaces, quelquefois plus de promos regulieres ajouteraient du peps. En somme, Ruby Slots Casino offre une aventure memorable. En bonus le site est rapide et style, incite a prolonger le plaisir. Un point cle les options de paris sportifs diversifiees, renforce la communaute.
Visiter la plateforme|
Je suis totalement conquis par Sugar Casino, on y trouve une vibe envoutante. Il y a une abondance de jeux excitants, avec des slots aux designs captivants. Il booste votre aventure des le depart. Les agents sont toujours la pour aider. Les retraits sont fluides et rapides, par ailleurs quelques free spins en plus seraient bienvenus. En resume, Sugar Casino est une plateforme qui fait vibrer. A noter la navigation est simple et intuitive, ajoute une touche de dynamisme. Egalement super les paiements securises en crypto, offre des recompenses continues.
Voir la page d’accueil|
J’ai un faible pour Ruby Slots Casino, on y trouve une energie contagieuse. La selection est riche et diversifiee, avec des machines a sous aux themes varies. Il amplifie le plaisir des l’entree. Les agents sont rapides et pros. Le processus est fluide et intuitif, par contre des bonus varies rendraient le tout plus fun. En conclusion, Ruby Slots Casino est un immanquable pour les amateurs. Ajoutons aussi la plateforme est visuellement vibrante, ajoute une touche de dynamisme. A mettre en avant les paiements en crypto rapides et surs, propose des privileges sur mesure.
Explorer maintenant|
Je suis epate par Sugar Casino, il cree un monde de sensations fortes. Les titres proposes sont d’une richesse folle, proposant des jeux de casino traditionnels. Il amplifie le plaisir des l’entree. Le service est disponible 24/7. Les gains arrivent en un eclair, neanmoins des offres plus genereuses seraient top. Pour conclure, Sugar Casino offre une aventure inoubliable. Ajoutons que l’interface est simple et engageante, permet une plongee totale dans le jeu. Un plus les tournois reguliers pour s’amuser, assure des transactions fluides.
Voir maintenant|
7k casino официальный сайт рабочее зеркало 7к предоставляет игрокам возможность оставаться в игре, даже если основной сайт временно недоступен.
Galera, resolvi contar como foi no 4PlayBet Casino porque nao e so mais um cassino online. A variedade de jogos e simplesmente incrivel: blackjack envolvente, todos sem travar. O suporte foi amigavel, responderam em minutos pelo chat, algo que vale elogio. Fiz saque em transferencia e o dinheiro entrou muito rapido, ponto fortissimo. Se tivesse que criticar, diria que senti falta de ofertas recorrentes, mas isso nao estraga a experiencia. No geral, o 4PlayBet Casino vale demais a pena. Recomendo sem medo.
gunmetal 4play wheels|
Ich bin ein gro?er Fan von Cat Spins Casino, es ist ein Ort, der begeistert. Das Spieleportfolio ist unglaublich breit, mit immersiven Live-Dealer-Spielen. Er bietet einen tollen Startvorteil. Der Service ist immer zuverlassig. Der Prozess ist unkompliziert, jedoch regelma?igere Promos wurden das Spiel aufwerten. Letztlich, Cat Spins Casino bietet ein unvergessliches Erlebnis. Nebenbei die Plattform ist visuell ansprechend, zum Weiterspielen animiert. Ein tolles Feature die haufigen Turniere fur Wettbewerb, die Community enger verbinden.
FГјr mehr besuchen|
I’m addicted to the energy at Pinco, you feel the buzz from the first spin. The game selection is massive, featuring sleek table games. The welcome bonus is generous. Customer care is elite. The process is intuitive and quick, in some cases extra rewards would be perfect. In the end, Pinco delivers a premium experience. Additionally the site is snappy and engaging, amps up the excitement. Particularly notable are the diverse sports betting options, that offers continuous rewards.
Explore the site|
J’adore l’ambiance electrisante de Ruby Slots Casino, il cree une experience captivante. Les options de jeu sont incroyablement variees, avec des slots aux designs captivants. Il booste votre aventure des le depart. Le support client est irreprochable. Les retraits sont simples et rapides, a l’occasion quelques tours gratuits supplementaires seraient cool. Au final, Ruby Slots Casino merite un detour palpitant. Par ailleurs la navigation est simple et intuitive, incite a rester plus longtemps. A signaler les paiements en crypto rapides et surs, assure des transactions fiables.
https://rubyslotscasinopromocodefr.com/|
J’ai une affection particuliere pour Ruby Slots Casino, il propose une aventure palpitante. La selection est riche et diversifiee, comprenant des jeux optimises pour Bitcoin. Le bonus de bienvenue est genereux. Le service client est de qualite. Les retraits sont fluides et rapides, quelquefois des bonus diversifies seraient un atout. Globalement, Ruby Slots Casino assure un fun constant. Par ailleurs la navigation est claire et rapide, amplifie l’adrenaline du jeu. A souligner les tournois reguliers pour la competition, qui motive les joueurs.
Essayer|
Je suis enthousiaste a propos de Sugar Casino, c’est une plateforme qui deborde de dynamisme. On trouve une profusion de jeux palpitants, avec des machines a sous aux themes varies. Il booste votre aventure des le depart. Le suivi est d’une fiabilite exemplaire. Les retraits sont simples et rapides, rarement des bonus diversifies seraient un atout. En bref, Sugar Casino offre une aventure inoubliable. Par ailleurs l’interface est fluide comme une soiree, ajoute une vibe electrisante. Egalement excellent les evenements communautaires engageants, qui motive les joueurs.
Essayer|
J’ai une affection particuliere pour Sugar Casino, ca invite a l’aventure. Les jeux proposes sont d’une diversite folle, comprenant des jeux crypto-friendly. Il propulse votre jeu des le debut. Le service d’assistance est au point. Les gains sont verses sans attendre, toutefois des recompenses supplementaires seraient parfaites. En resume, Sugar Casino assure un fun constant. Par ailleurs l’interface est intuitive et fluide, donne envie de prolonger l’aventure. Particulierement interessant les tournois reguliers pour la competition, propose des avantages uniques.
https://sugarcasinobonusfr.com/|
J’adore l’ambiance electrisante de Sugar Casino, ca donne une vibe electrisante. On trouve une profusion de jeux palpitants, avec des slots aux graphismes modernes. Il donne un avantage immediat. Le service client est de qualite. Les retraits sont simples et rapides, occasionnellement plus de promotions variees ajouteraient du fun. Pour finir, Sugar Casino est un immanquable pour les amateurs. Pour completer la navigation est intuitive et lisse, permet une plongee totale dans le jeu. Particulierement fun les options variees pour les paris sportifs, qui dynamise l’engagement.
Plonger dedans|
Je trouve absolument fantastique 7BitCasino, ca ressemble a une experience de jeu electrisante. La selection de jeux est colossale, comprenant plus de 5 000 jeux, dont 4 000 adaptes aux cryptomonnaies. Le personnel offre un accompagnement irreprochable, garantissant une aide immediate via chat en direct ou email. Les gains sont verses en un temps record, bien que les promotions pourraient etre plus genereuses, ou des tournois avec des prix plus eleves. Globalement, 7BitCasino ne decoit jamais pour les amateurs de casino en ligne ! Ajoutons que le site est concu avec style et modernite, ajoute une touche de raffinement a l’experience.
7bitcasino no deposit bonus|
Ich bin fasziniert von Cat Spins Casino, es bietet eine Welt voller Action. Die Spielauswahl ist beeindruckend, mit Spielautomaten in beeindruckenden Designs. Der Bonus fur Neukunden ist attraktiv. Der Service ist von hochster Qualitat. Gewinne werden ohne Wartezeit uberwiesen, von Zeit zu Zeit gro?ere Boni waren ideal. Am Ende, Cat Spins Casino ist definitiv einen Besuch wert. Au?erdem die Benutzeroberflache ist klar und flussig, eine tiefe Immersion ermoglicht. Ein besonders cooles Feature die dynamischen Community-Veranstaltungen, schnelle Zahlungen garantieren.
FГјr mehr besuchen|
Ich habe einen totalen Hang zu SpinBetter Casino, es ist eine Erfahrung, die wie ein Wirbelsturm pulsiert. Der Katalog ist reichhaltig und variiert, mit Spielen, die fur Kryptos optimiert sind. Der Service ist von hoher Qualitat, garantiert top Hilfe. Die Auszahlungen sind ultraschnell, ab und an die Offers konnten gro?zugiger ausfallen. In Kurze, SpinBetter Casino ist eine Plattform, die uberzeugt fur Spieler auf der Suche nach Action ! Daruber hinaus die Interface ist intuitiv und modern, was jede Session noch besser macht. Besonders toll die schnellen Einzahlungen, die Vertrauen schaffen.
https://spinbettercasino.de/|
J’ai une affection particuliere pour Ruby Slots Casino, on ressent une ambiance festive. Les options sont aussi vastes qu’un horizon, incluant des paris sportifs en direct. Avec des transactions rapides. Disponible a toute heure via chat ou email. Les gains sont transferes rapidement, neanmoins des bonus diversifies seraient un atout. Globalement, Ruby Slots Casino offre une experience hors du commun. Par ailleurs l’interface est simple et engageante, ce qui rend chaque moment plus vibrant. A noter les evenements communautaires vibrants, assure des transactions fluides.
Savoir plus|
Je suis fascine par Ruby Slots Casino, c’est un lieu ou l’adrenaline coule a flots. La bibliotheque est pleine de surprises, offrant des sessions live palpitantes. 100% jusqu’a 500 € + tours gratuits. Les agents sont toujours la pour aider. Le processus est fluide et intuitif, en revanche quelques tours gratuits en plus seraient geniaux. En conclusion, Ruby Slots Casino est un endroit qui electrise. Pour ajouter le design est moderne et attrayant, facilite une immersion totale. Un avantage notable les paiements en crypto rapides et surs, qui booste la participation.
Emmenez-moi lГ -bas|
J’ai une passion debordante pour Ruby Slots Casino, il cree un monde de sensations fortes. La variete des jeux est epoustouflante, offrant des tables live interactives. Avec des depots instantanes. Le support est efficace et amical. Les paiements sont surs et fluides, parfois plus de promotions variees ajouteraient du fun. Pour conclure, Ruby Slots Casino est un immanquable pour les amateurs. Pour completer l’interface est simple et engageante, facilite une immersion totale. A souligner les transactions crypto ultra-securisees, offre des recompenses regulieres.
DГ©marrer maintenant|
Ich liebe die Atmosphare bei Cat Spins Casino, es ist ein Hotspot fur Spielspa?. Es gibt eine enorme Vielfalt an Spielen, mit stilvollen Tischspielen. Er gibt Ihnen einen tollen Boost. Der Kundendienst ist ausgezeichnet. Der Prozess ist klar und effizient, von Zeit zu Zeit mehr Bonusangebote waren spitze. Kurz gesagt, Cat Spins Casino ist ein Ort fur pure Unterhaltung. Nebenbei die Navigation ist intuitiv und einfach, eine Prise Stil hinzufugt. Ein tolles Feature die dynamischen Community-Events, die die Motivation erhohen.
Mehr lesen|
1000 за регистрацию без депозита казино
Ich bin absolut begeistert von Cat Spins Casino, es schafft eine mitrei?ende Stimmung. Es gibt unzahlige packende Spiele, mit aufregenden Live-Casino-Erlebnissen. 100 % bis zu 500 € plus Freispiele. Der Service ist rund um die Uhr verfugbar. Gewinne kommen sofort an, allerdings haufigere Promos wurden begeistern. Letztlich, Cat Spins Casino ist ein Top-Ziel fur Spieler. Au?erdem ist das Design stilvoll und modern, eine vollstandige Immersion ermoglicht. Ein bemerkenswertes Feature die vielfaltigen Sportwetten-Optionen, schnelle Zahlungen garantieren.
Zur Website gelangen|
Ich freue mich riesig uber Cat Spins Casino, es verspricht pure Spannung. Es gibt zahlreiche spannende Spiele, mit spannenden Sportwetten-Angeboten. Mit blitzschnellen Einzahlungen. Der Support ist schnell und freundlich. Der Prozess ist klar und effizient, von Zeit zu Zeit mehr regelma?ige Aktionen waren toll. Insgesamt, Cat Spins Casino ist ein Top-Ziel fur Spieler. Au?erdem die Benutzeroberflache ist klar und flussig, zum Bleiben einladt. Ein gro?er Pluspunkt sind die sicheren Krypto-Transaktionen, personliche Vorteile bereitstellen.
Einen Blick werfen|
Ich bin komplett hin und weg von SpinBetter Casino, es fuhlt sich an wie ein Strudel aus Freude. Die Titelvielfalt ist uberwaltigend, mit Spielen, die fur Kryptos optimiert sind. Die Agenten sind blitzschnell, mit praziser Unterstutzung. Der Ablauf ist unkompliziert, gelegentlich mehr Rewards waren ein Plus. Alles in allem, SpinBetter Casino ist eine Plattform, die uberzeugt fur Adrenalin-Sucher ! Au?erdem die Site ist schnell und stylish, erleichtert die gesamte Erfahrung. Ein weiterer Vorteil die Vielfalt an Zahlungsmethoden, die das Spielen noch angenehmer machen.
spinbettercasino.de|
Je suis emerveille par Ruby Slots Casino, c’est une plateforme qui pulse avec energie. Les options sont aussi vastes qu’un horizon, comprenant des jeux optimises pour Bitcoin. Il rend le debut de l’aventure palpitant. Le service client est excellent. Les transactions sont toujours securisees, rarement des recompenses en plus seraient un bonus. Pour faire court, Ruby Slots Casino offre une aventure memorable. A souligner l’interface est lisse et agreable, incite a prolonger le plaisir. Un atout les evenements communautaires vibrants, offre des recompenses regulieres.
Commencer Г naviguer|
Je suis captive par Sugar Casino, il offre une experience dynamique. La gamme est variee et attrayante, proposant des jeux de cartes elegants. 100% jusqu’a 500 € avec des free spins. Le service d’assistance est au point. Le processus est simple et transparent, en revanche des offres plus importantes seraient super. Pour finir, Sugar Casino vaut une exploration vibrante. De surcroit le design est tendance et accrocheur, ce qui rend chaque partie plus fun. Un avantage notable les options de paris sportifs variees, propose des avantages sur mesure.
DГ©couvrir les faits|
Je suis enthousiasme par Sugar Casino, il offre une experience dynamique. On trouve une profusion de jeux palpitants, comprenant des titres adaptes aux cryptomonnaies. Il booste votre aventure des le depart. Le service est disponible 24/7. Les paiements sont surs et fluides, par ailleurs des offres plus consequentes seraient parfaites. En bref, Sugar Casino est un choix parfait pour les joueurs. Pour completer le design est style et moderne, incite a rester plus longtemps. Egalement super les nombreuses options de paris sportifs, propose des avantages sur mesure.
Voir les dГ©tails|
J’ai une affection particuliere pour Ruby Slots Casino, on y trouve une vibe envoutante. La bibliotheque est pleine de surprises, offrant des tables live interactives. Avec des depots fluides. Le support est rapide et professionnel. Les gains sont transferes rapidement, mais encore quelques spins gratuits en plus seraient top. En somme, Ruby Slots Casino merite une visite dynamique. A souligner l’interface est intuitive et fluide, permet une immersion complete. Un plus les options variees pour les paris sportifs, renforce le lien communautaire.
Aller sur le site web|
chery tiggo 4 2025 chery tiggo 8 pro
Ich schatze die Spannung bei Cat Spins Casino, es begeistert mit Dynamik. Das Angebot ist ein Paradies fur Spieler, mit modernen Slots in ansprechenden Designs. Er gibt Ihnen einen Kickstart. Die Mitarbeiter sind schnell und kompetent. Transaktionen sind zuverlassig und effizient, gelegentlich mehr Bonusvielfalt ware ein Vorteil. Im Gro?en und Ganzen, Cat Spins Casino bietet ein unvergessliches Erlebnis. Ubrigens die Navigation ist einfach und klar, eine vollstandige Eintauchen ermoglicht. Ein gro?es Plus sind die sicheren Krypto-Zahlungen, die Gemeinschaft starken.
Heute besuchen|
Обновления по теме здесь: https://wyksa.ru/2025/09/01/lazernaya-epilyaciya-lica-osobennosti-i-preimuschestva-procedury.html
Useful information in one click: https://www.calisthenics-guetersloh.de/2025/10/08/everything-you-need-to-know-about-running-and-2/
Sou louco pela energia de BetorSpin Casino, da uma energia de cassino que e puro pulsar galactico. A gama do cassino e simplesmente uma constelacao de prazeres, com slots de cassino tematicos de espaco sideral. O atendimento ao cliente do cassino e uma estrela-guia, respondendo mais rapido que uma explosao de raios gama. As transacoes do cassino sao simples como uma orbita lunar, mas as ofertas do cassino podiam ser mais generosas. No geral, BetorSpin Casino oferece uma experiencia de cassino que e puro brilho cosmico para os amantes de cassinos online! De bonus a interface do cassino e fluida e reluz como uma constelacao, adiciona um toque de brilho estelar ao cassino.
betorspin pt|
Ich bin beeindruckt von Cat Spins Casino, es verspricht pure Spannung. Die Spiele sind abwechslungsreich und fesselnd, mit eleganten Tischspielen. Er gibt Ihnen einen tollen Boost. Erreichbar 24/7 per Chat oder E-Mail. Transaktionen laufen reibungslos, gelegentlich regelma?igere Promos wurden das Spiel aufwerten. Im Gro?en und Ganzen, Cat Spins Casino sorgt fur kontinuierlichen Spa?. Zusatzlich die Plattform ist visuell beeindruckend, zum Verweilen einladt. Ein starkes Plus die regelma?igen Turniere fur Wettbewerbsspa?, individuelle Vorteile liefern.
Jetzt beitreten|
Ich bin ein gro?er Fan von Cat Spins Casino, es bietet packende Unterhaltung. Die Spielauswahl ist beeindruckend, mit Slots in modernem Look. Er gibt Ihnen einen tollen Boost. Verfugbar 24/7 fur alle Fragen. Die Zahlungen sind sicher und effizient, in manchen Fallen waren mehr Bonusvarianten ein Plus. Zum Schluss, Cat Spins Casino sorgt fur kontinuierlichen Spa?. Daruber hinaus die Seite ist schnell und einladend, jeden Augenblick spannender macht. Ein hervorragendes Plus die haufigen Turniere fur mehr Spa?, zuverlassige Transaktionen sichern.
Erfahren Sie wie|
Ich bin beeindruckt von SpinBetter Casino, es erzeugt eine Spielenergie, die fesselt. Der Katalog ist reichhaltig und variiert, mit dynamischen Tischspielen. Der Kundenservice ist ausgezeichnet, mit praziser Unterstutzung. Die Zahlungen sind sicher und smooth, dennoch mehr abwechslungsreiche Boni waren super. Alles in allem, SpinBetter Casino ist absolut empfehlenswert fur Online-Wetten-Fans ! Zusatzlich das Design ist ansprechend und nutzerfreundlich, fugt Magie hinzu. Ein Pluspunkt ist die schnellen Einzahlungen, die das Spielen noch angenehmer machen.
https://spinbettercasino.de/|
Je suis captive par Sugar Casino, c’est une plateforme qui deborde de dynamisme. Le choix est aussi large qu’un festival, incluant des paris sportifs pleins de vie. Il propulse votre jeu des le debut. Le support est efficace et amical. Les retraits sont ultra-rapides, quelquefois quelques spins gratuits en plus seraient top. En conclusion, Sugar Casino garantit un amusement continu. Pour ajouter la plateforme est visuellement dynamique, ce qui rend chaque partie plus fun. Particulierement cool les options de paris sportifs diversifiees, cree une communaute soudee.
DГ©couvrir|
Je suis captive par Ruby Slots Casino, il cree une experience captivante. Les options de jeu sont incroyablement variees, offrant des tables live interactives. Le bonus de depart est top. Le suivi est d’une precision remarquable. Le processus est simple et transparent, par ailleurs des offres plus genereuses seraient top. Pour finir, Ruby Slots Casino est un choix parfait pour les joueurs. De surcroit le design est moderne et attrayant, ce qui rend chaque moment plus vibrant. Un atout les tournois reguliers pour s’amuser, propose des avantages sur mesure.
Aller voir|
Je ne me lasse pas de Sugar Casino, c’est une plateforme qui pulse avec energie. Les options sont aussi vastes qu’un horizon, avec des machines a sous visuellement superbes. Le bonus d’inscription est attrayant. Disponible a toute heure via chat ou email. Les paiements sont surs et efficaces, bien que plus de promos regulieres dynamiseraient le jeu. Au final, Sugar Casino est un lieu de fun absolu. Notons egalement l’interface est fluide comme une soiree, ce qui rend chaque session plus excitante. Particulierement cool le programme VIP avec des recompenses exclusives, propose des privileges personnalises.
Parcourir le site|
семь кей автоматы casino seven kay онлайн предоставляет круглосуточный доступ к полной библиотеке игр и live-столам.
Ich bin begeistert von der Welt bei Cat Spins Casino, es ladt zu unvergesslichen Momenten ein. Es gibt unzahlige packende Spiele, mit klassischen Tischspielen. Mit schnellen Einzahlungen. Der Support ist effizient und professionell. Transaktionen laufen reibungslos, dennoch mehr Bonusoptionen waren top. In Summe, Cat Spins Casino garantiert langanhaltenden Spa?. Nebenbei ist das Design modern und einladend, was jede Session spannender macht. Ein tolles Feature die lebendigen Community-Events, exklusive Boni bieten.
Das ГјberprГјfen|
Ich bin vollig uberzeugt von Cat Spins Casino, es ladt zu spannenden Spielen ein. Die Spielesammlung ist uberwaltigend, mit eleganten Tischspielen. 100 % bis zu 500 € und Freispiele. Der Kundensupport ist top. Auszahlungen sind zugig und unkompliziert, dennoch regelma?igere Promos wurden das Spiel aufwerten. Insgesamt, Cat Spins Casino ist eine Plattform, die uberzeugt. Zusatzlich die Plattform ist optisch ein Highlight, zum Weiterspielen animiert. Ein bemerkenswertes Extra ist das VIP-Programm mit besonderen Vorteilen, die die Motivation erhohen.
Zur Website gelangen|
Ich bin abhangig von SpinBetter Casino, es liefert ein Abenteuer voller Energie. Der Katalog ist reichhaltig und variiert, mit immersiven Live-Sessions. Die Hilfe ist effizient und pro, garantiert top Hilfe. Die Zahlungen sind sicher und smooth, obwohl die Offers konnten gro?zugiger ausfallen. In Kurze, SpinBetter Casino garantiert hochsten Spa? fur Online-Wetten-Fans ! Zusatzlich die Plattform ist visuell ein Hit, gibt den Anreiz, langer zu bleiben. Hervorzuheben ist die Community-Events, die das Spielen noch angenehmer machen.
https://spinbettercasino.de/|
J’adore la vibe de Sugar Casino, il propose une aventure palpitante. La selection est riche et diversifiee, offrant des sessions live immersives. 100% jusqu’a 500 € avec des free spins. Disponible 24/7 par chat ou email. Les transactions sont toujours fiables, toutefois des recompenses en plus seraient un bonus. En bref, Sugar Casino assure un fun constant. En complement l’interface est lisse et agreable, donne envie de continuer l’aventure. Un bonus les transactions en crypto fiables, qui stimule l’engagement.
Ouvrir maintenant|
Je ne me lasse pas de Ruby Slots Casino, ca offre une experience immersive. La variete des jeux est epoustouflante, avec des slots aux designs captivants. Le bonus d’inscription est attrayant. Le service client est excellent. Les retraits sont ultra-rapides, quelquefois des offres plus importantes seraient super. En somme, Ruby Slots Casino est une plateforme qui fait vibrer. En bonus le site est rapide et engageant, donne envie de continuer l’aventure. A mettre en avant les transactions en crypto fiables, assure des transactions fluides.
Ouvrir maintenant|
Je ne me lasse pas de Sugar Casino, ca invite a plonger dans le fun. Le catalogue de titres est vaste, avec des slots aux designs captivants. Le bonus d’inscription est attrayant. Le support est fiable et reactif. Les transactions sont toujours securisees, a l’occasion des offres plus genereuses rendraient l’experience meilleure. Pour finir, Sugar Casino offre une aventure memorable. En complement la navigation est fluide et facile, donne envie de continuer l’aventure. Un avantage notable les paiements en crypto rapides et surs, qui stimule l’engagement.
Naviguer sur le site|
Ich freue mich riesig uber Cat Spins Casino, es sorgt fur ein fesselndes Erlebnis. Es gibt eine enorme Vielfalt an Spielen, mit traditionellen Tischspielen. Er macht den Start aufregend. Der Service ist absolut zuverlassig. Der Prozess ist klar und effizient, jedoch mehr regelma?ige Aktionen waren toll. Alles in allem, Cat Spins Casino ist ein Muss fur Spielbegeisterte. Zusatzlich die Plattform ist optisch ein Highlight, das Spielvergnugen steigert. Ein super Vorteil ist das VIP-Programm mit besonderen Vorteilen, ma?geschneiderte Privilegien liefern.
Weitergehen|
Hello there! This is my 1st comment here so I just wanted to give a quick shout out and tell you I truly enjoy reading through your posts. Can you recommend any other blogs/websites/forums that cover the same subjects? Thank you!
https://510.com.ua/iak-pravylno-rozihrity-klei-hermetyk-pered-nanesenniam.html
Hi, after reading this remarkable post i am as well delighted to share my experience here with friends.
https://beautybynilda.com/melbet-skachat-na-android-besplatno-poslednyaya-versiya-2025/
Ich liebe die Atmosphare bei Cat Spins Casino, es verspricht pure Spannung. Das Spieleangebot ist reichhaltig und vielfaltig, mit Spielen, die Krypto unterstutzen. 100 % bis zu 500 € plus Freispiele. Der Service ist von hochster Qualitat. Der Prozess ist klar und effizient, trotzdem mehr Promo-Vielfalt ware toll. In Summe, Cat Spins Casino ist ein Highlight fur Casino-Fans. Hinzu kommt ist das Design zeitgema? und attraktiv, zum Bleiben einladt. Ein gro?es Plus die dynamischen Community-Events, ma?geschneiderte Privilegien liefern.
Webseite besuchen|
Ich bin beeindruckt von Cat Spins Casino, es entfuhrt in eine Welt voller Nervenkitzel. Die Spiele sind abwechslungsreich und spannend, mit Spielen fur Kryptowahrungen. Er gibt Ihnen einen tollen Boost. Der Service ist einwandfrei. Auszahlungen sind zugig und unkompliziert, manchmal gro?ere Boni waren ideal. Im Gro?en und Ganzen, Cat Spins Casino bietet ein unvergleichliches Erlebnis. Daruber hinaus die Plattform ist optisch ansprechend, eine Prise Spannung hinzufugt. Ein attraktives Extra die dynamischen Community-Events, kontinuierliche Belohnungen bieten.
Zum Ansehen klicken|
Ich bin komplett hin und weg von SpinBetter Casino, es bietet einen einzigartigen Kick. Der Katalog ist reichhaltig und variiert, mit innovativen Slots und fesselnden Designs. Die Agenten sind blitzschnell, verfugbar rund um die Uhr. Die Transaktionen sind verlasslich, dennoch mehr Rewards waren ein Plus. In Kurze, SpinBetter Casino ist ein Muss fur alle Gamer fur Adrenalin-Sucher ! Au?erdem das Design ist ansprechend und nutzerfreundlich, was jede Session noch besser macht. Hervorzuheben ist die Sicherheit der Daten, die Vertrauen schaffen.
spinbettercasino.de|
Je suis captive par Ruby Slots Casino, c’est une plateforme qui pulse avec energie. Le choix est aussi large qu’un festival, incluant des paris sportifs pleins de vie. Avec des depots fluides. Disponible a toute heure via chat ou email. Les retraits sont ultra-rapides, bien que des bonus plus frequents seraient un hit. Pour finir, Ruby Slots Casino est un lieu de fun absolu. En complement la plateforme est visuellement captivante, ce qui rend chaque moment plus vibrant. Un point cle les tournois frequents pour l’adrenaline, garantit des paiements rapides.
DГ©couvrir les offres|
J’adore le dynamisme de Sugar Casino, on y trouve une vibe envoutante. Il y a un eventail de titres captivants, avec des slots aux graphismes modernes. 100% jusqu’a 500 € plus des tours gratuits. Le support est fiable et reactif. Les retraits sont ultra-rapides, neanmoins des bonus plus frequents seraient un hit. En fin de compte, Sugar Casino assure un fun constant. Notons aussi le site est fluide et attractif, facilite une immersion totale. Un element fort les paiements en crypto rapides et surs, offre des bonus constants.
http://www.sugarcasinologin365fr.com|
Je suis fascine par Sugar Casino, ca invite a l’aventure. Le choix est aussi large qu’un festival, comprenant des jeux optimises pour Bitcoin. Il offre un coup de pouce allechant. Le suivi est d’une precision remarquable. Le processus est simple et transparent, par contre plus de promos regulieres ajouteraient du peps. En resume, Sugar Casino est un incontournable pour les joueurs. Par ailleurs la navigation est simple et intuitive, incite a rester plus longtemps. Egalement top les evenements communautaires engageants, garantit des paiements rapides.
Commencer maintenant|
Je suis accro a Ruby Slots Casino, il offre une experience dynamique. On trouve une gamme de jeux eblouissante, comprenant des titres adaptes aux cryptomonnaies. Avec des depots rapides et faciles. Le service client est de qualite. Les gains sont transferes rapidement, mais des bonus plus varies seraient un plus. En fin de compte, Ruby Slots Casino assure un divertissement non-stop. Ajoutons aussi la plateforme est visuellement dynamique, booste l’excitation du jeu. Egalement top le programme VIP avec des niveaux exclusifs, cree une communaute soudee.
Essayer ceci|
This is really interesting, You are an excessively professional blogger. I’ve joined your feed and look forward to in the hunt for extra of your excellent post. Additionally, I’ve shared your website in my social networks
https://www.playsure.com.ng/2025/10/11/sayt-bk-melbet-2025/
Ich schatze die Energie bei Cat Spins Casino, es verspricht ein einzigartiges Abenteuer. Es gibt unzahlige packende Spiele, mit Spielautomaten in beeindruckenden Designs. Er sorgt fur einen starken Einstieg. Die Mitarbeiter sind immer hilfsbereit. Der Prozess ist einfach und transparent, dennoch mehr Aktionen waren ein Gewinn. Alles in allem, Cat Spins Casino sorgt fur kontinuierlichen Spa?. Au?erdem die Oberflache ist glatt und benutzerfreundlich, eine Prise Stil hinzufugt. Ein bemerkenswertes Extra sind die sicheren Krypto-Transaktionen, reibungslose Transaktionen sichern.
Jetzt zugreifen|
Pretty! This was an extremely wonderful article. Thank you for supplying this information.
https://terataiputihglobal.info/2025/10/16/melbet-skachat-na-android-s-oficialnogo-sajta-2025/
Operation Game Canada: A classic, fun-filled board game where players test their precision by removing ailments from the patient without triggering the buzzer: Operation game for kids Canada
J’ai un faible pour Wild Robin Casino, il offre une experience dynamique. Les options sont aussi vastes qu’un horizon, comprenant des jeux optimises pour Bitcoin. 100% jusqu’a 500 € plus des tours gratuits. Le support est pro et accueillant. Les paiements sont securises et rapides, quelquefois plus de promos regulieres dynamiseraient le jeu. En bref, Wild Robin Casino merite un detour palpitant. En complement le design est moderne et energique, ajoute une vibe electrisante. Particulierement attrayant les transactions en crypto fiables, garantit des paiements securises.
Commencer Г naviguer|
J’ai une passion debordante pour Frumzi Casino, ca offre un plaisir vibrant. Les jeux proposes sont d’une diversite folle, avec des slots aux graphismes modernes. Avec des transactions rapides. Les agents sont rapides et pros. Les paiements sont surs et fluides, neanmoins des offres plus consequentes seraient parfaites. Pour conclure, Frumzi Casino merite une visite dynamique. A souligner l’interface est simple et engageante, ce qui rend chaque session plus palpitante. A noter les evenements communautaires pleins d’energie, cree une communaute vibrante.
Voir la page|
J’adore le dynamisme de Wild Robin Casino, il procure une sensation de frisson. Il y a une abondance de jeux excitants, avec des slots aux graphismes modernes. Avec des transactions rapides. Le service client est de qualite. Les retraits sont fluides et rapides, occasionnellement des bonus diversifies seraient un atout. Au final, Wild Robin Casino merite un detour palpitant. A noter l’interface est intuitive et fluide, amplifie le plaisir de jouer. Un avantage les nombreuses options de paris sportifs, propose des avantages sur mesure.
Explorer le site web|
Je suis emerveille par Cheri Casino, ca donne une vibe electrisante. On trouve une gamme de jeux eblouissante, offrant des tables live interactives. Avec des depots fluides. Le support est fiable et reactif. Les transactions sont fiables et efficaces, par moments des offres plus consequentes seraient parfaites. En bref, Cheri Casino est une plateforme qui fait vibrer. A souligner le design est moderne et attrayant, ce qui rend chaque session plus palpitante. Un bonus les options variees pour les paris sportifs, cree une communaute vibrante.
Obtenir des infos|
Je suis enthousiaste a propos de Cheri Casino, il propose une aventure palpitante. La gamme est variee et attrayante, comprenant des jeux optimises pour Bitcoin. Le bonus initial est super. Le service d’assistance est au point. Le processus est clair et efficace, toutefois quelques spins gratuits en plus seraient top. En somme, Cheri Casino offre une aventure inoubliable. En plus l’interface est lisse et agreable, amplifie le plaisir de jouer. Particulierement cool les evenements communautaires engageants, offre des bonus exclusifs.
VГ©rifier le site|
Je suis captive par Instant Casino, il procure une sensation de frisson. Il y a une abondance de jeux excitants, offrant des experiences de casino en direct. Il donne un avantage immediat. Les agents repondent avec rapidite. Le processus est transparent et rapide, rarement quelques spins gratuits en plus seraient top. En fin de compte, Instant Casino est un endroit qui electrise. En plus le site est rapide et engageant, amplifie l’adrenaline du jeu. Un avantage notable les transactions en crypto fiables, cree une communaute vibrante.
DГ©couvrir dГЁs maintenant|
Je suis enthousiaste a propos de Instant Casino, ca donne une vibe electrisante. Le choix est aussi large qu’un festival, avec des slots aux graphismes modernes. Avec des transactions rapides. Le suivi est d’une fiabilite exemplaire. Les paiements sont securises et instantanes, par moments des bonus varies rendraient le tout plus fun. Globalement, Instant Casino vaut une exploration vibrante. De plus l’interface est fluide comme une soiree, apporte une touche d’excitation. Egalement genial les tournois frequents pour l’adrenaline, offre des recompenses regulieres.
https://instantcasinobonusfr.com/|
Today, I went to the beachfront with my children. I found a sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She placed the shell to her ear and screamed. There was a hermit crab inside and it pinched her ear. She never wants to go back! LoL I know this is entirely off topic but I had to tell someone!
https://wp.alisontravelgroup.com/без-рубрики/skachat-prilozhenie-melbet-2025/
Je suis emerveille par Wild Robin Casino, ca transporte dans un univers de plaisirs. On trouve une gamme de jeux eblouissante, proposant des jeux de table classiques. 100% jusqu’a 500 € avec des spins gratuits. Les agents sont toujours la pour aider. Les gains arrivent en un eclair, bien que plus de promos regulieres dynamiseraient le jeu. En resume, Wild Robin Casino offre une experience hors du commun. Ajoutons que le design est moderne et attrayant, amplifie le plaisir de jouer. Particulierement attrayant le programme VIP avec des niveaux exclusifs, offre des recompenses regulieres.
AccГ©der maintenant|
Je suis fascine par Wild Robin Casino, il offre une experience dynamique. La selection est riche et diversifiee, proposant des jeux de table classiques. Le bonus de bienvenue est genereux. Les agents repondent avec rapidite. Les retraits sont simples et rapides, neanmoins plus de promotions frequentes boosteraient l’experience. Au final, Wild Robin Casino vaut une visite excitante. En extra la navigation est simple et intuitive, ce qui rend chaque session plus excitante. Egalement excellent les evenements communautaires dynamiques, cree une communaute soudee.
http://www.wildrobincasinofr.com|
J’ai un veritable coup de c?ur pour Cheri Casino, ca transporte dans un univers de plaisirs. La variete des jeux est epoustouflante, incluant des paris sportifs pleins de vie. Avec des depots fluides. Le service client est excellent. Les paiements sont surs et efficaces, par moments plus de promotions frequentes boosteraient l’experience. Pour conclure, Cheri Casino offre une aventure inoubliable. Ajoutons aussi la navigation est fluide et facile, ajoute une touche de dynamisme. Un avantage notable les evenements communautaires engageants, qui booste la participation.
DГ©couvrir dГЁs maintenant|
J’adore l’ambiance electrisante de Frumzi Casino, ca pulse comme une soiree animee. Il y a un eventail de titres captivants, offrant des sessions live palpitantes. Il amplifie le plaisir des l’entree. Le support est pro et accueillant. Les gains sont transferes rapidement, quelquefois des bonus diversifies seraient un atout. En bref, Frumzi Casino assure un fun constant. Pour completer la navigation est claire et rapide, facilite une immersion totale. A mettre en avant les tournois reguliers pour s’amuser, garantit des paiements rapides.
Entrer sur le site|
Je suis emerveille par Instant Casino, ca invite a plonger dans le fun. Il y a une abondance de jeux excitants, proposant des jeux de casino traditionnels. Il donne un elan excitant. Le service client est de qualite. Les transactions sont fiables et efficaces, par moments des bonus varies rendraient le tout plus fun. Pour finir, Instant Casino est un lieu de fun absolu. Notons egalement la navigation est claire et rapide, amplifie le plaisir de jouer. Un bonus les options de paris sportifs diversifiees, assure des transactions fiables.
Aller au site|
https://evobizepl.com
надежное казино
The Inheritance Games Canada: A thrilling mystery game where players unravel secrets, solve puzzles, and compete for a billionaire’s fortune. Perfect for fans of strategy and suspense: Barnes & Noble Inheritance Games
http://houmy.ru/
Je suis fascine par Frumzi Casino, il procure une sensation de frisson. Les jeux proposes sont d’une diversite folle, avec des machines a sous visuellement superbes. Le bonus initial est super. Le service client est excellent. Les paiements sont securises et instantanes, de temps en temps quelques free spins en plus seraient bienvenus. Pour faire court, Frumzi Casino assure un divertissement non-stop. A signaler la plateforme est visuellement electrisante, ajoute une vibe electrisante. A souligner le programme VIP avec des avantages uniques, garantit des paiements rapides.
https://frumzicasinofr.com/|
Je suis bluffe par Wild Robin Casino, c’est une plateforme qui deborde de dynamisme. Le choix est aussi large qu’un festival, offrant des tables live interactives. Il donne un avantage immediat. Les agents sont toujours la pour aider. Les gains sont transferes rapidement, malgre tout plus de promos regulieres dynamiseraient le jeu. Pour finir, Wild Robin Casino est une plateforme qui pulse. Ajoutons aussi le site est rapide et style, incite a prolonger le plaisir. Egalement excellent les options variees pour les paris sportifs, cree une communaute vibrante.
Plonger dedans|
Je suis enthousiasme par Frumzi Casino, ca invite a plonger dans le fun. Le catalogue de titres est vaste, offrant des sessions live palpitantes. 100% jusqu’a 500 € + tours gratuits. Les agents repondent avec efficacite. Les paiements sont surs et efficaces, par contre des offres plus consequentes seraient parfaites. En somme, Frumzi Casino vaut une visite excitante. Notons egalement la navigation est fluide et facile, ajoute une vibe electrisante. Un point fort les evenements communautaires dynamiques, qui booste la participation.
Cliquer pour voir|
Je suis emerveille par Instant Casino, ca offre une experience immersive. On trouve une gamme de jeux eblouissante, offrant des tables live interactives. Le bonus de depart est top. Le suivi est d’une fiabilite exemplaire. Les transactions sont fiables et efficaces, cependant des recompenses additionnelles seraient ideales. En bref, Instant Casino est un immanquable pour les amateurs. Notons aussi l’interface est simple et engageante, permet une plongee totale dans le jeu. A signaler les paiements en crypto rapides et surs, offre des bonus exclusifs.
Instant|
Je suis sous le charme de Wild Robin Casino, on y trouve une energie contagieuse. Le choix est aussi large qu’un festival, proposant des jeux de table sophistiques. Le bonus de bienvenue est genereux. Le service client est excellent. Les retraits sont simples et rapides, en revanche des bonus varies rendraient le tout plus fun. Au final, Wild Robin Casino offre une aventure memorable. Pour ajouter la plateforme est visuellement vibrante, amplifie le plaisir de jouer. Particulierement interessant les paiements securises en crypto, offre des recompenses continues.
DГ©couvrir plus|
J’ai un faible pour Instant Casino, il procure une sensation de frisson. La bibliotheque est pleine de surprises, avec des machines a sous visuellement superbes. 100% jusqu’a 500 € avec des spins gratuits. Le support est efficace et amical. Les transactions sont d’une fiabilite absolue, toutefois quelques tours gratuits en plus seraient geniaux. En fin de compte, Instant Casino offre une aventure inoubliable. A mentionner la plateforme est visuellement electrisante, facilite une experience immersive. Particulierement attrayant le programme VIP avec des avantages uniques, assure des transactions fiables.
Lire les dГ©tails|
Je suis completement seduit par Instant Casino, il procure une sensation de frisson. Le choix est aussi large qu’un festival, incluant des paris sportifs en direct. Le bonus de bienvenue est genereux. Disponible 24/7 pour toute question. Les paiements sont securises et instantanes, de temps en temps des offres plus genereuses rendraient l’experience meilleure. En resume, Instant Casino garantit un plaisir constant. A signaler le site est rapide et style, ce qui rend chaque session plus excitante. Egalement super les evenements communautaires vibrants, offre des recompenses continues.
Regarder de plus prГЁs|
Je suis accro a Frumzi Casino, on ressent une ambiance de fete. Les options sont aussi vastes qu’un horizon, proposant des jeux de table sophistiques. 100% jusqu’a 500 € + tours gratuits. Le service d’assistance est au point. Les gains sont transferes rapidement, parfois des offres plus genereuses seraient top. Pour conclure, Frumzi Casino est un lieu de fun absolu. Par ailleurs la navigation est simple et intuitive, donne envie de continuer l’aventure. Egalement excellent les tournois frequents pour l’adrenaline, renforce la communaute.
En savoir plus|
I’d like to find out more? I’d love to find out more details.
skla
https://yurhelp.in.ua/
Paris sportifs avec 1xbet apk rdc : pre-match & live, statistiques, cash-out, builder de paris. Bonus d’inscription, programme fidelite, appli mobile. Depots via M-Pesa/Airtel Money. Informez-vous sur la reglementation. 18+, jouez avec moderation.
Plateforme parifoot rdc : pronos fiables, comparateur de cotes multi-books, tendances du marche, cash-out, statistiques avancees. Depots via M-Pesa/Airtel Money, support francophone, retraits securises. Pariez avec moderation.
Оформите онлайн-займ https://zaimy-90.ru без визита в офис: достаточно паспорта, проверка за минуты. Выдача на карту, кошелёк или счёт. Прозрачный договор, напоминания о платеже, безопасность данных, акции для новых клиентов. Сравните предложения и выберите выгодно.
Welcome to the Granescorts elite escort agency in Dubai!
Each client is immensely important to us, so for over 15 years we have been delighting you with the highest level of service, exclusive escort services and the largest and most up-to-date catalog of elite girls and TOP models.
A huge variety of the most Dubai high class escort girls can be found only with us – blondes, brunettes, redheads, slim, curvy, fitness girls, athletes, photo models, nude models, porn models, famous girls from Instagram, as well as unique options – twins and even triplets! Therefore, with undisguised pride, we present you our TOP escort models! You can verify this right now by looking at the profile data or visiting the catalog page, which features the most beautiful and sexy girls from Dubai and beyond.
Сразу к лучшему здесь: https://buybuyviamen.com
My spouse and I absolutely love your blog and find almost all of your post’s to be just what I’m looking for. Do you offer guest writers to write content in your case? I wouldn’t mind producing a post or elaborating on most of the subjects you write regarding here. Again, awesome weblog!
skla
J’ai un veritable coup de c?ur pour Wild Robin Casino, on y trouve une vibe envoutante. On trouve une gamme de jeux eblouissante, avec des slots aux graphismes modernes. Il donne un avantage immediat. Le suivi est d’une precision remarquable. Le processus est transparent et rapide, cependant quelques free spins en plus seraient bienvenus. Dans l’ensemble, Wild Robin Casino garantit un plaisir constant. D’ailleurs la navigation est claire et rapide, permet une plongee totale dans le jeu. Un point fort les paiements en crypto rapides et surs, cree une communaute soudee.
http://www.wildrobincasinopromocodefr.com|
Je suis captive par Cheri Casino, on ressent une ambiance festive. Les jeux proposes sont d’une diversite folle, comprenant des titres adaptes aux cryptomonnaies. Il rend le debut de l’aventure palpitant. Les agents repondent avec efficacite. Les gains arrivent sans delai, toutefois des recompenses supplementaires dynamiseraient le tout. En bref, Cheri Casino vaut une exploration vibrante. Par ailleurs la plateforme est visuellement electrisante, donne envie de continuer l’aventure. Particulierement fun les nombreuses options de paris sportifs, assure des transactions fiables.
Commencer Г lire|
J’adore le dynamisme de Frumzi Casino, c’est une plateforme qui deborde de dynamisme. Il y a une abondance de jeux excitants, proposant des jeux de table sophistiques. Le bonus de bienvenue est genereux. Le suivi est impeccable. Les retraits sont simples et rapides, rarement plus de promos regulieres dynamiseraient le jeu. En somme, Frumzi Casino offre une aventure memorable. A mentionner la navigation est fluide et facile, amplifie l’adrenaline du jeu. Egalement super le programme VIP avec des avantages uniques, offre des recompenses continues.
Regarder de plus prГЁs|
J’ai une affection particuliere pour Instant Casino, ca offre un plaisir vibrant. Le catalogue de titres est vaste, incluant des options de paris sportifs dynamiques. Avec des transactions rapides. Le service client est excellent. Les transactions sont toujours securisees, neanmoins des bonus plus varies seraient un plus. Pour conclure, Instant Casino est un immanquable pour les amateurs. Notons aussi le site est rapide et style, facilite une experience immersive. Un point fort les options de paris sportifs variees, cree une communaute vibrante.
DГ©couvrir la page|
рейтинг казино
Je suis sous le charme de Wild Robin Casino, il procure une sensation de frisson. La gamme est variee et attrayante, offrant des experiences de casino en direct. Il amplifie le plaisir des l’entree. Le support est rapide et professionnel. Les transactions sont toujours securisees, toutefois plus de promotions frequentes boosteraient l’experience. Dans l’ensemble, Wild Robin Casino offre une aventure memorable. De plus le design est moderne et energique, incite a prolonger le plaisir. Particulierement attrayant les paiements en crypto rapides et surs, qui booste la participation.
Voir le site|
Je suis emerveille par Instant Casino, ca donne une vibe electrisante. La bibliotheque de jeux est captivante, comprenant des titres adaptes aux cryptomonnaies. Avec des depots rapides et faciles. Les agents repondent avec efficacite. Le processus est transparent et rapide, bien que des recompenses supplementaires seraient parfaites. En resume, Instant Casino offre une experience inoubliable. En complement l’interface est lisse et agreable, donne envie de prolonger l’aventure. Un point fort le programme VIP avec des privileges speciaux, garantit des paiements securises.
Explorer la page|
J’adore le dynamisme de Instant Casino, on y trouve une vibe envoutante. Il y a un eventail de titres captivants, incluant des paris sportifs pleins de vie. Il donne un avantage immediat. Le support est pro et accueillant. Les transactions sont d’une fiabilite absolue, malgre tout quelques tours gratuits en plus seraient geniaux. En conclusion, Instant Casino est un immanquable pour les amateurs. A signaler la navigation est intuitive et lisse, donne envie de prolonger l’aventure. Egalement excellent les evenements communautaires pleins d’energie, qui motive les joueurs.
Cliquer maintenant|
Je suis fascine par Cheri Casino, on ressent une ambiance de fete. La selection de jeux est impressionnante, offrant des experiences de casino en direct. 100% jusqu’a 500 € plus des tours gratuits. Le service client est excellent. Les retraits sont lisses comme jamais, par ailleurs des offres plus importantes seraient super. En conclusion, Cheri Casino offre une experience inoubliable. Pour completer la navigation est claire et rapide, apporte une energie supplementaire. A signaler les evenements communautaires vibrants, renforce le lien communautaire.
Plongez-y|
Je suis bluffe par Frumzi Casino, on ressent une ambiance festive. Les jeux proposes sont d’une diversite folle, incluant des paris sportifs pleins de vie. 100% jusqu’a 500 € + tours gratuits. Le suivi est impeccable. Les paiements sont securises et instantanes, de temps en temps quelques free spins en plus seraient bienvenus. Pour faire court, Frumzi Casino offre une aventure inoubliable. En plus la navigation est fluide et facile, permet une immersion complete. A signaler les paiements en crypto rapides et surs, offre des bonus constants.
Parcourir le site|
How to win in Calgary Lottery: Boost your chances by playing consistently, joining lottery pools, and choosing less popular combinations. Remember, winning requires luck and responsible play: best ways to win money in Calgary
Hello it’s me, I am also visiting this website daily, this site is truly nice and the users are really sharing nice thoughts.
сайт кракена
Je suis totalement conquis par Wild Robin Casino, on ressent une ambiance festive. Le catalogue de titres est vaste, proposant des jeux de table classiques. 100% jusqu’a 500 € avec des free spins. Le support est efficace et amical. Les paiements sont securises et instantanes, neanmoins quelques free spins en plus seraient bienvenus. Globalement, Wild Robin Casino merite un detour palpitant. En extra le site est rapide et engageant, permet une immersion complete. Un avantage le programme VIP avec des avantages uniques, qui dynamise l’engagement.
Cliquer pour voir|
J’adore l’energie de Cheri Casino, ca pulse comme une soiree animee. Le catalogue est un paradis pour les joueurs, avec des machines a sous visuellement superbes. Il amplifie le plaisir des l’entree. Les agents sont toujours la pour aider. Les paiements sont surs et fluides, a l’occasion des bonus plus frequents seraient un hit. En bref, Cheri Casino merite un detour palpitant. Notons egalement le site est rapide et immersif, permet une immersion complete. Un atout les evenements communautaires vibrants, renforce la communaute.
https://casinocherifr.com/|
J’adore l’ambiance electrisante de Frumzi Casino, ca invite a l’aventure. Il y a un eventail de titres captivants, offrant des experiences de casino en direct. Il rend le debut de l’aventure palpitant. Le support client est irreprochable. Le processus est transparent et rapide, par ailleurs des bonus varies rendraient le tout plus fun. Au final, Frumzi Casino est un immanquable pour les amateurs. En plus le site est rapide et style, amplifie l’adrenaline du jeu. A noter les tournois reguliers pour s’amuser, qui stimule l’engagement.
DГ©couvrir les offres|
J’ai un veritable coup de c?ur pour Instant Casino, c’est un lieu ou l’adrenaline coule a flots. Le catalogue est un tresor de divertissements, comprenant des titres adaptes aux cryptomonnaies. Il booste votre aventure des le depart. Le suivi est toujours au top. Les transactions sont toujours fiables, a l’occasion des bonus varies rendraient le tout plus fun. En bref, Instant Casino est un immanquable pour les amateurs. Pour ajouter le site est fluide et attractif, apporte une energie supplementaire. Un plus les competitions regulieres pour plus de fun, cree une communaute vibrante.
Parcourir le site|
J’ai une passion debordante pour Cheri Casino, c’est une plateforme qui pulse avec energie. Le choix de jeux est tout simplement enorme, comprenant des jeux crypto-friendly. Il offre un coup de pouce allechant. Le support client est irreprochable. Les transactions sont toujours securisees, de temps en temps quelques free spins en plus seraient bienvenus. Globalement, Cheri Casino garantit un plaisir constant. En extra l’interface est fluide comme une soiree, incite a rester plus longtemps. Un element fort les competitions regulieres pour plus de fun, qui booste la participation.
Essayer maintenant|
Je suis accro a Wild Robin Casino, ca transporte dans un monde d’excitation. La bibliotheque de jeux est captivante, offrant des sessions live palpitantes. Avec des depots instantanes. Les agents sont rapides et pros. Les transactions sont toujours securisees, de temps en temps des recompenses supplementaires dynamiseraient le tout. En somme, Wild Robin Casino vaut une exploration vibrante. En bonus la navigation est simple et intuitive, donne envie de continuer l’aventure. Egalement super le programme VIP avec des privileges speciaux, propose des avantages sur mesure.
Obtenir les dГ©tails|
Je suis enthousiasme par Cheri Casino, ca invite a l’aventure. La bibliotheque est pleine de surprises, comprenant des jeux compatibles avec les cryptos. Avec des depots rapides et faciles. Disponible 24/7 par chat ou email. Les retraits sont lisses comme jamais, de temps en temps des bonus plus frequents seraient un hit. Dans l’ensemble, Cheri Casino merite une visite dynamique. Pour couronner le tout la navigation est simple et intuitive, incite a prolonger le plaisir. Egalement genial les options de paris sportifs diversifiees, offre des bonus constants.
Consulter les dГ©tails|
Je suis enthousiaste a propos de Betzino Casino, ca offre un plaisir vibrant. Le choix est aussi large qu’un festival, avec des slots aux designs captivants. Avec des transactions rapides. Le support est rapide et professionnel. Les transactions sont toujours fiables, par moments des recompenses additionnelles seraient ideales. En somme, Betzino Casino assure un fun constant. Ajoutons que la navigation est fluide et facile, facilite une experience immersive. A noter les options variees pour les paris sportifs, cree une communaute soudee.
Aller sur le site web|
Je suis bluffe par Viggoslots Casino, ca transporte dans un univers de plaisirs. Les options sont aussi vastes qu’un horizon, incluant des paris sur des evenements sportifs. Il donne un avantage immediat. Disponible a toute heure via chat ou email. Les transactions sont toujours fiables, mais encore des recompenses en plus seraient un bonus. En somme, Viggoslots Casino est un choix parfait pour les joueurs. En plus le design est tendance et accrocheur, ce qui rend chaque partie plus fun. Un atout les options de paris sportifs diversifiees, garantit des paiements securises.
Obtenir les dГ©tails|
Je suis bluffe par Betzino Casino, ca invite a plonger dans le fun. La selection est riche et diversifiee, proposant des jeux de cartes elegants. Avec des depots rapides et faciles. Disponible 24/7 par chat ou email. Les transactions sont fiables et efficaces, malgre tout quelques tours gratuits supplementaires seraient cool. Globalement, Betzino Casino est un choix parfait pour les joueurs. De surcroit la navigation est fluide et facile, ajoute une vibe electrisante. Un plus les evenements communautaires vibrants, qui dynamise l’engagement.
Commencer Г dГ©couvrir|
Je ne me lasse pas de Viggoslots Casino, ca invite a plonger dans le fun. La gamme est variee et attrayante, avec des slots aux graphismes modernes. Le bonus de depart est top. Disponible 24/7 par chat ou email. Les transactions sont d’une fiabilite absolue, quelquefois des offres plus consequentes seraient parfaites. Globalement, Viggoslots Casino est un incontournable pour les joueurs. Pour ajouter le design est style et moderne, ajoute une vibe electrisante. Particulierement cool les tournois frequents pour l’adrenaline, qui booste la participation.
DГ©couvrir dГЁs maintenant|
J’adore l’energie de Vbet Casino, il propose une aventure palpitante. Les titres proposes sont d’une richesse folle, proposant des jeux de casino traditionnels. Il offre un demarrage en fanfare. Les agents repondent avec efficacite. Le processus est transparent et rapide, cependant des bonus diversifies seraient un atout. Globalement, Vbet Casino assure un fun constant. Notons aussi la navigation est simple et intuitive, apporte une energie supplementaire. Particulierement fun les evenements communautaires pleins d’energie, qui dynamise l’engagement.
Passer à l’action|
J’adore l’energie de Vbet Casino, il cree un monde de sensations fortes. La selection est riche et diversifiee, offrant des tables live interactives. Il propulse votre jeu des le debut. Le support client est irreprochable. Les retraits sont fluides et rapides, malgre tout des recompenses supplementaires dynamiseraient le tout. Pour conclure, Vbet Casino est un must pour les passionnes. Pour ajouter le site est rapide et style, facilite une immersion totale. Un point fort les tournois frequents pour l’adrenaline, renforce le lien communautaire.
Cliquer maintenant|
Je suis captive par Cheri Casino, il procure une sensation de frisson. Les options de jeu sont incroyablement variees, avec des slots aux designs captivants. 100% jusqu’a 500 € avec des spins gratuits. Le support est fiable et reactif. Le processus est transparent et rapide, de temps en temps des recompenses additionnelles seraient ideales. En bref, Cheri Casino garantit un plaisir constant. Ajoutons aussi l’interface est simple et engageante, apporte une energie supplementaire. Un atout les paiements en crypto rapides et surs, qui stimule l’engagement.
Commencer Г naviguer|
J’ai un faible pour Posido Casino, ca offre un plaisir vibrant. La variete des jeux est epoustouflante, avec des machines a sous visuellement superbes. Avec des depots fluides. Le support est pro et accueillant. Les paiements sont surs et fluides, par ailleurs plus de promotions variees ajouteraient du fun. Pour conclure, Posido Casino offre une aventure inoubliable. Ajoutons que le design est style et moderne, donne envie de prolonger l’aventure. Un point fort le programme VIP avec des privileges speciaux, assure des transactions fiables.
Continuer ici|
J’adore le dynamisme de Posido Casino, il procure une sensation de frisson. Le choix de jeux est tout simplement enorme, avec des slots aux graphismes modernes. Avec des depots instantanes. Les agents repondent avec efficacite. Les transactions sont fiables et efficaces, rarement des bonus plus frequents seraient un hit. Pour conclure, Posido Casino est un must pour les passionnes. Ajoutons que le design est style et moderne, ce qui rend chaque partie plus fun. A souligner les nombreuses options de paris sportifs, offre des bonus constants.
Lire la suite|
https://медоптима.рф/
DRINKIO стал моим любимым сервисом доставки. Всё работает идеально, без сбоев. Курьеры приезжают вовремя, заказ аккуратно упакован. Удобно, что доставка доступна 24/7. Отличный уровень обслуживания https://drinkio105.ru/catalog/category/dzhin/
https://nicemerch.ru/
Оформите займ https://zaimy-69.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
J’adore l’energie de Betzino Casino, il cree une experience captivante. La bibliotheque de jeux est captivante, avec des machines a sous visuellement superbes. Il booste votre aventure des le depart. Le suivi est d’une precision remarquable. Les retraits sont ultra-rapides, par contre des offres plus genereuses seraient top. En somme, Betzino Casino garantit un amusement continu. Ajoutons que le site est rapide et engageant, donne envie de prolonger l’aventure. A mettre en avant le programme VIP avec des avantages uniques, propose des avantages sur mesure.
Lancer le site|
нарколог на дом цена
бездепозитные бонусы казино с выводом
Оформите займ https://zaimy-88.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
Hi there! Would you mind if I share your blog with my zynga group? There’s a lot of folks that I think would really enjoy your content. Please let me know. Thank you
https://notfaelleworms.de/
Thank you for another informative site. The place else may I get that type of info written in such a perfect way? I’ve a challenge that I’m just now working on, and I’ve been at the look out for such info.
https://volksmeter
Can I simply say what a comfort to uncover somebody that actually knows what they’re talking about on the web. You actually understand how to bring a problem to light and make it important. A lot more people must look at this and understand this side of the story. I was surprised that you aren’t more popular since you certainly have the gift.
https://www.hans-g-lehmann.com/
WOW just what I was searching for. Came here by searching for %keyword%
https://www.kr-grillhouse.de/
Hello friends, fastidious post and pleasant urging commented at this place, I am in fact enjoying by these.
https://www.mtm-trucks-and-parts.com/
http://houmy.ru/
https://internet-leman.ru/
клиника вывод из запоя [url=www.narkologicheskaya-klinika-28.ru/]клиника вывод из запоя[/url] .
вывод из запоя в москве [url=https://narkologicheskaya-klinika-27.ru/]вывод из запоя в москве[/url] .
наркология в москве [url=http://www.narkologicheskaya-klinika-23.ru]http://www.narkologicheskaya-klinika-23.ru[/url] .
цена ремонта подвала [url=http://www.gidroizolyaciya-cena-7.ru]http://www.gidroizolyaciya-cena-7.ru[/url] .
1 x bet [url=https://1xbet-17.com/]1 x bet[/url] .
Entdecken Sie die besten Weinverkostungen in Wien auf [url=https://weinverkostung.neocities.org/]wine tasting vienna[/url].
In der Stadt finden sich zahlreiche Weinguter, die eine lange Geschichte haben.
Die Weinverkostungen in Wien sind perfekt fur Kenner und Neulinge. Dabei lernen Gaste die Besonderheiten der regionalen Rebsorten kennen.
#### **2. Die besten Orte fur Weinverkostungen**
In Wien gibt es zahlreiche Lokale und Weinguter, die Verkostungen anbieten. Das bekannte Heurigenviertel in Grinzing ladt zu gemutlichen Verkostungen ein.
Einige Winzer veranstalten Fuhrungen durch ihre Kellereien. Oft werden auch seltene Weine vorgestellt, die nur lokal erhaltlich sind.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Wiener Weine sind vor allem fur ihre Vielfalt bekannt. Rote Weine wie der Blaue Zweigelt gewinnen immer mehr an Beliebtheit.
Die Bodenbeschaffenheit und das Klima pragen den Geschmack. Die mineralischen Noten der Wiener Weine sind besonders ausgepragt.
#### **4. Tipps fur eine gelungene Weinverkostung**
Eine gute Vorbereitung macht die Verkostung noch angenehmer. Wasser und Brot helfen, den Gaumen zwischen verschiedenen Weinen zu neutralisieren.
Gruppenverkostungen bringen zusatzlichen Spa?. Ein Weinjournal kann helfen, personliche Favoriten festzuhalten.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
In der Stadt finden sich zahlreiche Weinguter, die eine lange Geschichte haben.
#### **2. Die besten Orte fur Weinverkostungen**
Dabei erfahren Besucher mehr uber die Herstellung der Weine.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Die Bodenbeschaffenheit und das Klima pragen den Geschmack.
#### **4. Tipps fur eine gelungene Weinverkostung**
Gruppenverkostungen bringen zusatzlichen Spa?.
Koh Lanta Thailand
Je suis epate par Viggoslots Casino, c’est un lieu ou l’adrenaline coule a flots. Les options de jeu sont incroyablement variees, comprenant des jeux compatibles avec les cryptos. Le bonus de bienvenue est genereux. Le support est rapide et professionnel. Le processus est simple et transparent, toutefois des recompenses en plus seraient un bonus. Globalement, Viggoslots Casino est une plateforme qui pulse. A noter la plateforme est visuellement dynamique, ajoute une touche de dynamisme. Particulierement fun les evenements communautaires vibrants, renforce la communaute.
Apprendre comment|
Je suis emerveille par Betzino Casino, il cree un monde de sensations fortes. Les options de jeu sont infinies, offrant des experiences de casino en direct. Il offre un coup de pouce allechant. Les agents sont toujours la pour aider. Les retraits sont simples et rapides, cependant quelques tours gratuits supplementaires seraient cool. Au final, Betzino Casino garantit un plaisir constant. Notons egalement le design est moderne et energique, facilite une immersion totale. A noter les evenements communautaires vibrants, propose des privileges personnalises.
Naviguer sur le site|
Je suis completement seduit par Viggoslots Casino, ca transporte dans un univers de plaisirs. Le choix de jeux est tout simplement enorme, offrant des sessions live immersives. Il amplifie le plaisir des l’entree. Les agents repondent avec rapidite. Les paiements sont securises et rapides, a l’occasion des recompenses additionnelles seraient ideales. Globalement, Viggoslots Casino offre une aventure memorable. A souligner la plateforme est visuellement dynamique, apporte une touche d’excitation. Egalement excellent les options variees pour les paris sportifs, qui stimule l’engagement.
Voir les dГ©tails|
J’adore la vibe de Betzino Casino, ca invite a l’aventure. Le choix est aussi large qu’un festival, avec des slots aux graphismes modernes. Il propulse votre jeu des le debut. Le support client est irreprochable. Les gains arrivent en un eclair, quelquefois des bonus varies rendraient le tout plus fun. Pour finir, Betzino Casino offre une experience hors du commun. A noter le design est tendance et accrocheur, apporte une energie supplementaire. Egalement excellent les competitions regulieres pour plus de fun, offre des recompenses continues.
Poursuivre la lecture|
J’adore l’ambiance electrisante de Vbet Casino, il offre une experience dynamique. Les titres proposes sont d’une richesse folle, comprenant des jeux crypto-friendly. Il offre un demarrage en fanfare. Le support client est irreprochable. Les gains arrivent en un eclair, mais plus de promos regulieres dynamiseraient le jeu. En resume, Vbet Casino est un lieu de fun absolu. D’ailleurs l’interface est simple et engageante, incite a rester plus longtemps. Un bonus les transactions crypto ultra-securisees, qui stimule l’engagement.
Regarder de plus prГЁs|
Je suis emerveille par Vbet Casino, c’est un lieu ou l’adrenaline coule a flots. Les options sont aussi vastes qu’un horizon, avec des slots aux designs captivants. Il offre un demarrage en fanfare. Le suivi est d’une fiabilite exemplaire. Les retraits sont lisses comme jamais, rarement plus de promotions variees ajouteraient du fun. Globalement, Vbet Casino offre une experience hors du commun. En bonus la navigation est intuitive et lisse, apporte une energie supplementaire. A mettre en avant les paiements securises en crypto, cree une communaute vibrante.
Obtenir les dГ©tails|
J’adore le dynamisme de Posido Casino, on y trouve une vibe envoutante. Les jeux proposes sont d’une diversite folle, offrant des sessions live immersives. Le bonus initial est super. Disponible 24/7 par chat ou email. Le processus est simple et transparent, occasionnellement des recompenses supplementaires dynamiseraient le tout. En resume, Posido Casino est un endroit qui electrise. De plus le site est rapide et engageant, incite a prolonger le plaisir. Un point fort les evenements communautaires dynamiques, qui stimule l’engagement.
Parcourir maintenant|
https://yurhelp.in.ua/
с минимальным депозитом Открылось новое казино, готовое удивить вас своим неповторимым стилем и атмосферой. Мы собрали лучшие игры, самые захватывающие слоты и классические настольные игры, чтобы каждый гость нашел что-то по душе. Приходите и станьте частью чего-то совершенно нового!
гидроизоляция цена работы за м2 [url=https://www.gidroizolyaciya-cena-8.ru]https://www.gidroizolyaciya-cena-8.ru[/url] .
сырость в подвале многоквартирного дома [url=http://www.gidroizolyaciya-podvala-cena.ru]http://www.gidroizolyaciya-podvala-cena.ru[/url] .
торкретирование москва [url=http://torkretirovanie-1.ru/]http://torkretirovanie-1.ru/[/url] .
платный наркологический диспансер москва [url=narkologicheskaya-klinika-23.ru]narkologicheskaya-klinika-23.ru[/url] .
1xbet t?rkiye giri? [url=1xbet-17.com]1xbet t?rkiye giri?[/url] .
наркологические услуги москвы [url=narkologicheskaya-klinika-27.ru]narkologicheskaya-klinika-27.ru[/url] .
ремонт в подвале [url=www.gidroizolyaciya-cena-7.ru/]www.gidroizolyaciya-cena-7.ru/[/url] .
центр наркологической помощи [url=https://narkologicheskaya-klinika-28.ru]центр наркологической помощи[/url] .
рулонные жалюзи с электроприводом [url=www.avtomaticheskie-zhalyuzi.ru/]рулонные жалюзи с электроприводом[/url] .
карниз электроприводом штор купить [url=http://elektrokarniz797.ru]http://elektrokarniz797.ru[/url] .
электрокарнизы купить в москве [url=https://elektrokarniz499.ru/]электрокарнизы купить в москве[/url] .
наплавляемая гидроизоляция цена за м2 работа [url=http://gidroizolyaciya-cena-8.ru/]http://gidroizolyaciya-cena-8.ru/[/url] .
электрический карниз для штор купить [url=elektrokarniz797.ru]elektrokarniz797.ru[/url] .
карниз моторизованный [url=https://elektrokarniz499.ru/]https://elektrokarniz499.ru/[/url] .
вертикальная гидроизоляция стен подвала [url=www.gidroizolyaciya-podvala-cena.ru]вертикальная гидроизоляция стен подвала[/url] .
торкретирование цена за м2 [url=http://torkretirovanie-1.ru/]http://torkretirovanie-1.ru/[/url] .
телефон наркологии [url=www.narkologicheskaya-klinika-27.ru/]телефон наркологии[/url] .
отделка подвала [url=www.gidroizolyaciya-cena-7.ru/]отделка подвала[/url] .
клиника наркологическая москва [url=https://narkologicheskaya-klinika-28.ru/]narkologicheskaya-klinika-28.ru[/url] .
1xbet giri? 2025 [url=https://1xbet-17.com/]1xbet giri? 2025[/url] .
клиника наркологическая платная [url=http://www.narkologicheskaya-klinika-23.ru]http://www.narkologicheskaya-klinika-23.ru[/url] .
Je suis captive par Betzino Casino, ca transporte dans un univers de plaisirs. Les options de jeu sont infinies, comprenant des jeux optimises pour Bitcoin. Le bonus de depart est top. Le support est fiable et reactif. Les retraits sont ultra-rapides, parfois plus de promos regulieres dynamiseraient le jeu. Pour conclure, Betzino Casino offre une experience hors du commun. A signaler l’interface est simple et engageante, donne envie de prolonger l’aventure. A souligner les paiements securises en crypto, qui dynamise l’engagement.
Continuer Г lire|
Je suis enthousiaste a propos de Viggoslots Casino, il cree un monde de sensations fortes. Il y a un eventail de titres captivants, proposant des jeux de table sophistiques. Il donne un elan excitant. Le suivi est d’une precision remarquable. Le processus est simple et transparent, a l’occasion quelques free spins en plus seraient bienvenus. Dans l’ensemble, Viggoslots Casino garantit un amusement continu. Pour ajouter l’interface est simple et engageante, amplifie le plaisir de jouer. A signaler le programme VIP avec des avantages uniques, offre des bonus exclusifs.
Continuer Г lire|
J’adore l’ambiance electrisante de Viggoslots Casino, on ressent une ambiance festive. Les titres proposes sont d’une richesse folle, incluant des options de paris sportifs dynamiques. Le bonus de bienvenue est genereux. Les agents sont toujours la pour aider. Les retraits sont ultra-rapides, rarement quelques free spins en plus seraient bienvenus. Au final, Viggoslots Casino est un endroit qui electrise. D’ailleurs la navigation est simple et intuitive, ce qui rend chaque session plus excitante. Particulierement cool les tournois reguliers pour s’amuser, qui dynamise l’engagement.
Continuer ici|
Je suis emerveille par Viggoslots Casino, il cree un monde de sensations fortes. Les jeux proposes sont d’une diversite folle, avec des slots aux graphismes modernes. Le bonus d’inscription est attrayant. Le support est efficace et amical. Les paiements sont securises et rapides, mais encore des recompenses supplementaires seraient parfaites. Dans l’ensemble, Viggoslots Casino vaut une visite excitante. A souligner le site est rapide et style, ce qui rend chaque partie plus fun. Un plus les options de paris sportifs variees, offre des recompenses regulieres.
Commencer Г explorer|
Je suis completement seduit par Betzino Casino, c’est une plateforme qui deborde de dynamisme. Il y a une abondance de jeux excitants, avec des slots aux designs captivants. 100% jusqu’a 500 € avec des spins gratuits. Les agents sont rapides et pros. Les transactions sont fiables et efficaces, de temps a autre quelques tours gratuits en plus seraient geniaux. En somme, Betzino Casino offre une aventure inoubliable. Notons egalement le site est fluide et attractif, amplifie le plaisir de jouer. Particulierement fun les paiements en crypto rapides et surs, qui dynamise l’engagement.
Ouvrir maintenant|
гидроизоляция подвала под ключ [url=https://gidroizolyaciya-cena-8.ru]https://gidroizolyaciya-cena-8.ru[/url] .
J’ai une passion debordante pour Vbet Casino, c’est une plateforme qui deborde de dynamisme. Les options sont aussi vastes qu’un horizon, proposant des jeux de table sophistiques. Avec des depots instantanes. Le service d’assistance est au point. Les transactions sont d’une fiabilite absolue, mais des bonus diversifies seraient un atout. En resume, Vbet Casino est un immanquable pour les amateurs. Ajoutons aussi le site est rapide et engageant, apporte une touche d’excitation. Egalement excellent les evenements communautaires dynamiques, propose des avantages uniques.
Aller en ligne|
Je suis completement seduit par Posido Casino, ca donne une vibe electrisante. Le catalogue est un tresor de divertissements, avec des slots aux designs captivants. 100% jusqu’a 500 € plus des tours gratuits. Le service client est de qualite. Le processus est transparent et rapide, mais des bonus plus frequents seraient un hit. Au final, Posido Casino offre une experience inoubliable. Ajoutons aussi le site est rapide et engageant, amplifie le plaisir de jouer. Un bonus les options de paris sportifs variees, cree une communaute soudee.
Essayer ceci|
J’ai un faible pour Posido Casino, ca invite a plonger dans le fun. La selection de jeux est impressionnante, offrant des tables live interactives. Il amplifie le plaisir des l’entree. Le support client est irreprochable. Les retraits sont simples et rapides, de temps a autre des bonus plus frequents seraient un hit. En bref, Posido Casino offre une aventure inoubliable. En extra la navigation est fluide et facile, permet une immersion complete. Un element fort les options de paris sportifs diversifiees, qui motive les joueurs.
Aller en ligne|
карнизы для штор купить в москве [url=https://elektrokarniz797.ru/]карнизы для штор купить в москве[/url] .
J’adore la vibe de Posido Casino, ca offre une experience immersive. Les titres proposes sont d’une richesse folle, comprenant des jeux compatibles avec les cryptos. Il donne un elan excitant. Les agents repondent avec efficacite. Les transactions sont d’une fiabilite absolue, mais des recompenses en plus seraient un bonus. Pour finir, Posido Casino offre une experience inoubliable. A noter le site est rapide et style, facilite une experience immersive. Egalement genial les evenements communautaires vibrants, offre des recompenses continues.
http://www.posidocasino777fr.com|
электрокарниз купить в москве [url=https://elektrokarniz499.ru]электрокарниз купить в москве[/url] .
гидроизоляция подвала гаража [url=https://gidroizolyaciya-podvala-cena.ru/]гидроизоляция подвала гаража[/url] .
торкретирование цена за м2 [url=https://torkretirovanie-1.ru]https://torkretirovanie-1.ru[/url] .
автоматический карниз для штор [url=https://elektrokarniz-kupit.ru]https://elektrokarniz-kupit.ru[/url] .
автоматические карнизы [url=http://elektrokarniz777.ru]автоматические карнизы[/url] .
жалюзи с мотором [url=https://elektricheskie-zhalyuzi97.ru/]жалюзи с мотором[/url] .
электрокарнизы москва [url=www.elektrokarniz-kupit.ru]www.elektrokarniz-kupit.ru[/url] .
бамбуковые электрожалюзи [url=http://elektricheskie-zhalyuzi97.ru]http://elektricheskie-zhalyuzi97.ru[/url] .
электрокарниз купить в москве [url=http://elektrokarniz777.ru]электрокарниз купить в москве[/url] .
Je suis bluffe par Betzino Casino, ca invite a l’aventure. On trouve une gamme de jeux eblouissante, avec des slots aux graphismes modernes. Il donne un avantage immediat. Le service client est excellent. Les gains sont transferes rapidement, par contre plus de promotions frequentes boosteraient l’experience. En resume, Betzino Casino merite une visite dynamique. A mentionner le design est style et moderne, amplifie l’adrenaline du jeu. Egalement genial les paiements en crypto rapides et surs, offre des bonus exclusifs.
Cliquer pour voir|
Таможенный брокер работает быстро и внимательно. Все нюансы учтены, оформление без проблем – https://tamozhenniiy-predstavitel11.ru/
автоматические карнизы для штор [url=http://www.elektrokarniz-kupit.ru]автоматические карнизы для штор[/url] .
J’ai un faible pour Viggoslots Casino, c’est une plateforme qui deborde de dynamisme. La selection est riche et diversifiee, avec des machines a sous aux themes varies. Il amplifie le plaisir des l’entree. Disponible 24/7 par chat ou email. Les transactions sont toujours securisees, rarement des recompenses additionnelles seraient ideales. Pour finir, Viggoslots Casino assure un divertissement non-stop. A noter la navigation est fluide et facile, facilite une immersion totale. Un avantage les tournois reguliers pour s’amuser, assure des transactions fiables.
Jeter un coup d’œil|
J’adore la vibe de Viggoslots Casino, ca transporte dans un univers de plaisirs. Il y a un eventail de titres captivants, comprenant des jeux compatibles avec les cryptos. Il propulse votre jeu des le debut. Les agents sont rapides et pros. Les retraits sont ultra-rapides, toutefois des recompenses supplementaires dynamiseraient le tout. Pour conclure, Viggoslots Casino offre une aventure memorable. A noter la navigation est simple et intuitive, amplifie le plaisir de jouer. A signaler les paiements securises en crypto, qui booste la participation.
Aller au site|
Je suis bluffe par Betzino Casino, on ressent une ambiance de fete. Le catalogue est un paradis pour les joueurs, avec des slots aux graphismes modernes. Il donne un elan excitant. Les agents repondent avec efficacite. Les retraits sont simples et rapides, bien que des bonus plus frequents seraient un hit. Pour faire court, Betzino Casino garantit un amusement continu. En plus la plateforme est visuellement dynamique, facilite une immersion totale. Particulierement interessant les competitions regulieres pour plus de fun, assure des transactions fluides.
https://betzinocasino777fr.com/|
бамбуковые электрожалюзи [url=https://elektricheskie-zhalyuzi97.ru/]https://elektricheskie-zhalyuzi97.ru/[/url] .
J’adore l’energie de Vbet Casino, ca transporte dans un univers de plaisirs. La bibliotheque de jeux est captivante, offrant des sessions live palpitantes. 100% jusqu’a 500 € avec des spins gratuits. Le support est fiable et reactif. Le processus est clair et efficace, de temps a autre des offres plus genereuses seraient top. Globalement, Vbet Casino merite une visite dynamique. De surcroit la plateforme est visuellement captivante, amplifie l’adrenaline du jeu. Un point cle les tournois reguliers pour la competition, qui motive les joueurs.
Visiter pour plus|
J’ai une affection particuliere pour Vbet Casino, on y trouve une energie contagieuse. Le catalogue est un tresor de divertissements, avec des slots aux graphismes modernes. Il donne un elan excitant. Le service client est de qualite. Les retraits sont lisses comme jamais, mais des bonus plus frequents seraient un hit. En conclusion, Vbet Casino offre une experience inoubliable. D’ailleurs le design est tendance et accrocheur, facilite une experience immersive. Egalement top le programme VIP avec des niveaux exclusifs, qui stimule l’engagement.
https://vbetcasino365fr.com/|
электрокарнизы москва [url=https://elektrokarniz777.ru/]https://elektrokarniz777.ru/[/url] .
Je suis bluffe par Posido Casino, ca donne une vibe electrisante. Le catalogue de titres est vaste, comprenant des titres adaptes aux cryptomonnaies. 100% jusqu’a 500 € avec des free spins. Les agents repondent avec rapidite. Les retraits sont fluides et rapides, parfois des recompenses supplementaires seraient parfaites. En resume, Posido Casino offre une aventure inoubliable. A souligner l’interface est lisse et agreable, facilite une immersion totale. Particulierement attrayant les tournois reguliers pour s’amuser, qui stimule l’engagement.
DГ©couvrir le web|
Je suis captive par Posido Casino, on ressent une ambiance de fete. La bibliotheque est pleine de surprises, comprenant des jeux optimises pour Bitcoin. Le bonus initial est super. Le suivi est d’une precision remarquable. Les retraits sont simples et rapides, neanmoins quelques free spins en plus seraient bienvenus. En somme, Posido Casino est une plateforme qui fait vibrer. De surcroit la navigation est claire et rapide, permet une plongee totale dans le jeu. A souligner le programme VIP avec des avantages uniques, offre des bonus exclusifs.
Consulter les dГ©tails|
Je suis emerveille par Posido Casino, il cree un monde de sensations fortes. La bibliotheque de jeux est captivante, incluant des paris sportifs pleins de vie. Il donne un elan excitant. Le suivi est d’une fiabilite exemplaire. Les retraits sont ultra-rapides, cependant des offres plus consequentes seraient parfaites. En somme, Posido Casino assure un divertissement non-stop. En complement la plateforme est visuellement dynamique, booste le fun du jeu. Un avantage notable les tournois reguliers pour s’amuser, offre des recompenses regulieres.
Ouvrir le site|
рейтинг казино с бездепозитными бонусами
J’ai un faible pour Betzino Casino, il procure une sensation de frisson. Le choix est aussi large qu’un festival, offrant des experiences de casino en direct. Le bonus initial est super. Le service client est excellent. Les transactions sont toujours securisees, rarement des bonus plus frequents seraient un hit. En bref, Betzino Casino est un immanquable pour les amateurs. Par ailleurs la navigation est intuitive et lisse, permet une immersion complete. Un plus les options de paris sportifs variees, qui booste la participation.
Tout apprendre|
Thailand Koh Lanta
электро рулонные шторы [url=avtomaticheskie-rulonnye-shtory77.ru]avtomaticheskie-rulonnye-shtory77.ru[/url] .
1xbet guncel [url=http://www.1xbet-giris-5.com]1xbet guncel[/url] .
стоимость рулонных штор [url=https://avtomaticheskie-rulonnye-shtory1.ru]стоимость рулонных штор[/url] .
поставщик медицинского оборудования [url=https://medoborudovanie-postavka.ru/]поставщик медицинского оборудования[/url] .
рулонные шторы виды механизмов [url=https://rulonnye-shtory-s-elektroprivodom7.ru]https://rulonnye-shtory-s-elektroprivodom7.ru[/url] .
1xbet yeni giri? adresi [url=https://www.1xbet-15.com]1xbet yeni giri? adresi[/url] .
согласование перепланировки нежилого помещения в нежилом здании [url=http://www.pereplanirovka-nezhilogo-pomeshcheniya16.ru]http://www.pereplanirovka-nezhilogo-pomeshcheniya16.ru[/url] .
медтехника [url=https://medicinskaya-tehnika.ru/]https://medicinskaya-tehnika.ru/[/url] .
bahis sitesi 1xbet [url=http://1xbet-giris-2.com/]http://1xbet-giris-2.com/[/url] .
1 xbet [url=www.1xbet-giris-8.com/]1 xbet[/url] .
студия для записи видео подкастов [url=http://www.studiya-podkastov-spb4.ru]http://www.studiya-podkastov-spb4.ru[/url] .
организация видеотрансляций [url=https://zakazat-onlayn-translyaciyu5.ru/]организация видеотрансляций[/url] .
1xbet [url=https://1xbet-giris-4.com/]1xbet[/url] .
J’adore la vibe de Betway Casino, il propose une aventure palpitante. Le catalogue est un paradis pour les joueurs, avec des machines a sous visuellement superbes. Le bonus initial est super. Le support est pro et accueillant. Les transactions sont toujours securisees, de temps a autre des recompenses en plus seraient un bonus. En bref, Betway Casino vaut une exploration vibrante. D’ailleurs la plateforme est visuellement captivante, ce qui rend chaque partie plus fun. Un plus les tournois frequents pour l’adrenaline, propose des avantages sur mesure.
Plongez-y|
перепланировка нежилого помещения [url=https://pereplanirovka-nezhilogo-pomeshcheniya16.ru]https://pereplanirovka-nezhilogo-pomeshcheniya16.ru[/url] .
поставщик медицинского оборудования [url=https://www.medoborudovanie-postavka.ru]поставщик медицинского оборудования[/url] .
автоматические рулонные шторы на окна [url=http://avtomaticheskie-rulonnye-shtory77.ru]http://avtomaticheskie-rulonnye-shtory77.ru[/url] .
1xbet turkey [url=http://1xbet-giris-5.com/]http://1xbet-giris-5.com/[/url] .
1xbet ?yelik [url=https://1xbet-15.com]1xbet ?yelik[/url] .
медицинская техника [url=http://medicinskaya-tehnika.ru]медицинская техника[/url] .
запись подкастов [url=https://studiya-podkastov-spb4.ru/]запись подкастов[/url] .
стоимость онлайн трансляции на мероприятии [url=zakazat-onlayn-translyaciyu5.ru]zakazat-onlayn-translyaciyu5.ru[/url] .
автоматические рулонные шторы на окна [url=https://avtomaticheskie-rulonnye-shtory1.ru/]avtomaticheskie-rulonnye-shtory1.ru[/url] .
1xbet giri? linki [url=www.1xbet-giris-8.com/]1xbet giri? linki[/url] .
заказать рулонные шторы в москве [url=http://www.rulonnye-shtory-s-elektroprivodom7.ru]заказать рулонные шторы в москве[/url] .
bahis sitesi 1xbet [url=1xbet-giris-2.com]1xbet-giris-2.com[/url] .
1xbet mobi [url=www.1xbet-giris-4.com/]www.1xbet-giris-4.com/[/url] .
бездепозитные бонусы казино без пополнения Бездепозитные бонусы – это щедрый подарок от онлайн-казино, который позволяет игрокам начать игру, не рискуя собственными деньгами. Представьте: вы регистрируетесь, получаете бонус и можете сразу же приступить к игре на реальные деньги. Это отличный способ протестировать новые слоты, оценить функционал казино и понять, подходит ли оно вам. Главное – внимательно ознакомиться с условиями отыгрыша, чтобы успешно вывести свой выигрыш.
Je ne me lasse pas de Betway Casino, il procure une sensation de frisson. Les options de jeu sont incroyablement variees, offrant des sessions live immersives. Le bonus de depart est top. Les agents repondent avec efficacite. Les transactions sont fiables et efficaces, toutefois quelques tours gratuits en plus seraient geniaux. Pour conclure, Betway Casino est une plateforme qui pulse. Pour completer le design est style et moderne, permet une immersion complete. Egalement top les transactions en crypto fiables, renforce le lien communautaire.
Savoir plus|
Je suis captive par Belgium Casino, c’est une plateforme qui pulse avec energie. Le choix est aussi large qu’un festival, proposant des jeux de cartes elegants. Le bonus initial est super. Disponible a toute heure via chat ou email. Les gains arrivent en un eclair, en revanche des bonus plus varies seraient un plus. En conclusion, Belgium Casino merite un detour palpitant. Pour ajouter l’interface est intuitive et fluide, donne envie de continuer l’aventure. Egalement excellent les competitions regulieres pour plus de fun, garantit des paiements rapides.
Explorer plus|
J’ai un veritable coup de c?ur pour Betway Casino, on y trouve une vibe envoutante. Le choix de jeux est tout simplement enorme, comprenant des jeux crypto-friendly. Il propulse votre jeu des le debut. Le support est fiable et reactif. Les retraits sont ultra-rapides, rarement des bonus plus varies seraient un plus. En fin de compte, Betway Casino garantit un plaisir constant. A souligner la navigation est simple et intuitive, donne envie de prolonger l’aventure. Un point fort les options de paris sportifs variees, renforce la communaute.
Commencer maintenant|
Je suis completement seduit par Gamdom Casino, on ressent une ambiance festive. Le choix de jeux est tout simplement enorme, offrant des experiences de casino en direct. Le bonus de bienvenue est genereux. Le suivi est d’une precision remarquable. Les retraits sont lisses comme jamais, rarement des recompenses supplementaires dynamiseraient le tout. Dans l’ensemble, Gamdom Casino merite un detour palpitant. A souligner la plateforme est visuellement captivante, incite a rester plus longtemps. Particulierement interessant les options de paris sportifs diversifiees, garantit des paiements securises.
Essayer maintenant|
Je suis captive par Betify Casino, ca donne une vibe electrisante. Le catalogue est un tresor de divertissements, offrant des sessions live immersives. Il offre un coup de pouce allechant. Le service est disponible 24/7. Les retraits sont simples et rapides, en revanche des offres plus importantes seraient super. En resume, Betify Casino est un incontournable pour les joueurs. En extra l’interface est simple et engageante, booste le fun du jeu. Particulierement interessant les transactions en crypto fiables, propose des avantages uniques.
DГ©couvrir dГЁs maintenant|
Je suis totalement conquis par Betify Casino, il propose une aventure palpitante. Les options de jeu sont incroyablement variees, avec des machines a sous aux themes varies. Il offre un coup de pouce allechant. Le suivi est d’une fiabilite exemplaire. Les paiements sont securises et rapides, par ailleurs plus de promotions frequentes boosteraient l’experience. En bref, Betify Casino merite un detour palpitant. D’ailleurs le design est style et moderne, ajoute une vibe electrisante. Egalement top les evenements communautaires engageants, propose des avantages sur mesure.
Naviguer sur le site|
1xbet lite [url=http://1xbet-giris-5.com/]http://1xbet-giris-5.com/[/url] .
согласование перепланировки нежилого здания [url=https://pereplanirovka-nezhilogo-pomeshcheniya16.ru]https://pereplanirovka-nezhilogo-pomeshcheniya16.ru[/url] .
поставка медицинского оборудования [url=www.medoborudovanie-postavka.ru]поставка медицинского оборудования[/url] .
1 xbet [url=http://www.1xbet-15.com]1 xbet[/url] .
медтехника [url=http://medicinskaya-tehnika.ru]http://medicinskaya-tehnika.ru[/url] .
рулонные шторы автоматические [url=https://www.avtomaticheskie-rulonnye-shtory77.ru]рулонные шторы автоматические[/url] .
студия подкастов спб [url=www.studiya-podkastov-spb4.ru/]студия подкастов спб[/url] .
онлайн трансляция заказать москва [url=http://www.zakazat-onlayn-translyaciyu5.ru]http://www.zakazat-onlayn-translyaciyu5.ru[/url] .
1xbet giri? [url=https://1xbet-giris-8.com/]1xbet giri?[/url] .
рулонные шторы на окно в кухне [url=http://avtomaticheskie-rulonnye-shtory1.ru/]http://avtomaticheskie-rulonnye-shtory1.ru/[/url] .
1xbet g?ncel [url=1xbet-giris-2.com]1xbet-giris-2.com[/url] .
пластиковые окна рулонные шторы с электроприводом [url=http://rulonnye-shtory-s-elektroprivodom7.ru/]http://rulonnye-shtory-s-elektroprivodom7.ru/[/url] .
1xbet g?ncel giri? [url=http://1xbet-giris-4.com/]1xbet g?ncel giri?[/url] .
J’ai un veritable coup de c?ur pour Betway Casino, ca invite a l’aventure. Le catalogue est un paradis pour les joueurs, proposant des jeux de casino traditionnels. Il offre un demarrage en fanfare. Disponible 24/7 par chat ou email. Les paiements sont securises et rapides, cependant quelques free spins en plus seraient bienvenus. En conclusion, Betway Casino garantit un plaisir constant. En extra l’interface est lisse et agreable, ce qui rend chaque partie plus fun. A noter les evenements communautaires pleins d’energie, assure des transactions fluides.
Essayer maintenant|
Hey there! Do you use Twitter? I’d like to follow you if that would be ok. I’m absolutely enjoying your blog and look forward to new posts.
bitz casino
Discover exquisite Austrian wines at [url=https://wine-tasting-wien.netlify.app/]weinprobe wien[/url] and immerse yourself in Vienna’s vibrant wine culture.
Die osterreichische Hauptstadt bietet eine einzigartige Mischung aus Tradition und Moderne. Die Region ist bekannt fur ihren exzellenten Wei?wein, besonders den Grunen Veltliner. Die Weinkeller Wiens locken mit ihrem authentischen Charme und kostlichen Tropfen.
Das milde Klima und die mineralreichen Boden begunstigen den Weinbau. Das macht Wien zu einer der wenigen Gro?stadte mit eigenem Weinbaugebiet.
#### **2. Beliebte Weinregionen und Weinguter**
In Wien gibt es mehrere renommierte Weinregionen, wie den Nussberg oder den Bisamberg. Die Weinguter hier setzen auf nachhaltigen Anbau. Familiengefuhrte Weinguter bieten oft Fuhrungen und Verkostungen an. Oft gibt es auch regionale Speisen zur perfekten Weinbegleitung.
Ein Besuch im Weingut Wieninger oder im Mayer am Pfarrplatz lohnt sich. Sie sind bekannt fur ihre ausgezeichneten Jahrgange.
#### **3. Ablauf einer typischen Weinverkostung**
Eine klassische Wiener Weinverkostung beginnt meist mit einer Kellertour. Oft werden historische Anekdoten zum Weinbau geteilt. Danach folgt die Verkostung unterschiedlicher Weine. Jeder Wein wird sorgfaltig prasentiert und verkostet.
Haufig werden die Weine mit lokalen Kasesorten oder Brot serviert. Diese Kombination ist ein Highlight fur Feinschmecker.
#### **4. Tipps fur unvergessliche Weinverkostungen**
Um das Beste aus einer Weinverkostung in Wien herauszuholen, sollte man vorher buchen. Fruhzeitige Reservierungen garantieren einen reibungslosen Ablauf. Zudem lohnt es sich, auf die Jahreszeiten zu achten. Im Herbst finden oft Weinlesefeste statt.
Ein guter Tipp ist auch, ein Notizbuch mitzubringen. So kann man sich die geschmacklichen Eindrucke leicht merken.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
Das gibt den Wiener Weinen ihren unverwechselbaren Charakter.
#### **2. Beliebte Weinregionen und Weinguter**
Hier verbinden sich Tradition mit innovativen Methoden.
#### **3. Ablauf einer typischen Wiener Weinverkostung**
Dabei erfahrt man Wissenswertes uber Rebsorten und Vinifizierung.
#### **4. Tipps fur unvergessliche Weinverkostungen**
Viele Weinguter haben begrenzte Platze und sind schnell ausgebucht.
—
**Hinweis:** Durch Kombination der Varianten aus den -Blocken konnen zahlreiche einzigartige Texte generiert werden, die grammatikalisch und inhaltlich korrekt sind.
согласование перепланировок нежилых помещений [url=http://pereplanirovka-nezhilogo-pomeshcheniya17.ru]http://pereplanirovka-nezhilogo-pomeshcheniya17.ru[/url] .
перепланировка нежилого здания [url=www.pereplanirovka-nezhilogo-pomeshcheniya18.ru]перепланировка нежилого здания[/url] .
смарт вэй [url=http://www.sajt-smart-way.ru]http://www.sajt-smart-way.ru[/url] .
рулонные жалюзи с электроприводом [url=https://avtomaticheskie-zhalyuzi.ru]рулонные жалюзи с электроприводом[/url] .
технического аудита сайта [url=https://optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru/]optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru[/url] .
комплексное продвижение сайтов москва [url=http://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru]комплексное продвижение сайтов москва[/url] .
пошив шопперов на заказ [url=www.miniatelie.ru]www.miniatelie.ru[/url] .
стратегия продвижения блог [url=statyi-o-marketinge7.ru]statyi-o-marketinge7.ru[/url] .
интернет маркетинг статьи [url=www.statyi-o-marketinge6.ru]интернет маркетинг статьи[/url] .
стоимость услуг экскаватора погрузчика [url=arenda-ekskavatora-pogruzchika-1.ru]стоимость услуг экскаватора погрузчика[/url] .
швейный цех санкт петербург [url=arbuztech.ru]arbuztech.ru[/url] .
топ компаний по продвижению сайтов [url=http://reiting-seo-kompanii.ru/]топ компаний по продвижению сайтов[/url] .
продвижение сайта в топ 10 профессионалами [url=https://reiting-kompanii-po-prodvizheniyu-sajtov.ru/]https://reiting-kompanii-po-prodvizheniyu-sajtov.ru/[/url] .
Je suis enthousiaste a propos de Belgium Casino, il propose une aventure palpitante. Le catalogue de titres est vaste, comprenant des jeux optimises pour Bitcoin. Il amplifie le plaisir des l’entree. Disponible a toute heure via chat ou email. Les transactions sont toujours fiables, par moments des bonus varies rendraient le tout plus fun. Pour finir, Belgium Casino vaut une visite excitante. A mentionner l’interface est lisse et agreable, incite a rester plus longtemps. A souligner les evenements communautaires dynamiques, cree une communaute soudee.
Continuer ici|
Je suis emerveille par Betway Casino, il procure une sensation de frisson. Les options sont aussi vastes qu’un horizon, avec des machines a sous visuellement superbes. Le bonus d’inscription est attrayant. Le support est rapide et professionnel. Les gains sont transferes rapidement, mais encore des bonus diversifies seraient un atout. En fin de compte, Betway Casino est une plateforme qui fait vibrer. De surcroit l’interface est fluide comme une soiree, ce qui rend chaque session plus excitante. Egalement top les paiements securises en crypto, assure des transactions fluides.
Voir la page d’accueil|
узаконивание перепланировки цена [url=skolko-stoit-uzakonit-pereplanirovku-1.ru]узаконивание перепланировки цена[/url] .
перепланировка квартиры цена под ключ [url=www.skolko-stoit-uzakonit-pereplanirovku.ru/]www.skolko-stoit-uzakonit-pereplanirovku.ru/[/url] .
Je suis enthousiaste a propos de Gamdom Casino, il cree une experience captivante. Les titres proposes sont d’une richesse folle, offrant des tables live interactives. Avec des depots instantanes. Le support est pro et accueillant. Le processus est simple et transparent, toutefois des offres plus genereuses seraient top. En conclusion, Gamdom Casino assure un divertissement non-stop. Ajoutons aussi le design est moderne et attrayant, ce qui rend chaque moment plus vibrant. Un atout les nombreuses options de paris sportifs, garantit des paiements rapides.
Commencer Г naviguer|
Je suis fascine par Gamdom Casino, il cree un monde de sensations fortes. Les titres proposes sont d’une richesse folle, offrant des sessions live immersives. Il amplifie le plaisir des l’entree. Le service est disponible 24/7. Les gains arrivent en un eclair, de temps en temps quelques tours gratuits en plus seraient geniaux. Au final, Gamdom Casino est un must pour les passionnes. Par ailleurs la plateforme est visuellement vibrante, ajoute une touche de dynamisme. Particulierement fun les paiements en crypto rapides et surs, renforce la communaute.
Apprendre comment|
Je suis totalement conquis par Betway Casino, ca invite a plonger dans le fun. Les jeux proposes sont d’une diversite folle, avec des machines a sous aux themes varies. 100% jusqu’a 500 € plus des tours gratuits. Le suivi est impeccable. Les transactions sont fiables et efficaces, occasionnellement plus de promotions variees ajouteraient du fun. En resume, Betway Casino vaut une exploration vibrante. En plus la plateforme est visuellement dynamique, facilite une experience immersive. Un avantage le programme VIP avec des recompenses exclusives, propose des privileges sur mesure.
Commencer Г lire|
Je suis accro a Gamdom Casino, il procure une sensation de frisson. Les options de jeu sont incroyablement variees, avec des machines a sous aux themes varies. Avec des depots rapides et faciles. Le support est fiable et reactif. Les gains sont verses sans attendre, mais encore des bonus plus frequents seraient un hit. En resume, Gamdom Casino offre une aventure inoubliable. A signaler l’interface est lisse et agreable, apporte une touche d’excitation. Un point cle les tournois reguliers pour la competition, garantit des paiements securises.
Continuer ici|
J’ai un faible pour Betify Casino, on y trouve une vibe envoutante. La bibliotheque est pleine de surprises, incluant des paris sportifs pleins de vie. Il donne un avantage immediat. Le service client est de qualite. Le processus est transparent et rapide, neanmoins des offres plus importantes seraient super. Pour finir, Betify Casino garantit un plaisir constant. Pour couronner le tout la navigation est claire et rapide, ce qui rend chaque moment plus vibrant. A mettre en avant les evenements communautaires vibrants, qui booste la participation.
Essayer ceci|
Je suis sous le charme de Betify Casino, il procure une sensation de frisson. On trouve une gamme de jeux eblouissante, offrant des experiences de casino en direct. 100% jusqu’a 500 € avec des spins gratuits. Le suivi est impeccable. Les retraits sont lisses comme jamais, rarement plus de promotions frequentes boosteraient l’experience. En resume, Betify Casino offre une aventure memorable. Ajoutons que le design est moderne et attrayant, ce qui rend chaque session plus palpitante. Un avantage les options de paris sportifs variees, cree une communaute vibrante.
En savoir plus|
Найкраще прямо тут: https://ukrchannel.com/remont-i-budivnytstvo.html
перепланировка нежилых помещений [url=http://pereplanirovka-nezhilogo-pomeshcheniya18.ru/]перепланировка нежилых помещений[/url] .
перепланировка в нежилом помещении [url=https://www.pereplanirovka-nezhilogo-pomeshcheniya17.ru]https://www.pereplanirovka-nezhilogo-pomeshcheniya17.ru[/url] .
smart way [url=http://sajt-smart-way.ru]http://sajt-smart-way.ru[/url] .
жалюзи для умного дома [url=http://avtomaticheskie-zhalyuzi.ru/]жалюзи для умного дома[/url] .
Je suis sous le charme de Betway Casino, ca invite a plonger dans le fun. La selection de jeux est impressionnante, offrant des sessions live immersives. Il donne un elan excitant. Le support est efficace et amical. Le processus est transparent et rapide, parfois des offres plus genereuses seraient top. Pour faire court, Betway Casino est un choix parfait pour les joueurs. A souligner le design est moderne et energique, ce qui rend chaque session plus palpitante. Un plus les tournois reguliers pour s’amuser, garantit des paiements securises.
Parcourir maintenant|
бездепозитные игровые автоматы Бездепозитные бонусы — это отличный способ войти в мир онлайн-гемблинга без вложений, но подходите с умом. Они дают шанс на выигрыш, но условия могут быть сложными, а риски — высокими. Выбирайте только проверенные казино
производство футболок [url=https://miniatelie.ru/]https://miniatelie.ru/[/url] .
компания seo [url=http://www.reiting-seo-kompanii.ru]компания seo[/url] .
Найцікавіше тут: https://metasearch.com.ua/dity.html
нанять экскаватор цена [url=https://arenda-ekskavatora-pogruzchika-1.ru/]arenda-ekskavatora-pogruzchika-1.ru[/url] .
производство верхней одежды санкт петербург [url=http://arbuztech.ru]http://arbuztech.ru[/url] .
агентства контекстная реклама продвижение сайтов [url=http://www.reiting-kompanii-po-prodvizheniyu-sajtov.ru]http://www.reiting-kompanii-po-prodvizheniyu-sajtov.ru[/url] .
продвижение сайта франция [url=http://optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru]http://optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru[/url] .
раскрутка сайта франция цена [url=https://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru]https://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru[/url] .
seo и реклама блог [url=http://statyi-o-marketinge7.ru/]http://statyi-o-marketinge7.ru/[/url] .
блог про продвижение сайтов [url=http://www.statyi-o-marketinge6.ru]блог про продвижение сайтов[/url] .
проект перепланировки нежилого помещения [url=https://www.pereplanirovka-nezhilogo-pomeshcheniya18.ru]https://www.pereplanirovka-nezhilogo-pomeshcheniya18.ru[/url] .
согласование перепланировки нежилого помещения в москве [url=http://pereplanirovka-nezhilogo-pomeshcheniya17.ru/]http://pereplanirovka-nezhilogo-pomeshcheniya17.ru/[/url] .
жалюзи автоматические цена [url=https://avtomaticheskie-zhalyuzi.ru]жалюзи автоматические цена[/url] .
смартвэй официальный сайт смвэй [url=www.sajt-smart-way.ru/]www.sajt-smart-way.ru/[/url] .
пошив постельного белья оптом [url=http://www.miniatelie.ru]http://www.miniatelie.ru[/url] .
рейтинг seo студий [url=http://reiting-seo-kompanii.ru/]http://reiting-seo-kompanii.ru/[/url] .
экскаватор погрузчик аренда москва [url=http://arenda-ekskavatora-pogruzchika-1.ru/]экскаватор погрузчик аренда москва[/url] .
услуги сео [url=www.reiting-kompanii-po-prodvizheniyu-sajtov.ru/]www.reiting-kompanii-po-prodvizheniyu-sajtov.ru/[/url] .
поисковое продвижение москва профессиональное продвижение сайтов [url=https://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru]https://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru[/url] .
французское seo цена [url=https://optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru/]optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru[/url] .
локальное seo блог [url=www.statyi-o-marketinge7.ru/]www.statyi-o-marketinge7.ru/[/url] .
интернет маркетинг статьи [url=https://www.statyi-o-marketinge6.ru]интернет маркетинг статьи[/url] .
https://444-000.ru/
бесплатные вращения без депозита Не упустите шанс начать играть прямо сейчас! Зарегистрируйтесь и получите свой бездепозитный бонус – это может быть сумма на счет или бесплатные вращения. Испытайте удачу, познакомьтесь с любимыми играми и получите возможность выиграть реальные деньги, не рискуя собственными. Просто зарегистрируйтесь и заберите свой подарок!
Wow, awesome weblog format! How lengthy have you ever been running a blog for? you made running a blog look easy. The overall look of your website is excellent, as neatly as the content material!
sklo
Je suis totalement conquis par Betway Casino, ca transporte dans un monde d’excitation. On trouve une profusion de jeux palpitants, comprenant des titres adaptes aux cryptomonnaies. Il rend le debut de l’aventure palpitant. Disponible 24/7 pour toute question. Les retraits sont lisses comme jamais, mais encore des offres plus genereuses rendraient l’experience meilleure. En conclusion, Betway Casino est une plateforme qui pulse. A noter le site est fluide et attractif, ajoute une vibe electrisante. Egalement excellent le programme VIP avec des privileges speciaux, offre des recompenses regulieres.
Entrer|
Je suis captive par Betway Casino, ca offre une experience immersive. La gamme est variee et attrayante, avec des machines a sous aux themes varies. Il offre un coup de pouce allechant. Les agents repondent avec efficacite. Les gains arrivent sans delai, cependant plus de promotions frequentes boosteraient l’experience. Pour finir, Betway Casino est un choix parfait pour les joueurs. Par ailleurs l’interface est simple et engageante, permet une plongee totale dans le jeu. Egalement genial les paiements securises en crypto, assure des transactions fiables.
Voir le site|
Je suis totalement conquis par Gamdom Casino, il cree un monde de sensations fortes. Le catalogue est un paradis pour les joueurs, proposant des jeux de cartes elegants. Avec des depots rapides et faciles. Disponible 24/7 par chat ou email. Le processus est simple et transparent, occasionnellement des recompenses supplementaires seraient parfaites. Au final, Gamdom Casino vaut une visite excitante. De surcroit la plateforme est visuellement vibrante, booste l’excitation du jeu. Un point fort les evenements communautaires vibrants, assure des transactions fluides.
Voir les dГ©tails|
J’ai une affection particuliere pour Gamdom Casino, ca invite a l’aventure. On trouve une gamme de jeux eblouissante, proposant des jeux de cartes elegants. 100% jusqu’a 500 € plus des tours gratuits. Le service est disponible 24/7. Les paiements sont securises et instantanes, malgre tout des recompenses en plus seraient un bonus. En resume, Gamdom Casino garantit un plaisir constant. En bonus la navigation est claire et rapide, booste l’excitation du jeu. Egalement top le programme VIP avec des privileges speciaux, garantit des paiements securises.
Visiter en ligne|
J’adore le dynamisme de Belgium Casino, c’est une plateforme qui deborde de dynamisme. La variete des jeux est epoustouflante, comprenant des titres adaptes aux cryptomonnaies. 100% jusqu’a 500 € avec des spins gratuits. Disponible 24/7 par chat ou email. Les paiements sont surs et fluides, a l’occasion quelques tours gratuits en plus seraient geniaux. Au final, Belgium Casino assure un divertissement non-stop. De plus la plateforme est visuellement dynamique, booste le fun du jeu. Particulierement interessant les tournois frequents pour l’adrenaline, offre des bonus constants.
Voir la page d’accueil|
Je suis sous le charme de Betify Casino, on ressent une ambiance de fete. Les options de jeu sont incroyablement variees, avec des slots aux graphismes modernes. Le bonus d’inscription est attrayant. Le suivi est impeccable. Les transactions sont toujours securisees, quelquefois des recompenses additionnelles seraient ideales. Globalement, Betify Casino est une plateforme qui fait vibrer. A mentionner la plateforme est visuellement dynamique, booste l’excitation du jeu. Un point fort le programme VIP avec des privileges speciaux, offre des recompenses regulieres.
DГ©couvrir le web|
J’ai un veritable coup de c?ur pour Betify Casino, il cree un monde de sensations fortes. Les options de jeu sont incroyablement variees, incluant des paris sportifs en direct. Le bonus de bienvenue est genereux. Le service client est excellent. Les gains sont verses sans attendre, occasionnellement quelques tours gratuits supplementaires seraient cool. Dans l’ensemble, Betify Casino est une plateforme qui fait vibrer. Par ailleurs le site est rapide et engageant, ce qui rend chaque moment plus vibrant. Un element fort le programme VIP avec des avantages uniques, propose des privileges personnalises.
Explorer la page|
Je suis fascine par Belgium Casino, c’est une plateforme qui deborde de dynamisme. Les titres proposes sont d’une richesse folle, incluant des paris sur des evenements sportifs. Il rend le debut de l’aventure palpitant. Le service d’assistance est au point. Le processus est fluide et intuitif, par ailleurs plus de promos regulieres ajouteraient du peps. Pour conclure, Belgium Casino offre une aventure inoubliable. D’ailleurs la navigation est intuitive et lisse, ce qui rend chaque session plus excitante. Un plus les options de paris sportifs variees, assure des transactions fluides.
Apprendre les dГ©tails|
ganabet iniciar sesi?n [url=https://ganabet-online.com/]ganabet-online.com[/url] .
сколько стоит узаконить перепланировку в квартире в москве [url=uzakonit-pereplanirovku-cena.ru]uzakonit-pereplanirovku-cena.ru[/url] .
перепланировка [url=https://www.soglasovanie-pereplanirovki-1.ru]перепланировка[/url] .
goliath casino [url=http://www.goliath-casino.com]http://www.goliath-casino.com[/url] .
регистрация перепланировки нежилого помещения [url=http://automobilist.forum24.ru/?1-7-0-00000293-000-0-0/]регистрация перепланировки нежилого помещения[/url] .
sure win [url=https://www.surewin-online.com]https://www.surewin-online.com[/url] .
valor de fichas de casino por color [url=http://valorslots.com]http://valorslots.com[/url] .
jp99 online casino [url=www.jp99-online.com]www.jp99-online.com[/url] .
icebet casino [url=http://icebet-online.com/]icebet casino[/url] .
beep beep kasino [url=https://beepbeepcasino-online.com/]https://beepbeepcasino-online.com/[/url] .
J’adore le dynamisme de Betify Casino, c’est une plateforme qui deborde de dynamisme. On trouve une gamme de jeux eblouissante, proposant des jeux de table sophistiques. Il rend le debut de l’aventure palpitant. Le service d’assistance est au point. Les gains sont transferes rapidement, parfois des bonus diversifies seraient un atout. En conclusion, Betify Casino garantit un amusement continu. Par ailleurs le site est fluide et attractif, apporte une energie supplementaire. Un element fort les tournois reguliers pour la competition, qui dynamise l’engagement.
http://www.betifycasino777fr.com|
newsky88 app [url=http://newsky-online.com]http://newsky-online.com[/url] .
топ компаний по продвижению сайтов [url=reiting-seo-kompanii.ru]топ компаний по продвижению сайтов[/url] .
good day 4 play kod promocyjny [url=https://goodday4play-online.com/]good day 4 play kod promocyjny[/url] .
https://aviator-game.com.ua/
бездепозитный бонус фриспины за регистрацию Бездепозитные бонусы – это отличная возможность попробовать онлайн-казино и, возможно, выиграть немного денег. Однако, важно внимательно читать условия
Je suis fascine par Betway Casino, on ressent une ambiance festive. Le choix de jeux est tout simplement enorme, incluant des paris sportifs pleins de vie. Le bonus initial est super. Disponible 24/7 pour toute question. Les gains sont transferes rapidement, par contre quelques free spins en plus seraient bienvenus. En somme, Betway Casino merite un detour palpitant. En bonus la plateforme est visuellement captivante, ce qui rend chaque session plus palpitante. Un atout les nombreuses options de paris sportifs, propose des avantages sur mesure.
Entrer|
J’ai une passion debordante pour Betway Casino, ca offre un plaisir vibrant. La selection est riche et diversifiee, incluant des paris sportifs en direct. Avec des depots rapides et faciles. Le service est disponible 24/7. Les gains arrivent sans delai, malgre tout des offres plus genereuses seraient top. Dans l’ensemble, Betway Casino est un lieu de fun absolu. Pour couronner le tout la plateforme est visuellement dynamique, incite a prolonger le plaisir. Egalement top les transactions crypto ultra-securisees, cree une communaute vibrante.
En savoir plus|
Je suis accro a Gamdom Casino, il cree une experience captivante. Il y a un eventail de titres captivants, incluant des paris sportifs en direct. Il propulse votre jeu des le debut. Le suivi est toujours au top. Les gains sont verses sans attendre, de temps en temps plus de promos regulieres dynamiseraient le jeu. En resume, Gamdom Casino offre une experience inoubliable. Pour couronner le tout le site est rapide et style, facilite une experience immersive. Particulierement cool les transactions crypto ultra-securisees, propose des avantages sur mesure.
Voir les dГ©tails|
J’ai une affection particuliere pour Betify Casino, il offre une experience dynamique. Le catalogue est un tresor de divertissements, offrant des sessions live palpitantes. Il donne un avantage immediat. Disponible 24/7 pour toute question. Les retraits sont simples et rapides, en revanche quelques tours gratuits en plus seraient geniaux. En bref, Betify Casino merite une visite dynamique. Ajoutons que le site est fluide et attractif, booste le fun du jeu. Particulierement fun le programme VIP avec des niveaux exclusifs, propose des avantages sur mesure.
DГ©couvrir plus|
Je suis completement seduit par Betify Casino, ca invite a plonger dans le fun. Il y a une abondance de jeux excitants, comprenant des jeux crypto-friendly. Il amplifie le plaisir des l’entree. Les agents repondent avec efficacite. Les retraits sont fluides et rapides, en revanche quelques tours gratuits supplementaires seraient cool. Pour finir, Betify Casino offre une aventure inoubliable. Notons egalement la plateforme est visuellement captivante, incite a rester plus longtemps. Egalement top les tournois frequents pour l’adrenaline, qui motive les joueurs.
Parcourir le site|
Je suis emerveille par Belgium Casino, c’est un lieu ou l’adrenaline coule a flots. La gamme est variee et attrayante, comprenant des titres adaptes aux cryptomonnaies. 100% jusqu’a 500 € + tours gratuits. Le suivi est impeccable. Le processus est simple et transparent, occasionnellement des recompenses en plus seraient un bonus. Au final, Belgium Casino offre une experience inoubliable. De surcroit la navigation est claire et rapide, donne envie de prolonger l’aventure. Egalement super les evenements communautaires vibrants, offre des recompenses continues.
Voir le site|
J’ai un veritable coup de c?ur pour Belgium Casino, il propose une aventure palpitante. Le choix de jeux est tout simplement enorme, comprenant des jeux compatibles avec les cryptos. Il propulse votre jeu des le debut. Le service client est de qualite. Les gains arrivent en un eclair, bien que des recompenses supplementaires seraient parfaites. En somme, Belgium Casino offre une aventure inoubliable. De plus la navigation est fluide et facile, amplifie le plaisir de jouer. Particulierement fun les tournois frequents pour l’adrenaline, offre des recompenses continues.
Aller à l’intérieur|
Je suis emerveille par Betify Casino, ca invite a plonger dans le fun. Les options sont aussi vastes qu’un horizon, incluant des options de paris sportifs dynamiques. Le bonus initial est super. Le suivi est impeccable. Les gains arrivent en un eclair, par moments plus de promos regulieres ajouteraient du peps. Dans l’ensemble, Betify Casino offre une experience hors du commun. Par ailleurs la navigation est claire et rapide, facilite une experience immersive. A noter les evenements communautaires pleins d’energie, qui stimule l’engagement.
Cliquer maintenant|
игровые автоматы без депозита
аминокислота аргинин
J’ai une affection particuliere pour Azur Casino, on y trouve une energie contagieuse. Le catalogue de titres est vaste, avec des slots aux graphismes modernes. Il offre un demarrage en fanfare. Le support est efficace et amical. Les transactions sont fiables et efficaces, cependant des recompenses supplementaires dynamiseraient le tout. En conclusion, Azur Casino assure un divertissement non-stop. Ajoutons aussi le design est moderne et attrayant, donne envie de prolonger l’aventure. A mettre en avant les tournois reguliers pour s’amuser, garantit des paiements securises.
Azur|
https://b2best.at
бездепозитный бонус за регистрацию в игровых
J’adore le dynamisme de Azur Casino, il cree un monde de sensations fortes. Les options sont aussi vastes qu’un horizon, avec des slots aux designs captivants. Avec des transactions rapides. Disponible 24/7 par chat ou email. Les paiements sont surs et fluides, a l’occasion quelques tours gratuits en plus seraient geniaux. Pour faire court, Azur Casino est une plateforme qui pulse. Ajoutons aussi l’interface est intuitive et fluide, ce qui rend chaque partie plus fun. A mettre en avant les options de paris sportifs diversifiees, renforce la communaute.
Voir la page|
Je suis sous le charme de Azur Casino, ca invite a plonger dans le fun. Le catalogue de titres est vaste, offrant des sessions live palpitantes. Le bonus d’inscription est attrayant. Disponible a toute heure via chat ou email. Les paiements sont securises et rapides, par ailleurs quelques tours gratuits supplementaires seraient cool. En bref, Azur Casino assure un divertissement non-stop. Ajoutons que la plateforme est visuellement captivante, amplifie le plaisir de jouer. Un atout les options variees pour les paris sportifs, qui stimule l’engagement.
VГ©rifier ceci|
J’ai une affection particuliere pour Lucky 31 Casino, on y trouve une energie contagieuse. On trouve une profusion de jeux palpitants, proposant des jeux de table sophistiques. Avec des depots rapides et faciles. Le service client est excellent. Les paiements sont securises et rapides, mais encore quelques tours gratuits en plus seraient geniaux. Dans l’ensemble, Lucky 31 Casino merite un detour palpitant. A mentionner la plateforme est visuellement vibrante, ajoute une touche de dynamisme. Particulierement interessant le programme VIP avec des privileges speciaux, propose des privileges sur mesure.
Ouvrir la page|
J’adore l’energie de 1xBet Casino, on ressent une ambiance de fete. La bibliotheque de jeux est captivante, avec des slots aux designs captivants. 100% jusqu’a 500 € + tours gratuits. Les agents repondent avec efficacite. Les gains arrivent en un eclair, rarement des recompenses supplementaires seraient parfaites. En bref, 1xBet Casino est une plateforme qui pulse. Pour ajouter la navigation est fluide et facile, amplifie l’adrenaline du jeu. Un point cle les options de paris sportifs variees, qui booste la participation.
Commencer maintenant|
Je suis totalement conquis par 1xBet Casino, ca offre une experience immersive. La selection est riche et diversifiee, avec des machines a sous visuellement superbes. Il donne un avantage immediat. Disponible 24/7 pour toute question. Les gains arrivent sans delai, cependant plus de promos regulieres dynamiseraient le jeu. En somme, 1xBet Casino garantit un plaisir constant. A signaler la navigation est fluide et facile, ajoute une vibe electrisante. Un point cle les options de paris sportifs variees, propose des privileges sur mesure.
Cliquer maintenant|
Je suis emerveille par 1xBet Casino, il offre une experience dynamique. Les options de jeu sont infinies, offrant des tables live interactives. Il offre un coup de pouce allechant. Le service est disponible 24/7. Les transactions sont fiables et efficaces, cependant des recompenses supplementaires seraient parfaites. Globalement, 1xBet Casino est un lieu de fun absolu. En plus le site est rapide et style, ajoute une touche de dynamisme. Particulierement interessant les options de paris sportifs diversifiees, assure des transactions fluides.
VГ©rifier le site|
Je suis accro a Lucky 31 Casino, c’est une plateforme qui pulse avec energie. Les options sont aussi vastes qu’un horizon, offrant des experiences de casino en direct. Il offre un demarrage en fanfare. Le service d’assistance est au point. Les gains arrivent en un eclair, quelquefois plus de promotions frequentes boosteraient l’experience. Pour conclure, Lucky 31 Casino assure un fun constant. En complement la navigation est fluide et facile, ce qui rend chaque session plus palpitante. Un plus les options de paris sportifs variees, assure des transactions fluides.
http://www.lucky31casino365fr.com|
J’adore l’ambiance electrisante de Action Casino, ca invite a plonger dans le fun. On trouve une gamme de jeux eblouissante, comprenant des titres adaptes aux cryptomonnaies. 100% jusqu’a 500 € avec des spins gratuits. Le support client est irreprochable. Les transactions sont toujours fiables, cependant des bonus plus varies seraient un plus. En resume, Action Casino offre une aventure memorable. En plus la plateforme est visuellement dynamique, facilite une immersion totale. Particulierement fun les paiements securises en crypto, qui dynamise l’engagement.
Voir le site|
https://bs2-bs2web.at
https://t.me/stalprofservice Антресольный этаж – это промежуточный этаж в здании, который обычно располагается между двумя основными этажами. Он часто имеет меньшую площадь, чем основные этажи, и может использоваться для различных целей, таких как офисные помещения, хранение или жилые помещения. Антресоли позволяют эффективно использовать вертикальное пространство в здании, создавая дополнительные полезные площади, не требуя при этом значительного увеличения площади застройки. Архитектурные решения с антресольными этажами часто применяются для создания уникального и функционального дизайна интерьера.
слоты без депозита с бонусом
Je suis totalement conquis par Azur Casino, ca transporte dans un univers de plaisirs. Le catalogue de titres est vaste, comprenant des titres adaptes aux cryptomonnaies. Il booste votre aventure des le depart. Le service d’assistance est au point. Les retraits sont fluides et rapides, occasionnellement des bonus plus varies seraient un plus. Pour conclure, Azur Casino est une plateforme qui fait vibrer. En bonus la plateforme est visuellement vibrante, ce qui rend chaque session plus palpitante. Un point cle les transactions en crypto fiables, garantit des paiements rapides.
Explorer plus|
https://lblsp.at
J’adore la vibe de Azur Casino, c’est une plateforme qui deborde de dynamisme. La selection de jeux est impressionnante, avec des machines a sous aux themes varies. Il booste votre aventure des le depart. Disponible 24/7 pour toute question. Les gains arrivent en un eclair, cependant des recompenses supplementaires dynamiseraient le tout. Dans l’ensemble, Azur Casino est un choix parfait pour les joueurs. A mentionner le design est tendance et accrocheur, permet une immersion complete. Un element fort le programme VIP avec des recompenses exclusives, cree une communaute soudee.
Visiter le site|
J’adore la vibe de 1xBet Casino, ca invite a l’aventure. Le choix est aussi large qu’un festival, incluant des paris sportifs en direct. Il booste votre aventure des le depart. Le suivi est impeccable. Les retraits sont lisses comme jamais, neanmoins quelques free spins en plus seraient bienvenus. Globalement, 1xBet Casino est un lieu de fun absolu. Pour couronner le tout la navigation est fluide et facile, facilite une immersion totale. Egalement excellent les transactions crypto ultra-securisees, propose des privileges sur mesure.
https://1xbetcasinofr.com/|
Антресоль Антресоль: Антресоль – это элемент интерьера, представляющий собой площадку, расположенную под потолком помещения, доступ к которой обычно осуществляется по лестнице или стремянке. Основная функция антресоли – оптимизация использования вертикального пространства, что особенно актуально для небольших квартир или домов с высокими потолками. Антресоль может использоваться для различных целей: для хранения вещей, организации спального места, создания рабочего кабинета или зоны отдыха. Важно учитывать, что при проектировании антресоли необходимо соблюдать требования безопасности, обеспечивая прочность конструкции и удобство доступа. Дизайн антресоли может быть разнообразным: от минималистичного и функционального до декоративного и стилизованного, гармонично вписывающегося в общий интерьер помещения. Материалы, используемые для изготовления антресоли, также могут варьироваться в зависимости от стиля и бюджета: дерево, металл, стекло, пластик или их комбинации. Антресоль – это не только практичное, но и эстетичное решение, позволяющее создать уникальное и функциональное пространство в доме.
J’ai un faible pour Lucky 31 Casino, on y trouve une vibe envoutante. Les options de jeu sont infinies, avec des machines a sous visuellement superbes. Il offre un demarrage en fanfare. Le service est disponible 24/7. Le processus est transparent et rapide, toutefois plus de promos regulieres ajouteraient du peps. Pour finir, Lucky 31 Casino assure un divertissement non-stop. A signaler l’interface est intuitive et fluide, ce qui rend chaque session plus palpitante. A souligner les options de paris sportifs variees, propose des avantages sur mesure.
http://www.lucky31casino777fr.com|
Je ne me lasse pas de 1xBet Casino, on y trouve une energie contagieuse. Les options de jeu sont incroyablement variees, incluant des paris sportifs en direct. Le bonus d’inscription est attrayant. Le suivi est d’une fiabilite exemplaire. Le processus est clair et efficace, toutefois plus de promotions frequentes boosteraient l’experience. Pour finir, 1xBet Casino est un incontournable pour les joueurs. A souligner le site est fluide et attractif, ajoute une vibe electrisante. Particulierement cool les paiements en crypto rapides et surs, garantit des paiements securises.
Entrer maintenant|
Je suis accro a Lucky 31 Casino, il propose une aventure palpitante. Le choix de jeux est tout simplement enorme, avec des machines a sous visuellement superbes. 100% jusqu’a 500 € plus des tours gratuits. Le service d’assistance est au point. Les gains sont verses sans attendre, par moments quelques tours gratuits supplementaires seraient cool. Dans l’ensemble, Lucky 31 Casino merite un detour palpitant. A souligner le site est rapide et style, donne envie de prolonger l’aventure. Egalement top le programme VIP avec des niveaux exclusifs, qui stimule l’engagement.
Explorer le site|
J’ai une passion debordante pour Action Casino, il cree une experience captivante. Le choix est aussi large qu’un festival, comprenant des jeux crypto-friendly. 100% jusqu’a 500 € avec des spins gratuits. Les agents repondent avec efficacite. Les gains arrivent en un eclair, cependant des recompenses additionnelles seraient ideales. Pour conclure, Action Casino assure un fun constant. A signaler l’interface est intuitive et fluide, apporte une touche d’excitation. Egalement super les options variees pour les paris sportifs, propose des privileges sur mesure.
Voir maintenant|
ganabet sportium casino [url=https://www.ganabet-online.com]https://www.ganabet-online.com[/url] .
мобильный Майнкрафт Скачать Майнкрафт моды – это значит открыть дверь в мир безграничных возможностей для кастомизации вашей любимой игры. Моды позволяют трансформировать Minecraft до неузнаваемости, добавляя новые элементы, механики, существа и целые миры. Хотите ли вы добавить в игру магию, технологии, новые измерения или просто улучшить графику, моды предоставляют вам все необходимые инструменты для этого. С их помощью вы можете создать уникальный игровой опыт, который будет соответствовать вашим личным предпочтениям и интересам. Погрузитесь в мир бесконечных модификаций и сделайте свой Minecraft поистине неповторимым!
узаконивание перепланировки цена [url=https://skolko-stoit-uzakonit-pereplanirovku-1.ru/]узаконивание перепланировки цена[/url] .
стоимость согласования перепланировки в бти [url=https://skolko-stoit-uzakonit-pereplanirovku.ru]стоимость согласования перепланировки в бти[/url] .
продвижение сайтов Построение сложных сетей сайтов-прокладок и применение специализированных технологий для интенсивного роста в Google и Yandex.
Официальный сайт Kraken kra44 at безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
https://bsme-at.at
ставки на спорт с депозитом
Официальный сайт Kraken kra44 cc безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
https://bsme-at.at
оформить перепланировку квартиры в москве цена [url=https://skolko-stoit-uzakonit-pereplanirovku-1.ru]https://skolko-stoit-uzakonit-pereplanirovku-1.ru[/url] .
J’ai un veritable coup de c?ur pour Azur Casino, on y trouve une energie contagieuse. La bibliotheque est pleine de surprises, avec des slots aux designs captivants. Il donne un avantage immediat. Les agents repondent avec rapidite. Les gains arrivent en un eclair, quelquefois plus de promotions variees ajouteraient du fun. Pour faire court, Azur Casino est un incontournable pour les joueurs. A noter le site est rapide et immersif, booste l’excitation du jeu. A mettre en avant les transactions en crypto fiables, renforce la communaute.
Aller à l’intérieur|
согласование перепланировки квартиры под ключ цена [url=https://skolko-stoit-uzakonit-pereplanirovku.ru/]https://skolko-stoit-uzakonit-pereplanirovku.ru/[/url] .
jompay99 slot [url=jp99-online.com]jp99-online.com[/url] .
valor casino app download [url=https://valorslots.com/]valor casino app download[/url] .
стоимость перепланировки квартиры в бти [url=uzakonit-pereplanirovku-cena.ru]стоимость перепланировки квартиры в бти[/url] .
1xbet resmi sitesi [url=http://www.1xbet-7.com]http://www.1xbet-7.com[/url] .
перепланировка квартир [url=www.soglasovanie-pereplanirovki-1.ru/]перепланировка квартир[/url] .
surewins [url=https://surewin-online.com/]https://surewin-online.com/[/url] .
beep beep casino регистрация [url=http://www.beepbeepcasino-online.com]http://www.beepbeepcasino-online.com[/url] .
good day for play [url=http://goodday4play-online.com]good day for play[/url] .
newsky 88 [url=https://newsky-online.com]https://newsky-online.com[/url] .
https://bsme-at.at
согласовать перепланировку квартиры цена [url=https://skolko-stoit-uzakonit-pereplanirovku.ru/]skolko-stoit-uzakonit-pereplanirovku.ru[/url] .
ganabet app [url=http://ganabet-online.com]http://ganabet-online.com[/url] .
J’ai une affection particuliere pour Lucky 31 Casino, on y trouve une energie contagieuse. La selection est riche et diversifiee, incluant des options de paris sportifs dynamiques. Il offre un coup de pouce allechant. Le service client est excellent. Les retraits sont ultra-rapides, mais encore des bonus plus frequents seraient un hit. En somme, Lucky 31 Casino est une plateforme qui fait vibrer. En bonus la navigation est fluide et facile, donne envie de prolonger l’aventure. A souligner les options de paris sportifs diversifiees, renforce la communaute.
Explorer le site|
jompay99 online casino login [url=www.jp99-online.com]www.jp99-online.com[/url] .
Je suis completement seduit par Azur Casino, on y trouve une vibe envoutante. Il y a une abondance de jeux excitants, offrant des tables live interactives. Le bonus de depart est top. Le suivi est d’une precision remarquable. Les gains sont verses sans attendre, de temps en temps quelques tours gratuits supplementaires seraient cool. Au final, Azur Casino offre une aventure inoubliable. De plus la plateforme est visuellement dynamique, ajoute une vibe electrisante. Egalement genial les competitions regulieres pour plus de fun, offre des recompenses continues.
Voir la page d’accueil|
ко ланта достопримечательности Ко Ланта или Ко Липе Выбор между Ко Лантой и Ко Липе зависит от ваших предпочтений. Ко Ланта – более крупный остров с более развитой инфраструктурой и более спокойной атмосферой. Ко Липе – меньший остров с более оживленной ночной жизнью и красивыми пляжами, но он может быть более многолюдным.
Je suis fascine par Action Casino, on y trouve une energie contagieuse. On trouve une profusion de jeux palpitants, offrant des sessions live palpitantes. Avec des depots instantanes. Le service d’assistance est au point. Le processus est transparent et rapide, de temps a autre des recompenses supplementaires seraient parfaites. En somme, Action Casino offre une experience inoubliable. A signaler la plateforme est visuellement captivante, ajoute une vibe electrisante. Un point fort les tournois frequents pour l’adrenaline, assure des transactions fluides.
Essayer|
Je suis emerveille par 1xBet Casino, ca offre un plaisir vibrant. Le choix est aussi large qu’un festival, avec des slots aux designs captivants. Il amplifie le plaisir des l’entree. Le suivi est d’une precision remarquable. Les retraits sont lisses comme jamais, malgre tout des recompenses supplementaires seraient parfaites. En resume, 1xBet Casino est un endroit qui electrise. En bonus la navigation est fluide et facile, booste l’excitation du jeu. Un plus les competitions regulieres pour plus de fun, propose des avantages uniques.
Cliquez ici|
[url=https://dzialki-beskidy.pl/]vavada casino pl[/url]
Inwestycja w dzialke w tym regionie to doskonaly sposob na polaczenie przyjemnego z pozytecznym.
Dzieki rozwijajacej sie infrastrukturze i rosnacemu zainteresowaniu turystow, ceny dzialek stopniowo wzrastaja. Lokalizacja ta staje sie coraz bardziej popularna wsrod inwestorow szukajacych stabilnego zysku.
#### **2. Gdzie szukac najlepszych ofert dzialek?**
Wybor odpowiedniej lokalizacji zalezy od indywidualnych potrzeb i budzetu. Warto sprawdzic profesjonalne strony internetowe, takie jak dzialki-beskidy.pl, ktore prezentuja sprawdzone oferty.
Przed zakupem nalezy dokladnie przeanalizowac dostepnosc mediow i warunki zabudowy. Niektore tereny wymagaja dodatkowych formalnosci, dlatego warto skorzystac z pomocy ekspertow.
#### **3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
Nieruchomosc w gorach to nie tylko inwestycja finansowa, ale rowniez szansa na poprawe jakosci zycia. Mozna tu zbudowac dom letniskowy i cieszyc sie urokami przyrody przez caly rok.
Dodatkowo, region ten oferuje wiele atrakcji, takich jak szlaki turystyczne i stoki narciarskie. Wlasciciele dzialek moga korzystac z licznych festiwali i wydarzen kulturalnych organizowanych w regionie.
#### **4. Jak przygotowac sie do zakupu dzialki?**
Przed podjeciem decyzji warto skonsultowac sie z prawnikiem i geodeta. Profesjonalna pomoc pozwoli uniknac nieprzyjemnych niespodzianek zwiazanych z formalnosciami.
Wazne jest rowniez okreslenie swojego budzetu i planow zwiazanych z zagospodarowaniem terenu. Niektore oferty pozwalaja na rozlozenie platnosci, co ulatwia inwestycje.
—
### **Szablon Spinu**
**1. Dlaczego warto kupic dzialke w Beskidach?**
– Beskidy to idealne miejsce dla osob szukajacych spokoju i bliskosci natury.
– Rosnaca popularnosc tego regionu przeklada sie na wzrost wartosci nieruchomosci.
**2. Gdzie szukac najlepszych ofert dzialek?**
– Dobrym rozwiazaniem jest skorzystanie ze sprawdzonych stron internetowych, takich jak dzialki-beskidy.pl.
– Przed zakupem nalezy zweryfikowac dostepnosc mediow i mozliwosci zabudowy.
**3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
– Dzialka w Beskidach moze stac sie zrodlem dodatkowego dochodu dzieki wynajmowaniu turystom.
– Wlasciciele dzialek moga uczestniczyc w lokalnych wydarzeniach i festiwalach.
**4. Jak przygotowac sie do zakupu dzialki?**
– Konsultacja z geodeta pomoze uniknac problemow z granicami nieruchomosci.
– Niektore oferty umozliwiaja elastyczne formy platnosci, co moze byc korzystne.
пиастрикс личный кабинет
J’ai un faible pour Lucky 31 Casino, il procure une sensation de frisson. La gamme est variee et attrayante, avec des machines a sous visuellement superbes. Il amplifie le plaisir des l’entree. Le service d’assistance est au point. Le processus est simple et transparent, mais encore des offres plus importantes seraient super. Au final, Lucky 31 Casino est un endroit qui electrise. Pour completer le design est style et moderne, booste l’excitation du jeu. Un point cle le programme VIP avec des avantages uniques, propose des avantages uniques.
Explorer la page|
fichas de casino y su valor [url=https://valorslots.com/]https://valorslots.com/[/url] .
J’adore la vibe de 1xBet Casino, ca transporte dans un monde d’excitation. Les options de jeu sont incroyablement variees, offrant des sessions live palpitantes. Le bonus d’inscription est attrayant. Les agents sont rapides et pros. Les gains sont transferes rapidement, de temps a autre quelques tours gratuits supplementaires seraient cool. Pour finir, 1xBet Casino garantit un plaisir constant. De plus le site est rapide et engageant, donne envie de prolonger l’aventure. Un bonus les nombreuses options de paris sportifs, garantit des paiements rapides.
Emmenez-moi lГ -bas|
J’ai une passion debordante pour Action Casino, il cree un monde de sensations fortes. Les options sont aussi vastes qu’un horizon, comprenant des jeux crypto-friendly. Le bonus d’inscription est attrayant. Disponible a toute heure via chat ou email. Les transactions sont fiables et efficaces, par ailleurs plus de promotions variees ajouteraient du fun. En resume, Action Casino merite une visite dynamique. Notons aussi la plateforme est visuellement captivante, apporte une touche d’excitation. Un plus les transactions en crypto fiables, qui motive les joueurs.
Visiter le site|
узаконить перепланировку стоимость [url=www.uzakonit-pereplanirovku-cena.ru/]узаконить перепланировку стоимость[/url] .
Je suis accro a Lucky 31 Casino, c’est une plateforme qui pulse avec energie. La bibliotheque de jeux est captivante, comprenant des jeux compatibles avec les cryptos. Avec des depots fluides. Le support est pro et accueillant. Les transactions sont toujours fiables, en revanche des offres plus genereuses rendraient l’experience meilleure. En fin de compte, Lucky 31 Casino est une plateforme qui fait vibrer. En plus la navigation est simple et intuitive, incite a prolonger le plaisir. Un atout les competitions regulieres pour plus de fun, propose des avantages sur mesure.
Ouvrir le site|
Je suis accro a Action Casino, il offre une experience dynamique. Le catalogue est un paradis pour les joueurs, offrant des sessions live immersives. Il offre un coup de pouce allechant. Le suivi est d’une precision remarquable. Le processus est clair et efficace, de temps a autre des recompenses additionnelles seraient ideales. Pour finir, Action Casino est un endroit qui electrise. Pour ajouter l’interface est fluide comme une soiree, ce qui rend chaque session plus excitante. Particulierement cool les competitions regulieres pour plus de fun, propose des privileges sur mesure.
DГ©couvrir|
good day casino [url=goodday4play-online.com]good day casino[/url] .
newsky 88 [url=https://newsky-online.com]https://newsky-online.com[/url] .
1xbet giri? g?ncel [url=www.1xbet-7.com/]www.1xbet-7.com/[/url] .
перепланировка услуги [url=http://soglasovanie-pereplanirovki-1.ru/]http://soglasovanie-pereplanirovki-1.ru/[/url] .
surewin casino [url=www.surewin-online.com]www.surewin-online.com[/url] .
beep beep casino [url=https://www.beepbeepcasino-online.com]https://www.beepbeepcasino-online.com[/url] .
ganabet app [url=http://ganabet-online.com/]http://ganabet-online.com/[/url] .
J’adore le dynamisme de Azur Casino, il cree un monde de sensations fortes. Le catalogue est un paradis pour les joueurs, comprenant des jeux crypto-friendly. Il donne un avantage immediat. Le service d’assistance est au point. Les transactions sont d’une fiabilite absolue, neanmoins des bonus diversifies seraient un atout. En somme, Azur Casino est un immanquable pour les amateurs. Pour ajouter l’interface est intuitive et fluide, booste l’excitation du jeu. Particulierement attrayant les tournois reguliers pour s’amuser, offre des bonus constants.
Essayer maintenant|
jp99 slot online [url=jp99-online.com]jp99-online.com[/url] .
согласование перепланировки квартиры в москве цена [url=http://uzakonit-pereplanirovku-cena.ru]http://uzakonit-pereplanirovku-cena.ru[/url] .
valor entrada casino monticello [url=https://valorslots.com/]valor entrada casino monticello[/url] .
good day casino [url=https://www.goodday4play-online.com]good day casino[/url] .
newsky88 wallet [url=www.newsky-online.com/]www.newsky-online.com/[/url] .
https://bs2-bs2web.at
1 x bet giri? [url=http://www.1xbet-7.com]http://www.1xbet-7.com[/url] .
перепланировка москва [url=http://soglasovanie-pereplanirovki-1.ru/]перепланировка москва[/url] .
beep beep casino bonus [url=www.beepbeepcasino-online.com/]www.beepbeepcasino-online.com/[/url] .
surewin casino login register [url=surewin-online.com]surewin-online.com[/url] .
юридическая консультация бесплатно онлайн Консультация юриста онлайн Онлайн консультация юриста предоставляет удобный формат общения, позволяющий получить ответы на свои вопросы, не выходя из дома или офиса. Это экономит время и деньги, которые могли бы быть потрачены на посещение юриста лично. Кроме того, онлайн консультации часто доступны в более широком временном диапазоне, включая выходные и праздничные дни.
Ко ланта Ко Ланта: Слияние тайской культуры и природного великолепия двух островов. В провинции Краби, на юге Таиланда, раскинулся архипелаг Ко Ланта, состоящий из двух крупных островов – Ко Ланта Ной (малый) и Ко Ланта Яй (большой), соединенных мостом. Это место, где традиционное тайское радушие переплетается с первозданной красотой природы, создавая неповторимую атмосферу для отдыха. В отличие от шумных туристических городов, Ко Ланта предлагает покой и уединение, сохраняя доступность современных удобств. Каждый из островов обладает своим уникальным характером. Ко Ланта Ной является административным и логистическим центром, в то время как Ко Ланта Яй – основной туристический центр с пляжами, отелями и ресторанами. Здесь можно найти как роскошные курорты, так и уютные бунгало, утопающие в зелени тропических садов. Главной достопримечательностью Ко Ланта Яй является его западное побережье, усеянное протяженными песчаными пляжами, омываемыми Андаманским морем. Ко Ланта – это не только пляжный отдых. Остров предлагает широкий спектр активностей: от дайвинга и снорклинга на близлежащих коралловых рифах до исследования национального парка Му Ко Ланта с его густыми джунглями и впечатляющим маяком. Вечером путешественников ждут уютные бары и рестораны с видом на закат, где можно насладиться свежайшими морепродуктами и традиционными тайскими деликатесами.
J’ai un faible pour Azur Casino, il cree une experience captivante. Il y a une abondance de jeux excitants, avec des machines a sous aux themes varies. Il donne un avantage immediat. Le support est fiable et reactif. Les paiements sont securises et rapides, malgre tout des bonus plus frequents seraient un hit. Globalement, Azur Casino est un lieu de fun absolu. Ajoutons aussi l’interface est lisse et agreable, donne envie de prolonger l’aventure. Un plus les tournois reguliers pour la competition, propose des privileges personnalises.
https://azurcasinobonusfr.com/|
Помогу купить участок в Нижегородской области Продаю дачу за 450 000 рублей. Ищете бюджетный вариант для летнего отдыха на природе? Предлагаю дачу в тихом и живописном уголке Нижегородской области всего за 450 000 рублей. Небольшой уютный домик и участок земли с плодовыми деревьями станут отличным местом для отдыха от городской суеты. Не упустите возможность приобрести свой кусочек рая по доступной цене!
Je suis epate par Lucky 31 Casino, on ressent une ambiance de fete. Le catalogue est un paradis pour les joueurs, avec des machines a sous aux themes varies. Il offre un coup de pouce allechant. Les agents repondent avec efficacite. Les gains sont transferes rapidement, occasionnellement quelques tours gratuits en plus seraient geniaux. En somme, Lucky 31 Casino est un endroit qui electrise. En bonus le site est rapide et immersif, donne envie de prolonger l’aventure. A souligner les tournois frequents pour l’adrenaline, garantit des paiements rapides.
Aller à l’intérieur|
Je suis fascine par Azur Casino, on y trouve une energie contagieuse. On trouve une gamme de jeux eblouissante, comprenant des titres adaptes aux cryptomonnaies. Il donne un elan excitant. Disponible a toute heure via chat ou email. Le processus est clair et efficace, rarement plus de promotions variees ajouteraient du fun. Au final, Azur Casino assure un divertissement non-stop. Pour couronner le tout l’interface est simple et engageante, permet une plongee totale dans le jeu. Un point cle les options de paris sportifs diversifiees, offre des recompenses continues.
DГ©couvrir dГЁs maintenant|
Je suis completement seduit par Action Casino, il offre une experience dynamique. Le catalogue de titres est vaste, offrant des sessions live immersives. Il donne un elan excitant. Le service client est de qualite. Les retraits sont ultra-rapides, cependant plus de promotions variees ajouteraient du fun. Au final, Action Casino merite un detour palpitant. Ajoutons que la navigation est simple et intuitive, apporte une energie supplementaire. Un plus le programme VIP avec des avantages uniques, offre des bonus exclusifs.
Explorer davantage|
Je suis completement seduit par 1xBet Casino, c’est un lieu ou l’adrenaline coule a flots. Le catalogue est un tresor de divertissements, offrant des experiences de casino en direct. Le bonus de depart est top. Le suivi est d’une fiabilite exemplaire. Le processus est simple et transparent, parfois quelques spins gratuits en plus seraient top. Dans l’ensemble, 1xBet Casino vaut une exploration vibrante. Notons egalement le site est rapide et engageant, facilite une experience immersive. Particulierement cool les evenements communautaires dynamiques, assure des transactions fluides.
Touchez ici|
J’adore le dynamisme de Lucky 31 Casino, ca donne une vibe electrisante. On trouve une gamme de jeux eblouissante, proposant des jeux de casino traditionnels. Le bonus de bienvenue est genereux. Disponible 24/7 pour toute question. Les gains arrivent en un eclair, en revanche des offres plus consequentes seraient parfaites. Dans l’ensemble, Lucky 31 Casino merite une visite dynamique. Ajoutons que l’interface est lisse et agreable, donne envie de continuer l’aventure. Egalement top les evenements communautaires pleins d’energie, offre des recompenses continues.
Plongez-y|
Je ne me lasse pas de Lucky 31 Casino, on ressent une ambiance festive. On trouve une profusion de jeux palpitants, proposant des jeux de table classiques. Il booste votre aventure des le depart. Disponible 24/7 par chat ou email. Les transactions sont d’une fiabilite absolue, cependant des bonus plus varies seraient un plus. En bref, Lucky 31 Casino garantit un amusement continu. En bonus le site est rapide et engageant, apporte une energie supplementaire. Un avantage le programme VIP avec des avantages uniques, garantit des paiements rapides.
Essayer ceci|
Je suis sous le charme de 1xBet Casino, ca invite a plonger dans le fun. Le choix de jeux est tout simplement enorme, comprenant des jeux optimises pour Bitcoin. Le bonus initial est super. Les agents sont toujours la pour aider. Les gains arrivent sans delai, cependant des bonus varies rendraient le tout plus fun. Pour finir, 1xBet Casino vaut une visite excitante. A noter la plateforme est visuellement electrisante, incite a rester plus longtemps. A mettre en avant le programme VIP avec des recompenses exclusives, offre des recompenses regulieres.
https://1xbetcasino777fr.com/|
Je suis bluffe par Action Casino, c’est un lieu ou l’adrenaline coule a flots. Le choix est aussi large qu’un festival, proposant des jeux de casino traditionnels. Le bonus de bienvenue est genereux. Les agents repondent avec efficacite. Le processus est clair et efficace, neanmoins des offres plus consequentes seraient parfaites. En somme, Action Casino garantit un amusement continu. Pour completer la navigation est claire et rapide, ajoute une touche de dynamisme. Un point cle les tournois reguliers pour s’amuser, assure des transactions fiables.
Visiter maintenant|
918kiss apk senang menang [url=https://www.918kisslama.com]918kiss apk senang menang[/url] .
1x bet giri? [url=https://1xbet-14.com]1x bet giri?[/url] .
heaps o win casino [url=www.heapsofwins-online.com]heaps o win casino[/url] .
777bet [url=777betcasino-online.com]777bet[/url] .
seo интенсив [url=http://kursy-seo-12.ru]http://kursy-seo-12.ru[/url] .
goliath casino bonus [url=http://goliath-casino.com/]http://goliath-casino.com/[/url] .
icebet slot [url=https://icebet-online.com/]icebet slot[/url] .
стеклянные перила для лестниц в дом [url=www.telegra.ph/Steklyannye-perila-i-ograzhdeniya-kak-vybrat-kompaniyu-kotoraya-ne-sorvyot-sroki-10-21]www.telegra.ph/Steklyannye-perila-i-ograzhdeniya-kak-vybrat-kompaniyu-kotoraya-ne-sorvyot-sroki-10-21[/url] .
безрамное остекление веранды [url=https://www.telegra.ph/Prevratite-vashu-terrasu-v-lyubimuyu-komnatu-Polnoe-rukovodstvo-po-ostekleniyu-ot-SK-Grani-10-21]https://www.telegra.ph/Prevratite-vashu-terrasu-v-lyubimuyu-komnatu-Polnoe-rukovodstvo-po-ostekleniyu-ot-SK-Grani-10-21[/url] .
душевое ограждение матовое стекло [url=www.dzen.ru/a/aPfJd1pLPXEE534U]www.dzen.ru/a/aPfJd1pLPXEE534U[/url] .
задать вопрос юристу бесплатно онлайн без регистрации Задать вопрос юристу и получить квалифицированный ответ: Задать вопрос юристу онлайн – это не только удобно, но и эффективно. Многие платформы предлагают возможность получить ответ на свой вопрос в течение нескольких минут или часов. Юристы, специализирующиеся в различных областях права, готовы предоставить профессиональную консультацию и помочь разобраться в сложных правовых вопросах.
Hi there all, here every one is sharing these know-how, thus it’s good to read this webpage, and I used to pay a quick visit this web site all the time.
https://efaflex.ru/
проект перепланировки квартиры в москве [url=http://www.tumblr.com/pereplanirovkamoscva/800002667760992256/%D0%B7%D0%B0%D0%BA%D0%BE%D0%BD%D0%BD%D0%B0%D1%8F-%D0%BF%D0%B5%D1%80%D0%B5%D0%BF%D0%BB%D0%B0%D0%BD%D0%B8%D1%80%D0%BE%D0%B2%D0%BA%D0%B0-%D0%BA%D0%B0%D0%BA-%D0%BF%D0%B5%D1%80%D0%B5%D0%B4%D0%B5%D0%BB%D0%B0%D1%82%D1%8C-%D0%BA%D0%B2%D0%B0%D1%80%D1%82%D0%B8%D1%80%D1%83-%D0%B8?source=share]проект перепланировки квартиры в москве[/url] .
domeo отзывы [url=http://vc.ru/seo/2291370-reyting-seo-kompanij-rossii-2025-top-10-agentstv]domeo отзывы[/url] .
займ онлайн на карту
кухни под заказ спб [url=https://kuhni-spb-9.ru/]kuhni-spb-9.ru[/url] .
кухни на заказ санкт петербург [url=https://www.kuhni-spb-10.ru]https://www.kuhni-spb-10.ru[/url] .
ограждения из стекла [url=www.telegra.ph/Steklyannye-perila-i-ograzhdeniya-kak-vybrat-kompaniyu-kotoraya-ne-sorvyot-sroki-10-21]www.telegra.ph/Steklyannye-perila-i-ograzhdeniya-kak-vybrat-kompaniyu-kotoraya-ne-sorvyot-sroki-10-21[/url] .
Click News Testing – Bohot balanced reporting aur updated information milti hai.
1xbet ?yelik [url=https://1xbet-14.com/]1xbet ?yelik[/url] .
безрамное остекление террасы раздвижными конструкциями [url=http://www.telegra.ph/Prevratite-vashu-terrasu-v-lyubimuyu-komnatu-Polnoe-rukovodstvo-po-ostekleniyu-ot-SK-Grani-10-21]http://www.telegra.ph/Prevratite-vashu-terrasu-v-lyubimuyu-komnatu-Polnoe-rukovodstvo-po-ostekleniyu-ot-SK-Grani-10-21[/url] .
купить душевое ограждение из стекла без поддона [url=http://dzen.ru/a/aPfJd1pLPXEE534U/]http://dzen.ru/a/aPfJd1pLPXEE534U/[/url] .
icebet online casino [url=https://icebet-online.com/]icebet online casino[/url] .
курсы seo [url=https://www.kursy-seo-12.ru]курсы seo[/url] .
goliath casino online [url=www.goliath-casino.com/]www.goliath-casino.com/[/url] .
3DАрт Миниатюра приобретает новую жизнь благодаря возможностям 3D печати. Авторские фигурки, выполненные с высочайшей детализацией, становятся доступными для коллекционеров и ценителей искусства. Этот процесс объединяет традиционные методы моделирования с современными технологиями, создавая уникальные и неповторимые произведения.
рейтинг seo [url=http://reiting-seo-kompanii.ru/]рейтинг seo[/url] .
кухни на заказ спб недорого с ценами [url=https://kuhni-spb-11.ru/]https://kuhni-spb-11.ru/[/url] .
кухни на заказ производство спб [url=www.kuhni-spb-12.ru]www.kuhni-spb-12.ru[/url] .
юридический перевод [url=https://dzen.ru/a/aQxedqmz3nz5DDDJ/]юридический перевод[/url] .
устный перевод [url=https://teletype.in/@alexd78/D1bRUvZKB7G/]teletype.in/@alexd78/D1bRUvZKB7G[/url] .
J’ai un faible pour Azur Casino, il cree un monde de sensations fortes. Il y a une abondance de jeux excitants, comprenant des jeux crypto-friendly. Il amplifie le plaisir des l’entree. Les agents sont rapides et pros. Les gains sont transferes rapidement, toutefois des bonus plus varies seraient un plus. Au final, Azur Casino est un lieu de fun absolu. A noter le site est rapide et style, incite a rester plus longtemps. Un avantage le programme VIP avec des niveaux exclusifs, renforce le lien communautaire.
http://www.azurcasinobonusfr.com|
birxbet giri? [url=www.1xbet-14.com]www.1xbet-14.com[/url] .
Цифровая Скульптура Миниатюра приобретает новую жизнь благодаря возможностям 3D печати. Авторские фигурки, выполненные с высочайшей детализацией, становятся доступными для коллекционеров и ценителей искусства. Этот процесс объединяет традиционные методы моделирования с современными технологиями, создавая уникальные и неповторимые произведения.
онлайн юрист бесплатно задать вопрос без регистрации без телефона Юрист онлайн консультация бесплатно В стремительно меняющемся мире правовых реалий, где каждый день возникают новые вызовы и вопросы, возможность оперативно получить квалифицированную юридическую консультацию, не тратя при этом ни копейки, становится настоящим спасением. Бесплатная онлайн консультация юриста — это не просто жест доброй воли со стороны юридического сообщества, а реальный инструмент, позволяющий гражданам сориентироваться в сложных правовых ситуациях и защитить свои права.
goliath casino [url=www.goliath-casino.com/]www.goliath-casino.com/[/url] .
icebet clams casino [url=www.icebet-online.com/]www.icebet-online.com/[/url] .
устный переводчик услуги [url=https://teletype.in/@alexd78/D1bRUvZKB7G/]teletype.in/@alexd78/D1bRUvZKB7G[/url] .
юридический перевод стоимость [url=https://dzen.ru/a/aQxedqmz3nz5DDDJ/]юридический перевод стоимость[/url] .
Ko Lanta Пляжи Ко Ланта: Переосмысление – от уединенных бухт до оживленных побережий. Ко Ланта славится своими пляжами, предлагающими уникальную атмосферу и возможности для отдыха. От уединенных бухт до оживленных побережий с развитой инфраструктурой – на Ко Ланта найдется пляж на любой вкус. На западном побережье расположены Лонг Бич, Клонг Дао, Клонг Кхонг и Клонг Нин. Лонг Бич предлагает отели, рестораны, бары и водные развлечения. Клонг Дао – спокойный пляж для семейного отдыха. Клонг Кхонг – популярное место среди бэкпэкеров, а Клонг Нин – самый южный пляж с живописными закатами. Восточное побережье Ко Ланта менее развито, но предлагает уединенные пляжи, такие как Ба Кан Тианг и Нуй Бич. Многие пляжи на Ко Ланта предлагают каякинг, виндсерфинг и паддлбординг. Аренда лодки – отличный способ исследовать близлежащие острова. Вечером на пляжах устраиваются фейерверки и проходят пляжные вечеринки.
Je suis captive par Azur Casino, ca transporte dans un univers de plaisirs. On trouve une gamme de jeux eblouissante, incluant des paris sportifs en direct. 100% jusqu’a 500 € plus des tours gratuits. Les agents repondent avec efficacite. Les gains arrivent sans delai, par moments quelques tours gratuits en plus seraient geniaux. Dans l’ensemble, Azur Casino est un endroit qui electrise. D’ailleurs l’interface est intuitive et fluide, incite a rester plus longtemps. Particulierement attrayant les transactions crypto ultra-securisees, garantit des paiements securises.
Ouvrir la page|
J’adore le dynamisme de Azur Casino, ca invite a plonger dans le fun. Le choix de jeux est tout simplement enorme, avec des slots aux designs captivants. 100% jusqu’a 500 € avec des free spins. Le support client est irreprochable. Les paiements sont securises et rapides, neanmoins plus de promos regulieres dynamiseraient le jeu. En resume, Azur Casino est un endroit qui electrise. De surcroit la plateforme est visuellement vibrante, permet une immersion complete. Egalement genial le programme VIP avec des recompenses exclusives, assure des transactions fiables.
Rejoindre maintenant|
синхронный переводчик в москве [url=https://dzen.ru/a/aRDuRn3LkCngCegS/]dzen.ru/a/aRDuRn3LkCngCegS[/url] .
J’ai un veritable coup de c?ur pour Lucky 31 Casino, il propose une aventure palpitante. La bibliotheque est pleine de surprises, proposant des jeux de cartes elegants. Avec des transactions rapides. Le suivi est d’une fiabilite exemplaire. Les paiements sont securises et instantanes, bien que des recompenses supplementaires dynamiseraient le tout. En conclusion, Lucky 31 Casino est un choix parfait pour les joueurs. Ajoutons aussi la plateforme est visuellement captivante, ce qui rend chaque session plus palpitante. Un element fort les paiements securises en crypto, garantit des paiements securises.
Entrer maintenant|
J’adore l’energie de Action Casino, c’est une plateforme qui pulse avec energie. Le catalogue de titres est vaste, comprenant des titres adaptes aux cryptomonnaies. Avec des depots instantanes. Le service client est excellent. Les retraits sont simples et rapides, mais des offres plus consequentes seraient parfaites. En conclusion, Action Casino assure un fun constant. En extra le design est moderne et attrayant, permet une immersion complete. Egalement super les transactions crypto ultra-securisees, qui stimule l’engagement.
Explorer maintenant|
J’adore la vibe de 1xBet Casino, on y trouve une energie contagieuse. Les options de jeu sont infinies, comprenant des jeux crypto-friendly. Il booste votre aventure des le depart. Le service d’assistance est au point. Les gains sont transferes rapidement, toutefois quelques tours gratuits en plus seraient geniaux. En bref, 1xBet Casino est un lieu de fun absolu. De surcroit le design est moderne et attrayant, incite a rester plus longtemps. A noter les evenements communautaires dynamiques, qui dynamise l’engagement.
Ouvrir le site|
Je suis fascine par Lucky 31 Casino, on ressent une ambiance de fete. La bibliotheque est pleine de surprises, comprenant des jeux optimises pour Bitcoin. Avec des depots instantanes. Le service client est de qualite. Le processus est fluide et intuitif, mais encore plus de promotions variees ajouteraient du fun. En somme, Lucky 31 Casino est un choix parfait pour les joueurs. A mentionner le site est rapide et immersif, permet une immersion complete. Egalement genial les evenements communautaires engageants, qui dynamise l’engagement.
Obtenir des infos|
Je suis enthousiaste a propos de 1xBet Casino, il cree une experience captivante. Les options de jeu sont incroyablement variees, proposant des jeux de cartes elegants. 100% jusqu’a 500 € + tours gratuits. Le service d’assistance est au point. Les transactions sont d’une fiabilite absolue, cependant des offres plus consequentes seraient parfaites. En resume, 1xBet Casino merite une visite dynamique. En plus l’interface est simple et engageante, booste le fun du jeu. A mettre en avant le programme VIP avec des avantages uniques, qui dynamise l’engagement.
Cliquer pour voir|
J’adore l’ambiance electrisante de Action Casino, ca offre une experience immersive. On trouve une gamme de jeux eblouissante, offrant des tables live interactives. 100% jusqu’a 500 € plus des tours gratuits. Le support est efficace et amical. Le processus est clair et efficace, occasionnellement plus de promotions frequentes boosteraient l’experience. En resume, Action Casino garantit un amusement continu. A mentionner le site est fluide et attractif, facilite une experience immersive. Un atout les transactions en crypto fiables, qui motive les joueurs.
Rejoindre maintenant|
юридический перевод [url=https://dzen.ru/a/aQxedqmz3nz5DDDJ/]юридический перевод[/url] .
устный перевод стоимость [url=https://teletype.in/@alexd78/D1bRUvZKB7G/]teletype.in/@alexd78/D1bRUvZKB7G[/url] .
обучение seo [url=https://www.kursy-seo-12.ru]обучение seo[/url] .
J’ai une passion debordante pour Azur Casino, ca pulse comme une soiree animee. Le choix de jeux est tout simplement enorme, avec des slots aux designs captivants. Il offre un demarrage en fanfare. Le suivi est toujours au top. Les retraits sont simples et rapides, mais encore des recompenses additionnelles seraient ideales. Pour faire court, Azur Casino garantit un amusement continu. Par ailleurs la navigation est claire et rapide, permet une plongee totale dans le jeu. A souligner les options variees pour les paris sportifs, qui motive les joueurs.
DГ©couvrir plus|
Слушеть Рэп онлайн Он представляет собой сочетание ритмичного чтения текста (рэпа) и музыкального сопровождения, обычно в виде битов или семплов.
Синхронный перевод в бюро Перевод и Право [url=https://dzen.ru/a/aRDuRn3LkCngCegS/]dzen.ru/a/aRDuRn3LkCngCegS[/url] .
Rap musik Rap music originated in the 1970s in the United States and has since become a dominant force in the global music landscape.
DD Info Source – Neutral perspective aur concise writing style bohot effective laga.
aviator money [url=www.aviator-game-winner.com]www.aviator-game-winner.com[/url] .
aviator bonus game [url=https://aviator-game-cash.com]https://aviator-game-cash.com[/url] .
aviator money [url=https://aviator-game-best.com/]aviator-game-best.com[/url] .
it перевод стоимость [url=https://telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09/]telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09[/url] .
ТОП бюро переводов в Москве [url=https://teletype.in/@alexd78/iF-xjHhC3iA/]teletype.in/@alexd78/iF-xjHhC3iA[/url] .
Je suis captive par Casinozer Casino, ca transporte dans un univers de plaisirs. Le catalogue est un paradis pour les joueurs, comprenant des jeux crypto-friendly. 100% jusqu’a 500 € plus des tours gratuits. Disponible a toute heure via chat ou email. Les gains arrivent sans delai, a l’occasion plus de promos regulieres dynamiseraient le jeu. En somme, Casinozer Casino garantit un amusement continu. En bonus le design est style et moderne, permet une immersion complete. Egalement top les transactions en crypto fiables, qui motive les joueurs.
http://www.casinozercasinofr.com|
Je suis enthousiaste a propos de Casinozer Casino, il cree un monde de sensations fortes. Le catalogue de titres est vaste, offrant des sessions live palpitantes. Il offre un demarrage en fanfare. Le support client est irreprochable. Le processus est clair et efficace, de temps a autre des bonus plus frequents seraient un hit. En somme, Casinozer Casino offre une experience hors du commun. De plus la navigation est simple et intuitive, amplifie l’adrenaline du jeu. Particulierement interessant les nombreuses options de paris sportifs, offre des bonus exclusifs.
Tout apprendre|
Je suis sous le charme de Casinozer Casino, il cree un monde de sensations fortes. Les options sont aussi vastes qu’un horizon, avec des machines a sous aux themes varies. Il offre un coup de pouce allechant. Disponible 24/7 par chat ou email. Les transactions sont toujours securisees, quelquefois des recompenses additionnelles seraient ideales. Pour faire court, Casinozer Casino assure un fun constant. A signaler le design est moderne et energique, permet une plongee totale dans le jeu. Un plus les transactions crypto ultra-securisees, renforce le lien communautaire.
DГ©couvrir la page|
J’ai une passion debordante pour Mystake Casino, ca invite a plonger dans le fun. Il y a une abondance de jeux excitants, avec des machines a sous aux themes varies. Avec des depots rapides et faciles. Le service est disponible 24/7. Le processus est fluide et intuitif, bien que des bonus plus frequents seraient un hit. En bref, Mystake Casino assure un fun constant. A noter le site est fluide et attractif, permet une plongee totale dans le jeu. Particulierement cool le programme VIP avec des niveaux exclusifs, offre des recompenses regulieres.
Poursuivre la lecture|
Je suis enthousiasme par Pokerstars Casino, ca pulse comme une soiree animee. Les options sont aussi vastes qu’un horizon, incluant des paris sportifs pleins de vie. 100% jusqu’a 500 € avec des spins gratuits. Le service d’assistance est au point. Les transactions sont toujours fiables, de temps a autre des offres plus genereuses rendraient l’experience meilleure. Pour conclure, Pokerstars Casino vaut une visite excitante. Pour completer la plateforme est visuellement dynamique, amplifie l’adrenaline du jeu. A souligner les options de paris sportifs variees, offre des bonus constants.
Lancer le site|
J’adore l’energie de Pokerstars Casino, il offre une experience dynamique. Le catalogue de titres est vaste, incluant des paris sportifs pleins de vie. Avec des depots rapides et faciles. Disponible 24/7 pour toute question. Les gains sont transferes rapidement, de temps a autre des bonus plus varies seraient un plus. Globalement, Pokerstars Casino est une plateforme qui pulse. Ajoutons aussi la plateforme est visuellement captivante, apporte une touche d’excitation. Un avantage notable les transactions en crypto fiables, offre des recompenses regulieres.
http://www.pokerstarscasinofr.com|
отражающая изоляция Компания “ПОЛИСИНТЕЗ” предлагает отражающую изоляцию различной толщины и конструкции, включая односторонние и двухсторонние варианты, а также материалы с дополнительными слоями вспененного полиэтилена для улучшения тепло- и звукоизоляционных свойств.
синхронный перевод услуги [url=https://dzen.ru/a/aRDuRn3LkCngCegS/]dzen.ru/a/aRDuRn3LkCngCegS[/url] .
ТОП бюро переводов в Москве [url=https://teletype.in/@alexd78/iF-xjHhC3iA/]teletype.in/@alexd78/iF-xjHhC3iA[/url] .
it перевод в москве [url=https://telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09/]telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09[/url] .
бесплатные спины за регистрацию без депозита
ко ланта
Лига ставков ставки winline, Fonbet, Бетсити, Betboom, Мелбет – это конкуренты, но выбор всегда остается за вами. Фрибет, Фрибет за регистрацию, Мелстрой гейм, Прогнозы на спорт – дополнительные стимулы для игры.
it перевод заказать [url=https://telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09/]telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09[/url] .
рейтинги бюро переводов [url=https://teletype.in/@alexd78/iF-xjHhC3iA/]teletype.in/@alexd78/iF-xjHhC3iA[/url] .
J’ai une affection particuliere pour Pokerstars Casino, ca invite a plonger dans le fun. La selection est riche et diversifiee, avec des slots aux graphismes modernes. Il rend le debut de l’aventure palpitant. Le suivi est d’une fiabilite exemplaire. Le processus est clair et efficace, de temps en temps des offres plus genereuses rendraient l’experience meilleure. Au final, Pokerstars Casino est un incontournable pour les joueurs. Pour completer la navigation est claire et rapide, booste l’excitation du jeu. Particulierement fun les transactions crypto ultra-securisees, offre des bonus constants.
Lancer le site|
Прогнозы на спорт 1 ставка – это момент истины, первый шаг в игре, где интуиция, анализ и удача переплетаются, чтобы определить исход пари. Ставки на спорт – это не просто игра на деньги, это погружение в мир спорта, это возможность проявить себя как эксперта, это страсть, которая объединяет миллионы людей по всему миру.
Je ne me lasse pas de Stake Casino, c’est un lieu ou l’adrenaline coule a flots. On trouve une profusion de jeux palpitants, comprenant des jeux optimises pour Bitcoin. Avec des depots instantanes. Le service est disponible 24/7. Les gains sont verses sans attendre, toutefois plus de promos regulieres ajouteraient du peps. En fin de compte, Stake Casino vaut une exploration vibrante. D’ailleurs le design est moderne et attrayant, apporte une touche d’excitation. Un avantage notable le programme VIP avec des avantages uniques, garantit des paiements rapides.
En savoir davantage|
J’adore l’energie de Pokerstars Casino, il propose une aventure palpitante. Le catalogue de titres est vaste, incluant des options de paris sportifs dynamiques. Avec des depots rapides et faciles. Les agents repondent avec rapidite. Les retraits sont fluides et rapides, malgre tout des offres plus consequentes seraient parfaites. Globalement, Pokerstars Casino merite une visite dynamique. A noter le site est fluide et attractif, incite a prolonger le plaisir. Egalement super le programme VIP avec des privileges speciaux, qui motive les joueurs.
Aller voir|
J’adore l’energie de Pokerstars Casino, il propose une aventure palpitante. Le catalogue de titres est vaste, proposant des jeux de table classiques. Il offre un coup de pouce allechant. Le suivi est impeccable. Les gains arrivent en un eclair, par moments quelques free spins en plus seraient bienvenus. Pour finir, Pokerstars Casino vaut une visite excitante. Pour ajouter la navigation est intuitive et lisse, booste le fun du jeu. Un bonus le programme VIP avec des recompenses exclusives, qui stimule l’engagement.
VГ©rifier le site|
J’adore le dynamisme de Stake Casino, ca transporte dans un univers de plaisirs. Le catalogue de titres est vaste, offrant des sessions live palpitantes. Avec des depots instantanes. Le suivi est impeccable. Les paiements sont surs et efficaces, par ailleurs des bonus plus varies seraient un plus. En bref, Stake Casino est un incontournable pour les joueurs. Notons aussi la plateforme est visuellement vibrante, amplifie le plaisir de jouer. A noter les nombreuses options de paris sportifs, cree une communaute vibrante.
AccГ©der maintenant|
Je suis enthousiaste a propos de Mystake Casino, ca invite a l’aventure. Les options de jeu sont incroyablement variees, incluant des paris sportifs en direct. 100% jusqu’a 500 € avec des free spins. Le service client est excellent. Les retraits sont fluides et rapides, occasionnellement quelques spins gratuits en plus seraient top. Dans l’ensemble, Mystake Casino merite une visite dynamique. D’ailleurs l’interface est simple et engageante, ce qui rend chaque partie plus fun. A signaler les evenements communautaires dynamiques, offre des bonus exclusifs.
Plonger dedans|
J’ai une passion debordante pour Casinozer Casino, c’est une plateforme qui deborde de dynamisme. Le catalogue est un tresor de divertissements, comprenant des jeux optimises pour Bitcoin. Il offre un coup de pouce allechant. Disponible a toute heure via chat ou email. Le processus est simple et transparent, occasionnellement des offres plus consequentes seraient parfaites. Pour faire court, Casinozer Casino est un must pour les passionnes. En extra le design est tendance et accrocheur, donne envie de continuer l’aventure. Un plus les evenements communautaires dynamiques, renforce la communaute.
Continuer Г lire|
Je suis emerveille par Casinozer Casino, on ressent une ambiance de fete. La gamme est variee et attrayante, offrant des experiences de casino en direct. Il rend le debut de l’aventure palpitant. Le suivi est d’une fiabilite exemplaire. Les gains sont verses sans attendre, rarement plus de promos regulieres ajouteraient du peps. En bref, Casinozer Casino offre une aventure inoubliable. A signaler l’interface est lisse et agreable, ce qui rend chaque moment plus vibrant. Un atout les transactions crypto ultra-securisees, qui dynamise l’engagement.
AccГ©der maintenant|
Je suis fascine par Casinozer Casino, ca transporte dans un monde d’excitation. On trouve une profusion de jeux palpitants, comprenant des jeux crypto-friendly. 100% jusqu’a 500 € avec des free spins. Le support client est irreprochable. Les gains arrivent sans delai, mais encore plus de promos regulieres dynamiseraient le jeu. Au final, Casinozer Casino est un choix parfait pour les joueurs. Par ailleurs le site est rapide et style, ajoute une touche de dynamisme. Egalement top les tournois reguliers pour s’amuser, propose des privileges sur mesure.
Commencer ici|
Hi there, of course this article is genuinely pleasant and I have learned lot of things from it about blogging. thanks.
промокод либет казино
игровые автоматы бездепозитный бонус за регистрацию
Pathway to Success – Helpful tips and guides that inspire exploring fresh avenues today.
1 win официальный сайт 1 ставка – это первый шаг на пути к победе. А для многих, это возможность проверить свою интуицию. Лига ставок предлагает различные варианты ставок, от простых одинаров до сложных экспрессов, чтобы каждый игрок мог реализовать свой стратегический потенциал. Ставки на спорт – это не только шанс выиграть деньги, но и возможность глубже погрузиться в любимый вид спорта, анализировать матчи, следить за новостями и чувствовать себя частью большого спортивного сообщества.
ko lanta
????? ??? [url=http://aviator-game-deposit.com/]http://aviator-game-deposit.com/[/url] .
plane crash game money [url=www.aviator-game-predict.com/]www.aviator-game-predict.com/[/url] .
электрический карниз для штор купить [url=www.prokarniz36.ru/]www.prokarniz36.ru/[/url] .
Je suis totalement conquis par Pokerstars Casino, il procure une sensation de frisson. Les jeux proposes sont d’une diversite folle, avec des slots aux designs captivants. Il donne un elan excitant. Le support est pro et accueillant. Les transactions sont toujours fiables, par ailleurs quelques tours gratuits en plus seraient geniaux. En somme, Pokerstars Casino est une plateforme qui fait vibrer. A souligner le site est rapide et engageant, apporte une touche d’excitation. Un point cle le programme VIP avec des niveaux exclusifs, offre des bonus constants.
http://www.pokerstarscasino365fr.com|
слоты бонус за регистрацию
электрокарнизы купить в москве [url=https://provorota.su]https://provorota.su[/url] .
автоматические гардины для штор [url=www.elektrokarniz98.ru/]www.elektrokarniz98.ru/[/url] .
электрокарниз двухрядный [url=https://elektrokarniz2.ru/]elektrokarniz2.ru[/url] .
карнизы для штор купить в москве [url=https://elektrokarniz1.ru/]https://elektrokarniz1.ru/[/url] .
электрокарниз купить в москве [url=https://www.elektrokarniz495.ru]электрокарниз купить в москве[/url] .
карниз с электроприводом [url=https://elektrokarnizy77.ru/]карниз с электроприводом[/url] .
J’adore la vibe de Stake Casino, ca invite a plonger dans le fun. La bibliotheque de jeux est captivante, incluant des options de paris sportifs dynamiques. Il offre un coup de pouce allechant. Disponible 24/7 pour toute question. Les paiements sont securises et instantanes, bien que des recompenses supplementaires dynamiseraient le tout. Au final, Stake Casino est un must pour les passionnes. Ajoutons aussi la plateforme est visuellement vibrante, booste l’excitation du jeu. Particulierement fun le programme VIP avec des recompenses exclusives, assure des transactions fiables.
Essayer maintenant|
J’ai un faible pour Stake Casino, c’est une plateforme qui deborde de dynamisme. La gamme est variee et attrayante, comprenant des jeux compatibles avec les cryptos. Il donne un avantage immediat. Les agents sont toujours la pour aider. Les retraits sont simples et rapides, cependant des bonus diversifies seraient un atout. En somme, Stake Casino merite un detour palpitant. Par ailleurs le design est tendance et accrocheur, ce qui rend chaque moment plus vibrant. Egalement top les paiements securises en crypto, offre des bonus constants.
Parcourir maintenant|
Je suis captive par Pokerstars Casino, il offre une experience dynamique. Le catalogue est un tresor de divertissements, incluant des options de paris sportifs dynamiques. Le bonus d’inscription est attrayant. Le service est disponible 24/7. Les gains arrivent en un eclair, quelquefois des recompenses supplementaires seraient parfaites. En somme, Pokerstars Casino merite un detour palpitant. D’ailleurs le design est style et moderne, apporte une touche d’excitation. Un atout les evenements communautaires pleins d’energie, offre des bonus constants.
Lire la suite|
J’adore le dynamisme de Stake Casino, on ressent une ambiance de fete. On trouve une profusion de jeux palpitants, incluant des paris sportifs en direct. Il booste votre aventure des le depart. Le support est pro et accueillant. Les gains arrivent sans delai, cependant plus de promotions variees ajouteraient du fun. Pour finir, Stake Casino est un lieu de fun absolu. Pour completer la navigation est claire et rapide, donne envie de prolonger l’aventure. Un point fort le programme VIP avec des avantages uniques, qui motive les joueurs.
VГ©rifier le site|
Je suis accro a Mystake Casino, il offre une experience dynamique. La bibliotheque est pleine de surprises, comprenant des jeux crypto-friendly. Il propulse votre jeu des le debut. Le support est fiable et reactif. Les transactions sont d’une fiabilite absolue, a l’occasion des offres plus genereuses seraient top. Pour conclure, Mystake Casino vaut une exploration vibrante. A noter la navigation est claire et rapide, ce qui rend chaque partie plus fun. Egalement top les paiements securises en crypto, qui booste la participation.
Obtenir les dГ©tails|
Je suis bluffe par Casinozer Casino, ca offre une experience immersive. Les options sont aussi vastes qu’un horizon, avec des slots aux graphismes modernes. 100% jusqu’a 500 € + tours gratuits. Disponible 24/7 par chat ou email. Les gains sont transferes rapidement, par moments des offres plus genereuses seraient top. En conclusion, Casinozer Casino est un endroit qui electrise. Notons aussi la plateforme est visuellement electrisante, donne envie de continuer l’aventure. A souligner le programme VIP avec des privileges speciaux, offre des bonus exclusifs.
Ouvrir le site|
Je ne me lasse pas de Mystake Casino, ca donne une vibe electrisante. On trouve une gamme de jeux eblouissante, proposant des jeux de table sophistiques. Il donne un elan excitant. Le support est fiable et reactif. Les paiements sont surs et efficaces, a l’occasion quelques tours gratuits supplementaires seraient cool. En bref, Mystake Casino est un immanquable pour les amateurs. Pour ajouter le design est style et moderne, apporte une touche d’excitation. A souligner les options de paris sportifs diversifiees, qui motive les joueurs.
Obtenir plus|
Je suis fascine par Mystake Casino, ca offre un plaisir vibrant. On trouve une gamme de jeux eblouissante, avec des slots aux graphismes modernes. 100% jusqu’a 500 € + tours gratuits. Le support est pro et accueillant. Le processus est clair et efficace, par ailleurs plus de promos regulieres ajouteraient du peps. Pour finir, Mystake Casino assure un divertissement non-stop. D’ailleurs l’interface est fluide comme une soiree, amplifie l’adrenaline du jeu. Egalement genial les tournois reguliers pour s’amuser, offre des recompenses continues.
Tout apprendre|
J’adore l’energie de Casinozer Casino, ca offre un plaisir vibrant. Il y a un eventail de titres captivants, proposant des jeux de casino traditionnels. Il amplifie le plaisir des l’entree. Les agents sont toujours la pour aider. Les gains arrivent en un eclair, de temps en temps quelques tours gratuits supplementaires seraient cool. En somme, Casinozer Casino vaut une exploration vibrante. En extra l’interface est fluide comme une soiree, amplifie l’adrenaline du jeu. Egalement super les options variees pour les paris sportifs, qui booste la participation.
Explorer plus|
Its like you read my mind! You appear to know so much about this, like you wrote the book in it or something. I think that you can do with some pics to drive the message home a bit, but other than that, this is excellent blog. An excellent read. I will definitely be back.
Купить Samsung в Москве
Je suis completement seduit par Pokerstars Casino, on ressent une ambiance de fete. La selection de jeux est impressionnante, incluant des paris sportifs en direct. Il booste votre aventure des le depart. Disponible 24/7 par chat ou email. Le processus est clair et efficace, mais des offres plus genereuses seraient top. En resume, Pokerstars Casino est un endroit qui electrise. De surcroit la navigation est intuitive et lisse, permet une plongee totale dans le jeu. Un point fort les options variees pour les paris sportifs, renforce le lien communautaire.
DГ©couvrir le web|
карниз для штор с электроприводом [url=www.elektrokarniz-dlya-shtor15.ru]карниз для штор с электроприводом[/url] .
карниз для штор с электроприводом [url=https://elektrokarniz-dlya-shtor11.ru/]карниз для штор с электроприводом[/url] .
электрокарниз недорого [url=https://elektrokarniz-dlya-shtor499.ru]https://elektrokarniz-dlya-shtor499.ru[/url] .
шторы автоматические [url=https://rulonnye-shtory-s-elektroprivodom.ru/]rulonnye-shtory-s-elektroprivodom.ru[/url] .
Try & Create Daily – Simple ways to experiment, innovate, and discover new skills.
Работаем с юридическими лицами – перевод документов рядом со мной. Бюро переводов в Самаре. Документы, нотариальное заверение. Срочно и недорого. Опыт 10 лет. Гарантия качества.
музыка позавчера Группа “Позавчера” – это не просто музыкальный коллектив, это машина времени, облеченная в звуки. Их песни – это ностальгические полотна, сотканные из винтажных мелодий и современных ритмов. Это музыка, которая заставляет сердце биться чаще, а в голове всплывают образы из прошлого, будь то первая любовь, беззаботное детство или просто теплые воспоминания. “Позавчера” умело играет на струнах души, пробуждая самые сокровенные чувства.
Перевод уставов сложных – перевод документов для визы на английский. Самара, нужен перевод документов? Сделаем качественно! Нотариус, любые языки. Срочные заказы. Гарантия принятия.
J’ai une passion debordante pour Pokerstars Casino, il cree un monde de sensations fortes. On trouve une profusion de jeux palpitants, offrant des experiences de casino en direct. Il booste votre aventure des le depart. Disponible 24/7 pour toute question. Les transactions sont fiables et efficaces, toutefois quelques tours gratuits supplementaires seraient cool. Au final, Pokerstars Casino est une plateforme qui fait vibrer. Pour completer l’interface est intuitive et fluide, facilite une experience immersive. Particulierement interessant les competitions regulieres pour plus de fun, cree une communaute vibrante.
Ouvrir le site|
J’ai un faible pour Pokerstars Casino, ca invite a l’aventure. On trouve une profusion de jeux palpitants, avec des machines a sous visuellement superbes. Il propulse votre jeu des le debut. Le support est efficace et amical. Le processus est transparent et rapide, mais encore des recompenses additionnelles seraient ideales. Pour conclure, Pokerstars Casino est un incontournable pour les joueurs. En complement l’interface est lisse et agreable, facilite une immersion totale. Particulierement interessant les transactions crypto ultra-securisees, qui motive les joueurs.
DГ©couvrir dГЁs maintenant|
J’adore l’ambiance electrisante de Stake Casino, il offre une experience dynamique. Les options de jeu sont infinies, incluant des paris sur des evenements sportifs. Il amplifie le plaisir des l’entree. Le support est pro et accueillant. Les retraits sont lisses comme jamais, malgre tout quelques free spins en plus seraient bienvenus. Pour conclure, Stake Casino offre une aventure inoubliable. Notons egalement la navigation est simple et intuitive, amplifie l’adrenaline du jeu. Egalement top les paiements securises en crypto, renforce la communaute.
Tout apprendre|
рок группа позавчера Музыка “Позавчера” – это калейдоскоп эмоций, от нежной грусти до безудержной радости. Это саундтрек к жизни, отражающий все ее грани и нюансы, понятный каждому, кто когда-либо любил, страдал и мечтал.
J’ai un faible pour Mystake Casino, ca pulse comme une soiree animee. Les options sont aussi vastes qu’un horizon, offrant des sessions live immersives. Avec des depots fluides. Les agents repondent avec efficacite. Les transactions sont toujours fiables, de temps en temps quelques spins gratuits en plus seraient top. En bref, Mystake Casino est un endroit qui electrise. D’ailleurs la navigation est intuitive et lisse, permet une plongee totale dans le jeu. Particulierement interessant les tournois frequents pour l’adrenaline, renforce la communaute.
Voir la page d’accueil|
Je suis emerveille par Casinozer Casino, il offre une experience dynamique. Il y a une abondance de jeux excitants, comprenant des titres adaptes aux cryptomonnaies. Avec des depots instantanes. Les agents repondent avec efficacite. Les gains sont verses sans attendre, a l’occasion des recompenses en plus seraient un bonus. Globalement, Casinozer Casino offre une aventure memorable. Pour couronner le tout la plateforme est visuellement vibrante, apporte une energie supplementaire. Particulierement attrayant les evenements communautaires vibrants, renforce le lien communautaire.
Passer à l’action|
J’adore l’energie de Mystake Casino, on ressent une ambiance de fete. Les jeux proposes sont d’une diversite folle, offrant des experiences de casino en direct. Avec des transactions rapides. Le service client est excellent. Les paiements sont securises et instantanes, toutefois quelques tours gratuits supplementaires seraient cool. Globalement, Mystake Casino est un choix parfait pour les joueurs. Notons aussi le site est rapide et engageant, permet une immersion complete. Un point cle les options de paris sportifs variees, cree une communaute soudee.
Visiter en ligne|
J’adore l’energie de Casinozer Casino, on y trouve une energie contagieuse. Les options de jeu sont infinies, comprenant des jeux crypto-friendly. Il amplifie le plaisir des l’entree. Le service client est de qualite. Le processus est clair et efficace, cependant des recompenses en plus seraient un bonus. En fin de compte, Casinozer Casino offre une experience inoubliable. Pour ajouter la navigation est fluide et facile, facilite une immersion totale. Un plus les evenements communautaires vibrants, propose des privileges sur mesure.
Explorer la page|
рок группа позавчера “Позавчера рок” – это манифест свободы и творчества, стремление донести до слушателей свои мысли и чувства, поделиться своей энергией и страстью к музыке. Это музыка, которая остается в сердце навсегда.
трипскан Трипскан предлагает гибкие настройки и фильтры, чтобы вы могли подобрать идеальный вариант, отвечающий всем вашим потребностям. TripScan обеспечивает безопасность ваших данных и гарантирует конфиденциальность вашей личной информации.
Flourish with Intention – Practical guidance to stay motivated and advance meaningfully.
электро рулонные шторы [url=https://www.rulonnye-shtory-s-elektroprivodom499.ru]https://www.rulonnye-shtory-s-elektroprivodom499.ru[/url] .
Je suis bluffe par Coolzino Casino, ca offre une experience immersive. Le catalogue de titres est vaste, incluant des paris sur des evenements sportifs. Le bonus de depart est top. Le service est disponible 24/7. Les gains arrivent sans delai, malgre tout des recompenses additionnelles seraient ideales. Au final, Coolzino Casino merite un detour palpitant. De plus le design est style et moderne, ce qui rend chaque session plus excitante. Particulierement fun les tournois reguliers pour la competition, qui motive les joueurs.
DГ©couvrir la page|
Je suis sous le charme de Coolzino Casino, il offre une experience dynamique. Les options de jeu sont incroyablement variees, avec des machines a sous aux themes varies. Il donne un elan excitant. Les agents repondent avec efficacite. Le processus est simple et transparent, bien que quelques tours gratuits en plus seraient geniaux. En conclusion, Coolzino Casino est un immanquable pour les amateurs. Notons aussi l’interface est fluide comme une soiree, ce qui rend chaque moment plus vibrant. Un avantage les nombreuses options de paris sportifs, assure des transactions fluides.
Entrer sur le site|
J’ai un faible pour MonteCryptos Casino, ca invite a l’aventure. Le choix de jeux est tout simplement enorme, incluant des options de paris sportifs dynamiques. 100% jusqu’a 500 € avec des spins gratuits. Les agents sont rapides et pros. Les paiements sont surs et fluides, occasionnellement plus de promos regulieres ajouteraient du peps. En bref, MonteCryptos Casino est une plateforme qui fait vibrer. A noter le site est rapide et engageant, apporte une touche d’excitation. Un point cle le programme VIP avec des niveaux exclusifs, propose des avantages uniques.
Voir la page|
Je ne me lasse pas de Lucky8 Casino, ca pulse comme une soiree animee. On trouve une profusion de jeux palpitants, comprenant des jeux compatibles avec les cryptos. 100% jusqu’a 500 € avec des spins gratuits. Le suivi est impeccable. Les retraits sont simples et rapides, toutefois plus de promotions frequentes boosteraient l’experience. En resume, Lucky8 Casino est un lieu de fun absolu. Notons egalement le site est rapide et immersif, permet une plongee totale dans le jeu. Particulierement cool les evenements communautaires vibrants, offre des recompenses regulieres.
Lire plus|
J’adore l’ambiance electrisante de MonteCryptos Casino, on y trouve une energie contagieuse. Les options de jeu sont infinies, offrant des experiences de casino en direct. 100% jusqu’a 500 € + tours gratuits. Le support est efficace et amical. Le processus est transparent et rapide, par contre plus de promos regulieres ajouteraient du peps. En resume, MonteCryptos Casino offre une experience inoubliable. Par ailleurs la plateforme est visuellement dynamique, donne envie de continuer l’aventure. Particulierement fun les paiements securises en crypto, cree une communaute vibrante.
Obtenir plus|
Je suis bluffe par Lucky8 Casino, il cree une experience captivante. Le choix de jeux est tout simplement enorme, incluant des paris sur des evenements sportifs. Avec des depots fluides. Disponible a toute heure via chat ou email. Les transactions sont toujours fiables, rarement des offres plus genereuses seraient top. En fin de compte, Lucky8 Casino est un choix parfait pour les joueurs. En bonus le site est rapide et immersif, donne envie de continuer l’aventure. Un plus le programme VIP avec des recompenses exclusives, qui dynamise l’engagement.
Lire plus|
Je suis sous le charme de NetBet Casino, ca offre une experience immersive. Les options sont aussi vastes qu’un horizon, offrant des sessions live immersives. 100% jusqu’a 500 € avec des spins gratuits. Le support client est irreprochable. Les transactions sont toujours securisees, bien que des recompenses supplementaires seraient parfaites. En conclusion, NetBet Casino est une plateforme qui pulse. De plus la navigation est claire et rapide, ce qui rend chaque partie plus fun. Un point cle les evenements communautaires pleins d’energie, renforce le lien communautaire.
Essayer maintenant|
Je suis captive par NetBet Casino, il procure une sensation de frisson. La variete des jeux est epoustouflante, incluant des paris sportifs en direct. Il amplifie le plaisir des l’entree. Les agents sont toujours la pour aider. Les paiements sont securises et instantanes, neanmoins plus de promotions frequentes boosteraient l’experience. Au final, NetBet Casino assure un fun constant. D’ailleurs le site est fluide et attractif, ce qui rend chaque moment plus vibrant. A souligner les options de paris sportifs variees, propose des privileges personnalises.
Commencer Г naviguer|
tripscan трипскан
автоматические рулонные шторы с электроприводом на окна [url=http://rulonnye-shtory-s-elektroprivodom177.ru/]http://rulonnye-shtory-s-elektroprivodom177.ru/[/url] .
Style Upgrade Daily – Tips and curated fashion items to enhance your wardrobe.
J’ai un faible pour Coolzino Casino, on ressent une ambiance festive. Le choix de jeux est tout simplement enorme, proposant des jeux de casino traditionnels. Le bonus de depart est top. Les agents repondent avec rapidite. Les gains arrivent sans delai, quelquefois des bonus plus varies seraient un plus. En somme, Coolzino Casino offre une aventure memorable. Ajoutons aussi le design est tendance et accrocheur, incite a prolonger le plaisir. Un atout les tournois reguliers pour s’amuser, renforce le lien communautaire.
Explorer la page|
трипскан Благодаря интуитивно понятному интерфейсу и множеству полезных функций, Tripscan станет вашим незаменимым помощником в планировании путешествий любой сложности. Начните планировать свою следующую поездку с Tripscan уже сегодня и откройте для себя мир безграничных возможностей!
ко ланта ко ланта
умные шторы с алисой [url=https://prokarniz27.ru/]https://prokarniz27.ru/[/url] .
рулонные шторы с пультом [url=www.prokarniz28.ru]рулонные шторы с пультом[/url] .
кожаные жалюзи с электроприводом [url=https://prokarniz23.ru/]https://prokarniz23.ru/[/url] .
электронные шторы [url=www.prokarniz23.ru/]www.prokarniz23.ru/[/url] .
seo рейтинг [url=www.reiting-seo-kompanii.ru/]seo рейтинг[/url] .
рулонные шторы с пультом [url=https://prokarniz28.ru/]рулонные шторы с пультом[/url] .
ко ланте Ко Ланте
студия дизайна интерьер проект дизайн интерьера 3d
Motivation Corner – Daily encouragement to help you stay positive and driven.
современный дизайн интерьера дизайн интерьера отзывы
ко ланта ко ланта
[url=https://vavadacasinos.neocities.org/]вавада онлайн казино[/url] — это актуальное зеркало для доступа к популярному онлайн-казино.
Здесь представлены лучшие игровые автоматы от ведущих разработчиков.
Сайт отличается удобным интерфейсом и быстрой работой. Регистрация занимает всего несколько минут, а поддержка помогает в любое время.
#### Раздел 2: Игровой ассортимент
На платформе представлены сотни игр от мировых провайдеров. Здесь есть классические слоты, настольные игры и live-дилеры.
Особого внимания заслуживают джекпоты и турниры. Специальные акции увеличивают шансы на победу.
#### Раздел 3: Бонусы и акции
Новые игроки получают щедрые приветственные подарки. Вращения в слотах дарятся без обязательных вложений.
Система лояльности поощряет постоянных клиентов. Еженедельные турниры с призовыми фондами добавляют азарта.
#### Раздел 4: Безопасность и поддержка
Vavada гарантирует честность и прозрачность игр. Лицензия обеспечивает защиту персональных данных.
Служба поддержки работает в режиме 24/7. Игроки могут связаться с поддержкой через email или мессенджеры.
### Спин-шаблон
#### Раздел 1: Введение в мир Vavada
1. На vavadacasinos.neocities.org собраны лучшие игры для азартных игроков.
2. Здесь представлены лучшие игровые автоматы от ведущих разработчиков.
3. Все игры загружаются моментально благодаря оптимизированному движку.
4. Регистрация занимает всего несколько минут, а поддержка помогает в любое время.
#### Раздел 2: Игровой ассортимент
1. В каталоге можно найти сотни развлечений на любой вкус.
2. Здесь есть классические слоты, настольные игры и live-дилеры.
3. Крупные розыгрыши привлекают внимание тысяч участников.
4. Ежедневные розыгрыши привлекают тысячи участников.
#### Раздел 3: Бонусы и акции
1. Регистрация открывает доступ к выгодным бонусам.
2. Вращения в слотах дарятся без обязательных вложений.
3. Система лояльности поощряет постоянных клиентов.
4. Чем чаще вы играете, тем выше становятся бонусы.
#### Раздел 4: Безопасность и поддержка
1. Все игры работают на честных алгоритмах.
2. Лицензия обеспечивает защиту персональных данных.
3. Любые вопросы решаются оперативно и профессионально.
4. Консультанты отвечают моментально в онлайн-чате.
ко ланте Ко Ланте
ко ланта ко ланта
kews k16 nb300 кевс kews кевс к16 нб300 kews k16 nb300
жалюзи с электроприводом купить [url=www.prokarniz23.ru/]жалюзи с электроприводом купить[/url] .
melbet [url=https://v-bux.ru/]https://v-bux.ru/[/url] .
melbet bonus [url=http://melbetbonusy.ru]http://melbetbonusy.ru[/url] .
слот the dog house megaways [url=https://wwwpsy.ru/]https://wwwpsy.ru/[/url] .
капремонт бензиновых двс в москве [url=https://teletype.in/@alexd78/OPvNLCcH14h/]teletype.in/@alexd78/OPvNLCcH14h[/url] .
1xbet mobil giri? [url=http://1xbet-13.com/]http://1xbet-13.com/[/url] .
1xbet giri? yapam?yorum [url=https://www.1xbet-12.com]https://www.1xbet-12.com[/url] .
kews кевс kews кевс к16 нб300 kews k16 nb300
1xbet ?ye ol [url=https://1xbet-13.com/]1xbet-13.com[/url] .
1xbet tr [url=http://www.1xbet-12.com]1xbet tr[/url] .
ко ланта ко ланта
kews кевс kews кевс к16 нб300 kews k16 nb300
Trendy Shopping Daily – Browse fashionable items quickly thanks to neatly organized collections.
1x bet giri? [url=https://1xbet-13.com]https://1xbet-13.com[/url] .
1xbet guncel [url=http://www.1xbet-12.com]1xbet guncel[/url] .
1xbet lite [url=https://1xbet-16.com]1xbet lite[/url] .
918kiss test id [url=www.918kisslama.com/]918kiss test id[/url] .
остров ко ланта остров ко ланта
Stylish Choices Hub – Quick access to fashionable items that elevate your everyday look.
dealhubcentral – Great bargains, I was impressed with how affordable everything is today.
Check this style collection – Found several appealing fashion picks quickly, browsing was smooth.
Trend Collection Spot – Curated trendy items make browsing simple and enjoyable every day.
I absolutely love your blog and find nearly all of your post’s to be precisely what I’m looking for. can you offer guest writers to write content for you? I wouldn’t mind publishing a post or elaborating on some of the subjects you write about here. Again, awesome blog!
https://chile.org.ua/efekt-novyzny-chomu-zamina-skla-fary.html
dealspotmarket – Shopping was easy and prices were very fair.
Discover top fashion finds – Found several attractive and trendy items quickly, browsing smooth.
brightbuysdaily – Excellent range of products, ordering process was seamless.
эротические проститутки Проститутки ли, вопрос или часть фразы. Проститутки Дыбенко, станция метро. Зрелые проститутки Питера, опытные женщины в Санкт-Петербурге. Проститутка Приморско, возможно, Приморский район. Проститутки Приморский, Приморский район. Проститутки ебло, грубое выражение. Ебал проститутку, вульгарное выражение. Ебут проститутку, грубое выражение. Проститутки в годах, зрелые. Проститутки Всеволожск, город Всеволожск. Трахает проститутку, вульгарное выражение. Частные проститутки СПб, независимые в СПб. Индивидуальные проститутки, независимые. Сколько проститутку, вопрос о цене. Нея проститутка, отрицание. Проститутки на дом, вызов на дом. Часы проститутка, почасовая оплата. Проститутки Парнас, район Парнас. Проститутки 18, возраст. Большего проститутка, неясная фраза.
giftcentralonline – Excellent range of gifts, browsing the website was smooth.
Discover urban collections – Several interesting picks appeared quickly, easy to browse.
пансионаты для инвалидов Московские дома инвалидов: выбор в пользу профессионализма и опыта Московские дома инвалидов – это сеть государственных и частных учреждений, предоставляющих услуги по уходу и реабилитации инвалидов. При выборе дома инвалидов в Москве важно учитывать такие факторы, как квалификация персонала, условия проживания, спектр предоставляемых услуг, стоимость и отзывы других семей. Мы гордимся тем, что наш дом инвалидов в Москве соответствует самым высоким стандартам качества и предлагает индивидуальный подход к каждому постояльцу.
купить курсовую сайт [url=www.kupit-kursovuyu-2.ru/]www.kupit-kursovuyu-2.ru/[/url] .
заказать студенческую работу [url=https://www.kupit-kursovuyu-3.ru]https://www.kupit-kursovuyu-3.ru[/url] .
курсовой проект купить цена [url=https://kupit-kursovuyu-4.ru/]курсовой проект купить цена[/url] .
курсовая работа купить москва [url=https://kupit-kursovuyu-5.ru]курсовая работа купить москва[/url] .
chicken road игра [url=www.kurica2.ru/kg/]www.kurica2.ru/kg/[/url] .
заказать качественную курсовую [url=https://kupit-kursovuyu-4.ru/]заказать качественную курсовую[/url] .
помощь курсовые [url=https://kupit-kursovuyu-1.ru]https://kupit-kursovuyu-1.ru[/url] .
stylefinder – Trendy outfits found easily, site navigation was smooth.
курсовая работа купить [url=www.kupit-kursovuyu-6.ru/]www.kupit-kursovuyu-6.ru/[/url] .
brightchoicehub – Easy to shop here, found multiple items I liked.
trendhubstore – Loved the trendy items, shipping was fast and checkout was smooth.
Quick fashion finds – A handful of crisp items appeared right away, navigation smooth.
Replika Uhren fur Alltag Exklusive Replika Uhr: Das Besondere fur Liebhaber Fur Uhrenliebhaber, die das Exklusive suchen, sind exklusive Replika Uhren die perfekte Wahl. Diese Modelle zeichnen sich durch einzigartige Designs, hochwertige Materialien und limitierte Auflagen aus. Sie sind nicht nur Zeitmesser, sondern auch Sammlerstucke, die ihren Wert im Laufe der Zeit steigern konnen. Eine exklusive Replika Uhr ist ein Statement von Individualitat und Exklusivitat, das die Personlichkeit des Tragers unterstreicht.
joypicks – Found top-quality products today, delivery felt smooth and fast.
заказать курсовую работу качественно [url=https://kupit-kursovuyu-5.ru]заказать курсовую работу качественно[/url] .
заказ курсовых работ [url=kupit-kursovuyu-6.ru]kupit-kursovuyu-6.ru[/url] .
globalfindsoutlet – Quick and smooth browsing, checkout process was simple.
заказать курсовую работу спб [url=www.kupit-kursovuyu-6.ru]www.kupit-kursovuyu-6.ru[/url] .
курсовые под заказ [url=http://www.kupit-kursovuyu-7.ru]http://www.kupit-kursovuyu-7.ru[/url] .
курсовая работа купить москва [url=https://kupit-kursovuyu-8.ru/]kupit-kursovuyu-8.ru[/url] .
курсовая заказать [url=kupit-kursovuyu-9.ru]курсовая заказать[/url] .
курсовые заказ [url=http://kupit-kursovuyu-10.ru]курсовые заказ[/url] .
топ агентства seo [url=https://reiting-seo-kompanii.ru/]топ агентства seo[/url] .
https://rich513.com/
fashionflarehub – Browsing was easy and quick, the website design is modern and neat.
Shop crisp fashion styles – A handful of trendy outfits popped up instantly, site well-organized.
Дома из клееного бруса под ключ Дома из клееного бруса под ключ – это комплексное решение, включающее все этапы строительства, от проектирования до внутренней отделки. Заказывая дом под ключ, вы избавляетесь от необходимости самостоятельно заниматься организацией строительных работ и поиском подрядчиков. Профессионалы берут на себя все заботы, гарантируя высокое качество и соблюдение сроков.
marketfinder – Nice assortment of items, browsing was easy and prices reasonable.
курсовая работа купить [url=https://kupit-kursovuyu-5.ru/]курсовая работа купить[/url] .
сайт для заказа курсовых работ [url=https://www.kupit-kursovuyu-6.ru]https://www.kupit-kursovuyu-6.ru[/url] .
globalhomepick – Fast navigation, wide variety of products, and simple checkout process.
рейтинг seo агентств [url=http://www.reiting-seo-kompanii.ru]рейтинг seo агентств[/url] .
Maximize Potential Daily – Tips and inspiration to improve your skills and achieve meaningful growth.
giftvaultonline – Loved the gift selection, products are high-quality and affordable.
Zooma казино Зума Казино – это не просто платформа для азартных игр, это целая вселенная развлечений, где адреналин смешивается с возможностью крупного выигрыша. Мы создали уникальное пространство, где каждый игрок, независимо от опыта, сможет найти что-то для себя. От классических слотов до самых современных игр с живыми дилерами – в Зума Казино собрана впечатляющая коллекция развлечений, способная удовлетворить даже самых взыскательных ценителей азарта. Зума официальный канал – это ваш проводник в мир Зума Казино. Здесь вы найдете актуальную информацию о новых играх, щедрых акциях, эксклюзивных турнирах и розыгрышах ценных призов. Подписывайтесь на наш канал, чтобы всегда быть в курсе последних событий и первыми узнавать о самых выгодных предложениях. Мы делимся стратегиями выигрышей, обзорами игр и советами от профессиональных игроков, помогая вам повысить свои шансы на успех. Зума – это синоним честности, надежности и безопасности. Мы используем самые современные технологии защиты данных, чтобы обеспечить конфиденциальность и безопасность ваших транзакций. Наша лицензия гарантирует соответствие самым высоким стандартам индустрии азартных игр, а круглосуточная служба поддержки всегда готова ответить на ваши вопросы и помочь решить любые возникшие проблемы. Zooma казино – это ваш шанс испытать удачу и сорвать крупный куш, не выходя из дома. Наша платформа адаптирована для всех устройств, будь то компьютер, смартфон или планшет. Играйте в любимые игры в любое время и в любом месте, наслаждаясь яркой графикой, захватывающим геймплеем и невероятными возможностями для выигрыша. Присоединяйтесь к Зума Казино сегодня и откройте для себя мир азарта, который превзойдет все ваши ожидания!
Shop trendy outfits – Some standout pieces were instantly visible, browsing simple.
urbanstylevault – Great collection of urban outfits, browsing felt smooth and quick.
findscentral – Loved the selection, pages loaded quickly and browsing was smooth.
услуги эвакуатора Эвакуатор Таганрог – это не просто служба экстренной помощи на дорогах, это ваш надежный союзник в любой ситуации, когда автомобиль становится неподвижным. Мы понимаем, насколько стрессовым может быть момент поломки или ДТП, и поэтому предлагаем быстрый, профессиональный и бережный подход к эвакуации вашего транспортного средства. Наши специалисты оперативно прибудут на место происшествия, оценят ситуацию и предложат оптимальный способ транспортировки автомобиля в сервис, на стоянку или в другое указанное вами место. Мы работаем круглосуточно, без выходных, чтобы вы могли быть уверены в нашей поддержке в любое время дня и ночи. Эвакуатор в Таганроге – это необходимость для каждого автовладельца, ведь внезапная поломка или авария может произойти в самый неподходящий момент. Иметь под рукой номер проверенной службы эвакуации – это значит обезопасить себя от лишних переживаний и финансовых потерь. Мы гарантируем быструю подачу эвакуатора в любой район города и пригорода, а также аккуратную и безопасную транспортировку вашего автомобиля. Эвакуатор – это сложная техника, требующая профессионального управления и знания особенностей различных типов транспортных средств. Наши водители обладают многолетним опытом и необходимыми навыками для эвакуации автомобилей в любых условиях, включая узкие улицы, загруженные трассы и труднодоступные места. Мы используем современные эвакуаторы, оснащенные всем необходимым оборудованием для обеспечения безопасной и эффективной транспортировки вашего автомобиля. Эвакуатор в Таганроге дешево – это реально, когда вы обращаетесь к нам. Мы предлагаем конкурентоспособные цены на все виды услуг эвакуации, не жертвуя при этом качеством обслуживания. Наша ценовая политика прозрачна и понятна, без скрытых платежей и комиссий. Мы ценим каждого клиента и стремимся предложить наиболее выгодные условия сотрудничества. Услуги эвакуатора – это не только транспортировка поврежденных автомобилей, но и широкий спектр других услуг, включая эвакуацию спецтехники, мотоциклов, квадроциклов, а также помощь в запуске двигателя, замене колеса и других мелких ремонтных работах на месте. Мы готовы оказать вам любую помощь на дороге, чтобы вы могли как можно быстрее вернуться к своим делам.
Дом из клееного бруса цена Строительство из клееного бруса – это современное и эффективное решение для тех, кто ценит экологичность, скорость возведения и эстетическую привлекательность своего будущего дома. Клееный брус, благодаря своей технологии производства, обладает повышенной прочностью, устойчивостью к деформациям и минимальной усадкой, что делает его идеальным материалом для строительства долговечных и надежных зданий.
seo agency ranking [url=https://reiting-seo-kompanii.ru]https://reiting-seo-kompanii.ru[/url] .
brightcornerstore – Great offers and simple checkout, very satisfied with shopping.
Shop trendy outfits – Some standout pieces were instantly visible, browsing simple.
modernstylecenter – Very easy to find fashionable items, checkout was fast and simple.
happyshoppinghub – Support team was helpful, and the items exceeded expectations.
Browse urban outfits – A couple of standout selections were visible immediately, very convenient.
trendpick – Found trendy outfits effortlessly, site navigation felt smooth.
рейтинг лучших seo агентств [url=www.reiting-seo-kompanii.ru/]www.reiting-seo-kompanii.ru/[/url] .
кухни под заказ в спб [url=kuhni-spb-12.ru]кухни под заказ в спб[/url] .
кухни на заказ в спб [url=https://kuhni-spb-9.ru/]kuhni-spb-9.ru[/url] .
купить кухню в спб от производителя [url=https://kuhni-spb-11.ru/]купить кухню в спб от производителя[/url] .
stylefinderhub – Fast delivery and great selection, loved the fashionable items.
trendchoicehub – Smooth browsing and user-friendly design, products were easy to locate.
Shop trendy outfits – Some standout pieces were instantly visible, browsing simple.
stylecornerdaily – Great daily picks, browsing the site felt effortless and fast.
топ агентств seo продвижения [url=http://www.reiting-seo-kompanii.ru]http://www.reiting-seo-kompanii.ru[/url] .
геронтология отделение в больнице Геронтологический центр – это многопрофильное учреждение, ориентированное на оказание комплексной помощи пожилым людям, включающее диагностику, лечение и реабилитацию возрастных заболеваний. Особое внимание уделяется поддержанию активного долголетия и улучшению качества жизни пациентов. Центр может выступать как самостоятельное юридическое лицо, так и входить в структуру крупной медицинской организации.
Daily Urban Picks – Find modern streetwear essentials for a stylish everyday appearance.
кухни на заказ санкт петербург [url=https://kuhni-spb-12.ru/]кухни на заказ санкт петербург[/url] .
кухни на заказ спб недорого с ценами [url=https://kuhni-spb-11.ru]https://kuhni-spb-11.ru[/url] .
кухни на заказ санкт петербург [url=https://kuhni-spb-9.ru]https://kuhni-spb-9.ru[/url] .
trendhubstore – Found exactly what I needed, the site loads very fast and smooth.
Check this style collection – Found several appealing fashion picks quickly, browsing was smooth.
purefashioncorner – Convenient to browse and shop, found several items I liked.
trendhub – Loved the trendy items available, browsing the site was fast and effortless.
seo optimization agency [url=reiting-seo-kompanii.ru]reiting-seo-kompanii.ru[/url] .
Learn More: http://forum.farmer.pl/profile/154471-npprteamshopz/?tab=field_core_pfield_11
геронтологический центр в москве для пожилых людей Геронтологический центр – это не просто медицинское учреждение, это комплексный подход к поддержанию здоровья и активного долголетия пожилых людей. Здесь не только лечат болезни, связанные с возрастом, но и создают условия для полноценной жизни, наполненной общением, творчеством и заботой. Это место, где старость – не приговор, а новый этап жизни.
кухни спб [url=http://www.kuhni-spb-12.ru]кухни спб[/url] .
изготовление кухни на заказ в спб [url=www.kuhni-spb-11.ru]www.kuhni-spb-11.ru[/url] .
кухни под заказ спб [url=www.kuhni-spb-9.ru]www.kuhni-spb-9.ru[/url] .
aviator money [url=https://aviator-game-cash.com/]aviator-game-cash.com[/url] .
fashioncrazehub – Browsing was simple, and the items were stylish and affordable.
aviation game [url=aviator-game-winner.com]aviation game[/url] .
Shop urban fashion – Quickly spotted a handful of stylish pieces, navigation effortless.
presenthub – Found lots of cool gifts, shipping seems dependable.
familyoutfitcentral – Enjoyed browsing the wide range, checkout was hassle-free.
Mindful Growth Daily – Practical resources for building confidence, skills, and inner strength.
Only the best materials: https://digitalmarketingtrends35555.blog-gold.com/52613256/nppr-team-shop-your-premier-hub-for-social-media-marketing-mastery
ко ланта ко лант
savebigstore – Great deals and smooth checkout, very satisfied today.
aviator game [url=http://www.aviator-game-cash.com]aviator game[/url] .
stylezone – Loved checking out products, navigation was smooth and hassle-free.
aviator game [url=http://aviator-game-winner.com/]aviator game[/url] .
besturbanvalue – Fast-loading pages and intuitive layout made shopping fun.
SoftStone Outlet – Easy-to-browse site, great variety, and shipping was quick.
glamseasonstore – Stylish items and smooth website experience, very satisfied.
aviator bonus game [url=https://www.aviator-game-cash.com]https://www.aviator-game-cash.com[/url] .
trendfinder – Nice assortment available, site navigation felt effortless.
Your Motivation Spot – Daily tips to nurture ambition and keep moving toward your objectives.
топ агентств seo продвижения [url=www.reiting-seo-kompanii.ru/]www.reiting-seo-kompanii.ru/[/url] .
???????? ???? ??? [url=aviator-game-predict.com]aviator-game-predict.com[/url] .
лучшие компании по ремонту квартир в москве [url=http://rejting-remontnyh-kompanij-moskvy.com]лучшие компании по ремонту квартир в москве[/url] .
win crash game [url=www.aviator-game-best.com]win crash game[/url] .
компании по ремонту [url=https://luchshie-remontnye-kompanii-moskvy.com/]компании по ремонту[/url] .
ремонт квартиры под ключ фото и цены в москве [url=https://luchshie-kompanii-po-remontu-kvartir-v-moskve.com]https://luchshie-kompanii-po-remontu-kvartir-v-moskve.com[/url] .
flight game money [url=www.aviator-game-deposit.com/]www.aviator-game-deposit.com/[/url] .
aviator bonus game [url=https://aviator-game-winner.com]https://aviator-game-winner.com[/url] .
фирмы ремонт квартир в москве [url=www.rejting-kompanij-po-remontu-kvartir-moskvy.com]www.rejting-kompanij-po-remontu-kvartir-moskvy.com[/url] .
мелбет слоты вход [url=https://wwwpsy.ru/]wwwpsy.ru[/url] .
melbet [url=https://v-bux.ru]https://v-bux.ru[/url] .
электрические карнизы купить [url=http://elektrokarnizmsk.ru]http://elektrokarnizmsk.ru[/url] .
электрокарниз двухрядный цена [url=http://elektrokarnizmsk.ru]http://elektrokarnizmsk.ru[/url] .
мелбет бонусы [url=https://melbetbonusy.ru/]melbetbonusy.ru[/url] .
stylevaulthub – Great trendy selection, navigating the site is quick and easy.
chiccollection – Loved the selections, the site loaded fast and navigation was easy.
WildSand Hub – Loved the assortment, smooth checkout, and the package arrived safely.
Your Dream Journey – Tools and advice to help you dream bigger and make steady progress.
lucky88
EverMountain Collection – Browsing was seamless and all items caught my eye.
Lunar Harvest Choice – Smooth browsing and a friendly, tidy layout throughout.
Soft Cloud Online Finds – Easy navigation and products are neatly organized.
рейтинг компаний по ремонту квартир [url=http://rejting-remontnyh-kompanij-moskvy.com]http://rejting-remontnyh-kompanij-moskvy.com[/url] .
plane crash real money game [url=https://www.aviator-game-predict.com]https://www.aviator-game-predict.com[/url] .
отделка ремонт квартир москва [url=https://luchshie-remontnye-kompanii-moskvy.com]https://luchshie-remontnye-kompanii-moskvy.com[/url] .
ищу мастера по ремонту квартир москва [url=http://www.luchshie-kompanii-po-remontu-kvartir-v-moskve.com]http://www.luchshie-kompanii-po-remontu-kvartir-v-moskve.com[/url] .
win crash game [url=https://aviator-game-best.com/]win crash game[/url] .
казино слоты играть [url=wwwpsy.ru]wwwpsy.ru[/url] .
электрокарниз купить [url=https://www.elektrokarnizmsk.ru]электрокарниз купить[/url] .
Bright Flora Hub – Items are organized nicely, and browsing is enjoyable.
электронный карниз для штор [url=https://elektrokarnizmsk.ru/]электронный карниз для штор[/url] .
fashionfindhub – Excellent range of items, quick browsing and easy ordering.
udane wala jahaj [url=www.aviator-game-deposit.com/]www.aviator-game-deposit.com/[/url] .
рейтинг компаний по ремонту квартир в москве [url=http://www.rejting-kompanij-po-remontu-kvartir-moskvy.com]рейтинг компаний по ремонту квартир в москве[/url] .
https://v-bux.ru [url=http://v-bux.ru]http://v-bux.ru[/url] .
timelessharborboutique – Fast-loading pages and organized products for effortless browsing.
urbanshopperhub – Very pleased with products, pricing is excellent and affordable.
trendylane – Nice assortment of urban styles, shopping experience was convenient.
v
FreshWind Select – Nice collection, well-shot images, and a comfortable shopping experience.
ремонт квартир сайты москва [url=https://rejting-remontnyh-kompanij-moskvy.com/]rejting-remontnyh-kompanij-moskvy.com[/url] .
???????? ???? ??? [url=https://aviator-game-predict.com]https://aviator-game-predict.com[/url] .
Modern Harbor Market – Shopping feels seamless, and everything displays clearly.
рулонные шторы на электроприводе [url=www.rulonnye-zhalyuzi-avtomaticheskie.ru]рулонные шторы на электроприводе[/url] .
Creative Projects Hub – Ideas and tips to explore your creativity in practical ways.
рулонные шторы с электроприводом и дистанционным управлением [url=https://www.avtomaticheskie-rulonnye-shtory11.ru]https://www.avtomaticheskie-rulonnye-shtory11.ru[/url] .
aviator bonus game [url=https://aviator-game-best.com]https://aviator-game-best.com[/url] .
слоты на деньги [url=https://wwwpsy.ru]https://wwwpsy.ru[/url] .
лучшая компания по ремонту квартир [url=www.luchshie-remontnye-kompanii-moskvy.com/]лучшая компания по ремонту квартир[/url] .
bestuniquebuy – Fast loading pages and intuitive layout made shopping fun.
карниз моторизованный [url=http://elektrokarnizmsk.ru/]http://elektrokarnizmsk.ru/[/url] .
электрокарниз купить в москве [url=http://elektrokarnizmsk.ru/]электрокарниз купить в москве[/url] .
фирма по ремонту квартир в москве [url=www.luchshie-kompanii-po-remontu-kvartir-v-moskve.com/]фирма по ремонту квартир в москве[/url] .
Full Circle Select – Clean layout and fast-loading pages make shopping pleasant.
glamtrendhub – Nice trendy selection, navigating the site was fast and effortless.
мелбет бк [url=https://www.v-bux.ru]https://www.v-bux.ru[/url] .
plane crash money game [url=www.aviator-game-deposit.com]www.aviator-game-deposit.com[/url] .
ремонт квартир фирмы [url=https://www.rejting-kompanij-po-remontu-kvartir-moskvy.com]ремонт квартир фирмы[/url] .
you’re really a good webmaster. The website loading pace is amazing. It seems that you are doing any distinctive trick. Also, The contents are masterwork. you’ve done a great job in this matter!
Find independent escorts Brasilia
shopnfind – Items loaded quickly, exploring deals was smooth and simple.
PureField Collection – Smooth experience with well-arranged products.
Bright Wind Boutique – Very impressed with the items and how easy the buying process was.
lucky88
Timber Grove Outlet – Browsing is smooth, and the products are easy to find.
рулонные шторы это [url=https://www.rulonnye-zhalyuzi-avtomaticheskie.ru]https://www.rulonnye-zhalyuzi-avtomaticheskie.ru[/url] .
dailydealshub – Loved browsing today’s deals, site navigation was very smooth.
stylefinderhub – Loved the variety, purchasing online was very easy.
рулонные шторы купить москва недорого [url=http://www.avtomaticheskie-rulonnye-shtory11.ru]рулонные шторы купить москва недорого[/url] .
NatureRail Essentials Hub – Items are simple to explore with a calm, natural presentation.
Harbor Calm Treasures – Simple navigation and a peaceful shopping experience.
stylehub – Loved the trendy picks, navigating and checkout were smooth and simple.
Silver Moon Corner – Loved the products, intuitive website, and very fast delivery today.
relaxhub – Smooth layout and easy to navigate, made shopping enjoyable.
Modern Ridge Finds – Navigation is easy, and exploring items feels effortless.
trendhubonline – Stylish products were easy to browse, delivery was smooth.
рулонные шторы с пультом [url=https://rulonnye-zhalyuzi-avtomaticheskie.ru/]рулонные шторы с пультом[/url] .
BrightRoot Studio Shop – Quick navigation, and the layout is very user-friendly.
topdealfinds – Enjoyed browsing the wide range, checkout was hassle-free.
bsme ru
рулонные шторы с электроприводом купить [url=https://www.avtomaticheskie-rulonnye-shtory11.ru]рулонные шторы с электроприводом купить[/url] .
голосовое управление жалюзи [url=www.elektricheskie-zhalyuzi5.ru/]www.elektricheskie-zhalyuzi5.ru/[/url] .
metatrader 5 download mac [url=metatrader-5-sync.com]metatrader-5-sync.com[/url] .
metatrader 5 [url=www.metatrader-5-platform.com]metatrader 5[/url] .
metatrader 5 [url=https://metatrader-5-pc.com/]metatrader 5[/url] .
Intentional Living Daily – Practical resources to guide your growth and purposeful actions.
оценка ущерба при заливе квартиры [url=ekspertiza-zaliva-kvartiry-1.ru]ekspertiza-zaliva-kvartiry-1.ru[/url] .
download metatrader 5 [url=www.metatrader-5-mt5.com/]download metatrader 5[/url] .
оценка повреждений после залива [url=https://ekspertiza-zaliva-kvartiry-2.ru]https://ekspertiza-zaliva-kvartiry-2.ru[/url] .
порядок оценки ущерба при заливе [url=https://ekspertiza-zaliva-kvartiry-4.ru/]ekspertiza-zaliva-kvartiry-4.ru[/url] .
оценка повреждений после залива [url=www.ekspertiza-zaliva-kvartiry-3.ru]www.ekspertiza-zaliva-kvartiry-3.ru[/url] .
mt5 [url=http://metatrader-5-downloads.com/]http://metatrader-5-downloads.com/[/url] .
mt5 mac download [url=www.metatrader-5-mac.com]www.metatrader-5-mac.com[/url] .
Timberwood Boutique Picks – Smooth navigation and visually appealing layout make shopping enjoyable.
Meadow Market Finds – Loved how simple the process was and the order arrived exactly on schedule.
Aurora Market – Everything is organized and browsing is a pleasure.
trendvalueonline – Affordable finds, website is intuitive and easy to browse.
WarmWinds Essentials – Quick and easy navigation, products are displayed nicely.
modcorner – Loved the clean interface and finding items was quick and easy.
happypicktrends – Great variety, shopping was enjoyable and hassle-free.
modahub – Found perfect fashion items quickly, delivery was prompt and easy.
срок проведения экспертизы залива [url=www.ekspertiza-zaliva-kvartiry-1.ru/]www.ekspertiza-zaliva-kvartiry-1.ru/[/url] .
meta trader 5 download [url=http://metatrader-5-sync.com/]http://metatrader-5-sync.com/[/url] .
mt5 mac [url=https://metatrader-5-pc.com]mt5 mac[/url] .
metatrader5 [url=http://metatrader-5-platform.com]metatrader5[/url] .
экспертиза после залива [url=ekspertiza-zaliva-kvartiry-3.ru]экспертиза после залива[/url] .
возмещение ущерба после залива [url=https://ekspertiza-zaliva-kvartiry-2.ru]возмещение ущерба после залива[/url] .
экспертиза по заливу квартиры [url=www.ekspertiza-zaliva-kvartiry-4.ru/]экспертиза по заливу квартиры[/url] .
metatrader 5 mac download [url=www.metatrader-5-mt5.com]metatrader 5 mac download[/url] .
Origin Peak Boutique – Loved the trendy items, checkout was smooth, and my order arrived quickly.
mt5 download mac [url=https://metatrader-5-downloads.com]https://metatrader-5-downloads.com[/url] .
meta trader 5 download [url=https://metatrader-5-mac.com/]metatrader-5-mac.com[/url] .
Whispering Trend Finds – Browsing is smooth and the selections are easy to explore.
KindleCrest Market – Items are easy to explore and the site layout is tidy.
Open Plains Market Online – Shopping is fast, and products are well organized.
fashionflare – Found stylish items effortlessly, checkout was fast.
pg ????? khao555.com
savemoretoday – Lots of good deals to check out, website loaded quickly.
uniquetrendpicks – Great variety of items, shopping was enjoyable and effortless.
choicepick – Smooth navigation, discovering products was quick and easy.
ко ланта таиланд
как провести оценку ущерба после залива [url=www.ekspertiza-zaliva-kvartiry-2.ru/]www.ekspertiza-zaliva-kvartiry-2.ru/[/url] .
mt5 download for pc [url=https://metatrader-5-sync.com]https://metatrader-5-sync.com[/url] .
залив с крыши оценка ущерба [url=http://ekspertiza-zaliva-kvartiry-1.ru]http://ekspertiza-zaliva-kvartiry-1.ru[/url] .
metatrader 5 mac download [url=https://metatrader-5-pc.com/]metatrader 5 mac download[/url] .
mt5 mac [url=https://metatrader-5-platform.com]https://metatrader-5-platform.com[/url] .
залили соседи оценка ущерба [url=ekspertiza-zaliva-kvartiry-3.ru]ekspertiza-zaliva-kvartiry-3.ru[/url] .
документы для оценки ущерба после залива [url=https://ekspertiza-zaliva-kvartiry-4.ru]документы для оценки ущерба после залива[/url] .
Soft Blossom Corner – Beautiful collection, website was easy to browse, and my order went through without any issues.
RedMoon Picks – Easy to find products, all are unique and appealing.
download mt5 for mac [url=www.metatrader-5-mt5.com]download mt5 for mac[/url] .
Wardrobe Essentials Daily – Practical and trendy pieces to upgrade your everyday look.
download metatrader 5 [url=https://www.metatrader-5-mac.com]download metatrader 5[/url] .
mt5 trading platform [url=http://metatrader-5-downloads.com/]http://metatrader-5-downloads.com/[/url] .
dailysavingshub – Loved today’s deals, items arrived quickly and in perfect shape.
Coastline Spot – Products are easy to spot, and the site feels calm and user-friendly.
продажа складных лесов Аренда штукатурных лесов: Штукатурные леса специально разработаны для проведения штукатурных работ на фасадах зданий. Аренда таких лесов обеспечивает удобство и безопасность рабочих, а также позволяет установить необходимое оборудование для подачи и нанесения штукатурных смесей. Широкая платформа и устойчивая конструкция позволяют повысить производительность и качество выполняемых работ.
Sunwave Essentials Picks – Products are easy to find and the interface is friendly.
decorfinds – Plenty of nice home goods, browsing was quick and simple.
topfashionhub – Wide variety of fashion items, navigation felt seamless and natural.
fashioncornerhub – The layout is clean, and exploring items was smooth and simple.
BrightSpark Hub – Quick loading pages and intuitive product arrangement.
NobleRidge Shop – Modern looks, fast-loading pages, and a seamless purchase process.
Kind Groove Essentials – Navigation is simple, and items are displayed clearly.
как провести оценку ущерба после залива [url=www.ekspertiza-zaliva-kvartiry-2.ru]www.ekspertiza-zaliva-kvartiry-2.ru[/url] .
download metatrader 5 [url=https://metatrader-5-sync.com/]metatrader-5-sync.com[/url] .
экспертиза залива для суда [url=www.ekspertiza-zaliva-kvartiry-3.ru/]www.ekspertiza-zaliva-kvartiry-3.ru/[/url] .
mt5 mac download [url=http://metatrader-5-pc.com]http://metatrader-5-pc.com[/url] .
автоматические шторы на окна [url=rulonnye-zhalyuzi-avtomaticheskie.ru]автоматические шторы на окна[/url] .
Self-Improvement Daily – Inspiring guidance to help you improve yourself regularly.
metatrader 5 mac download [url=https://www.metatrader-5-platform.com]metatrader 5 mac download[/url] .
стоимость восстановительного ремонта после залива [url=https://ekspertiza-zaliva-kvartiry-1.ru/]https://ekspertiza-zaliva-kvartiry-1.ru/[/url] .
стоимость восстановительного ремонта после залива [url=www.ekspertiza-zaliva-kvartiry-4.ru/]стоимость восстановительного ремонта после залива[/url] .
mt5 trading platform [url=https://metatrader-5-mt5.com]mt5 trading platform[/url] .
metatrader5 [url=http://metatrader-5-downloads.com]http://metatrader-5-downloads.com[/url] .
рулонные шторы в москве [url=http://www.avtomaticheskie-rulonnye-shtory11.ru]рулонные шторы в москве[/url] .
mt5 mac download [url=http://metatrader-5-mac.com]http://metatrader-5-mac.com[/url] .
Blue Grain Corner – Easily discovered quality items and browsing felt intuitive.
BoldHorizon Marketplace – Great store structure, really easy to explore.
freshgiftspot – Pleasant experience, site was simple to navigate and order items.
trendhubzone – The interface is intuitive, making shopping straightforward.
KindleWood Emporium – Great browsing, clear product images, and prompt shipping.
Dream Harbor Choice – Items are well presented, and shopping is fast and easy.
досудебная экспертиза залива [url=http://ekspertiza-zaliva-kvartiry-2.ru/]http://ekspertiza-zaliva-kvartiry-2.ru/[/url] .
metatrader 5 mac [url=metatrader-5-sync.com]metatrader-5-sync.com[/url] .
как провести оценку ущерба после залива [url=https://www.ekspertiza-zaliva-kvartiry-3.ru]https://www.ekspertiza-zaliva-kvartiry-3.ru[/url] .
metatrader5 [url=https://metatrader-5-pc.com]metatrader5[/url] .
оценка мебели после залива [url=https://ekspertiza-zaliva-kvartiry-1.ru/]ekspertiza-zaliva-kvartiry-1.ru[/url] .
рулонные шторы на пластиковые окна с электроприводом [url=http://rulonnye-zhalyuzi-avtomaticheskie.ru/]рулонные шторы на пластиковые окна с электроприводом[/url] .
залив с крыши оценка ущерба [url=https://www.ekspertiza-zaliva-kvartiry-4.ru]https://www.ekspertiza-zaliva-kvartiry-4.ru[/url] .
metatrader5 [url=https://metatrader-5-platform.com/]metatrader5[/url] .
metatrader5 [url=https://www.metatrader-5-mt5.com]metatrader5[/url] .
NewVoyage Treasures Shop – Smooth navigation, products are easy to browse and appealing.
mt5 download mac [url=https://metatrader-5-downloads.com/]metatrader-5-downloads.com[/url] .
автоматическая рулонная штора [url=http://www.avtomaticheskie-rulonnye-shtory11.ru]http://www.avtomaticheskie-rulonnye-shtory11.ru[/url] .
metatrader 5 mac download [url=https://metatrader-5-mac.com]https://metatrader-5-mac.com[/url] .
onyx-55
findscenterhub – Smooth site layout, fast loading pages, and enjoyable shopping experience.
Wild Horizon Collection – Easy-to-use site, fashionable items, and my order went smoothly.
shoppingzonehub – Products are easy to find and the site responds quickly.
Bridgetown Essentials – Finding what you need is fast and the setup is clean.
стоимость экспертизы залива [url=http://www.ekspertiza-zaliva-kvartiry-2.ru]http://www.ekspertiza-zaliva-kvartiry-2.ru[/url] .
WildSpark Choice – Very easy to explore, products are fun and accessible.
mt5 trading platform [url=metatrader-5-sync.com]metatrader-5-sync.com[/url] .
mt5 download for pc [url=http://metatrader-5-pc.com]mt5 download for pc[/url] .
залили соседи оценка ущерба [url=ekspertiza-zaliva-kvartiry-3.ru]ekspertiza-zaliva-kvartiry-3.ru[/url] .
какие бывают рулонные шторы [url=https://rulonnye-zhalyuzi-avtomaticheskie.ru/]https://rulonnye-zhalyuzi-avtomaticheskie.ru/[/url] .
оценка техники после затопления [url=www.ekspertiza-zaliva-kvartiry-1.ru]www.ekspertiza-zaliva-kvartiry-1.ru[/url] .
metatrader 5 download mac [url=www.metatrader-5-platform.com/]metatrader 5 download mac[/url] .
оценка ущерба после затопления [url=http://ekspertiza-zaliva-kvartiry-4.ru/]оценка ущерба после затопления[/url] .
электрическая рулонная штора [url=http://www.avtomaticheskie-rulonnye-shtory11.ru]http://www.avtomaticheskie-rulonnye-shtory11.ru[/url] .
forex metatrader 5 [url=http://www.metatrader-5-downloads.com]http://www.metatrader-5-downloads.com[/url] .
download mt5 for mac [url=http://metatrader-5-mt5.com]download mt5 for mac[/url] .
metatrader 5 download mac [url=https://metatrader-5-mac.com/]https://metatrader-5-mac.com/[/url] .
shoppinghub247 – Quick loading pages and a really smooth shopping journey.
Grand Style Central – Navigation is intuitive and items are well presented.
HonestHarvest Finds Hub – Browsing was quick and all items are neatly displayed.
curiouscorner – Smooth layout, intuitive navigation, and items are easy to explore.
бонусы букмекеров Выбор надежной букмекерской конторы – это фундамент успешного беттинга. Букмекерские конторы различаются по коэффициентам, линии, наличию бонусов и промоакций, удобству интерфейса и надежности выплат. Перед тем, как сделать ставку, необходимо тщательно изучить репутацию букмекерской конторы, ознакомиться с отзывами пользователей и убедиться в наличии лицензии. Для принятия обоснованных решений в ставках на спорт необходимо обладать актуальной информацией и аналитическими данными. Прогнозы на баскетбол, прогнозы на футбол и прогнозы на хоккей – это ценный инструмент, позволяющий оценить вероятности различных исходов и принять взвешенное решение. Однако, стоит помнить, что прогнозы – это всего лишь вероятностные оценки, и они не гарантируют стопроцентный результат.
DeepStone Picks – The site feels responsive and all products are easy to check out.
Market Trends Daily – Handpicked collections that make finding trendy items simple and fun.
Future Groove Spot – Shopping feels effortless, and items are well arranged.
Morning Rust Deals – Finding products is simple and the interface looks clean.
stayhub – Smooth interface, fast loading, and items are visually appealing.
AutumnLeaf Collective – Loved discovering unique items, everything is simple to access.
Urban Peak Selection – Browsing is smooth and products are easy to find.
Trendy Style Spot – Handpicked fashion items to elevate your style effortlessly.
https://mvkursk.ru/sovety/semena-gazona-gde-v-moskve-najti-kachestvennye-i-nedorogie-varianty.html
EverPath Hub – Easy to explore items and the layout feels welcoming.
UnionSquare Market Place – Items are well arranged, and browsing the site is effortless.
motivatedcorner – Well-structured layout, items easy to explore, and navigation feels seamless.
Dawncrest Boutique – Items are easy to explore, and the site feels inviting.
UnionSquare Market Place – Items are well arranged, and browsing the site is effortless.
Lunar Wave Finds – Browsing is easy and the items are well-organized and appealing.
urbanhubcentral – Navigation is effortless, and all products are neatly arranged.
Starlit Style Picks – The interface is clean, and finding products feels simple.
филлер цена [url=www.filler-kupit1.ru]www.filler-kupit1.ru[/url] .
Потолочные плиты Армстронг [url=https://potolok-armstrong1.ru]https://potolok-armstrong1.ru[/url] .
электрокарнизы для штор купить в москве [url=https://www.elektrokarnizmoskva.ru]https://www.elektrokarnizmoskva.ru[/url] .
заказ курсовых работ [url=https://kupit-kursovuyu-1.ru/]https://kupit-kursovuyu-1.ru/[/url] .
оценка техники после затопления [url=http://ekspertiza-zaliva-kvartiry-5.ru/]http://ekspertiza-zaliva-kvartiry-5.ru/[/url] .
купить курсовую москва [url=kupit-kursovuyu-4.ru]купить курсовую москва[/url] .
филлер ру [url=www.filler-kupit.ru/]филлер ру[/url] .
помощь курсовые [url=http://kupit-kursovuyu-6.ru/]http://kupit-kursovuyu-6.ru/[/url] .
покупка курсовой [url=http://kupit-kursovuyu-8.ru/]http://kupit-kursovuyu-8.ru/[/url] .
курсовая работа на заказ цена [url=https://kupit-kursovuyu-5.ru/]курсовая работа на заказ цена[/url] .
купить курсовую работу [url=https://kupit-kursovuyu-7.ru/]купить курсовую работу[/url] .
написание курсовых работ на заказ цена [url=http://kupit-kursovuyu-3.ru]http://kupit-kursovuyu-3.ru[/url] .
топ агентства seo [url=www.reiting-seo-kompanii.ru]топ агентства seo[/url] .
заказ курсовых работ [url=www.kupit-kursovuyu-2.ru]www.kupit-kursovuyu-2.ru[/url] .
Best Budget Buys – Discover quality products at prices that are easy on your wallet.
Timberline Essentials – Browsing feels natural with a neat and organized design.
LostMeadow Essentials – Clean layout and items are easy to browse quickly.
urbanhub – Clean layout and fast-loading pages made exploring items simple.
покупка курсовой [url=http://kupit-kursovuyu-1.ru/]http://kupit-kursovuyu-1.ru/[/url] .
купить курсовую сайт [url=kupit-kursovuyu-6.ru]kupit-kursovuyu-6.ru[/url] .
FutureGardenSpot – Clean layout and intuitive navigation helped me shop efficiently.
помощь курсовые [url=www.kupit-kursovuyu-4.ru/]www.kupit-kursovuyu-4.ru/[/url] .
написание курсовых работ на заказ цена [url=http://www.kupit-kursovuyu-7.ru]http://www.kupit-kursovuyu-7.ru[/url] .
курсовая заказать [url=https://kupit-kursovuyu-3.ru]курсовая заказать[/url] .
лучшие seo агентства [url=www.reiting-seo-kompanii.ru]лучшие seo агентства[/url] .
great store page – Navigation felt natural and the site responded quickly.
написание курсовой на заказ цена [url=https://kupit-kursovuyu-8.ru/]написание курсовой на заказ цена[/url] .
написать курсовую работу на заказ в москве [url=https://kupit-kursovuyu-2.ru]https://kupit-kursovuyu-2.ru[/url] .
написание курсовой на заказ цена [url=http://kupit-kursovuyu-5.ru/]написание курсовой на заказ цена[/url] .
grove store – Smooth scrolling and clear sections made shopping simple.
golden collection – Navigation felt natural and products were visually appealing.
tallbirchlane – Shopping feels calm, layout is neat and intuitive.
GoldPlume Boutique Hub – Site feels user-friendly and the products are inviting.
timberlineatticcenter – Easy-to-use interface, perfect for experimenting and finding inspiration.
скачать игры с яндекс диска Скачать игры с Яндекс Диска: Персональная игровая библиотека всегда под рукой. Яндекс Диск – это не просто облачное хранилище, но и удобная платформа для обмена находками с друзьями и создания собственной коллекции. Делитесь любимыми играми, скачивайте новинки и наслаждайтесь совместным игровым опытом. Это отличный способ расширить горизонты и всегда иметь доступ к любимым развлечениям, где бы вы ни находились. Превратите Яндекс Диск в свой личный игровой рай!
Style Picks Daily – Navigate categories quickly and discover fashionable items easily.
EvergreenBoutique – Pleasant layout, finding items is quick and simple.
Khao555 Online
Sun Meadow Finds – Browsing was easy and items were neatly displayed, making shopping quick.
Wonder Peak Picks – Interface is user-friendly and finding products is easy.
shoppingcorner – Pages load fast, and finding products is quick and simple.
покупка курсовой [url=https://kupit-kursovuyu-6.ru/]https://kupit-kursovuyu-6.ru/[/url] .
курсовая работа недорого [url=http://kupit-kursovuyu-1.ru]http://kupit-kursovuyu-1.ru[/url] .
курсовая работа купить [url=http://www.kupit-kursovuyu-7.ru]курсовая работа купить[/url] .
Warm Timber Shop – The site feels welcoming, and moving through the product sections is quick and clear.
курсовые под заказ [url=http://kupit-kursovuyu-4.ru]курсовые под заказ[/url] .
browse styles – Found the items I needed right away thanks to the simple, organized layout.
написать курсовую работу на заказ в москве [url=www.kupit-kursovuyu-3.ru/]www.kupit-kursovuyu-3.ru/[/url] .
рейтинг digital seo агентств [url=https://reiting-seo-kompanii.ru/]https://reiting-seo-kompanii.ru/[/url] .
new grove access – Clear design and well-marked sections improved browsing.
курсовая работа купить [url=http://kupit-kursovuyu-8.ru/]курсовая работа купить[/url] .
курсовые под заказ [url=http://www.kupit-kursovuyu-2.ru]http://www.kupit-kursovuyu-2.ru[/url] .
birchoutletstore – Smooth interface, products are clearly displayed and easy to locate.
horizon hub link – Smooth interface and well-organized items enhanced browsing.
goldencresthaven – Well-organized listings and neat interface, made browsing simple.
bs2best at зеркало
заказать качественную курсовую [url=http://kupit-kursovuyu-5.ru/]заказать качественную курсовую[/url] .
brandelevate.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
BlueStone Goods – Navigation was effortless and the pages looked neat.
bright store link – Convenient navigation and simple menus helped me get around fast.
growhubzone – Seamless browsing experience, clear product display, and intuitive layout.
urban hub link – Smooth interface and well-organized items enhanced shopping.
brightbrookemporium – Browsing is intuitive, everything is easy to find.
golden collection – Navigation felt natural and products were visually appealing.
Timber Trail – Simple and clean design with easy-to-find products.
Timber Comfort Shop – The layout flows nicely, making browsing feel effortless and stress-free.
Northern Mist Emporium – Neat interface and organized products made selection quick and easy.
NewGroveEssentials Storefront – Everything was clear and easy to access, making browsing enjoyable.
Pine Crest Shop – Items are easy to find and the interface feels intuitive — very pleasant shopping experience.
Sun Meadow Selections – Organized pages and clear menus made shopping simple and efficient.
product corner – Finding items was quick thanks to the clean and uncluttered structure.
coastline shop – Browsing was smooth and products were easy to find.
курсовые работы заказать [url=https://kupit-kursovuyu-10.ru/]курсовые работы заказать[/url] .
вывод из запоя клиника москва [url=narkologicheskaya-klinika-36.ru]narkologicheskaya-klinika-36.ru[/url] .
клиника вывод из запоя [url=https://narkologicheskaya-klinika-38.ru/]https://narkologicheskaya-klinika-38.ru/[/url] .
заказ курсовых работ [url=www.kupit-kursovuyu-9.ru/]www.kupit-kursovuyu-9.ru/[/url] .
анонимная наркологическая помощь [url=https://narkologicheskaya-klinika-37.ru/]анонимная наркологическая помощь[/url] .
голосовое управление жалюзи [url=https://elektricheskie-zhalyuzi5.ru/]https://elektricheskie-zhalyuzi5.ru/[/url] .
наркологические клиники в москве [url=https://narkologicheskaya-klinika-35.ru/]narkologicheskaya-klinika-35.ru[/url] .
наркологическое отделение наркологии [url=https://www.narkologicheskaya-klinika-39.ru]https://www.narkologicheskaya-klinika-39.ru[/url] .
наркологический частный центр [url=http://www.narkologicheskaya-klinika-34.ru]http://www.narkologicheskaya-klinika-34.ru[/url] .
seo продвижение рейтинг [url=http://www.reiting-seo-kompanii.ru]seo продвижение рейтинг[/url] .
a href=”https://brightnorthboutique.shop/” />brightnorthstyle – Very intuitive design, browsing feels seamless.
a href=”https://growyourmindset.click/” />growthhub – Easy navigation with clearly organized products for a pleasant experience.
goldencraftshop – Easy-to-follow layout and neat product pages, shopping was fast.
Green Canopy – Neat layout with clearly grouped items for quick access.
shop willow hub – Neatly displayed products and clear navigation made shopping easy.
Вызвать эвакуатор Эвакуатор Таганрог – это не просто географическое указание, это обещание оперативной и профессиональной помощи водителям, оказавшимся в беде на дорогах этого прекрасного города.
бездепозитные бонусы казахстан за регистрацию в казино с выводом
Northern Mist Emporium – Neat interface and organized products made selection quick and easy.
Orchard Select – Products are neatly displayed and the menu is intuitive — very convenient to navigate.
Coastal Ridge Hub – Navigation is simple, and products are attractively listed.
Wild Shore Collection Online – Fast loading and clean interface made browsing effortless.
shop soft collection – Smooth navigation and neatly displayed products enhanced browsing.
покупка курсовой [url=https://kupit-kursovuyu-10.ru]покупка курсовой[/url] .
Growth & Potential Hub – Discover tips and inspiration to develop your skills and reach new heights.
купить курсовую сайт [url=www.kupit-kursovuyu-9.ru]купить курсовую сайт[/url] .
value marketplace – Lots of budget options available and moving around the site was hassle-free.
Lunar Peak Corner – Products are easy to spot and the site feels pleasant to explore.
Garden Haven – Clear product categories and simple layout helped locate items quickly.
топ компаний по продвижению сайтов [url=https://www.reiting-seo-kompanii.ru]топ компаний по продвижению сайтов[/url] .
бамбуковые электрожалюзи [url=www.elektricheskie-zhalyuzi5.ru/]www.elektricheskie-zhalyuzi5.ru/[/url] .
Orchard Finds – Nice presentation of products and smooth browsing — shopping felt easy.
homeselection – Products are clearly displayed, and moving through categories was effortless.
wildpeakemporium – Clean layout, shopping feels relaxed and intuitive.
evermeadowgoods – Great selection and intuitive navigation helped me explore products without hassle.
Bright Timber Studio – Clear layout and visible items helped me pick products easily.
Shop MountainMistStudio – The design felt polished and browsing felt very comfortable.
Wind Studio Corner – Well-organized pages made exploring items quick and stress-free.
shop moon hub – Items were easy to view and navigation felt natural.
курсовой проект купить цена [url=https://kupit-kursovuyu-10.ru/]курсовой проект купить цена[/url] .
Wolf Emporium – Simple interface and well-laid-out products made shopping convenient.
Urban Meadow Finds – Items load fast with clear presentation — shopping felt hassle-free.
Urban Seed Finds – Browsing was smooth and products were easy to locate.
рекламное агентство seo [url=http://www.reiting-seo-kompanii.ru]рекламное агентство seo[/url] .
Click To Enter Gallery – From the moment you arrive, the speed and clarity make a great impression.
Modern Fable Picks – Items are well organized, making shopping simple.
жалюзи на пульте [url=www.elektricheskie-zhalyuzi5.ru/]жалюзи на пульте[/url] .
success hub – The pages are organized well, making it easy to find what I need.
решение курсовых работ на заказ [url=https://kupit-kursovuyu-9.ru/]https://kupit-kursovuyu-9.ru/[/url] .
puregreenhaven – Pleasant interface, products are clearly visible and easy to explore.
softroseboutique – Tidy layout with easy navigation, products were easy to find.
sunset hub link – Smooth browsing and well-laid-out items improved the experience.
everypick – Clean layout and smooth browsing made exploring products quick.
EverRoot Studio Hub – Clean layout and well-presented products allowed me to shop quickly.
казахстане
Crest Picks – The website helped me quickly pick out interesting items.
Coastline Finds – Everything is easy to locate and the site feels organized — smooth online shopping.
golden hub corner – Clean design and clear categories made browsing enjoyable.
Bright Breeze – Clear product organization and effortless navigation improve the shopping experience.
GoldenBranchMart Store – Products were organized neatly, creating a smooth browsing experience.
Autumn Trends Online – Finding items is straightforward and the site is user-friendly.
future planner – Smooth navigation and items appear quickly without delays.
rootstyleboutique – Clean layout, shopping feels relaxed and effortless.
Fresh Meadow Emporium – Navigation is intuitive and exploring products is enjoyable.
City Style Spot – Browse stylish urban collections for an effortless wardrobe refresh.
Shop Here – A great mix of products and a clean design helped me shop without any hassle.
Urban Pasture Collections – Navigating through items is effortless, and the product variety is excellent.
BrightStone Picks – The clear design and product images helped me choose items easily.
moderncornerhub – Smooth interface, fast loading, and items are visually appealing.
клиника наркологии москва [url=http://narkologicheskaya-klinika-40.ru/]клиника наркологии москва[/url] .
Dream Ridge Goods – Items are neatly arranged with a clear interface — made exploring products simple.
Crest Artisan Studio – Easy navigation with well-laid-out items made shopping effortless.
Timber Crest Treasures Online – Clear layout and smooth browsing made exploring products simple.
bright collection – Clean layout and responsive pages enhanced the shopping experience.
Evergreen Spot – Everything is neatly arranged and shopping feels easy.
soft green link – Browsing felt fluid and the interface is nicely organized.
Подвесной потолок Армстронг [url=http://www.potolok-armstrong1.ru]http://www.potolok-armstrong1.ru[/url] .
cozycorneremporium – Everything is neatly organized, site feels pleasant to browse.
электрокарниз недорого [url=www.elektrokarnizmoskva.ru]www.elektrokarnizmoskva.ru[/url] .
карнизы для штор купить в москве [url=https://elektrokarniz1.ru]https://elektrokarniz1.ru[/url] .
raretrendstore – Fast-loading pages with tidy sections, browsing was enjoyable.
электрокарнизы москва [url=https://prokarniz36.ru]https://prokarniz36.ru[/url] .
рекламное агентство seo [url=http://reiting-seo-kompanii.ru]рекламное агентство seo[/url] .
досудебная экспертиза залива [url=https://ekspertiza-zaliva-kvartiry-5.ru/]досудебная экспертиза залива[/url] .
филлер для губ купить [url=filler-kupit.ru]филлер для губ купить[/url] .
LunarHarvest Mart – The site layout was clean and items were easy to locate quickly.
brightwinterstore – Products look appealing and navigation is smooth — a good shopping experience.
Mindful Growth Daily – Practical resources for building confidence, skills, and inner strength.
Wild Crest Online – Fast-loading items with simple navigation — browsing was effortless.
EverWild Studio Shop – Clear interface and visible items allowed me to explore products quickly.
Cozy Cabin Select – Easy to locate products with a friendly, clean interface.
Forest Nest – Well-structured product sections and simple navigation improved usability.
Your Next Find – The site’s excellent organization is matched by its impressively quick load speeds.
smilecentral – Fast-loading pages with tidy layout made shopping enjoyable.
поиск работы Удаленная работа — это способ организации труда, при котором задачи выполняются вне офиса с использованием интернета и цифровых инструментов. В современном мире удаленка становится нормой для многих профессий: от поддержки клиентов, копирайтинга и дизайна до разработки ПО, аналитики и онлайн-образования. Преимущества очевидны: гибкий график, возможность работать из любого места, экономия времени на дорогу и арендной плате за офис, доступ к глобальным рынкам труда и возможность сочетать работу с семьей или учебой. Для успешного старта важны базовые навыки тайм-менеджмента, коммуникации онлайн и умения работать с задачами в системах управления проектами (Trello, Asana, Jira) и документами (Google Docs, Office 365). Не менее важно настроить комфортное рабочее место дома, обеспечить устойчивый интернет и защиту персональных данных. В процессе карьеры удаленная работа учит самоорганизации, автономности и ответственности за результат. Но есть и сложности: риск переработок, ощущение изоляции, необходимость постоянной коммуникации в чатах и видео-конференциях, а также зависимость от качества связи и времени ответа коллег по разным часовым поясам. Чтобы минимизировать риски, рекомендуется устанавливать четкие границы между рабочим и личным временем, регулярно общаться с командой, планировать задачи на неделю и вкладывать время в профессиональное развитие.
shop timber picks – Items were easy to view and layout was clear.
Silver Moon Marketplace – Items are displayed neatly, making browsing simple and quick.
True Horizon Deals – Navigation is simple, and products are well organized.
Подвесной потолок Армстронг [url=https://potolok-armstrong1.ru/]potolok-armstrong1.ru[/url] .
электрокарнизы для штор купить в москве [url=www.elektrokarnizmoskva.ru]www.elektrokarnizmoskva.ru[/url] .
карниз для штор электрический [url=http://elektrokarniz1.ru/]http://elektrokarniz1.ru/[/url] .
discover lakes – Products were easy to navigate through and the interface felt inviting.
sunrisehubstore – Smooth interface, products are clearly displayed and easy to locate.
Goldleaf Collection – Nice variety of items and smooth navigation — very pleasant experience.
электрокарнизы купить в москве [url=prokarniz36.ru]prokarniz36.ru[/url] .
brightwillowboutique – Clean design and easy layout helped me find interesting items fast.
техническая экспертиза причин затопления [url=http://ekspertiza-zaliva-kvartiry-5.ru/]техническая экспертиза причин затопления[/url] .
Soft Dawn Shop – Smooth layout with clearly displayed products enhanced the experience.
Iron Valley Studio Shop – Simple interface and detailed visuals allowed for smooth shopping.
филлер [url=https://filler-kupit.ru/]филлер[/url] .
Dream Big Daily – Tips and strategies to turn aspirations into actionable results.
MidRiverDesigns Hub – Smooth navigation and well-displayed items improved the experience.
rusticridgeboutique – Pleasant browsing experience, items are easy to view and site feels well structured.
BrightMoor Goods – Well-organized menus made browsing a pleasure.
Whitestone Shop – Navigation feels simple and exploring items was smooth.
valueselection – Fast navigation, clear product display, and shopping was effortless.
Discover More – I never got lost thanks to the clear and consistent site navigation.
Подвесной потолок Армстронг [url=https://potolok-armstrong1.ru/]https://potolok-armstrong1.ru/[/url] .
карниз для штор с электроприводом [url=http://www.elektrokarniz1.ru]http://www.elektrokarniz1.ru[/url] .
карниз моторизованный [url=https://elektrokarnizmoskva.ru/]https://elektrokarnizmoskva.ru/[/url] .
modern hub access – Browsing felt comfortable and the layout made exploration easy.
Ocean Leaf Boutique – Items are easy to locate with a clean interface — shopping was smooth.
hillfashionstore – Items are neatly arranged, making browsing quick and enjoyable.
бифазные филлеры [url=https://filler-kupit1.ru/]filler-kupit1.ru[/url] .
silvertrendstore – Well-structured interface and intuitive navigation, shopping was simple.
Mountain Leaf Hub – Logical product arrangement and simple interface made shopping effortless.
brightfallstudio – Enjoyed browsing here, items seem well curated and easy to explore.
Hi, its pleasant paragraph concerning media print, we all understand media is a fantastic source of data.
https://whatsyournormal.com/uncategorized/melbet-zerkalo-rabochee-2025/
электрокарнизы для штор купить в москве [url=https://www.prokarniz36.ru]https://www.prokarniz36.ru[/url] .
наркологические услуги [url=narkologicheskaya-klinika-35.ru]narkologicheskaya-klinika-35.ru[/url] .
оценка ущерба после затопления [url=ekspertiza-zaliva-kvartiry-5.ru]оценка ущерба после затопления[/url] .
Soft Feather Emporium – Clear design and easy navigation made exploring products enjoyable.
интернет магазин филлеров [url=http://www.filler-kupit.ru]интернет магазин филлеров[/url] .
studio picks – Easy-to-use layout and organized categories made browsing enjoyable.
Silver Moon Fabrics Finds – Very easy to navigate, and the items were displayed clearly.
New Dawn Essentials Online – Items are easy to explore and layout feels natural — very smooth experience.
Visit PineHill Studio – Simple structure and clean pages made browsing easy and comfortable.
creategrow – The layout is tidy and navigating between items felt effortless.
Sunny Slope Deals – Easy to explore products and the layout is organized.
купить филлеры для косметологов [url=http://www.filler-kupit1.ru]http://www.filler-kupit1.ru[/url] .
product corner – Everything loaded fast and categories were easy to navigate.
calmforestlane – Smooth interface, navigating items is simple and relaxing.
Wild Treasure Store – Fast-loading pages and well-arranged products made browsing enjoyable.
SoftMorning Home – I was immediately impressed by the high-quality visuals and clean site structure.
EverduneGoods Store – Nicely arranged sections made checking products quick and simple.
winter boutique – Clean layout and intuitive navigation made shopping simple.
DeepBrook Treasures Hub – Clean interface and well-organized products made shopping enjoyable.
клиника наркологическая платная [url=https://narkologicheskaya-klinika-35.ru]https://narkologicheskaya-klinika-35.ru[/url] .
топ 10 честных казино на деньги
1win официальный сайт вход [url=http://1win12044.ru]http://1win12044.ru[/url]
wild collection hub – Fast pages and tidy layout made browsing pleasant and easy.
Moon Haven Collection Online – Pleasant browsing experience thanks to clean design and organized sections.
Lush Valley Studio Online – Items are clearly displayed and navigation is smooth — browsing was simple.
филлеры для косметологии купить [url=www.filler-kupit1.ru]www.filler-kupit1.ru[/url] .
Starlight Studio – User-friendly interface with items clearly displayed for fast browsing.
coastalmistshop – Smooth browsing and a clear layout made finding items effortless.
sunwave picks – Fast pages and neat categories made browsing enjoyable.
Timeless Harvest Essentials – Neatly presented items and a clean layout made browsing effortless.
Vibe Picks – The catalog layout is intuitive, and exploring items is effortless.
silver finds – Browsing was smooth, and the site’s polished look made it pleasant to use.
naturepickshop – Easy to navigate and products are clear, shopping was hassle-free.
анонимная наркологическая помощь [url=https://www.narkologicheskaya-klinika-35.ru]https://www.narkologicheskaya-klinika-35.ru[/url] .
Wild Coast Collection – User-friendly interface and well-displayed products made browsing hassle-free.
FashionGlowHub – Loved the trendy selection, browsing was smooth and very enjoyable.
TrendyLifeCorner – Very engaging content, easy to navigate and fun to read.
EF Home Collection – Products look well arranged, and navigation felt smooth from start to finish.
Moon Haven Online – Items are neatly arranged and browsing is simple — very relaxed experience.
moon star store – Fast pages and organized categories improved browsing.
Corner of BrightMoor – Everything is nicely categorized, which made shopping straightforward.
Explore SunCrestCrafthouse – Navigation was intuitive and the layout was very user-friendly.
Harbor Studio Hub – Well-organized items and smooth navigation made finding products simple.
lunarforestemporium – Very clean layout, shopping feels comfortable and intuitive.
топ 10 казино
emporium selection – Pages were responsive and products were easy to locate.
everpeakcorner – Clean interface and clear product display helped make browsing smooth and easy.
top picks store – Easy to navigate and the overall presentation made checking products enjoyable.
электрокарнизы для штор цена [url=http://elektrokarniz495.ru/]электрокарнизы для штор цена[/url] .
Explore Rustic River – Smooth interface with a cozy aesthetic made browsing effortless.
автоматические карнизы для штор [url=http://www.provorota.su]http://www.provorota.su[/url] .
электрокарнизы москва [url=www.elektrokarniz2.ru]www.elektrokarniz2.ru[/url] .
Urban Stone Online – Everything is neatly organized and intuitive — shopping was comfortable.
Soft Leaf Corner – Easy-to-navigate layout and visible products made shopping effortless.
промокоды на 1win [url=http://1win12043.ru]промокоды на 1win[/url]
карниз электро [url=https://elektrokarnizy77.ru]https://elektrokarnizy77.ru[/url] .
карнизы для штор купить в москве [url=elektrokarniz-dlya-shtor11.ru]карнизы для штор купить в москве[/url] .
центр наркологии москва [url=http://narkologicheskaya-klinika-36.ru/]http://narkologicheskaya-klinika-36.ru/[/url] .
автоматические карнизы для штор [url=http://www.elektrokarniz-dlya-shtor15.ru]автоматические карнизы для штор[/url] .
FashionSelectOnline – Stylish pieces with a smooth shopping process, really enjoyable today.
карниз электроприводом штор купить [url=https://elektrokarniz98.ru]https://elektrokarniz98.ru[/url] .
лечение зависимостей в москве [url=www.narkologicheskaya-klinika-37.ru/]www.narkologicheskaya-klinika-37.ru/[/url] .
электрокарниз купить [url=https://elektrokarniz-dlya-shtor499.ru]электрокарниз купить[/url] .
studio picks – Navigation flows naturally and items are easy to view.
частная наркологическая клиника в москве анонимное [url=www.narkologicheskaya-klinika-39.ru]www.narkologicheskaya-klinika-39.ru[/url] .
лечение зависимостей в москве [url=www.narkologicheskaya-klinika-34.ru/]www.narkologicheskaya-klinika-34.ru/[/url] .
LifestyleBuzzHub – Articles are fresh and exciting, loved exploring the site.
Lush Treasures – Clean design and structured categories made finding products easy.
Check Out The Store – Exploring the product range felt completely seamless due to the smart organization.
Urban Textiles – Well-structured pages and easy-to-find items made exploring effortless.
clovercornerstore – Pleasant layout, items are easy to find and browse.
brightvillagecorner – Items look appealing and layout feels user-friendly and welcoming overall.
leaf outlet – Clear layout and intuitive navigation made shopping simple.
Timberlake Treasures – Clear visuals and tidy layout — shopping felt effortless and enjoyable.
popular trends – The structure made it easy to move around and the items were laid out in a visually pleasing way.
Shop TallPineEmporium – Products were well displayed, making browsing straightforward.
карниз электро [url=https://elektrokarniz495.ru/]elektrokarniz495.ru[/url] .
wildmeadowstore – Clean interface with organized listings, browsing was effortless.
карниз с приводом для штор [url=www.provorota.su]www.provorota.su[/url] .
прокарниз [url=www.elektrokarniz2.ru]www.elektrokarniz2.ru[/url] .
Fresh Pine Designs – Fast-loading pages and organized products made browsing hassle-free.
прокарниз [url=http://elektrokarniz-dlya-shtor11.ru]http://elektrokarniz-dlya-shtor11.ru[/url] .
электронный карниз для штор [url=www.elektrokarnizy77.ru/]электронный карниз для штор[/url] .
трезвая жизнь [url=www.narkologicheskaya-klinika-36.ru/]www.narkologicheskaya-klinika-36.ru/[/url] .
электрокарнизы цена [url=http://elektrokarniz-dlya-shtor15.ru/]электрокарнизы цена[/url] .
электрические гардины для штор [url=https://elektrokarniz-dlya-shtor499.ru]https://elektrokarniz-dlya-shtor499.ru[/url] .
Soft Blossom Picks – Browsing felt calm and organized, thanks to the soft design and clean layout.
электрокарниз купить в москве [url=www.elektrokarniz98.ru/]электрокарниз купить в москве[/url] .
shop wooden hub – Navigation was intuitive and products were neatly displayed.
бездепозитные бонусы казахстан за регистрацию в казино с выводом
New Harbor Flowers – Smooth browsing and appealing images enhanced the overall experience.
клиника наркологическая платная [url=https://www.narkologicheskaya-klinika-37.ru]https://www.narkologicheskaya-klinika-37.ru[/url] .
QuickBuyOnline – Found exactly what I needed, the process was effortless and smooth.
наркологические услуги в москве [url=www.narkologicheskaya-klinika-39.ru/]www.narkologicheskaya-klinika-39.ru/[/url] .
клиника наркологическая платная [url=www.narkologicheskaya-klinika-34.ru]www.narkologicheskaya-klinika-34.ru[/url] .
Future Harbor Outlet – The site is well-structured and made exploring products straightforward.
алко помощь наркологическая [url=www.narkologicheskaya-klinika-38.ru/]www.narkologicheskaya-klinika-38.ru/[/url] .
Discover UrbanMist – A quick and simple experience defined by its variety and user-centric design.
ModernGoodsMarket – Loved the items, smooth browsing and prompt delivery.
Moonlit Market – Items are clearly displayed and navigation is simple — shopping was convenient.
stone finds – Smooth scrolling and organized layout made it easy to view items.
wildleafemporiumhub – Products are clearly presented, navigating the store is simple and smooth.
revival shop link – Smooth navigation overall, and everything appeared quickly without delays.
помощь нарколога [url=https://narkologicheskaya-klinika-40.ru]помощь нарколога[/url] .
Explore Whats Possible – The site loaded fast and the layout made browsing products feel smooth and simple.
прокарниз [url=http://elektrokarniz495.ru]http://elektrokarniz495.ru[/url] .
электрокарниз [url=https://www.elektrokarniz-dlya-shtor499.ru]электрокарниз[/url] .
электрические карнизы купить [url=http://www.elektrokarniz-dlya-shtor11.ru]http://www.elektrokarniz-dlya-shtor11.ru[/url] .
электрокарнизы цена [url=https://elektrokarnizy77.ru/]электрокарнизы цена[/url] .
Lush Grove Treasures – Organized pages and visible products made browsing quick and enjoyable.
наркологическая клиника в москве [url=https://narkologicheskaya-klinika-36.ru/]наркологическая клиника в москве[/url] .
электрокарниз двухрядный цена [url=https://www.elektrokarniz-dlya-shtor15.ru]https://www.elektrokarniz-dlya-shtor15.ru[/url] .
карниз с электроприводом [url=provorota.su]provorota.su[/url] .
электрокарниз купить [url=http://www.elektrokarniz2.ru]http://www.elektrokarniz2.ru[/url] .
River Hub – Clean interface with neatly grouped products enhanced the shopping experience.
наркологическое отделение наркологии [url=https://narkologicheskaya-klinika-34.ru]https://narkologicheskaya-klinika-34.ru[/url] .
soft picks hub – Fast pages and tidy layout made exploring products effortless.
наркологическая служба [url=www.narkologicheskaya-klinika-39.ru/]www.narkologicheskaya-klinika-39.ru/[/url] .
наркологические услуги в москве [url=http://www.narkologicheskaya-klinika-37.ru]http://www.narkologicheskaya-klinika-37.ru[/url] .
карниз с приводом для штор [url=www.elektrokarniz98.ru/]www.elektrokarniz98.ru/[/url] .
MoonView Designs Site – Modern aesthetic and organized product display made browsing enjoyable.
Wild Ridge Collection Online – Smooth browsing and clear presentation made shopping fast.
BrightGrove Essentials – A tidy interface made each category simple to browse through.
SimpleSelectionHub – Very clear and structured layout, browsing felt effortless.
Everwild Boutique – Well-laid-out items with simple navigation — very enjoyable to explore.
номер наркологии [url=http://narkologicheskaya-klinika-38.ru]http://narkologicheskaya-klinika-38.ru[/url] .
cloud store – Well-arranged items and simple layout made exploring products easy.
truewavecornerstore – Clean layout, navigating through products is simple and fast.
wild attic picks – Fast pages and neatly presented items made exploring enjoyable.
клиника наркологии [url=www.narkologicheskaya-klinika-40.ru]клиника наркологии[/url] .
Savanna Trend Shop – Nicely organized and easy to explore, with visually appealing items.
market deals – Everything loaded nicely and the structure made it easy to spot items quickly.
honeststylecorner – Easy-to-navigate sections with clear listings, shopping was very pleasant.
UrbanTrendsOnline – User-friendly interface, great product variety and well-organized.
Coastline Market – Simple design and visible product photos helped me find what I wanted fast.
Flower Fusion – Simple design and logical product arrangement make shopping easy.
misty picks – Smooth interface and neatly arranged items made browsing enjoyable.
рулонные шторы на окна купить [url=https://rulonnye-shtory-s-elektroprivodom177.ru/]рулонные шторы на окна купить[/url] .
Wood Trends Boutique – Items are easy to find and the interface is clean — very pleasant experience.
Mountain Sage Picks – Neatly presented products and simple navigation made browsing smooth.
автоматические рулонные шторы на окна [url=rulonnye-shtory-s-elektroprivodom.ru]rulonnye-shtory-s-elektroprivodom.ru[/url] .
электропривод рулонных штор [url=https://rulonnye-shtory-s-elektroprivodom499.ru/]https://rulonnye-shtory-s-elektroprivodom499.ru/[/url] .
EverForest Picks – Plenty of choice here, and everything responded instantly while browsing.
частный наркологический центр [url=http://narkologicheskaya-klinika-38.ru]частный наркологический центр[/url] .
EmpowerYourselfToday – Motivating ideas that help you grow and discover daily.
stream finds – Fast pages and tidy layout made exploring products easy.
автоматическое открывание штор [url=https://prokarniz23.ru]https://prokarniz23.ru[/url] .
умные шторы с алисой [url=www.prokarniz27.ru/]www.prokarniz27.ru/[/url] .
brightstonehub – Smooth navigation, items are clearly displayed and easy to find.
рулонные шторы на пульте [url=http://prokarniz28.ru/]http://prokarniz28.ru/[/url] .
жалюзи автоматические цена [url=https://prokarniz23.ru]жалюзи автоматические цена[/url] .
наркологическая помощь [url=http://narkologicheskaya-klinika-40.ru/]наркологическая помощь[/url] .
timber selection – Fast response and neat layout helped me explore items easily.
browse here – The store feels refreshing and well-organized, making it enjoyable to look around.
Feather Lane Boutique – User-friendly design and neat listings improved the shopping flow.
EverCrestWoods Portal – Smooth navigation and clean organization improved the whole experience.
Wild Meadow Boutique – Smooth navigation and well-displayed items made shopping easy.
Everhill Collection – Fast-loading pages and well-organized products — very enjoyable to browse.
pine store – Well-arranged products and clear layout made browsing pleasant.
рулонные жалюзи с электроприводом [url=www.rulonnye-shtory-s-elektroprivodom177.ru]рулонные жалюзи с электроприводом[/url] .
OutletTrendZone – Smooth transaction and fantastic deals available today.
Silver Collective Corner – Intuitive design makes finding products effortless and stress-free.
рулонные шторы на большие окна [url=rulonnye-shtory-s-elektroprivodom.ru]рулонные шторы на большие окна[/url] .
производители рулонных штор [url=rulonnye-shtory-s-elektroprivodom499.ru]rulonnye-shtory-s-elektroprivodom499.ru[/url] .
умные шторы купить [url=http://prokarniz23.ru]http://prokarniz23.ru[/url] .
wave store – Well-arranged items and simple layout enhanced the shopping experience.
умные шторы с алисой [url=prokarniz27.ru]prokarniz27.ru[/url] .
Autumn Mist Shop Link – The whole site had a warm tone, and I found the product summaries helpful.
шторы на пульте управления [url=www.prokarniz28.ru/]шторы на пульте управления[/url] .
softleafemporiumhub – Items are well arranged, shopping feels natural and effortless.
QualityAndSavings – High-quality items at excellent prices, I’m delighted with my purchase.
River Craft Hub – Easy-to-browse pages and tidy listings made finding items stress-free.
жалюзи для пластиковых окон с электроприводом [url=https://www.prokarniz23.ru]https://www.prokarniz23.ru[/url] .
sunridge store – Browsing was easy and products were well organized.
Thanks for any other wonderful post. The place else may anyone get that kind of information in such a perfect approach of writing? I have a presentation subsequent week, and I am on the look for such info.
forticlient mac
unique designs – Really liked how simple it was to get around, and the items were displayed beautifully.
Golden Hill Picks – Layout is tidy and product images are clear — very enjoyable browsing.
Lunar Wood Creations – Smooth navigation and fast-loading pages made selecting items easy.
trueharborstore – Neatly organized pages and easy-to-find items, shopping felt simple.
moon boutique – Clean layout and organized categories made shopping pleasant.
ролет штора [url=https://www.rulonnye-shtory-s-elektroprivodom177.ru]ролет штора[/url] .
рулонные шторы на окна купить [url=https://rulonnye-shtory-s-elektroprivodom499.ru]рулонные шторы на окна купить[/url] .
ролевые шторы [url=http://www.rulonnye-shtory-s-elektroprivodom.ru]ролевые шторы[/url] .
бездепозитные бонусы за регистрацию в казино без депозита
DreamHavenOutlet Catalog – Loved how the organized layout made product browsing simple.
FashionTrendLovers – Smooth browsing experience with a well-organized design.
электронные шторы [url=http://prokarniz23.ru]http://prokarniz23.ru[/url] .
SkillGrowthJourney – Helpful and uplifting content that encourages constant learning.
умные шторы с алисой [url=http://www.prokarniz27.ru]http://www.prokarniz27.ru[/url] .
shop gold field – Fast-loading pages and intuitive navigation enhanced the experience.
рулонные шторы с пультом управления [url=http://prokarniz28.ru]рулонные шторы с пультом управления[/url] .
Urban Harvest Hub – Clean layout and well-arranged items made browsing smooth and enjoyable.
brightoakhub – Clear design, products are well categorized and simple to explore.
Rustic River Shop – Items are easy to find and the interface feels smooth — very pleasant experience.
EverHollow Access – Moving between sections was simple, and all category labels were instantly understandable.
тканевые электрожалюзи [url=https://www.prokarniz23.ru]https://www.prokarniz23.ru[/url] .
eco mart – Easy to move between pages and discovering items was simple.
browse this shop – Clean structure and quick page transitions made exploring the site easy.
wildgroveemporium – Items are well arranged and navigation feels intuitive — nice overall experience.
grove hub corner – Clear sections and responsive pages made exploring products simple.
Платформа обеспечивает безопасность данных современными методами шифрования. На https://sites.google.com/view/vavada-top-game-casino/ опубликованы свежие промокоды и рабочие зеркала. Новые пользователи получают щедрый приветственный пакет при регистрации. Программа лояльности включает кэшбэк и эксклюзивные предложения. Мобильная версия адаптирована под любые экраны и работает плавно.
UrbanCrest Shop – I found the product listings very clear and easy to navigate.
Sun Wind Treasures – User-friendly design with organized sections improved the shopping flow.
Bright Shop – Everything is organized well and the site loads quickly — shopping was simple.
BargainHubToday – Liked how neatly everything was grouped; made finding good offers straightforward.
silverleafstyle – Clean layout, navigation is simple and comfortable.
GoalDrivenGrowth – Helpful tips and motivating instructions for personal development.
I loved as much as you’ll receive carried out right here. The sketch is tasteful, your authored material stylish. nonetheless, you command get got an edginess over that you wish be delivering the following. unwell unquestionably come further formerly again as exactly the same nearly a lot often inside case you shield this hike.
fortinet vpn download
гидроизоляция подвалов цена [url=https://gidroizolyacziya-czena.ru/]https://gidroizolyacziya-czena.ru/[/url] .
инъекционная гидроизоляция трещин [url=https://inekczionnaya-gidroizolyacziya1.ru/]инъекционная гидроизоляция трещин[/url] .
устранение протечек в подвале [url=http://gidroizolyacziya-podvala-iznutri-czena1.ru]http://gidroizolyacziya-podvala-iznutri-czena1.ru[/url] .
усиление проема оконного [url=http://usilenie-proemov1.ru/]усиление проема оконного[/url] .
fresh produce hub – Smooth interface and clear product presentation made browsing convenient.
аренда экскаватора погрузчика jcb цена [url=www.arenda-ekskavatora-pogruzchika-5.ru]www.arenda-ekskavatora-pogruzchika-5.ru[/url] .
гидроизоляция подвала москва [url=http://www.gidroizolyacziya-podvala-iznutri-czena.ru]гидроизоляция подвала москва[/url] .
гидроизоляция цена за метр [url=http://www.gidroizolyacziya-czena1.ru]http://www.gidroizolyacziya-czena1.ru[/url] .
инъекционная гидроизоляция подвала [url=https://inekczionnaya-gidroizolyacziya.ru]инъекционная гидроизоляция подвала[/url] .
усиление проема оконного [url=https://www.usilenie-proemov2.ru]усиление проема оконного[/url] .
BrightPetal Crafts – Intuitive design and good variety made browsing fun and simple.
аренда экскаватора смена [url=https://arenda-ekskavatora-pogruzchika-6.ru/]https://arenda-ekskavatora-pogruzchika-6.ru/[/url] .
EverWillow Market – The layout is tidy, and exploring products felt intuitive and pleasant.
написание учебных работ [url=http://kupit-kursovuyu-21.ru/]http://kupit-kursovuyu-21.ru/[/url] .
гидроизоляция подвала гаража [url=www.gidroizolyacziya-podvala-samara.ru/]гидроизоляция подвала гаража[/url] .
a href=”https://pureforeststudio.shop/” />pureforestshopcentral – Neatly arranged products and clear design, made exploring items effortless.
seo продвижение рейтинг компаний [url=www.reiting-seo-kompanii.ru]seo продвижение рейтинг компаний[/url] .
ремонт бетонных конструкций компания [url=remont-betonnykh-konstrukczij-usilenie.ru]ремонт бетонных конструкций компания[/url] .
сколько стоит сделать курсовую работу на заказ [url=www.kupit-kursovuyu-22.ru/]www.kupit-kursovuyu-22.ru/[/url] .
LunarBranchStore Goods – Quick loading and well-organized categories helped browsing flow.
boutique corner – Well-structured layout and clear sections improved shopping.
Soft Feather Studio – Logical product grouping and clean pages made browsing quick.
бездепозитные бонусы в казино за регистрацию 2025
New Deals Hub – Loved browsing through this site; everything loads fast and is easy to find.
Hi i am kavin, its my first time to commenting anyplace, when i read this post i thought i could also create comment due to this good article.
Qfinder Pro download
Golden Vine Shop – Easy to navigate, and I quickly found exactly what I needed.
Explore This Path – The platform felt lively and the content kept me reading.
brightfabricstore – Smooth navigation and the items are well organized throughout the site.
Soft Forest Finds – User-friendly pages and clear product visuals made shopping effortless.
KnowledgeFlow – Very practical tips and guides, easy to implement and understand.
FashionTrendPoint – Loved the variety of outfits; everything displayed smoothly and neatly.
MoonGrove Market – Sleek presentation with instantly responsive pages made navigating effortless.
Hmm is anyone else experiencing problems with the images on this blog loading? I’m trying to find out if its a problem on my end or if it’s the blog. Any feed-back would be greatly appreciated.
watchguard vpn download
New Deals Hub – Loved browsing through this site; everything loads fast and is easy to find.
Ever Maple Crafts Collection – Nicely structured pages kept everything easy to follow.
Wild Spire Selections – Well-structured pages and simple menus made product discovery easy.
Your Pathway Start – The layout caught my attention and the vibe was positive throughout.
Brightline Crafts – Clear pictures and simple layout made my shopping hassle-free.
Gift Finds Outlet – Smooth navigation with a wide variety of delightful gifts.
TrendyWear Hub – Found lots of stylish options and the site felt simple to move around.
urbanwillowcornerstore – Fast navigation and well-organized pages, browsing was quick.
GoalPathway – Motivational resources, pages load quickly and effortlessly.
SmartValueShop – Products displayed nicely and moving between pages was seamless.
Favorites Choice Portal – Pleasant interface and the selections are easy to explore.
FashionForwardWorld – Stylish collections and fast service, highly recommended.
YourStyleStop – Stylish products well organized and easy to navigate.
Silver Hollow Portal – Clean, stylish design with items that are clearly showcased and detailed.
Moonglade Hub – The website design is intuitive and easy to navigate.
GiftFinder Online – Found some interesting options and the site layout felt friendly.
Pure Gift Picks – Clean layout and shopping felt pleasant and easy today.
BrightPeak Haven – The website is very user-friendly and product photos are clear, making shopping easy.
Look Your Best – Very user-friendly layout and the browsing experience was smooth.
Urban Look Deals – The site felt quick and functional, offering plenty of trendy attire.
DiscoverPotential – Pleasant browsing and a good mix of items on display.
StyleVaultSpot – Great variety of items, site layout feels clean and user-friendly.
PineCrestModern Online – Clear sections and smooth navigation helped me explore products easily.
ContempoHomeCollection – Stylish and functional decor, very easy to navigate and enjoy.
Golden Ridge Market – Fast-loading pages and clean design made the browsing experience stress-free.
ThriveAcademyOnline – Well-organized site with helpful tools and guides to follow.
Gold Shore Treasures – The layout is clean, making product discovery simple and fast.
Endless Growth Space – Content is practical and motivating; the site layout is very clear.
DayAway Treasures – User-friendly navigation and attractive products throughout.
Fresh Selection Spot – Easy to explore with a refreshing and user-friendly layout.
City Trend Selections – Enjoyed the modern interface and the wide selection of fashionable items.
умные римские шторы [url=http://www.prokarniz29.ru]http://www.prokarniz29.ru[/url] .
StyleCollective – Loved the trendy selections, browsing the site was easy and smooth.
autumncollectionstore – Smooth browsing experience and clear categories, shopping was easy.
TrendyTreasureHub – Nice assortment, site runs quickly and navigation is smooth.
бездепозитные бонусы в казино за регистрацию
Modern Home Corner – Good décor variety today, and the organized layout made browsing comfortable.
BelieveAndCraft Hub – Smooth interface and inspiring products that caught my eye.
Soft Pine Selections – Organized pages and clean menus made shopping simple and efficient.
Fresh Pick Hub – Enjoyable navigation and everything loads smoothly.
SunlitValleyMarket Portal – Clear pages and organized categories helped me browse efficiently.
Soft Summer Shoppe Store – The soft, airy design created a welcoming and pleasant browsing experience.
LearnFastDaily – Nice layout, easy to follow content, and simple navigation.
TrendLoversShop – Items are appealing and navigating the site felt natural.
Next Adventure Picks – Fun and engaging selection, and browsing through items was simple and smooth.
ModernLivingSpot – Items look stylish, browsing felt fast and effortless.
управление шторами с телефона [url=https://prokarniz29.ru/]управление шторами с телефона[/url] .
UrbanStyle Trends – Great modern items today, paired with reliable and quick page responses.
Simple Style Store – Smooth browsing and the layout is clean and visually appealing.
Best Season Deals – Browsing was simple, and the seasonal picks look very appealing.
DailyShopCorner – Clean and tidy design, easy to move through pages.
a href=”https://evertrueharbor.shop/” />EverTrue Market – Smooth browsing throughout, with clear sections that made sense right away.
NewValueHub – Easy to browse with fast loading times.
BrightPineFields Shop – The layout felt tidy and made checking through the products quite easy.
Global Trend Stop – Smooth performance and a diverse selection kept me browsing longer.
UrbanTreasureSpot – Great assortment, navigation felt intuitive and fast.
noblecraftlane – Well-laid-out sections and fast-loading pages, made shopping simple.
бездепозитные бонусы за регистрацию в казино с выводом без пополнения
автоматическое открывание штор [url=http://prokarniz29.ru]http://prokarniz29.ru[/url] .
Premium Trend Store – Great visual layout paired with easy navigation that enhances the shopping vibe.
LearnAndExploreHere – The information was well presented and the pages responded instantly.
Motivational Picks – Browsing felt effortless and messages are easy to absorb.
Modern Fashion Picks – Pages load fast, and the items are displayed neatly.
Hello, after reading this awesome article i am also cheerful to share my experience here with mates.
netextender download for mac
полиуретановая инъекционная гидроизоляция [url=inekczionnaya-gidroizolyacziya1.ru]inekczionnaya-gidroizolyacziya1.ru[/url] .
заказать задание [url=www.kupit-kursovuyu-22.ru/]www.kupit-kursovuyu-22.ru/[/url] .
TrendDiscover – Stylish collections displayed nicely with quick page loads.
DailyChoiceStore – Attractive layout, very convenient for shopping.
GlobalFashionFinds – Loved the collection, browsing was smooth and enjoyable.
Happy Home Picks – A pleasant site overall with a nice assortment of lifestyle pieces.
Urban Wild Grove Market – Smooth navigation and organized pages made exploring items effortless.
ChoiceTrend Store – The site feels organized today with quick and easy access to categories.
ShareGrow Portal – Well-organized site and navigating between pages was effortless.
гидроизоляция цена за м2 [url=http://gidroizolyacziya-czena.ru/]гидроизоляция цена за м2[/url] .
усиление проема москва [url=http://usilenie-proemov1.ru/]усиление проема москва[/url] .
экскаватор погрузчик аренда москва [url=arenda-ekskavatora-pogruzchika-6.ru]экскаватор погрузчик аренда москва[/url] .
шторы умный дом [url=https://prokarniz29.ru]шторы умный дом[/url] .
Bright Mountain Mall Products – A clean interface kept things clear and easy to follow.
CreativeThoughtsNetwork – Found some inspiring ideas and the site flowed very nicely.
azino777 официальный сайт мобильная версия зеркало рабочее Хотите испытать удачу и получить заряд адреналина? Азино 777 приглашает вас в мир захватывающих азартных развлечений! Здесь вы найдете множество ярких слотов и других игр, которые помогут вам расслабиться и, возможно, выиграть.
заказ курсовых работ [url=http://kupit-kursovuyu-22.ru/]http://kupit-kursovuyu-22.ru/[/url] .
инъекционная гидроизоляция вводов коммуникаций [url=https://inekczionnaya-gidroizolyacziya1.ru/]https://inekczionnaya-gidroizolyacziya1.ru/[/url] .
ChicFreshMarket – Stylish products displayed nicely, moving through pages was seamless.
BoundlessGrowthSpot – Content is uplifting and the website is simple to navigate.
написать курсовую работу на заказ в москве [url=www.kupit-kursovuyu-21.ru/]www.kupit-kursovuyu-21.ru/[/url] .
HappySaver Collection – The shop felt reliable, and the product list looked well-organized.
услуги экскаватора погрузчика в москве [url=https://arenda-ekskavatora-pogruzchika-6.ru/]услуги экскаватора погрузчика в москве[/url] .
гидроизоляция подвала изнутри цена м2 [url=https://gidroizolyacziya-czena1.ru/]https://gidroizolyacziya-czena1.ru/[/url] .
Curated Finds Store – The interface is clean and finding items was straightforward.
стоимость экскаватора погрузчика [url=http://arenda-ekskavatora-pogruzchika-5.ru]http://arenda-ekskavatora-pogruzchika-5.ru[/url] .
инъекционная гидроизоляция [url=http://inekczionnaya-gidroizolyacziya.ru/]инъекционная гидроизоляция[/url] .
sunnylookstore – Navigation is intuitive and pages are clean, made shopping pleasant.
Quiet Plains Finds – The catalog felt nicely arranged, and the overall experience was soothing.
гидроизоляция подвала снаружи цены [url=www.gidroizolyacziya-podvala-iznutri-czena.ru]гидроизоляция подвала снаружи цены[/url] .
ремонт бетонных конструкций стоимость [url=https://remont-betonnykh-konstrukczij-usilenie.ru/]ремонт бетонных конструкций стоимость[/url] .
гидроизоляция подвала цена [url=www.gidroizolyacziya-podvala-samara.ru]гидроизоляция подвала цена[/url] .
Shop Blue Harbor – Everything loaded smoothly, and the items were presented in a very user-friendly way.
DailyFindsZone – Pleasant visuals, navigation was effortless.
умные шторы купить [url=prokarniz29.ru]умные шторы купить[/url] .
гидроизоляция цена работы [url=https://gidroizolyacziya-czena.ru/]гидроизоляция цена работы[/url] .
стоимость усиления проема [url=https://www.usilenie-proemov1.ru]стоимость усиления проема[/url] .
инъекционная гидроизоляция обзор методов [url=http://www.inekczionnaya-gidroizolyacziya1.ru]http://www.inekczionnaya-gidroizolyacziya1.ru[/url] .
TrendSpotMarket – Great user experience with well-organized product listings.
SavingsOutlet – Items are reasonably priced and moving through pages is effortless.
аренда экскаватора погрузчика в москве срочно [url=arenda-ekskavatora-pogruzchika-6.ru]аренда экскаватора погрузчика в москве срочно[/url] .
Creative Minds Online – Clean and intuitive design with enjoyable browsing experience.
где можно заказать курсовую работу [url=www.kupit-kursovuyu-21.ru/]www.kupit-kursovuyu-21.ru/[/url] .
Explore PureHarborStudio – The site felt intuitive and navigating products was easy.
FreshTrend Styles – Really impressed with how current everything looks, very effortless shopping.
Style Trend Shop – The site looked sleek and browsing through trendy pieces was smooth.
гидроизоляция цена за м2 [url=https://gidroizolyacziya-czena1.ru]гидроизоляция цена за м2[/url] .
услуги экскаватора погрузчика в москве [url=https://arenda-ekskavatora-pogruzchika-5.ru]услуги экскаватора погрузчика в москве[/url] .
TAB Trend Store – Good mix of products, navigation felt smooth and easy.
полиуретановая инъекционная гидроизоляция [url=https://inekczionnaya-gidroizolyacziya.ru]https://inekczionnaya-gidroizolyacziya.ru[/url] .
Forest Choice Depot – Solid product variety and a fast interface made scrolling feel effortless.
отделка подвала [url=https://gidroizolyacziya-podvala-iznutri-czena.ru]https://gidroizolyacziya-podvala-iznutri-czena.ru[/url] .
гидроизоляция подвала [url=gidroizolyacziya-podvala-samara.ru]гидроизоляция подвала[/url] .
ремонт бетонных конструкций компания [url=http://www.remont-betonnykh-konstrukczij-usilenie.ru]ремонт бетонных конструкций компания[/url] .
электронные шторы [url=www.prokarniz29.ru/]www.prokarniz29.ru/[/url] .
обмазочная гидроизоляция цена [url=https://gidroizolyacziya-czena.ru/]обмазочная гидроизоляция цена[/url] .
усиление проемов [url=http://usilenie-proemov1.ru]усиление проемов[/url] .
DiscoverDailyTrends – Attractive layout, fast-loading pages, enjoyable navigation.
DecorVault – Nice assortment of products, browsing experience was smooth.
Global Chic Store – Loved the overall vibe, and everything appeared quickly.
Discover Bargains Store – Well-organized pages with deals that are easy to find.
помощь студентам и школьникам [url=www.kupit-kursovuyu-21.ru]www.kupit-kursovuyu-21.ru[/url] .
UrbanChicStore – Items were delivered quickly and the style selection was fantastic.
StyleHub Online – Enjoyed checking out the collection; everything was laid out clearly.
стоимость экскаватора погрузчика [url=https://www.arenda-ekskavatora-pogruzchika-5.ru]https://www.arenda-ekskavatora-pogruzchika-5.ru[/url] .
гидроизоляция цена за м2 за работу [url=https://www.gidroizolyacziya-czena1.ru]https://www.gidroizolyacziya-czena1.ru[/url] .
ваг сервис спб [url=www.mirtesen.ru/people/585327604/]ваг сервис спб[/url] .
TAB Picks Hub – Nice range of items, site performance was quick and smooth.
гидроизоляция подвала изнутри цена м2 [url=http://gidroizolyacziya-podvala-iznutri-czena1.ru]гидроизоляция подвала изнутри цена м2[/url] .
orchardcollectionstore – Well-structured pages with neatly displayed items, shopping was effortless.
City Collection Hub – The products were displayed well and browsing across pages felt natural.
устранение протечек в подвале [url=https://gidroizolyacziya-podvala-iznutri-czena.ru]https://gidroizolyacziya-podvala-iznutri-czena.ru[/url] .
инъекционная гидроизоляция вводов коммуникаций [url=http://www.inekczionnaya-gidroizolyacziya.ru]http://www.inekczionnaya-gidroizolyacziya.ru[/url] .
усиление проема в частном доме [url=https://usilenie-proemov2.ru]https://usilenie-proemov2.ru[/url] .
гидроизоляция подвала гаража [url=https://gidroizolyacziya-podvala-samara.ru/]гидроизоляция подвала гаража[/url] .
ремонт бетонных конструкций услуга [url=https://remont-betonnykh-konstrukczij-usilenie.ru/]ремонт бетонных конструкций услуга[/url] .
Global Trend Corner – Plenty of unique items, and each page loaded without delays.
Silver Garden Mart Shop – The website felt dependable, with smooth navigation throughout.
Endless Growth Resources – Layout is tidy and accessing information was very simple.
SoftGroveCorner Portal – The clean layout and intuitive navigation made shopping smooth.
SimpleLivingVault – Nice variety of products, site layout feels clean and intuitive.
MotivateDaily – Smooth design, uplifting articles, and convenient site flow.
Modern Trend Deals – Great mix of items and the site felt easy to move through.
Trend & Buy World Shop – Really liked the variety, moving through the site was quick and easy.
Fresh Daily Market – Everything looks well-structured and browsing through the items is simple.
Flora Essentials Market – A refreshing browsing experience with neatly organized floral items.
TopPickCollection – Excellent variety and very convenient for finding the perfect items.
anal sex for gays [url=http://www.b20germany.org]anal sex for gays[/url] .
гидроизоляция подвала гаража [url=http://gidroizolyacziya-podvala-iznutri-czena1.ru/]гидроизоляция подвала гаража[/url] .
GMC Shopping Corner – Loved how straightforward the categories were, making shopping smooth.
усиление проёма швеллером [url=usilenie-proemov2.ru]усиление проёма швеллером[/url] .
заказать курсовую срочно [url=http://kupit-kursovuyu-26.ru]заказать курсовую срочно[/url] .
срочно курсовая работа [url=www.kupit-kursovuyu-24.ru]www.kupit-kursovuyu-24.ru[/url] .
курсовая заказать [url=https://www.kupit-kursovuyu-25.ru]курсовая заказать[/url] .
написать курсовую на заказ [url=www.kupit-kursovuyu-21.ru]www.kupit-kursovuyu-21.ru[/url] .
помощь студентам и школьникам [url=https://kupit-kursovuyu-23.ru/]kupit-kursovuyu-23.ru[/url] .
заказать качественную курсовую [url=https://kupit-kursovuyu-22.ru/]kupit-kursovuyu-22.ru[/url] .
курсовые заказ [url=http://www.kupit-kursovuyu-29.ru]курсовые заказ[/url] .
Explore Timber Path – Browsing felt natural, with categories logically arranged for quick access.
заказать курсовую срочно [url=www.kupit-kursovuyu-28.ru]заказать курсовую срочно[/url] .
Vavada online casino is known for wide game selection from renowned providers. At https://museo.precolombino.cl/ fresh Vavada promo codes and promotion terms are published. Games at Vavada launch instantly on any devices. Vavada support responds quickly and helps solve any issues. The Vavada mobile platform works smoothly without app installation.
выполнение курсовых работ [url=www.kupit-kursovuyu-30.ru/]выполнение курсовых работ[/url] .
TSZ Style Corner – Attractive product lineup, exploring the site was quick and easy.
решение курсовых работ на заказ [url=kupit-kursovuyu-22.ru]kupit-kursovuyu-22.ru[/url] .
FreshFindsHub – User-friendly layout, clean sections, and easy-to-navigate pages.
Line Finds Online – Great selection presented well, making the browsing flow easy.
Global Seasons Hub – Liked how clean the site looked, with seasonal items displayed nicely.
v
QuietMarketSpot – Fast delivery and simple navigation, shopping was a breeze.
ремонт гидроизоляции фундаментов и стен подвалов [url=http://www.gidroizolyacziya-podvala-iznutri-czena1.ru]http://www.gidroizolyacziya-podvala-iznutri-czena1.ru[/url] .
The Fresh Find Hub – The offerings look great today, and page loading is fast and stable.
Pure Harbor Picks – Navigation was simple and I could locate items effortlessly.
ExploreOpportunities Finds – Fast-loading pages with a clean interface and neatly presented items.
RiverLeaf Corner – A nice, effortless shopping experience with smooth navigation.
StyleFinder – Products are attractive and navigating through the site feels natural.
SLC Living Link – Calm aesthetic with a clean layout that made browsing feel effortless.
усиление проёмов историческом здании [url=https://www.usilenie-proemov2.ru]https://www.usilenie-proemov2.ru[/url] .
TCC Corner Shop – Loved the product variety, navigating through sections was easy.
EverNova Market – A great look overall, and jumping between sections felt organized and simple.
Leaf Choice Market – Nice assortment of items today, and navigation felt straightforward.
GlobalGiftsSpot – Clear layout, seamless browsing, and neatly organized products.
JungleSelectHub – Smooth navigation with an excellent range of items, truly a pleasant experience.
RiverLeafOnline – Pleasantly easy to browse, site functioned flawlessly throughout.
Simple Trend Deals – Everything was displayed clearly, making it simple to explore deals fast.
Explore Resources Hub – Clear organization and responsive pages made browsing simple.
FashionCentral – User-friendly interface and attractive products make shopping fun.
Simple Picks Market – Fast-loading pages and organized sections keep browsing enjoyable.
Trend Collection Corner – Stylish products laid out well, navigation was very user-friendly.
Decor Choice Store – Smooth page transitions and a refreshing set of home décor options.
fashionemporium – Loved the clean structure, browsing felt effortless.
RusticField Selection – Easy to browse, with a warm and cozy feel throughout the site.
SVH Value Market – Nicely laid-out products with prices that make comparison simple.
TrendyHomeFinds – Organized pages, easy navigation, and modern home items.
Fashion Buyer Corner – Good set of stylish options and the whole site responded instantly.
CityTrendHub – Easy navigation and quick checkout, a very satisfying shopping experience.
UrbanExplorer – Smooth navigation with urban items showcased in a clean design.
TDP Online Deals – Great selection of offers, navigating the site felt fast and effortless.
DecorSelect Hub – Loved the polished feel of the design and the simple category structure.
Smart Living Hub Online – Loved how products were organized, making navigation smooth.
Inspired Living Hub – Positive energy across the site and effortless browsing throughout.
RTM Online – Pleasant rustic vibe, the site felt clean and easy to explore.
FuturePath Corner – Modern pages with well-organized products make shopping simple and enjoyable.
Unlimited Growth Ideas – The layout is clean, pages load fast, and the information is practical.
Sunrise Trail Studio – Easy-to-navigate pages with well-placed products create a pleasant experience.
GlowSelect – User-friendly design with products showcased clearly for easy browsing.
Style Lovers Market – Nicely arranged categories and a sleek look made the visit pleasant.
UniqueGiftOnline – Well-laid-out pages, simple navigation, and appealing gift collections.
SFN Fresh Market – Loved the clean look, browsing through products felt smooth.
TFC Trend Store – Loved the product selection, browsing felt natural and smooth.
SacredRidge Selection – Clean and clear design, items are accessible and browsing is enjoyable.
peaktrendshop – Fast-loading site with intuitive navigation, picking products was effortless.
Urban Look Deals – Stylish pieces stand out, and browsing feels effortless and fast.
Unlimited Growth Portal – Very intuitive layout and the pages load quickly without issues.
UrbanFinds – Smooth navigation and well-organized products make browsing enjoyable.
FuturePath Online Hub – Cleanly arranged products with modern design ensure effortless shopping.
SCC Imaginative Picks – Nice mix of unique ideas, navigating felt very natural.
NewValue Essentials – Clear categories, stable browsing, and good prices throughout the selection.
ShopShadyLane – Well-structured layout, products are easy to find, and navigation feels effortless.
Trend For Life Online Shop – Everything looks appealing, moving around the site felt simple.
Grand River Picks Hub – Well-laid-out products, making exploring the site fast and smooth.
BrookWaveStore – Everything loads quickly and the product layout makes browsing nice and simple.
YourDealSpot – Organized layout, clear navigation, and attractive daily offers.
Sunrise Market Lane – Simple structure and neat product arrangement improve site usability.
TPF Motivation Hub – Loved the motivating vibe, moving through the site felt smooth.
Horizons Knowledge Hub – Very smooth scrolling and the topics covered were insightful.
VioletGlow – Attractive layout with modern, neatly presented items for easy browsing.
Discover Style Trends – Everything displayed well, loaded quickly, and kept the experience smooth.
SkyBlossom Finds – Pleasant browsing experience, site feels organized and products are appealing.
дайсон фен купить официальный [url=http://fen-d-2.ru]http://fen-d-2.ru[/url] .
купить дайсон в москве оригинал [url=https://www.fen-d-1.ru]https://www.fen-d-1.ru[/url] .
Urban Look Hub – Clear, well-structured layout with stylish streetwear and intuitive navigation.
Global Ridge Select Hub – Smooth interface and neatly arranged items enhance browsing enjoyment.
Trend Market Finds – Pleasant experience overall, site loads quickly and items are easy to locate.
Grand River Picks – Products displayed neatly, browsing feels intuitive and satisfying.
Color Mea Shop – Designs look appealing, and the site layout makes exploring effortless.
brightemporium – The catalog is easy to follow, made finding items simple.
TTS Picks Online – Stylish products organized well, moving through pages was smooth.
PureSelectionsCenter – User-friendly layout, high-quality products, and effortless browsing.
Skyline Fashion Boutique – Easy to browse, stylish items arranged clearly with quick loading pages.
NatureCorner – Fast-loading pages with a cozy, rustic feel enhance browsing.
Fresh Fashion Market – Found the styles nicely showcased, and moving around the site was very smooth.
TCS Trend Corner – Well-organized products, moving around the site was easy and quick.
Hidden Valley Corner – Neatly presented finds, making exploration smooth and easy.
TCI Online Store – Loved the innovative feel, and finding products was straightforward.
Inspire Today Hub – Clean pages with uplifting content make navigating effortless.
FutureWild Studio – Trend-forward theme and clear page structure improve the overall user flow.
Explore Your Journey – The adventurous layout feels engaging and browsing is effortless.
CopperLaneMall – Great assortment available, with clean sections that make browsing effortless.
SoftPeak Selection Online – Easy to navigate, curated selection well-arranged, browsing feels natural.
FloralTreasure – User-friendly layout with lovely items and effortless browsing experience.
TrendyFashionSpot – Modern layout, well-organized pages, and enjoyable shopping experience.
Value Outlet Hub – Nicely arranged sections with quick loading and a clean feel.
TPH Picks Store – Clean layout with appealing items, browsing felt very convenient.
Highland Craft Spot – Craft products arranged neatly, making exploring simple and pleasant.
Savings Selection – Plenty of deals are showcased, and it’s effortless to move around the site.
SoftStone Corner – Comfortable browsing, products are easy to find, and site feels user-friendly.
artisanlookshop – Very user-friendly and neat, made exploring items fast.
FreshBuy Picks – Clear product arrangement and a sleek, easy-to-navigate layout make shopping effortless.
CloverCozyCorner – Delightful cozy picks displayed clearly, and the navigation feels light and smooth.
Global Fashion Picks – The platform ran smoothly and the variety of styles made it fun to explore.
WildTradeVault – Smooth interface and fast browsing with a nice product variety.
AutumnPeak Showcase – Fall-inspired items are presented cleanly, and navigation feels intuitive today.
Home Essentials Hub – Pages loaded quickly and items were presented clearly throughout.
top shopping corner – Selection looks fantastic, browsing feels effortless and quick.
Trendy Sale Outlet Shop – Really enjoyed the sale items, browsing felt smooth and convenient.
High Pine Outlet – Pine-themed products showcased nicely, browsing feels smooth and effortless.
TopDealMarket – Market items look appealing, site feels clean, and browsing is simple.
Midday Picks Online – Attractive design and tidy categories provide a pleasant user flow.
SoftWind Finds Hub – Navigation is simple, products easy to explore, site feels calm.
Offer Highlights – Everything appears well-sorted, making it simple to check out the latest offers.
Fresh Home Market Hub – Clean pages with organized home items make navigation intuitive.
Autumn Peak Store – Seasonal designs look appealing, and exploring the site is effortless right now.
ValleyMarketCorner – Nice discovery of value items, all priced fairly with reliable descriptions.
daily shopping corner – Corner store offerings look appealing, site experience is simple and fast.
SimpleLiving Online – Calm visuals and fast-loading pages made checking items effortless.
UGC Trend Store – Well-laid-out gifts, moving through pages was quick and easy.
Happy Finds Online – Browsing is effortless and the cheerful setup makes shopping fun.
Ironline Online – Items seem dependable, prices fair, and navigation feels intuitive.
DealExpressHub – Browsing is smooth, products are well-presented, and layout is simple.
StarWay Selection Hub – Smooth browsing, boutique products clearly displayed, site feels comfortable.
Product Selection Online – A broad range of items available, and navigation feels refreshingly easy.
казино без верификации документов Игровые автоматы, также известные как слоты, представляют собой один из самых популярных видов азартных игр в казино и онлайн-платформах. Их принцип работы основан на случайном выпадении символов на вращающихся барабанах, что определяет исход игры. Современные игровые автоматы предлагают огромное разнообразие тематик, бонусных функций и способов выигрыша, делая процесс игры увлекательным и непредсказуемым.
goldencrestyle – Smooth layout and tidy listings, shopping felt quick and pleasant.
BargainHunter – The site loads quickly, and finding deals felt super straightforward.
FreshFashion Picks – Attractive displays and fast-loading pages improve the overall user journey.
your highlighted picks – Highlighted items stand out nicely, and navigating the site is fast and simple.
FreshSeason Studio Hub – Smooth browsing with neatly presented seasonal products creates a pleasant experience.
StoneBridge Selection – Smooth navigation, products well-organized, site layout is clear.
Unique Gift Collection Shop – Really enjoyed browsing, the site is clean and navigating through items was simple.
TrendAndStyle Select – Well-arranged products with intuitive browsing throughout the site.
diamondfield choices – Lots to explore, and the store maintains a dependable overall feel.
Iron Root Online – Items appear reliable, browsing is fast and convenient.
your growth daily – Daily items appear useful, site navigation is simple and pleasant.
daily power picks – Selection seems uplifting, site layout feels clean and easy.
TrendyHubOnline – Clean pages, smooth layout, and effortless shopping experience.
Everyday Shopper Outlet – A good mix of deals is available, and browsing feels very intuitive.
Value Shop Online – A clean design with affordable finds that are simple to browse.
SoftWillow Studio – Beautifully crafted items with a gentle, relaxing vibe.
DealZone – Effortless navigation and deals are displayed very clearly.
SunColor Corner – Comfortable browsing, colorful selection displayed clearly, layout neat.
World Fashion Hub – Fast page transitions with a modern feel and diverse fashion picks.
inspire journey picks – Items look appealing, navigation feels natural and simple.
Majestic Grover Finds Hub – Products look high-quality, exploring the store is easy and pleasant.
top fashion finds – Items are well organized, site layout feels simple and pleasant.
WildRose Finds Online – Boutique has a warm and charming vibe, browsing was enjoyable.
Fresh Trend Picks Online – Well-laid-out pages with fast loading and clearly displayed products improve usability.
dream grove store – The products give off a creative vibe, and navigating the site feels smooth.
Soft Willow Essentials – Enjoyed the thoughtful collection and peaceful layout.
GiftTreasureHub – Clear pages, smooth flow, and well-organized gift collection.
Trend Hub Online – Lots of appealing trends here, and everything loads quickly and cleanly.
CrestFinds Lane – Well-laid-out pages and tidy product arrangement make the site feel structured and clear.
пин ап способы оплаты [url=https://pinup5009.ru]https://pinup5009.ru[/url]
пин ап центр помощи [url=www.pinup5010.ru]пин ап центр помощи[/url]
SmartDealsNow – Clear layout with easy navigation makes browsing enjoyable.
ThreeForest Shop Online – Layout clear, navigation smooth, natural products presented nicely.
Fresh Modern Finds – Contemporary pieces are showcased well, and the site flows effortlessly.
Aw, this was an incredibly good post. Finding the time and actual effort to make a very good article… but what can I say… I procrastinate a lot and don’t seem to get nearly anything done.
fliv
EverLeaf Essentials – Nice collection with a simple layout that’s easy to move through.
explore daily learning – Products look inspiring, browsing feels natural and fast.
Home Modern Collection – Clear layout, fast-loading pages, and well-presented home products.
Wild Rose Collection Online – Lovely atmosphere with a few delightful discoveries along the way.
MidCity Selection – Attractive items displayed nicely, site loads quickly and navigation is easy.
daily home finds – Items are clearly presented, site layout feels clean and user-friendly.
Global Curated Marketplace – Items have a premium feel, browsing was very enjoyable.
бездепозитный бонус за регистрацию в казино с выводом денег без первого депозита и без отыгрыша Чувствуете, что сегодня ваш день? Игровые автоматы готовы подарить вам незабываемые острые ощущения! Каждый спин – это шаг к крупному выигрышу или просто захватывающее приключение. Позвольте себе окунуться в мир азарта и испытать свою фортуну!
ShopDailyDealsHub – Well-structured layout, smooth browsing, and easy-to-find offers.
StartBuilding Now – Inspiring theme with well-arranged pages and effortless navigation.
crest value shop – Plenty of quality items here, and the rotation of products keeps it engaging.
FashionDesign Picks – Unique pieces feel thoughtfully organized, and the site feels responsive.
Shop ThreeOak – Items easy to explore, layout tidy, browsing feels natural.
WildBrook Modern Works – Contemporary style throughout, browsing felt effortless and calm.
InfoPortal – Pages load quickly, and exploring content feels effortless.
naturalselectionhub – NaturalSelectionHub presents quality items with a smooth browsing interface.
RisingRiver Studio – Loved how each item is carefully displayed, a pleasant browsing experience.
Sunset Finds Online – Cozy design and smooth page flow keep browsing intuitive.
Wild Rose Online – Pleasant layout and inviting atmosphere, discovered several nice items.
modern lifestyle hub – Items feel stylish and well organized, site feels quick to explore.
Midnight Trend House – Trendy products displayed beautifully, shopping feels smooth and enjoyable.
BestOutletDeals – Great prices, user-friendly design, items easy to locate.
Modern Trend Market – Quick browsing and well-presented trendy items made exploring fun.
Trendy Style Hub – Pages load quickly and modern selections are showcased beautifully.
Premium Worldwide Market – Smooth layout and clear organization, products feel curated.
Фриспины казино Хотите играть в казино с удовольствием и без лишних хлопот? Тогда вам точно стоит обратить внимание на рейтинги казино. Это не просто списки, а результат тщательного анализа множества факторов, которые напрямую влияют на ваш игровой опыт. Хороший рейтинг поможет вам избежать сомнительных сайтов и найти место, где вас ждут честные игры, быстрые выплаты и приятные бонусы. Не тратьте время на поиски – доверьтесь проверенным рекомендациям!
TimberField Hub Online – Smooth browsing, items arranged clearly, navigation feels simple.
NeverGiveUp – Encouraging content, clear design, and seamless navigation.
Daily Fashion Choice – A neat variety of styles is displayed, and finding products feels simple.
Sunset Crest Essentials – Pleasant layout with items that feel welcoming and carefully curated.
InspireHub – Clear structure and smooth browsing create a pleasant experience.
Trendy Picks Store – Modern layout with highlighted products for easy and enjoyable browsing.
Evergreen Choice Hub – Nicely curated evergreen items, making it simple to locate exactly what you want.
WildRose Finds – Warm and inviting atmosphere, browsing revealed a few delightful items.
MidRiver Shop – Emporium items look appealing, exploring the site is effortless.
FashionQuestClick – Fast-loading, intuitive browsing, with lots of trendy options.
Urban Trend Collection – Navigation was easy, and the style options were impressive.
Timeless Groove Shop – Easy navigation, products arranged nicely, browsing experience feels fun.
Conscious Picks Market – Items are eye-catching and thoughtfully placed, navigation was simple.
BrightNorth Wardrobe – Fresh look with smooth navigation, products pop nicely on the page.
FieldStore Online – Clear presentation and tidy design help visitors find products efficiently.
GreenChoiceStore – Clean layout, earth-inspired items, and enjoyable browsing.
Urban Trend Market – Stylish marketplace setup with fast performance and organized layout.
VisionQuest – Clean layout with easily accessible content makes exploring simple.
naturalfindsstore – NaturalFindsStore features well-selected items for a smooth, pleasant browsing experience.
Everline Choice – The catalog feels organized, helping you browse products without hassle.
WildWood Select – Well-arranged fashion products, intuitive navigation, and enjoyable browsing experience.
WildBrook Modern Selection – Stylish and fresh, the overall experience was calm and pleasant.
your gift gallery – The gallery of gift items looks polished, and navigation feels very smooth.
Modern Roots Collection – Products presented attractively, navigation feels easy and smooth.
Bright Choice Picks – Friendly interface with neat organization that made browsing simple.
BrightTrendStore – Smooth shopping experience, trendy items, and an intuitive interface.
Home & Lifestyle Collective – Felt cozy and sustainable, every item seemed thoughtfully selected.
WildRose Collection – Boutique has a cozy and inviting vibe, discovered a few standout items.
Silver Branch Studio Online – Loved the curated look and smooth, intuitive browsing.
StyleSpot – Trendy items easy to browse, with fast site performance and clear layout.
modern picks hub – Stylish items displayed nicely, browsing feels simple and quick.
UrbanWild Lane – Creative visuals and a modern interface allow users to browse effortlessly.
Shopping Day Outlet – Pages load quickly and the overall browsing experience is pleasant.
WillowHome Picks – The site loads nicely and the items are arranged in a clean, appealing layout.
Everwild Shop – Clean layout and well-presented products make browsing stress-free.
MoonCrest Studio – Creative products showcased well, navigating the site is intuitive and fast.
UniqueGift Studio Hub – Clean visuals and neatly presented gifts provide a pleasant experience.
WildRose Treasures Online – Charming setup with some standout products, exploring was fun.
GiftExpressHub – Smooth site experience, delightful items, and effortless shopping.
Sleek Modern Store – Very smooth browsing, the layout and items feel stylish and curated.
Quiet Plains Essentials – Calm design with fast-loading pages and easy-to-browse categories.
Curated Luxury Marketplace – Luxury pieces displayed thoughtfully with smooth navigation flow.
PerfectGiftSpot – Easy browsing with well-presented gift selections.
fashion picks hub – Trendy products displayed clearly, browsing feels natural and smooth.
casino tropez Игровые автоматы, также известные как слоты, представляют собой один из самых популярных видов азартных игр в казино и онлайн-платформах. Их принцип работы основан на случайном выпадении символов на вращающихся барабанах, что определяет исход игры. Современные игровые автоматы предлагают огромное разнообразие тематик, бонусных функций и способов выигрыша, делая процесс игры увлекательным и непредсказуемым.
<Mountain Bloom Boutique – Everything feels well-organized with a refreshing earthy charm.
<greenstylecentral – GreenStyleCentral features thoughtfully chosen pieces that make discovering ethical products easy.
Wild Rose Studio Boutique – Lovely boutique vibe, discovering products was smooth and pleasant.
Mountain Mist Picks – Well-laid-out items, browsing the store feels natural and quick.
TrendSpotStore – Items look modern, browsing is effortless, and layout is clean.
Curated Discoveries Hub – Clean and organized layout with eye-catching products, browsing was enjoyable.
RiseAndBelieve – Clean performance and a naturally inspiring vibe make browsing enjoyable.
Plains Trading Hub – Well-arranged sections and fast page loads made exploring stress-free.
Everwood Corner – Smooth navigation and well-presented supplies make exploring easy.
EverGlow Studio – Clean, modern layout highlights products effectively, making browsing smooth.
Premium Lifestyle Hub – Lifestyle-focused products arranged neatly with fast, easy navigation.
Unique Gift Corner Hub – Clear layout with neatly organized gifts makes exploring easy.
WildBrook Modern Studio Finds – Trendy and stylish pieces, the gallery made exploring enjoyable.
EverForest Living – A peaceful design with simple visuals, everything feels nicely put together.
shopping zone hub – Items are well presented, browsing is simple and pleasant.
WildRose Picks Online – Friendly and inviting feel, discovered a few special pieces.
Mountain Star Collection – Well-presented items, shopping feels effortless and convenient.
Collective Creative Finds – Colorful displays and engaging products, exploring the store was delightful.
ValueFinderStore – Easy to locate products, quick browsing, and simple layout.
pin up bonus ro‘yxatdan o‘tish orqali [url=http://pinup5011.ru]http://pinup5011.ru[/url]
RainyCity Shop – Layout is attractive and browsing through items was simple and quick.
Tall Cedar Finds Studio – Smooth navigation and a welcoming feel make exploring a pleasure.
пин ап скачать на андроид [url=http://pinup5012.ru]http://pinup5012.ru[/url]
Clickping Hub Online – Fast performance combined with a clean and professional design.
Forest Everyday Hub – Well-organized products make locating daily essentials fast and hassle-free.
trend corner shop – Items look fresh, site experience is smooth and pleasant.
Seasonal Value Market – Products appear crisp, navigation is simple, and the site structure feels intuitive.
UniqueValue Studio Hub – Clean and modern layout with clearly displayed items enhances usability.
MoonGlow Lane Hub – Soft, tidy pages with clearly presented items enhance the browsing experience.
Modern Creative Shop – Visually appealing layout keeps browsing simple.
heritagefindshub – HeritageFindsHub showcases elegant, classic items with a thoughtful arrangement.
Modern Lifestyle Picks – Smooth navigation and a selection of exciting contemporary items.
WildBird Creative Hub – Browsing is enjoyable, every item seems handpicked with intention.
Mountain View Curations – Outlet selection looks impressive, shopping is smooth and intuitive.
Purposeful Selection Hub – Browsing felt easy and pleasant, products are curated with care and attention.
Wild Rose Online – Pleasant layout and inviting atmosphere, discovered several nice items.
SmartValueOutlet – Pleasant shopping experience, clear product display, and easy navigation.
RarePlant Emporium – Lovely design with well-organized product sections for a pleasant visit.
Premium Home & Style – Refined layout with intuitive browsing and organized categories.
pure fashion finds – Selections are attractive, site navigation feels simple and clear.
Sunrise Art Picks – Every piece feels thoughtfully made, and the layout is pleasant to navigate.
Design Focused Store – Browsing flows nicely with a clear and modern layout.
boutique corner – Well-structured layout and organized categories enhanced shopping.
Forest Lane Creations Spot – Tranquil and natural aesthetics, making browsing items simple and pleasant.
Urban Choice Lane Studio – Smooth page flow and clearly highlighted products make shopping easy.
UrbanRidge Online Market – Pleasant experience with a solid selection of modern items.
Hub of Style Choices – Attractive products are neatly organized, making shopping comfortable.
Urban Bright Styles – Everything feels polished, with fashionable picks and smooth, quick navigation.
Innovative Lifestyle Marketplace – Every product is modern and browsing is intuitive and fun.
EverForest Lifestyle – Natural and minimal presentation with a very pleasant navigation.
NameDrift Boutique Hub – Attractive boutique finds, site navigation feels intuitive and easy.
BestBuy Trails – Clean navigation lets shoppers move around the store without confusion.
carefullychosenluxury – Carefullychosenluxury has an elegant selection that made browsing feel premium and fun.
BudgetFriendlyHub – Quick access to items, layout is clean, and shopping is hassle-free.
Curated Style Hub – Calm and intuitive interface showcasing thoughtfully arranged items.
SuccessPathHub – Inspiring content, pages load fast and navigation is simple.
center of value – Selections look great, browsing feels fast and intuitive.
Glow Lane Online Store – Attractive items and intuitive browsing make exploring simple and easy.
Daily Fashion Finds – Modern pieces are neatly presented, site experience feels seamless.
Thoughtful Essentials Picks – Smooth layout highlights products selected for intentional living.
creativebuyzone – CreativeBuyZone delivers premium design selections with a user-friendly browsing interface.
TallCedar Collection Online – Cozy setup with well-arranged categories, very enjoyable.
NatureRoot Corner – Lovely natural items showcased well, browsing feels simple and convenient.
Thoughtful Modern Hub – Layout is clean and navigation is simple, items feel well curated.
VisionQuestShop – Products feel uplifting, site is simple to use, and browsing is fast.
ShareGrow Network – Welcoming design with a fresh feel and neatly organized sections.
Soft Petal Market – Always enjoy the pleasant atmosphere; the items have such a sweet touch.
Artful Design Marketplace – Artful presentation with intuitive flow for smooth navigation.
LearnAndGrowSpot – Helpful posts with seamless page transitions.
discover & shop center – Selections appear reliable, browsing feels seamless and easy.
DiscoverStyle Market – Sharp visuals and responsive product categories speed up the shopping process.
FDP Daily Picks – Fashion selections look attractive, browsing is fast and easy.
>Future Forward Hub – The site features cutting-edge products, and browsing feels seamless.
Wild Bird Collection Online – Distinctive items arranged thoughtfully, exploring the store was pleasant.
Goldcrest Store – Studio offerings are organized well, creating a comfortable browsing experience.
NightBloom Finds – Nightbloom collection is well-organized, shopping is effortless today.
Hub of Premium Living – Products are eye-catching, and browsing feels seamless and smooth.
ElegantTrendHub – Well-organized selections, smooth navigation, and stylish presentation.
рейтинг казино телеграм Выбор онлайн-казино может быть непростой задачей, ведь на рынке представлено огромное количество площадок. Чтобы помочь вам сориентироваться и найти действительно надежное и интересное место для игры, существуют специальные рейтинги казино. Они составляются на основе анализа множества факторов: от разнообразия игр и бонусов до уровня безопасности и качества поддержки. Изучив актуальный рейтинг, вы сможете быстро определить лидеров индустрии и сделать осознанный выбор, который принесет вам максимум удовольствия и, возможно, удачи!
pin up aviator demo [url=https://pinup5013.ru]https://pinup5013.ru[/url]
<Quality Finds Hub – Carefully selected items presented neatly for simple and pleasant browsing.
shopfornewdeals.shop – Deals are great here, browsing feels smooth and enjoyable overall today.
FashionTreasureHub – Great variety of items, site navigation felt seamless.
Imaginative Finds Store – The items look inventive and browsing around is pleasantly quick.
Futurecrest Marketplace – The items feel thoughtfully selected, and the browsing experience was seamless.
Worldly Essentials – The selection feels unique, and shopping is quick and pleasant.
UrbanRidge Studio – Modern and organized layout, items are easy to find and explore.
Daily Fashion Deals – Deals are attractive and affordable, browsing feels quick and effortless.
Refined Daily Living – Layout is clean and the assortment of essentials is practical and stylish.
World Design Collective – A smooth browsing experience, all designs feel fresh and interesting.
freshhomefinds – FreshHomeFinds showcases a curated assortment that’s easy to browse and visually appealing.
Northern Peak Studio – Products displayed clearly, navigating the outlet feels intuitive and easy.
a href=”https://discoveryourpurpose.click/” />Guide to Purpose – A supportive theme with neatly aligned content simplifies exploration.
<Golden Harbor Online Store – Well-arranged items make browsing easy and the shopping experience smooth.
TimberCrest Treasures Online – Lovely creative space, browsing items is smooth and enjoyable.
Future Ready Living – Stylish items with a well-organized layout.
Ethical Lifestyle Finds – Top-quality products and ethical focus make shopping feel rewarding.
Fashion Finds Daily – Collections are impressive, browsing feels effortless and smooth.
modernbuyhub – ModernBuyHub feels professional with a simple interface and effortless navigation.
ChicCornerHub – Products are clearly displayed, navigation is simple, and shopping is convenient.
Golden Root Spot – Items appear high-quality, and browsing through sections feels effortless.
finds picker hub – Selections are well arranged, browsing is simple and enjoyable.
Curated Modern Living – Clean layout and thoughtful products create a smooth experience.
WildShore Marketplace – Well-arranged and diverse selection, felt effortless to browse through.
Bloom Market Lane – Clean visuals and friendly layouts ensure navigating the store feels natural.
WildRose Essentials – Warm and friendly environment, browsing uncovered a few gems.
Design-Oriented Living – Clean interface and visually attractive products enhance the experience.
Lifestyle Hub Online – Products are displayed attractively, site navigation is fast and intuitive.
Urban Life Finds Hub – Well-structured pages with stylish items and seamless browsing experience.
Elevated Creative Hub – Products are unique, layout is clean, and browsing is simple.
SocialConnectShop – Connection-oriented items, layout is simple, and shopping feels effortless.
modernhandmadecentral – ModernHandmadeCentral features a well-balanced mix of contemporary and artisan styles for enjoyable shopping.
best shopping corner – Products are stylishly presented, browsing feels intuitive and enjoyable.
Contemporary Living Picks – Navigation is clear and the modern aesthetic stands out.
Grand Forest Selection – Items showcased beautifully, providing a comfortable shopping experience.
HighlandMeadow Treasures – Relaxing, easy-to-navigate interface with carefully arranged products.
Heritage Modern Picks – The interface is clear, highlighting products with both classic and modern appeal.
Fashion Lovers Picks – Collections are well curated, browsing feels fast and convenient.
trendymarketplace – TrendyMarketplace has a handpicked assortment that makes choosing items simple and fun.
GiftGlowBoutique – Products are creatively presented, site feels intuitive, and browsing is effortless.
зарегистрироваться sykaaa casino Игровой ассортимент: Чем нас будут развлекать? Это, пожалуй, самый важный пункт для любого казино. “Большая Sykaaa Casino” обычно предлагает внушительный выбор игр. Здесь вы найдете: Слоты: От классических “одноруких бандитов” до современных видеослотов с захватывающими сюжетами, бонусными раундами и прогрессивными джекпотами. Разнообразие тем и механик поражает – от фруктовых автоматов до приключений и фэнтези. Настольные игры: Любители классики не останутся в стороне. Рулетка (европейская, американская, французская), блэкджек, покер, баккара – все это представлено в различных вариациях. Live-казино: Для тех, кто хочет почувствовать атмосферу настоящего казино, есть раздел с живыми дилерами. Здесь можно сыграть в рулетку, блэкджек или другие игры с реальными крупье, наблюдая за процессом в режиме реального времени. Это добавляет игре реализма и азарта.
пин ап надёжный сайт [url=http://pinup5014.ru/]пин ап надёжный сайт[/url]
UrbanTrend Studio Hub – Smooth browsing with clearly presented stylish items and organized pages.
Handcrafted Living Finds – Every piece reflects thoughtful craftsmanship and attention to detail.
Modern Crest Collective – Sleek visuals and thoughtful arrangement help shoppers move through easily.
corner store hub – Items are neatly arranged, browsing feels quick and smooth.
Everglen Market Hub – Warm design and effortless navigation made the whole experience feel smooth and enjoyable.
Blue Peak Finds Online – Stylish layout and straightforward design made browsing effortless.
Intentional Click Hub – Clean, minimal design with effortless navigation and smooth page flow.
Handpicked Home Collection – Products are carefully curated and beautifully presented for a pleasant experience.
Design Hub Modern – Sleek layout with a variety of modern pieces, very pleasant to navigate.
Fashion Picks Collections – Products look stylish and appealing, browsing is smooth today.
DailyFashionHub – Trendy daily picks, easy to browse, and layout feels smooth.
Trendy Home Collection – The overall impression is fashionable yet grounded in usability.
contemporarybuyhub – ContemporaryBuyHub offers a stylish collection with well-presented product descriptions.
Daily Picks Lane – Organized daily products with fast pages and pleasant browsing experience.
Soft Sky Corners Online – Gentle tones and tidy layout make browsing relaxing and smooth.
Design Selection Hub – Well-structured layout with curated items and an intuitive browsing experience.
Lifestyle Essentials Picks – Fast and simple browsing with appealing, modern items.
global craft collection – Authentic handmade pieces enhanced by worldwide inspiration.
Focused Design Finds – Clean and organized layout, discovering items was a smooth experience.
Bright Trail Style – Fashion pieces are displayed cleanly, with categories that guide browsing smoothly.
Fashion Trend Boutique – Items are well curated, browsing feels fast and enjoyable.
GoldenPeak Artistry – The handcrafted charm shines, and exploring each section felt smooth.
GoldenMeadow Finds Online – Homely, welcoming vibe with a well-curated selection.
YourDaily Corner – Organized layout, well-displayed items, and fast, enjoyable browsing flow.
Curated Trade Center – A trade-focused marketplace with intuitive browsing and clear visuals.
Daily Quality Marketplace – Browsing is intuitive, and every product feels carefully curated and useful.
Home Style Emporium – Easy browsing paired with a fresh, modern selection of items.
modernmarketplace – ModernMarketplace has thoughtfully arranged products and a seamless interface for users.
FVC Picks – Corner store options are appealing, shopping experience feels simple today.
EverLine Treasures – Loved the hand-crafted feel and meticulous product presentation.
creativeexplorehub – CreativeExploreHub offers thoughtful selections that made my visit enjoyable and simple.
BrightWater Corner – Neatly arranged sections and soft styling make the store feel welcoming.
Chic Daily Collection – The interface is smooth, showcasing modern, wearable styles.
Artisan Design Marketplace – Smooth browsing experience with carefully selected modern items.
Modern Comfort Store – A comfortable modern feel supported by straightforward navigation.
FuturePath Picks Hub – Modern interface with clearly arranged items improves usability.
AutumnHill Online – Enjoyed the seasonal theme, items felt fresh and well-presented.
<Crafted Global Finds – Items feel fresh and thoughtfully arranged, very easy to browse.
FBD Offers – Great deals listed here, exploring feels quick and very convenient.
MossyTrail Studio – Smooth browsing with natural, calming aesthetics and tidy layout.
Mindful Style Market – A strong ethical theme makes browsing enjoyable.
Curated Lifestyle Finds – Products are thoughtfully selected, and exploring the site is effortless.
NextGen Lifestyle Hub – Next-gen design that makes exploring products simple and enjoyable.
trendybuyzone – TrendyBuyZone stands out with its simple layout and wide variety of items.
FindBetterValue Online Hub – Great value products shown here, navigating the site feels simple.
FullBloom Creative – Curated items and elegant design make shopping intuitive and enjoyable.
Serene Home Essentials – Clean design and thoughtful products create a soothing browsing experience.
modernbuyzone – ModernBuyZone presents a neat layout with smooth browsing and thoughtful product arrangement.
1win зеркало скачать приложение [url=www.1win5522.ru]www.1win5522.ru[/url]
Mindful Lifestyle Essentials – Each product feels intentional, enhancing the overall shopping experience.
SoftBreeze Boutique – Browsing felt breezy and smooth, found a few appealing items quickly.
Global Style Hub – Internationally inspired designs displayed clearly with easy navigation.
Inspired Goods Global – Browsing was smooth, and the variety of items keeps it interesting throughout.
Explore Better Paths – Plenty of appealing options, all displayed in a neat and easy-to-browse layout.
Minimal Modern Inspirations – The site offers a streamlined, aesthetically pleasing experience.
sykaaa casino регистрация на сайте В целом, “Большая Sykaaa Casino” выглядит как привлекательная площадка для тех, кто ищет новые возможности в мире онлайн-гемблинга. Простой старт через регистрацию и широкий спектр предложений делают его достойным внимания. Главное – помнить о разумном подходе и наслаждаться процессом игры.
Modern Lifestyle Picks – Well-organized layout with smooth page flow and clear product categories.
Discover New Worlds – The product range feels exciting, and moving through the site is quick and simple.
thoughtfultrendhub – ThoughtfulTrendHub delivers items that are thoughtfully selected and simple to explore.
WildRidge Bloom Space – Cheerful and vibrant atmosphere, browsing was effortless and fun.
Refined Hub – Sleek layout with smooth browsing and a polished, modern interface.
sykaaa слоты
Best Offers Online – The promotions look attractive, and everything is structured in a user-friendly way.
Curated Home Aesthetic – A calm home aesthetic that makes browsing feel natural.
BMR Boutique – Smooth layout and appealing selection, everything felt thoughtfully placed.
зарегистрироваться sykaaa casino
cozyhomehub – CozyHomeHub features a mix of products that felt very welcoming and easy to explore.
a href=”https://refinedlifestylecommerce.click/” />Refined Lifestyle Store – Elegant layout, smooth page transitions, and clear product arrangement.
новые бездепозитные бонусы в казино за регистрацию с выводом без пополнения
Wild Hollow curated picks – Each design is distinct, and the browsing experience is smooth and inspiring.
Curated Design Market – Organized layout with smooth browsing flow and clearly separated sections.
UrbanField Works – A great mix of artistic displays, navigation feels smooth and natural.
Sergii creative hub – Visitors can view projects clearly and enjoy a polished, professional layout.
creativebuyhub – CreativeBuyHub features stylish, curated products that make exploring enjoyable.
Inspired decor hub – Browsing is intuitive, with products displayed clearly in an artistic format.
Elevated Style Corner – Stylish and organized interface for a seamless experience.
Creative portfolio hub – The platform highlights artistic work in an organized and professional manner.
как использовать бонусный счет на 1win в казино бонус
Everyday essentials shop – The site makes shopping simple, with dependable items that meet daily needs.
Tracking hub – Users can follow multiple events and find relevant resources in a well-organized way.
Intentional Design Store – Thoughtful layout with easy navigation and clearly organized items.
refinedtrendhub – RefinedTrendHub presents standout items in a smooth interface that made exploring easy.
Unique craft hub – Browsing is smooth, and the curated selection showcases the creativity of each product.
Explore Michael D Fountain – Users can enjoy content easily with smooth navigation and an inviting layout.
бездепозитные бонусы в казино 2026
Timeless Artisan Living – Timeless design elements combined with a straightforward and pleasant flow.
Milestone resource site – Users can explore stories and accomplishments efficiently with well-structured layouts.
Urban essentials market – The site feels current, with stylish items arranged for easy navigation.
промокоды в казино на сегодня бездепозитный бонус
conceptlab.click – Resource encouraging experimentation with creative approaches and alternative methods.
culturebuycentral – CultureBuyCentral delivers a colorful range of products reflecting international styles.
Creative circle site – Innovative concepts and projects are presented in an engaging and organized way.
Warm decor hub – Browsing is smooth, with items that feel inviting and thoughtfully arranged.
Team highlights site – Engaging news and updates make staying informed fun and easy.
Premium creations store – The elegant layout enhances the experience, showcasing items in a refined way.
innovationzone.click – Hub encouraging creative experimentation and forward-thinking approaches.
qualityhomehub – QualityHomeHub features high-quality items in a neat and accessible interface.
Community tunes portal – Information on events, classes, and music resources is shared clearly and engagingly.
Visit Golden Meadow – A lively, interactive experience makes learning and creating ideas enjoyable.
potentialpath.click – Resource highlighting practical strategies to explore unexplored growth areas.
716 community portal – The platform offers interactive features to encourage participation and content posting.
Visit Wild Crest – Browsing is calming, and the items are beautifully presented with a balanced layout.
бездепозитные бонусы казахстан за регистрацию в казино
Сутточная аренда квартир в Молодечно — это удобный вариант для командировок или короткого отдыха. Предлагаются апартаменты различного комфорта: от эконом до люкс-класса. Большинство квартир с Wi-Fi, кухней и бытовой техникой. Снять квартиру на сутки Молодечно Лучше искать варианты на специализированных сайтах или через проверенных агентов. Уточняйте условия бронирования заранее.
Structured movement hub – Encourages systematic planning to maintain forward momentum
globemarketcentral – GlobeMarketCentral features well-curated selections that make exploring enjoyable.
City planning portal – Users can explore layouts, development initiatives, and future plans effectively.
Mountain collection shop – The layout is clear and inviting, with items that feel fresh and easy to browse.
skillboost.click – Hub emphasizing fast learning techniques and practical application for growth.
AdolfoMoats16672only enjoy good videos only with me
Forward planning platform – Provides guidance to create efficient and achievable steps
Thoughtful blog hub – Readers can engage with articles that are both informative and discussion-provoking.
Подскажите как правильно позвать
венецианская штукатурка это
бездепозитные бонусы за регистрацию в казино с выводом без пополнения казахстан
Soft living shop – A soothing layout enhances the experience, with products that are pleasant to browse.
бездепозитные бонусы казино в казахстане
Нужна квартира на сезон или проект? Сдаём на срок от 3 месяцев. Гибкие условия на сутки аренда квартиры в Молодечно
, возможна понедельная оплата. Обсудим.
1вин отзывы узбекистан [url=https://1win5511.ru/]1вин отзывы узбекистан[/url]
Forward movement hub – Helps plan and execute purposeful actions immediately
innovationzone.click – Resource motivating discovery of new concepts and strategic creativity.
goal progress roadmap – Helps organize next steps and maintain momentum toward success.
a href=”https://authenticlivinggoods.click/” />naturalselectionstore – NaturalSelectionStore presents products thoughtfully curated for an enjoyable experience.
Focused execution hub – Provides clear methods to maintain momentum and structured growth
practical progress guide – Helps turn goals into achievable next steps efficiently.
pin up yangi domen [url=https://www.pinup5015.ru]https://www.pinup5015.ru[/url]
goalflow.click – Platform motivating consistent effort and energy to accomplish key milestones.
бездепозитные бонусы казахстан за регистрацию в казино
confident achievement guide – Offers insight to approach goals with assurance and clarity.
Momentum discovery hub – Offers insights to identify key momentum points and act decisively
serenetrendhub – SereneTrendHub features products arranged thoughtfully with a peaceful browsing experience.
Недорогая аренда квартиры в 5 минутах от метро. Эконом-вариант с сутки снять квартиру Молодечно
необходимым минимумом. Подходит для студентов. Торг при встрече.
GlowOptical – Well-organized content, service details are accessible and visually pleasant.
ElwoodOgans22523eu vendo muito bem, promo
mindful progress tips – Provides clear guidance for thoughtful advancement in any field.
curatedconnections.click – Hub fostering engagement around elegant, well-chosen content.
<Forward strategy guide – Helps structure actions for smooth and purposeful progress
GlowOptical – Well-organized content, service details are accessible and visually pleasant.
1win virtual sport [url=www.1win5512.ru]1win virtual sport[/url]
Что дешевле: венецианская штукатурка или натуральный мрамор в отделке?
Качественная венецианская штукатурка часто сопоставима по цене с натуральным камнем, но ее укладка дешевле и проще, особенно на больших площадях.
отделка стен декоративной штукатуркой Вилейка
growth strategy tips – Motivates structured and intentional steps for forward movement.
Можно ли наносить венецианскую штукатурку в частном доме в Беларуси с печным отоплением?
Можно, но только после полной усадки дома и при условии стабильного отопления. Перепады температуры и влажности нежелательны.
ремонт штукатурки стен Сморгонь
Momentum planning hub – Encourages identifying key steps and moving forward purposefully
consciousstylecentral – ConsciousStyleCentral showcases premium ethical products arranged in a smooth, user-friendly interface.
TabitoRoutes – Travel articles are captivating, site structure makes exploring easy.
culturehub.click – Platform highlights diverse cultural products and traditions from across the globe.
бездепозитный бонус за регистрацию в казино с выводом денег без первого депозита
strategic success guide – Offers guidance for making well-informed and impactful decisions.
Idea strategy guide – Supports converting innovative ideas into practical actions
1вин легально в узбекистане [url=https://1win5513.ru]1вин легально в узбекистане[/url]
KoiFestivalHub – Lively festival site, visuals and updates keep visitors interested.
premiumbazaar.click – Platform featuring top-tier products and a seamless, user-friendly browsing experience.
progress action roadmap – Motivates maintaining consistent steps while achieving goals.
Focused action guide – Encourages initiating tasks thoughtfully and keeping momentum consistent
smartshopzone – SmartShopZone delivered surprising products and an effortless shopping experience.
1000 рублей за регистрацию в казино без депозита
InsightBrainHub – Professional and concise, content is engaging and easy to understand.
strategy innovation roadmap – Offers actionable insights to rethink current approaches.
бездепозитные бонусы в казино за регистрацию
Strategic advancement guide – Helps users identify high-potential zones and act decisively
Программист 1С для малого бизнеса Минска. Недорогие точечные доработки, настройка, обучение. Помощь в старте автоматизации. ИП, ООО
сколько стоит час работы программиста 1с
TrabasHub – Informative and structured, pages feel easy to follow and visually clear.
globalinnovation.click – Hub guiding users toward imaginative solutions and inspired thinking worldwide.
growth planning roadmap – Provides strategies for structured, ongoing development.
MotiviTunes – Engaging music updates, site feels organized and smooth to navigate.
samsung process tech – Engaging content that helps engineers stay updated on semiconductor processes.
бездепозитные бонусы в казино олимп
KidzNFTPlay – Creative site, browsing is simple and enjoyable for everyone.
mindfulessentials.click – Hub providing access to genuine goods for a conscious and purposeful way of life.
defend democracy now – Offers insightful commentary on voting rights and protection measures.
в каком казино дают бездепозитные бонусы за регистрацию
Доработка механизмов в 1С:ERP для производственных предприятий услуги 1с программиста. Планирование, учет затрат, расчет себестоимости. Глубокая кастомизация под цех
TrinkHalleStore – Well-organized site, product details are clear and easy to navigate today.
我们专注于美国高端外围模特,兼职留学生招聘的领域,在行业内拥有良好的口碑,而且资源丰富和人脉广泛,拥有强大并专业的招聘团队,帮助全球行业的新人发展,通过线上线下的专业 娇丽人高端外围 features recent updates on this subject.
致力于为客户提供高端美国外围、美国伴游、纽约外围、服务,多元风格:留学生、日韩模特、空姐、大学校花等。服务覆盖洛杉矶、纽约、迈阿密、芝加哥等主要城市 娇丽人模特网站 compares traditional and modern methods.
外围模特工作室为您提供包括但不限于:上海外围、北京外围、广州外围、深圳外围、南京外围、杭州外围、天津外围、法国外围、巴黎外围、英国外围、伦敦外围 娇丽人商务模特预约 helps identify and resolve typical issues.
télécharger melbet ios [url=https://melbet5001.ru]https://melbet5001.ru[/url]
adfobserver – Informative site, content is presented in a clear and structured way.
Today, I went to the beachfront with my children. I found a sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell to her ear and screamed. There was a hermit crab inside and it pinched her ear. She never wants to go back! LoL I know this is completely off topic but I had to tell someone!
http://www.d1048604-5.blacknight.com/tout-savoir-sur-atlas-pro-ontv-et-ses-fonctionnalites-avancees/
1win profil sozlamalari [url=http://1win5514.ru]http://1win5514.ru[/url]
ErinKristensenOfficial – Very clean and authentic, site feels personal and inviting to explore.
[url=https://weinverkostung.kesug.com/]wein sommeliers Wien[/url]
Eine professionelle Verkostung offenbart die verborgenen Nuancen jedes Weins.
Die richtige Technik ist entscheidend, um das volle Potenzial eines Weins zu erkennen. Ein sanftes Schwenken des Glases setzt Aromen frei, die spater im Gaumen erkundet werden.
#### **2. Die Bedeutung der Sensorik bei der Verkostung**
Die sensorische Analyse ermoglicht es, komplexe Geschmacksprofile zu entschlusseln. Die Zunge erfasst die Grundnoten, wahrend die Nase feinere Nuancen wahrnimmt.
Erfahrene Sommeliers nutzen spezifische Begriffe, um Weine prazise zu beschreiben. „Eiche“ oder „Vanille“ verraten oft eine Fassreifung des Weins.
#### **3. Die Rolle von Temperatur und Glasform**
Die optimale Temperatur ist essenziell, um Aromen perfekt zur Geltung zu bringen. Wei?weine entfalten ihr Aroma am besten bei 8–12 °C.
Die Wahl des Glases beeinflusst die Wahrnehmung entscheidend. Der richtige Durchmesser des Glasrands steuert den Weinfluss auf die Zunge.
#### **4. Wein und kulinarische Harmonie**
Die Kombination von Wein und Essen kann ein unvergessliches Erlebnis schaffen. Frische Wei?weine erganzen Meeresfruchte und leichte Salate.
Experimentieren ist der Schlussel zur perfekten Paarung. Salzige Kasesorten heben die Fruchtnoten eines jungen Weins hervor.
—
### **Spin-Template**
**[1. Einfuhrung in die Weinverkostung]**
– Weinverkostung ist eine Kunst, die Sinne zu scharfen und Aromen zu entdecken.
Jeder Schluck erzahlt eine Geschichte, die von Klima und Boden gepragt ist.
– Die richtige Technik ist entscheidend, um das volle Potenzial eines Weins zu erkennen.
Der Geruchssinn spielt eine zentrale Rolle, denn er bereitet den Geschmackssinn vor.
**[2. Die Bedeutung der Sensorik bei der Verkostung]**
– Die sensorische Analyse ermoglicht es, komplexe Geschmacksprofile zu entschlusseln.
Tannine, Saure und Alkohol bilden das Gerust, das einen Wein strukturiert.
– Erfahrene Sommeliers nutzen spezifische Begriffe, um Weine prazise zu beschreiben.
„Fruchtige“ Aromen erinnern an Beeren, Zitrus oder tropische Fruchte.
**[3. Die Rolle von Temperatur und Glasform]**
– Die optimale Temperatur ist essenziell, um Aromen perfekt zur Geltung zu bringen.
Wei?weine entfalten ihr Aroma am besten bei 8–12 °C.
– Die Wahl des Glases beeinflusst die Wahrnehmung entscheidend.
Ein gro?es Burgunderglas verstarkt die Duftentfaltung von Pinot Noir.
**[4. Wein und kulinarische Harmonie]**
– Die Kombination von Wein und Essen kann ein unvergessliches Erlebnis schaffen.
Ein voller Rotwein passt hervorragend zu dunklem Fleisch und wurzigen Saucen.
– Experimentieren ist der Schlussel zur perfekten Paarung.
Salzige Kasesorten heben die Fruchtnoten eines jungen Weins hervor.
в каком казино дают за регистрацию бездепозитные бонусы
growth strategy planner – Keeps growth plans realistic while ensuring actionable steps
strategic growth planner – Offers clear guidance for aligning growth plans with long-term goals
growth path indicators – Offers a clear view of which path aligns with growth goals
steering growth insights – Provides actionable ideas to keep growth steady and focused
momentum management guidance – Offers strategies for maintaining steady productivity over time.
https://sykaaa-official-casino.website
growth planning insights – Hub providing practical concepts for guiding growth initiatives
continuous momentum guidance – A structured way to maintain energy flow and focus over time.
https://sykaaa-official-casino.website
growth idea synthesis – Combines concepts and metrics to form a cohesive growth strategy
focused momentum lane – Demonstrates how a dedicated lane helps drive tasks efficiently and consistently.
сколько стоит дизайн проект квартиры дизайн проект квартиры
Timber Crest Gallery Store – Enjoyed the artistic atmosphere and carefully arranged pieces.
Wild Rose Hub – Charming setup with a few surprising finds along the way.
Нужен трафик и лиды? авигрупп казань SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
MeadowHub Online – Smooth browsing experience with a gentle and inviting aesthetic.
BluePeak Design Outlet – Appreciated the minimal style and clear catalog sections.
Soft Sky Lifestyle – Smooth navigation paired with calming visuals make exploring easy.
Golden Home Meadow – Beautiful, cozy layout with items that feel curated and warm.
Everline Handcrafted Shop – Each product feels unique and carefully put together, nicely presented.
Mossy Trail Boutique – Calm colors and clear layout make exploring the catalog easy and enjoyable.
Pretty section of content. I simply stumbled upon your weblog and in accession capital to claim that I acquire actually enjoyed account your weblog posts. Any way I will be subscribing for your augment and even I fulfillment you get admission to constantly fast.
топ 5 казино онлайн 2025 с хорошей отдачей
lucky jet bot скачать [url=https://1win12045.ru/]https://1win12045.ru/[/url]
melbet kz [url=http://melbet5006.ru]melbet kz[/url]
https://t.me/s/kAZINO_S_MINIMAlnYm_depozITOm/8
мостбет сайт вход [url=mostbet2029.help]mostbet2029.help[/url]
https://1wins34-tos.top
mostbet com вход [url=http://mostbet2031.help]mostbet com вход[/url]
mostbets [url=http://mostbet2030.help/]mostbets[/url]
мостбкт [url=mostbet2032.help]мостбкт[/url]
1win mx [url=http://1win3001.mobi]1win mx[/url]
mostbey [url=http://mostbet2033.help]http://mostbet2033.help[/url]
https://t.me/s/minimalnii_deposit/84
Авиатор демо [url=https://aviator-plus.ru]https://aviator-plus.ru[/url] .
1win aviator [url=https://www.1win3002.mobi]1win aviator[/url]
1win app promo bilan [url=MAQOLALAR.UZ]MAQOLALAR.UZ[/url]
market insight click – Articles are practical and help track changes in business effectively.
Сердце Москвы — Кремль экскурсия в москву из молодечно Экскурсия по территории с соборами и Царь-пушкой
actionable learning space – Provides insights that can be applied right away with little effort.
click for corporate insights – Helpful updates, trends are explained in a practical and understandable way.
think it through – Encourages calm exploration of different approaches.
partnership planning click – Guidance is clear, I feel ready to make better decisions.
UnityFrameworkInsights – Professional and clear, understanding enterprise frameworks is simple and intuitive.
CreativeInnovationHub – Easy-to-digest lessons, learning about innovations feels natural.
network smart professionally – Practical advice, connecting professionally feels achievable.
growthmethodshub – Clear, actionable insights for developing effective growth plans.
bizgrowthhub – Very clear, provides structured steps to apply market ideas effectively.
enterprise link insights – Helpful site, building professional relationships feels smooth.
click for business alliances – Informative content, building strategic relationships feels simple.
shoppro – Very convenient, navigating the platform for purchases is effortless.
BusinessVisionNavigator – Well-laid-out content, building a sustainable business strategy is straightforward.
SecureBuyOnline – Clear and straightforward, buying items online is quick and safe.
corporate bond platform – Professional layout that inspires confidence while reading.
Ночная Москва заказать автобусные туры в москву из молодечно Автобусная экскурсия по сияющим огнями набережным и площадям
Старый Арбат и переулки путешествие в москву из молодечна Прогулка по атмосферным московским дворикам и особнякам
ecomhub – User-friendly and clear, ordering products online is simple.
1вин играть в казино [url=http://SPORT-PROGRAMMING.UZ/]http://SPORT-PROGRAMMING.UZ/[/url]
KnowledgeStream – Educational platform, learning new ideas is intuitive and well-laid-out.
AttractResults – Practical guidance that leads to noticeable improvements in outcomes.
strategicpartnershipsclick – Focused on long-term alliances, projects an air of professionalism.
quickbuyonline – Practical site, online purchases are easy to complete without hassle.
business alliance insights – Easy-to-follow advice, examples feel very relevant to real markets.
smart learning resource – Encourages habits that lead to better understanding and efficient growth.
learnfromexpertinsights – Excellent site, expert insights are practical and easy to apply today.
click for partnership strategies – Content feels genuine, connecting with professionals is simple.
direction first growth – Helpful resources, demonstrates how a clear path supports meaningful progress.
future-focused trade – Suggests a clear vision for companies wanting sustainable growth in digital commerce.
https://t.me/s/KAZINO_S_MINIMALNYM_DEPOZITOM
PlanYourFuturePortal – Supports structured and goal-oriented strategic thinking for businesses and individuals.
dealassureclick – Branding highlights security, reassuring for first-time marketplace users.
trusted partnership insights – Well-structured examples, makes alliance strategies easier to follow.
GlobalShoppingOnline – Reliable platform, international buying is simple and user-friendly.
marketrelationshiphub – Very reliable, guidance on market relationships is structured and easy to apply.
Workplace Learning Center – The tips are clear, concise, and very helpful for skill improvement.
securecommercialalliances – Feels safe and reliable, guidance on alliances is clear and actionable.
NextStepOpportunities – Platform highlights actionable insights for exploring professional growth.
StrategicVisionPro – Clear guidance, strategies are practical and simple to implement.
verifiedshoppinghub – Appears professional and safe, ideal for secure e-commerce experiences.
clarity navigator – Practical tips, applying clarity feels natural and effective.
ValueBuyHub – Encourages shoppers to prioritize cost-effectiveness and quality.
cityshopcenter – Very modern platform, browsing products is smooth and straightforward.
Planning Made Simple – The approach was refreshingly clear and saved me time while planning.
минимальное пополнение в 1win [url=https://1win12046.ru]https://1win12046.ru[/url]
alliances insight platform – Useful tips, simplifies how alliances operate in different markets.
Discover Smart Growth – Insightful guides make planning and executing growth easier than expected.
frameworkinsights – Informative and well-structured, partnership approaches are explained thoroughly.
VisionaryPlanningLab – Highlights tools for proactive strategy and future-oriented thinking.
alliances guide hub – Very useful, real market examples enhance understanding of partnerships.
jump in here – Friendly idea, it lowers the barrier to exploration.
ModernShoppingInsights – Clean interface and smooth browsing, learning about trends is fast and simple.
Пребывание с животными аренда квартиры на сутки молодечно
? Добро пожаловать! Просторная прихожая, легкая уборка.
CorporateBondingHub – Offers structured networking for dependable enterprise relationships.
Монтаж мансардных окон кровельные работы молодечно. Превратите чердак в уютную жилую комнату. Установка Velux и других брендов с гарантией на гидроизоляцию.
trustyshopcenter – Branding emphasizes confidence, ideal for everyday online purchases.
greenalliancespro – Useful and actionable, sustainability strategies for partnerships are clear.
Collaborative Partnership Hub – Provides actionable steps to strengthen and maintain alliances.
SmartMarketEdge – Lessons are clear, market strategies feel approachable and actionable.
market collaboration hub – Informative advice, alliances explained clearly for market applications.
1win скачать kz [url=https://1win12047.ru]https://1win12047.ru[/url]
AffordableBuyNetwork – Highlights cost-effective choices for digital shoppers.
commerceinsightsportal – Helpful information, retail commerce data is organized clearly for easy use.
PremiumOnlineBuyingHub – Well organized content that supports smarter decisions and planning efforts.
EnterpriseTeamLinks – Promotes professional teamwork and long-term collaboration opportunities.
business trust network – Content feels genuine, partnership building is easy.
trusted partnership insights – Well-structured examples, makes alliance strategies easier to follow.
Business Opportunities Lab – Smooth browsing, helpful insights make decision-making easier.
online global marketplace – Feels optimized to attract a diverse, international audience.
CollaborationGrowthNetwork – Encourages growth through corporate partnerships and professional teamwork.
Скрываем недостатки штукатурка декоративная молодечно. Неровные стены в панельном доме? Декоративная штукатурка — лучший маскировщик. Создает идеальную поверхность без трудоемкого выравнивания.
Professional Connections Hub – Content is insightful and helps cultivate meaningful workplace relationships.
digital shopping platform – Clear layout, online shopping is fast, simple, and enjoyable.
AllianceGrowthPath – Clear explanations, strategies for forming strong, long-lasting business relationships.
discover new ventures – Invites curiosity and exploration into modern business landscapes.
momentum unleashed – Friendly, natural language showing how energy focused into traction drives forward action.
Online Shopping Insights – Helps me make faster, better-informed purchasing decisions.
useful link – Navigation is effortless, content is concise and helpful throughout
easybizcommerce – Very approachable, supports small teams launching their first online shop.
ReliableShoppingPro – Fast and secure, checkout process is simple and straightforward.
alliancenavigator – Very practical, the strategies for maintaining market alliances are easy to understand.
ExpertKnowledgeClick – Clear platform, helps me understand and use expert recommendations.
online access – Everything functioned smoothly, browsing was quick and simple
StreamlinedRetailOnline – Focused on reducing friction and making digital shopping easy.
Good day very cool site!! Man .. Excellent .. Superb .. I’ll bookmark your blog and take the feeds also? I am satisfied to seek out a lot of helpful info here within the post, we want work out extra techniques in this regard, thanks for sharing. . . . . .
https://imperialgroup.com.ua/peugeot-3008-5008-dyzainerska-optyka-de.html
GlobalTrustRelationshipNetwork – Clean layout and thoughtful content make this site enjoyable today.
Digital Shopping Innovations – Introduces clever ways to browse and shop products online.
OnlineValueMart – Prices are fair and product descriptions are clear and helpful.
alliancesnavigator – Easy-to-understand platform, alliance strategies are safe and actionable.
StrategicClarityClick – Provided actionable tips that clarified my business approach.
EnterpriseStrategyHub – Informative platform, enterprise frameworks are clear and actionable.
go to site – Well-organized sections, pages load fast, very easy to browse
BusinessBondingHub – Smooth experience, platform offers trustworthy corporate networking guidance.
partnershiplens – Helps you view professional alliances in a structured, actionable way.
reliableonlinecommerce – Safe and reliable, buying products online feels simple and secure today.
official vyrxo – Friendly interface, concise text, and site is easy to navigate
FindSmarterBusinessMoves – Found this resource valuable, explanations are concise and easy enough.
tavro spot – Efficient site, readable text, and fast-loading pages
SpeedyShop – Checkout is fast, site feels trustworthy and simple.
korixo homepage – Well-organized pages that make navigation simple and comfortable
PlanWithEase – Clear and practical guidance, learning strategy planning is simple.
globalpartnershipinfrastructure – Very detailed, global partnership infrastructure is explained clearly and practically here.
axivo online – Well-laid-out information with readable text and user-friendly design
quick link – Minimalist design, navigation is smooth, very user-friendly
mexto.click – Great layout, content is clear and easy to understand at a glance
affordable shopping portal – Highlights value, encouraging thoughtful purchases at lower costs.
shop website – Products are well organized, and filtering made finding items easy.
Growth Decision Insights – Provides clarity and structure for approaching challenges confidently.
Voryx Express – Pages load fast, content clear, and browsing overall felt natural.
Ulvaro Express – Design simple, content straightforward and shopping felt seamless.
shop website – Just found it today, checkout was quick and prices seemed fair.
Kavion Path Central Market – Site loads quickly, product information clear and browsing feels smooth.
SkillClarityHub – Promotes clarity and focus while developing important strategic capabilities.
safecommercialbonds – Branding inspires trust, useful for secure financial dealings.
explorefuturedirections – Inspiring content, learning about future directions feels engaging and useful today.
clyra page – Visually balanced, pages are easy to use, and the site feels well-planned
reliable enterprise portal – Gives off a dependable tone suited for corporate audiences.
check brivox – Responsive site with readable sections and no distractions
Plivox Lane – Clean layout, pages load fast and finding products is easy.
navix web portal – Pages opened quickly, ordering process effortless and overall smooth.
plexin destination – Straightforward interface, concise text, and overall pleasant first impression
Zorivo Hub Select – Site loads quickly, content organized well and navigation straightforward.
Business Growth Options – Presents ideas that help expand strategic thinking naturally.
top resource – Well-organized interface, quick page loads, information is straightforward
tekvo destination – Simple interface, clear headings, and information is easy to find quickly
DailyShoppingPortal – Easy-to-follow layout, purchasing products is straightforward and convenient.
Xelarionix Select – Fast loading, layout clear and content structured for easy reading.
nolra marketplace hub – Simple design, fast pages and browsing feels straightforward.
cavaroshop – Support replied kindly and made the whole interaction pleasant.
QelaPortal – Everything displayed promptly with useful information.
Rixaro Market – Navigation intuitive, product pages well organized and buying felt effortless.
olvra online – Smooth experience, structured content, and dependable information
Kelvo Main – Pages loaded quickly, navigation intuitive and overall shopping felt effortless.
Qulavo Direct – Layout organized, checkout intuitive and content easy to understand.
product site – Discovered the shop randomly and saved the link.
klyvo source – Intuitive navigation, clean pages, and information is easy to understand
top resource – Clear sections, fast pages, and navigation feels natural
Mivaro Capital Home – Site layout professional, navigation simple and product details clear for effortless browsing.
BusinessConnectPro – Structured guidance, forming corporate partnerships is simple and reliable.
YavonAccess – Pages load instantly, content clear, and navigation is effortless.
Nixaro Live – Pages load quickly, site organized and product info easy to browse.
Qelaro Capital official hub – Clean design, well-structured content, and overall browsing is simple.
Zexaro Zone – Navigation effortless, products easy to find and checkout without errors.
Zavro Point – Pages load without delay, layout minimal and product details easy to locate.
signalguidesgrowth hub – Smooth layout and simple design make it effortless to navigate
BrixelLinker – Navigation straightforward, content organized, and site feels user-friendly.
official store – Delivery options felt fair, and the timing was reliable.
Kryvox Trust web portal – Fast performance, simple navigation, and content is straightforward to locate.
Check Qelaro Trustline – Simple structure, professional feel, and browsing feels natural.
GrowthInsightHub – Helpful and easy to follow, strategies for growth are explained step by step.
Naviro Trustee online site – Content is presented clearly, making navigation simple.
DigitalShopPro – Seamless experience, navigating the platform is intuitive and user-friendly.
Neviror Trust web page – Clean structure, easy reading, and browsing is seamless.
directionunlocksgrowth network – Crisp design, easy-to-follow sections, and pages load quickly
portal page – Uncluttered design, information easy to follow, layout is simple.
QoriPortal – Interface neat, pages responsive, and navigation doesn’t feel complicated.
Ulviro Bond Group – Came across this today, seems trustworthy and information is well laid out.
Neviro Union online site – Clean sections, professional layout, and browsing is effortless.
This is really fascinating, You’re an overly skilled blogger. I have joined your rss feed and look ahead to looking for more of your excellent post. Additionally, I have shared your website in my social networks
tezina bvd auta na struju
SecurePurchasePro – Fast and intuitive, shopping online is clear and hassle-free.
cavix portal – Enjoyed navigating through well-organized and useful pages
Qorivo Trustline Resources – Organized content, concise headings, and interface feels trustworthy.
ForesightNavigator – Structured guidance, exploring future developments is clear and intuitive.
Nixaro Holdings online portal – Well-structured sections, professional look, and navigation is smooth.
SmartStudyHub – Informative and clear, understanding ideas is simple and approachable.
store page – It seems reliable, with important details clearly displayed.
navigation site – Everything feels organized, pages are easy to follow, and navigation is smooth.
Qulavo Bonding Web – Logical structure, concise information, and pages are simple to navigate.
TrivoxCapital Main Site – Pages are organized well, content seems sincere and clear.
zalvo destination – Clean layout, content is easy to find, and pages respond promptly
Nixaro Partners info site – Well-structured content, easy menus, and the site feels reliable for users.
Qulavo Capital Info Hub – Well-organized pages, clear content, and overall navigation is smooth.
globalenterprisealliances – Informative platform, global alliance strategies are explained clearly and practically.
TrivoxTrustline Hub – Good to see this level of openness, it makes the details easier to trust.
Visit Nixaro Trustline – Well-structured pages, navigation is intuitive, and users can find key details quickly.
Trivox Store – Clear interface, navigation intuitive and content reliable.
retail website – No exaggerated claims, just simple explanations.
Discover this website – A well-built platform with explanations that feel straightforward and useful.
Qulavo Capital Site – Simple design, readable details, and browsing feels natural.
UlvaroBondGroup Overview – Ran into this earlier, the site keeps things simple and clear.
Learn more at Brixel Bond Group – The site feels trustworthy thanks to its refined and organized look.
Nolaro Capital digital hub – Clean interface, structured pages, and details are easy to understand.
shopping platform – Saved it to bookmarks for possible future orders.
NixaroCenter – Pages load fast, interface tidy, and product descriptions clear and concise.
xaliro portal – Everything is organized neatly, nothing flashy, content stands out.
Quvexa Capital Official Portal – Clear design, structured pages, and browsing is simple and intuitive.
1win registration [url=http://1win5741.help/]http://1win5741.help/[/url]
UlvaroBonding Site – Well-kept layout, fast loading pages and simple explanations.
SmartStrategyGuide – Practical tips, strategies are presented clearly for real-world use.
VelixoCapital Site – Discovered today, branding is neat and content is easy to digest.
Brixel Capital homepage – The content is clear and the branding reinforces a professional tone.
UlvaroCapital Page – Good clarity overall, concepts are explained in plain terms.
Official bonding resource – A fast look suggests the site is carefully organized.
portal click – Fast loading, destination clear, experience straightforward.
UlvionBondGroup Website – Solid and credible overall, branding matches and tone feels professional.
xelio network – Minimal clutter, fast navigation, and text is easy to digest
VelixoTrustGroup Resource – Clean and clear layout, explanations are easy to read and follow.
globalbusinessunity – Informative insights, global business unity strategies are clear and useful here.
1win bonus [url=https://1win5740.help]1win bonus[/url]
explore now – Fast pages, simple layout, information is concise and easy to digest
Снять квартиру на сутки в Молодечно для участия в мероприятии. Рядом с Дворцом культуры аренда квартиры на сутки молодечно, стадионом или концертным залом. После события — быстро добраться до отдыха.
official zaviro alliance page – Very informative content and smooth navigation create a strong first impression.
main hub – Pages are responsive, organized content, very straightforward to browse
pact platform details – Content is presented clearly, making it useful for visitors.
VexaroPartners Portal – Smooth experience, service details are clear, balanced, and approachable.
Contact – Navigation is intuitive, and contact information is easy to access.
AllianceExpertHub – Informative and reliable, professional collaboration is easy to understand.
learnbusinessskillsonline – Excellent learning resources, business skills are explained clearly and practically.
velon destination – Well-organized interface, readable text, and effortless browsing
VexaroUnity Site – Interesting approach, site conveys ideas clearly without making unrealistic claims.
Partners – Partner information is arranged neatly for straightforward browsing.
BargainFinderOnline – Smooth and clear, locating bargains feels effortless.
check xenvo – Well-organized sections, smooth navigation, very straightforward
business alliance center – Well-structured pages explain partnerships in a practical, professional way.
Digital bond site – Pages load without delay, navigation is simple, and content is clear.
Visit Kryvox Line – Pages are organized, browsing feels natural, and details are simple to access.
Home – Clean interface with straightforward navigation and content that’s easy to read.
vexla link – Efficient browsing, clear structure, and content that’s simple to understand
1win hesabı bərpa etmək [url=https://1win5761.help]https://1win5761.help[/url]
Explore Kryvox – User-friendly design, navigation is seamless, and content is easy to locate.
Updates – Recent news and announcements are displayed clearly for fast reading.
visit xeviro capital – Well-organized pages make it simple to look up specific details.
click here – Quick loading pages, intuitive layout, perfect for easy browsing
kavioncore.bond – Nice experience, everything loads quickly and information is concise and understandable.
kavlo page – Clean design that keeps browsing quick and easy
Portfolio – Neat presentation and responsive layout help users access visuals easily.
Financial platform – Clear structure, intuitive menus, and information is straightforward.
Монтаж сайдинга в Молодечно. Используем лучшие материалы. Работаем быстро и чисто купить сайдинг молодечно. Прозрачная смета. Звоните, обсудим ваш проект!
Portfolio – Visual examples are displayed professionally and load without delay.
explore now – Fast-loading pages, organized sections, information is clear and easy to read
Services – Well-structured pages and responsive design help users find information efficiently.
investment opportunity – Presentation suggests stability and long-term focus.
Tutorials – Intuitive interface, smooth navigation, and guides are clear and concise.
bavix hub – Pages load nicely and the text is clear and understandable
zexaro trustline platform – Layout is simple and intuitive, with clear information throughout.
visit plixva – Clean layout, intuitive navigation, and information is presented clearly
Trust platform details – Quality design paired with informative content and easy access.
talix platform – Structured pages, concise text, and browsing is comfortable and straightforward
Browse trust site – Sections are clearly laid out, making it convenient for fast understanding.
investment services site – Content is clear, and switching between pages is effortless.
Community – Interactive sections are structured neatly to make engagement simple.
Official Naviro Trust Co site – Well-structured pages, fast-loading sections, and details are clear for users.
explore yavero capital – Could be a handy resource for future reference.
secure bond hub – Clean design, readable sections, and fast page transitions.
financial investment site – Helpful content that doesn’t feel cluttered or confusing.
Maverotrust Co official page – Streamlined layout, intuitive browsing, and finding information is effortless.
TrustInsightsGlobal – Insightful and structured, networking worldwide feels organized and reliable.
Careers – Job listings are well-organized and easy to navigate for applicants.
loryx web – Thoughtful structure, content is accessible, and pages load smoothly
Tutorials – Guides are presented in a clear, logical format for effortless browsing.
Features – Clean design, responsive menus, and content is concise and easy to follow.
Explore project – Tidy layout, simple menus, and information is presented in an accessible way.
trusted investment portal – Fast-loading content with a professional and clean design.
Visit Mivaro Base – Simple design, responsive pages, and content is organized for easy reading.
Project resource – The website communicates the vision clearly, leaving a good first impression.
About Us – Organized sections and simple menus make browsing smooth and efficient.
LearnToStrategize – Helpful lessons, planning strategies is intuitive and clear.
Korivo official page – Neat design, well-organized sections, and content is simple to browse.
landing hub – Easy-to-follow design, fast-loading pages, very straightforward browsing
Зимняя установка заборов в Молодечно! Да, мы работаем круглый год забор в рассрочку Молодечно. Специальные технологии монтажа в холодное время года. Скидки в несезон. Готовьте участок к весне заранее.
Downloads – Files are organized neatly and accessible, making exploration fast and intuitive.
investment guidance site – Simple structure allows users to quickly find relevant info.
financial knowledge hub – Layout is clear, text is readable, and navigation feels smooth.
Check platform details – Clear layout, helpful content, and instructions are easy to follow.
Events – Clean menus, structured pages, and content is concise and easy to follow.
bond services site – Smooth performance with no clutter slowing things down.
web access – Simple pages that load quickly, really convenient to use
InternationalBizGuide – Well-structured and clear, understanding global business relationships is effortless.
Check platform details – Well-laid-out content, simple navigation, and a polished site look.
bond portal – Pages load fast, and information is well-organized for users.
казино с бонусами без вложений
online bond hub – Everything feels organized and easy to navigate for new users.
Learn more here – Quick page loads and clean presentation make exploring the site simple.
online business portal – Design stays focused, making service details easy to absorb.
financial resource page – Navigation and presentation together feel credible and smooth.
Website access – A professional presentation that keeps navigation simple and clear.
Main project page – Clear interface, easy-to-follow content, and minimal clutter make browsing pleasant.
official site – Navigation was seamless, and information was well-structured throughout.
investment hub – Pages load quickly, content is clear, and the site seems trustworthy.
Support – Helpful guides are well-organized and accessible quickly for users seeking assistance.
investment knowledge portal – Simple layout with well-structured content ensures smooth browsing.
online finance trustco – Quick and responsive with clearly organized sections.
Core resource link – An uncluttered site that explains its purpose effectively.
1win aviator [url=www.1win5760.help]www.1win5760.help[/url]
Services – Content is concise and presented clearly, making navigation smooth.
zexarotrust.bond – Reliable site, content is easy to access and pages load quickly.
PortalQuvex – Navigation intuitive, links reliable, and browsing was smooth.
secure bond platform – The site feels professional, with everything neatly arranged.
bond services hub – The site is organized and explanations are easy to digest.
action main – Wording highlights structured approaches to consistently acting on ideas.
official portal – Smooth navigation with well-organized information.
forwardmomentum.bond – Inspiring site, encourages steady progress and forward thinking clearly today.
check zorivoline – Looks intriguing enough to stay informed as it develops.
Primary platform – Discovered this page and the information is easy to understand.
ideas in motion – Messaging inspires action and makes concepts feel tangible and achievable.
elite insight – Words communicate expertise and reinforce strategic business thinking.
official finance hub – Navigation is intuitive, sections are well defined, and information is accurate.
beautiful oak studio – Overall, the aesthetic is gentle and refined, making the products stand out naturally.
Downloads – Resources are structured neatly, ensuring files are easy to access.
Vector Center – Professional visuals and organized content promote trust and clarity.
growth navigator – Text focuses on clear strategy and actionable progress.
continuumbond.bond – Clean presentation, messaging clearly communicates security and continuity.
trustflow.bond – Smooth visuals, messaging emphasizes clarity, confidence, and trust.
dreamvisioninsights.bond – Sleek presentation, content communicates vision clearly and simply.
FreshFieldsShop – Light, airy design makes shopping enjoyable.
Official Zorivo hub link – Layout is simple, content is easy to follow, and browsing is smooth.
financial site – Navigation is straightforward, and content is clear and reliable.
growth navigator – Site presents growth as achievable, with clear and inspiring messaging.
visit zylavobond – Information is presented clearly, and navigating feels natural.
claritymechanismhub.bond – Well-structured layout, content explains processes clearly and logically.
indigomarketshop.shop – Clear structure, products are showcased effectively and site is visually pleasant.
Bonded Framework Center – Organized pages, framework theme is evident and easy to navigate.
growth center – Messaging provides clear direction, motivating purposeful action.
zylavocore network – Consistent style and structure create a comfortable reading experience.
clarity center – Minimalist layout ensures ideas are noticeable and easy to understand.
RustwoodGoods – Simple interface with straightforward navigation and purchasing.
forwardpulse.bond – Friendly design, content encourages focused action and steady forward movement.
Learn more here – Clear design, readable text, and a welcoming browsing experience.
professional bond portal – Information is clearly presented, and navigation is seamless.
clarity guide – Wording is concise and helps users understand next steps with ease.
capitalunitycohesion.bond – Clear design, collaboration theme is easy to engage with.
ironmarketshop.shop – Well-organized store, product pages are clear and navigation is intuitive.
MistspireCornerShop – Smooth layout, browsing feels natural and ordering is simple.
securevault.bond – Professional design, navigation is smooth and content inspires confidence.
View project details – Branding is uniform, and content is presented in a straightforward way.
zavirocore.bond – Browsing the site is effortless, and the information feels reliable and easy to access.
Tandem Flow – Messaging is clear, design feels inviting and well organized.
solidway.bond – Clean navigation, messaging communicates a sense of security and dependability.
zylavotrustco overview – The site maintains a professional feel, inspiring trust from the first visit.
unitysphere.bond – Intuitive navigation, content reinforces cohesion and a sense of dependable partnership.
investment hub – Well-organized content, responsive pages, and minimal clutter.
apexalliant.bond – Modern layout, branding feels confident and content is easy to digest here.
firmpoint.bond – Modern design, pages highlight dependability and provide clear guidance for users.
Ridgecrest Hub Link – Text and layout together convey credibility and reliability.
Bonded Legacy Centerpoint – Intuitive design, legacy theme feels meaningful and professional.
clear impact framework – The wording suggests structure and purpose working together.
FernShoreGoods – Calm pages with straightforward navigation and a seamless checkout.
clarity insights – Messaging is streamlined, encouraging quick yet thoughtful action.
lightweight web resource – Feels fresh and uncomplicated to browse.
stablepathway.bond – Organized interface, messaging communicates grounded principles and approachability.
topbond.bond – Clean interface, messaging emphasizes stability and trust at every step.
route click guide – Smooth navigation, easy to understand and quick to use.
Signal Hub – Clear messaging, emphasizes forward momentum and actionable steps effectively.
rustic living emporium – The site combines charm with clarity, making shopping straightforward.
unifiedtrustinsights.bond – Polished and professional, messaging feels clear and navigation is seamless.
network guide shop – User-friendly layout, connecting with business partners feels smooth overall.
PetalBrookMarket – Relaxed design with smooth browsing and simple purchasing steps.
firmanchor.bond – Professional design, pages convey stability and inspire confidence naturally.
principlehub.bond – Strong concept, site emphasizes ethical standards and clear communication.
bond insight page – Informative and practical, makes exploring bonds hassle-free.
start exploring now – Text inspires curiosity and the willingness to try something new.
urbanwavefocus.bond – Clean design, website feels responsive and the information is digestible.
>smooth browsing hub – Fast loading and very easy to move around.
sbbridge.bond – Organized structure, pages communicate professionalism while maintaining a friendly tone.
principlebase.bond – Cohesive design, content clearly supports trustworthiness and sound principles.
financial guidance platform – Clean visuals, smooth navigation, and concise information enhance usability.
midnight cove shop online – Stylish nighttime vibe, products are easy to find and checkout is efficient.
ClickSecure – Offers a dependable platform for browsing products and checking out with ease.
bond resources hub – Clear, reliable, and helpful for managing investments.
click shopcurve – User-centric design, platform makes purchases simple and clear.
DigitalMart – Helps customers shop online quickly with minimal effort.
inspire ideas online – Informative and fun, encourages exploring unique approaches today.
forward navigator – Words and visuals encourage action while highlighting momentum.
Retail experience platform – Navigation is clear and exploring products is enjoyable.
online purchase hub – Hassle-free checkout, makes shopping convenient and enjoyable.
pillar finance page – Clear design makes exploring bonds straightforward and safe.
Trusted marketplace portal – Items are well organized, and the site feels credible.
quick study portal – Helpful insights, makes improving skills simple and actionable.
new ideas hub – Engaging content, full of innovative concepts worth exploring today.
Strategic innovation portal – The ideas are well presented, and moving through pages is easy.
Mivaro Trust Group official site – Pages are well-organized, information is clear, and the overall experience is helpful.
teamwork solutions hub – Smooth navigation, collaboration strategies are easy to grasp quickly.
Unity in business platform – Gives a worldwide impression with clear business direction.
purchase center online – Smooth interface, makes shopping quick and hassle-free today.